Les Bell and Associates Pty Ltd
Site blog

Upcoming Courses
Sydney
- SE221 CISSP Fast Track Review, 17 - 21 March 2025
- SE221 CISSP Fast Track Review, 21 - 25 July 2025
- SE221 CISSP Fast Track Review, 3 - 7 November 2025
Melbourne
- SE221 CISSP Fast Track Review, 28 April - 2 May 2025
- SE221 CISSP Fast Track Review, 25 - 29 August 2025
Online Virtual
- SE221 CISSP Fast Track Review, 20 - 24 January 2025
- SE221 CISSP Fast Track Review, 3 - 7 March 2025
- SE221 CISSP Fast Track Review, 12 - 16 May 2025
- SE221 CISSP Fast Track Review, 23 - 27 June 2025
- SE221 CISSP Fast Track Review, 18 - 22 August 2025
- SE221 CISSP Fast Track Review, 23 - 17 October 2025
- SE221 CISSP Fast Track Review, 24 - 28 November 2025
Online Virtual, One Day per Week for 5 Weeks
Online with Evening Classes Delivery
- SE221E CISSP Fast Track Review Evening Classes, 19 February - 7 May 2025
- SE221E CISSP Fast Track Review Evening Classes, 3 September - 19 November 2025
About this Blog
I produce this blog while updating the course notes for various courses. Links within a story mostly lead to further details in those course notes, and will only be accessible if you are enrolled in the corresponding course. This is a shallow ploy to encourage ongoing study by our students. However, each item ends with a link to the original source.
These blog posts are collected at https://www.lesbell.com.au/blog/index.php?user=3. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Our flagship CISSP Fast Track Review course is now fully updated to meet the 15 April 2024 exam outline. The course includes new material on a number of topics - principally artificial intelligence, high performance computing and networking.
"The course did not need much updating at all", said course developer and presenter Les Bell. "The course is continually updated and has always been slightly ahead of the CISSP detailed content outline, on the assumption that the material will turn up in the Common Body of Knowledge sooner or later."
In particular the presentation slides used during the 5-day course are backed by a wiki which contains over 670 pages of detailed information as well as references and links to external sources. For example, the wiki already contained pages on machine learning and artificial intelligence, as well as separate pages on attack techniques such as prompt injection and training data extraction, making it easy to expand. Using a wiki has made it easy to cross-reference and reorganise topics which may appear in multiple domains of the CISSP CBK.
The course is taught in both 5-day face-to-face sessions and a virtual/online format, using a blended learning approach which includes an online component. This includes quizzes with feedback which links directly back into the wiki, so that students get immediate detailed feedback, speeding pre-exam revision. The course site also provides other resources such as discussion forums and post-class support.
Further information, including the course schedule, is at https://www.lesbell.com.au/mod/page/view.php?id=481 (the schedule of upcoming courses is, of course, below).
Upcoming Courses
- SE221 CISSP Fast Track Review, Sydney, 11 - 15 March 2024
- SE221 CISSP Fast Track Review, Melbourne, 18 - 22 March 2024
- SE221 CISSP Fast Track Review, Virtual/Online, 13 - 17 May 2024
- SE221 CISSP Fast Track Review, Virtual/Online, 17 - 21 June 2024
- SE221 CISSP Fast Track Review, Sydney, 22 - 26 July 2024
About this Blog
I produce this blog while updating the course notes for various courses. Links within a story mostly lead to further details in those course notes, and will only be accessible if you are enrolled in the corresponding course. This is a shallow ploy to encourage ongoing study by our students. However, each item ends with a link to the original source.
These blog posts are collected at https://www.lesbell.com.au/blog/index.php?user=3. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
We've all received them - those not-very-clever text messages, 'apparently' from a toll road tag operator or similar, warning that the tag account has run out of funds and needs to be topped up. I say, 'apparently', because to most of us they're very apparently not genuine - but it seems enough people fall for them to make it profitable for the operators, as they damn things just kept coming.

A SIM box containing multiple SIM's and cellphone modems, used for smishing (Wikimedia Commons)
But we should see a sharp decline, following an operation by the NSW Police Cybercrime Squad, who set up a strike force to investigate a syndicate allegedly responsible for sending over 80 million fraudulent messages (given Australia's population of 25 million, that represents over-saturation) over 5 months.
Around 6 am on Thursday 15th Feb, the NSW Police's Public Order & Riot Squad assisted Strike Force Kanbi detectives in executing search warrants at two Sydney apartments. In one, police arrested two men, aged 37 and 43, and located three large SIM boxes along with "a number" of SIM cards. In another nearby apartment, they arrested a 35-year-old man and located a large amount of identity information, SIM cards, eight mobile phones and some cannabis.
The strike force detectives were assisted by local telcos, using their information to locate these SIM boxes and then plan their dawn raids.
At Burwood police station, the men were all charged with 'use equipment connected to network to commit serious offence' under section 474.14(1) of the Criminal Code Act 1995 (Cth) and 'deal with identity info to commit an indictable offence' under Section 192J of the Crimes Act 1900 (NSW), which carries a maximum penalty of 10 years imprisonment. The younger man faces an additional charge of possessing a prohibited drug.
The men were refused bail and appeared in the Burwood Local Court the following morning. They were formally refused bail and remanded to reappear in the same court on Friday 1 March. I dare say the police forensics unit will be taking a close look at any and all seized devices to gather further information about this group and their activities - which could lead to a prolonged trial.
NSW Police, Three men charged over alleged SMS phishing scam responsible for sending over 80 million fraudulent texts, news release, 26 February 2024. Available online at https://www.police.nsw.gov.au/news/news_article?sq_content_src=%2BdXJsPWh0dHBzJTNBJTJGJTJGZWJpenByZC5wb2xpY2UubnN3Lmdvdi5hdSUyRm1lZGlhJTJGMTEwNjMzLmh0bWwmYWxsPTE%3D.
Sydney Criminal Lawyers, Use Telecommunications Network with Intent to Commit Serious Offence, web page, 21 August 2023. Available online at https://www.sydneycriminallawyers.com.au/criminal/legislation/criminal-code-act/use-telecommunications-network-with-intent-to-commit-serious-offence/.
Upcoming Courses
- SE221 CISSP Fast Track Review, Sydney, 11 - 15 March 2024
- SE221 CISSP Fast Track Review, Melbourne, 18 - 22 March 2024
- SE221 CISSP Fast Track Review, Virtual/Online, 13 - 17 May 2024
- SE221 CISSP Fast Track Review, Virtual/Online, 17 - 21 June 2024
- SE221 CISSP Fast Track Review, Sydney, 22 - 26 July 2024
About this Blog
I produce this blog while updating the course notes for various courses. Links within a story mostly lead to further details in those course notes, and will only be accessible if you are enrolled in the corresponding course. This is a shallow ploy to encourage ongoing study by our students. However, each item ends with a link to the original source.
These blog posts are collected at https://www.lesbell.com.au/blog/index.php?user=3. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Ten years after its introduction, the US National Institute of Standards and Technology (NIST) has updated its ubiquitous Cybersecurity Framework (CSF).

The old version 1.1 was widely adopted, primarily because unlike many national and international standards, it is free. However, it was initially developed for use within US government agencies, for whom NIST is legally the official standards regulatory body, and then extended to cover critical infrastructure. It required some adaptation when used by private-sector and non-US organizations, but that did not stop it becoming one of the most popular frameworks. In fact, the older versions were translated into 13 languages.
Framework - Not a Standard
It's important to understand that the CSF is a framework, not a standard. Frameworks sit above standards, and provide a higher-level view of the requirements mandated by a range of standards. In essence, a framework is a conceptual model, and can be useful in clarifying one's thinking about the entire range of cybersecurity activities.
Of course, most of those requirements are security controls - and in that sense, the CSF is a controls catalogue. However, it actually cross-references the controls and control objectives from a range of different standards.
Another key convenience of the CSF is that it makes compliance efforts and gap analysis significantly easier. An organisation which has already implemented, or perhaps achieved certification against, a particular standard can use the CSF to check off requirements which it already meets from other standards. This makes it much easier to identify the work required to comply with additional standards.
Organization
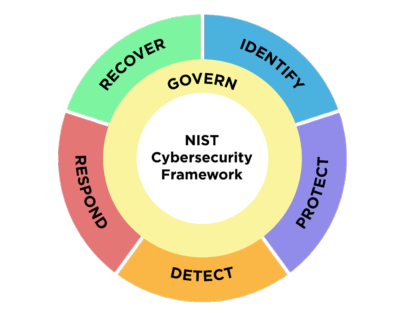
The original standard was organized around five key functions:
- Identify (assets, threats, vulnerabilities, etc.)
- Protect (assets, via authentication, authorization and other controls
- Detect (compromises and attacks)
- Respond (incident response)
- Recover (restore assets and operations)
To these has been added a new function, Govern, which encompasses the establishment, communication and monitoring of the organization's overall risk management strategy, policies and expectations. This is a large function, as it integrates with all the other functions.
Under the functions, as before we find categories and subcategories, along with the informative references which point to the relevant standards. However, the mapping spreadsheet now adds a column containing implementation examples, which help to clarify what the subcategory really means and how to comply.
Version 2.0 has been extensively reworked, with extensive community feedback on the draft, to meet the needs of a much wider set of communities, including the private sector and community organizations such as schools.
It has also been expanded - while the older versions really consisted of a single volume plus a huge spreadsheet mapping the framework to standards, it now adds an array of supporting resources. These include quick-start guides for small business and for the creation of organizational profiles, as well as guidance for the creation of community profiles. A second worksheet provides even more detail.
Also new is a searchable catalogue of informative references, as well as a Cybersecurity and Privacy Reference Tool (CPRT) which contains a browsable set of the NIST guidance documents. Finally, a CSF 2.0 Reference TOol allows exploration and searching of the entire CSF in both human-readable and machine readable (JSON) formats.
I would expect that many organizations will rapidly migrate to version 2.0 of the CSF. The framework can be found at https://www.nist.gov/cyberframework.
Uncredited, NIST Releases Version 2.0 of Landmark Cybersecurity Framework, news release, 26 February 2024. Available online at https://www.nist.gov/news-events/news/2024/02/nist-releases-version-20-landmark-cybersecurity-framework.
Upcoming Courses
- SE221 CISSP Fast Track Review, Sydney, 11 - 15 March 2024
- SE221 CISSP Fast Track Review, Melbourne, 18 - 22 March 2024
- SE221 CISSP Fast Track Review, Virtual/Online, 13 - 17 May 2024
- SE221 CISSP Fast Track Review, Virtual/Online, 17 - 21 June 2024
- SE221 CISSP Fast Track Review, Sydney, 22 - 26 July 2024
About this Blog
I produce this blog while updating the course notes for various courses. Links within a story mostly lead to further details in those course notes, and will only be accessible if you are enrolled in the corresponding course. This is a shallow ploy to encourage ongoing study by our students. However, each item ends with a link to the original source.
These blog posts are collected at https://www.lesbell.com.au/blog/index.php?user=3. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
 A recent news story reveals that artificial intelligence can pose yet another risk which many will not have anticipated.
A recent news story reveals that artificial intelligence can pose yet another risk which many will not have anticipated.
Many companies have switched to using chatbots to provide online customer support via their web sites - a chatbot will work 24/7 without breaks and, even better, without payment or complaining about working conditions. And of course, these chatbots have inevitably progressed from simple keyword-recognising rules engines to much more sophisticated conversationalists based on large language models. Ideally, these models would hardly need training - turn them loose on the company's web site, feed them a product catalog, pricing information and the related terms and conditions, and turn them loose to solve all your customer support problems.
However, a recent decision by the Civil Resolution Tribunal of British Columbia (Moffatt v. Air Canada) suggests that it's not quite that simple. Back in 2022, Jake Moffat suffered a family bereavement and needed to travel to Toronto to attend his grandmother's funeral. Some airlines offer concessions, such as reduced fares, for passengers traveling due to the death of an immediate family member (you learn something new every day). And so, Mr. Moffat went to the Air Canada web site to book his travel.
While on the site, he used the customer support chatbot, and asked it about bereavement fares. The reply (which Mr Moffat wisely captured as a screenshot) says, in part
Air Canada offers reduced bereavement fares if you need to travel because of an imminent death or a death in your immediate family.
…
If you need to travel immediately or have already travelled and would like to submit your ticket for a reduced bereavement rate, kindly do so within 90 days of the date your ticket was issued by completing our Ticket Refund Application form. (emphasis in original)
Now, the words "bereavement fares" were a highlighted and underlined link to Air Canada's specific web page dealing with bereavement travel - which says, in part, that the bereavement policy does not apply to requests for bereavement consideration oafter travel has been completed. Hence, the web page says one thing, but the chatbot says quite another.
In a previous telephone conversation with an Air Canada agent, Mr. Moffat was told that the bereavement fare would be approximately $C380. However, presumably relying on the information provided by the chatbot (though this is not explicitly stated), he went ahead and booked the Vancouver-Toronto flight, and a few days later booked the Toronto-Vancouver flight, for fares of $C794.98 and $C845.38, respectively.
He then set about applying for a partial refund of the fares to match the bereavement fare. Despite email exchanges through December 2022 and February 2023. Air Canada's position was that although the chatbot had provided "misleading words", it had provided the link to the bereavement travel web page and said that it would update the chatbot.
Before the Tribunal, Air Canada argued that it cannot be held liable for information provided by one of its agents, servants or representatives, and that the chatbot is a separate legal entity that is responsible for its own actions - a position the Tribunal found to be "remarkable". Holding that the chatbot is still just a part of the Air Canada web site, and that the company is responsible for all the information on that site, the Tribunal found that Mr. Moffat's claim of negligent misrepresentation was successful and awarded damages.
A few key takeways:
- It is reasonable for a customer (or other user) to rely upon the information provided by a chatbot.
- Although the chatbot may provide a link to an information page that contains additional information, there is no reason why a customer should know that one part of the site is accurate, and another is not.
- A chatbot effectively acts as an agent of the company which operates it. It really is not sensible to argue that it has independent agency in its own right.
Cecco, Leyland, Air Canada ordered to pay customer who was misled by airline’s chatbot, The Guardian, 17 February 2024. Available online at https://www.theguardian.com/world/2024/feb/16/air-canada-chatbot-lawsuit.
Moffatt v. Air Canada, 2024 BCCRT 149, CanLII, 14 February 2024. Available online at https://canlii.ca/t/k2spq.
Upcoming Courses
- SE221 CISSP Fast Track Review, Sydney, 11 - 15 March 2024
- SE221 CISSP Fast Track Review, Melbourne, 18 - 22 March 2024
- SE221 CISSP Fast Track Review, Virtual/Online, 13 - 17 May 2024
- SE221 CISSP Fast Track Review, Virtual/Online, 17 - 21 June 2024
- SE221 CISSP Fast Track Review, Sydney, 22 - 26 July 2024
About this Blog
I produce this blog while updating the course notes for our various courses. Links within a story mostly lead to further details in those course notes, and will only be accessible if you are enrolled in the corresponding course. This is a shallow ploy to encourage ongoing study by our students. However, each item ends with a link to the original source.
These blog posts are collected at https://www.lesbell.com.au/blog/index.php?user=3. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
One of my personal security mantras is: The enemy of security is complexity. A fascinating post in IEEE Spectrum makes the same point, specifically about contemporary approaches to software development.

In "Why Bloat Is Still Software's Biggest Vulnerability", Bert Hubert calls out software architects and developers generally over the dire state of software security, pointing to the last year's highly-publicized exploitations of Ivanti, MOVEit, Outlook, Confluence, Barracuda Email Security Gateway and the Citrix NetScaler products - to name just a few.
The current software market actually penalizes developers who take the time to deal with security properly. The market continuously demands new software, with more and more sophisticated features (if your product doesn't incorporate AI in some form, you're dead in the water). At the same time, customers prize convenience, and there's a huge advantage to the first movers in the market - hence a focus on shipping a minimum viable product before the seed capital runs out. Security? Well, we can figure that out later.
A particular problem is the increasing reliance on third-party - usually open-source - libraries sourced from repositories which may themselves have vulnerabilities. Hubert points to one, relatively simple, photo-sharing application which has 1,600 dependencies on external libraries (!). This provides an attacker with an enormous attack surface which is largely beyond the control of both the central application developer and the user.
External libraries are well-nigh essential when a product has to provide a wide range of functionality. As Hubert explains, the Barracuda Email Security Gateway vulnerability lay in the way a third-party Perl module would unpack Excel spreadsheets to scan them for malware - allowing arbitrary code execution as it did so. But if you're a security pro working on a mail gateway product, do you want to invest the time and effort required to write your own code to securely parse a spreadsheet file? I thought not.
To Hubert's credit, he puts his money where his mouth is by developing a lean image-sharing program that consists of just 1,600 lines of source code plus five important dependencies.
Is there an answer to the increasing complexity of software, along with the exponentially-growing attack surface it presents? It would be a brave man that pushes back against the demand for do-everything functionality, especially in a security product. But I can't help wondering how many times the Barracuda product actually saved a completely naive user from opening a spreadsheet and allowing it run a malware macro, versus how many organizations' networks were exploited via the vulnerability in the email gateway.
The US Cybersecurity & Infrastructure Security Agency has partnered with the Open Source Security Foundation (OpenSSF) Securing Software Repositories Working Group to publish the Principles for Package Repository Security framework. This defines four levels of security maturity for package repositories to be measured in areas sich as authentication, authorization, CLI tooling and general capabilities. This at least allows the establishment of a roadmap to secure that end of the software supply chain.
In the meantime, I know I'll be pursuing a lean approach wherever possible.
Cable, Jack and Zach Steindler, Principles for Package Repository Security, Open Source Security Foundation, February 2024. Available online at https://repos.openssf.org/principles-for-package-repository-security.
Hubert, Bert, Why Bloat Is Still Software’s Biggest Vulnerability: A 2024 plea for lean software, IEEE Spectrum, 8 February 2024. Available online at https://spectrum.ieee.org/lean-software-development.
Upcoming Courses
- SE221 CISSP Fast Track Review, Sydney, 11 - 15 March 2024
- SE221 CISSP Fast Track Review, Melbourne, 18 - 22 March 2024
- SE221 CISSP Fast Track Review, Virtual/Online, 13 - 17 May 2024
- SE221 CISSP Fast Track Review, Virtual/Online, 17 - 21 June 2024
- SE221 CISSP Fast Track Review, Sydney, 22 - 26 July 2024
About this Blog
I produce this blog while updating the course notes for various courses. Links within a story mostly lead to further details in those course notes, and will only be accessible if you are enrolled in the corresponding course. This is a shallow ploy to encourage ongoing study by our students. However, each item ends with a link to the original source.
These blog posts are collected at https://www.lesbell.com.au/blog/index.php?user=3. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
We have long known of the potential for machine learning algorithms to graft celebrity faces onto pornographic images, or to modify the pitch and timbre of a speaker's voice so as to emulate that of another person - a process known as deep faking. For several years now, we have seen examples of deepfaked video in which political identities such as US President Barack Obama, appear to say things they have never said, and such videos are reported to be used increasingly in state-sponsored information warfare.

(Image credit: Sean Pollock, via Unsplash)
For some time now, it has been possible to perform voice modification in real time - the pre-training of the model takes some time, but the subsequent voice modification through the model can be done by an app. However, now comes news of a whaling attack which is notable for at least three reasons:
- The apparent use of real-time voice and video deepfaking to trick a finance worker
- The deepfaking of multiple participants in a video conference
- The scale of the fraud - $HK200 million (approximately $US25.6 million)
An employee of a multinational company was apparently lured into attending a video call with several other staff. The email lure, apparently from the UK-based CFO of the firm, spoke of the need for a secret transaction, which raised the employee's suspicions. However, when he attended the linked video conference, his doubts were assuaged by the presence of several other attendees whom he recognised - all of whom were, in fact, faked.
Consequently, he followed the instructions and transferred the funds as requested. The scam was only discovered when the employee checked with the corporation's head office.
The case was one of several revealed by Hong Kong police in a press conference on Friday. In other cases, stolen HK identity cards were used to make fraudulent loan applications and AI deepfakes were used to trick facial recognition programs.
These cases show the need for increased security controls to be placed around video conferencing software and related email accounts. Organizations have been slow to deploy phishing-resistent multi-factor authentication technologies such as security keys and passkeys, preferring to rely on low-cost solutions such as mTAN's (the six-digit verification codes sent as text messages - these were deprecated by NIST back in 2017!). The result is a continuing high number of credential compromises.
This leads to secondary compromises, especially in systems which use an email address as a single sign-on identifier across multiple services. While the video conferencing system used in the attack above was not identified, all the big players - Zoom, Microsoft Teams/Skype and Google Meet - support federated identity management over protocols such as OAuth2. Consequently, once an email account falls, so do all the related services, including video conferencing.
Furthermore, most video conferencing platforms allow the user to choose their displayed name, so that an attacker need not even use a compromised account - they can just change their name.
Suggested mitigations for these attacks would include:
- Requiring phishing-resistant multi-factor authentication on privileged and influential email accounts (never allow the C-suite to claim they're too busy and important to waste their time - they need to be demonstrating security leadership)
- Configuring video-conferencing accounts to require meeting participants to log in using email accounts within the corporate domain and protected by MFA (although one participant's account may be compromised, it's unlikely all participants could be faked)
- Never allow the person whose identity you want to verify to control or set up the verification mechanism. The verifier should create the meeting and set its controls to be as restrictive as possible, and should initiate it at a time of their choosing - although deepfaking can be performed in real time, it may take the attacker some time to set up their software.
In the long run, organizations need to redesign their payment authorization procedures to incorporate stronger authentication using cryptographic techniques. Until they do, these types of business email compromise and whaling attacks will only increase in both frequency and severity.
(Thanks to Gadi Evron for directing us to this story.)
Chen, Heather and Kathleen Magramo, Finance worker pays out $25 million after video call with deepfake ‘chief financial officer’, CNN Asia, 4 February 2024. Available online at https://edition.cnn.com/2024/02/04/asia/deepfake-cfo-scam-hong-kong-intl-hnk/index.html.
Upcoming Courses
- SE221 CISSP Fast Track Review, Virtual/Online, 15 - 19 January 2024
- SE221 CISSP Fast Track Review, Sydney, 11 - 15 March 2024
- SE221 CISSP Fast Track Review, Melbourne, 18 - 22 March 2024
- SE221 CISSP Fast Track Review, Virtual/Online, 13 - 17 May 2024
- SE221 CISSP Fast Track Review, Virtual/Online, 17 - 21 June 2024
- SE221 CISSP Fast Track Review, Sydney, 22 - 26 July 2024
About this Blog
I produce this blog while updating the course notes for various courses. Links within a story mostly lead to further details in those course notes, and will only be accessible if you are enrolled in the corresponding course. This is a shallow ploy to encourage ongoing study by our students. However, each item ends with a link to the original source.
These blog posts are collected at https://www.lesbell.com.au/blog/index.php?user=3. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.

We'll be back early next year with new and updated courses!
Upcoming Courses
- SE221 CISSP Fast Track Review, Virtual/Online, 15 - 19 January 2024
- SE221 CISSP Fast Track Review, Sydney, 11 - 15 March 2024
- SE221 CISSP Fast Track Review, Melbourne, 18 - 22 March 2024
- SE221 CISSP Fast Track Review, Virtual/Online, 13 - 17 May 2024
- SE221 CISSP Fast Track Review, Virtual/Online, 17 - 21 June 2024
- SE221 CISSP Fast Track Review, Sydney, 22 - 26 July 2024
About this Blog
I produce this blog while updating the course notes for various courses. Links within a story mostly lead to further details in those course notes, and will only be accessible if you are enrolled in the corresponding course. This is a shallow ploy to encourage ongoing study by our students. However, each item ends with a link to the original source.
These blog posts are collected at https://www.lesbell.com.au/blog/index.php?user=3. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
The activities of a threat actor affialiated with the Russian Federal Security Service (FSB) have been detailed in a new report prepared by the UK's Nactional Cyber Security Centre and international partners, while the British Foreign Secretary has described their activies as "completely unacceptable", and two individuals have been designated under the UK's cyber sanctions regimen.

According to junior Foreign Office minister Leo Docherty, speaking to the House of Commons, the FSB "is behind a sustained effort to interfere in our democratic processes. They have targeted members of this house and the House of Lords. They have been targeting civil servants, journalists and NGO's. They have been targeting high-profile individuals and entities with a clear intent - using information they obtain to meddle in British politics".
Doherty singled out an FSB unit called Centre 18, which is associated with a threat group tracked by Microsoft as Star Blizzard (previously SEABORGIUM, and also known as Callisto Group, TA446 and COLDRIVER). The group has "selectively leaked and amplified the release of sensitive information in service of Russia's goals of confrontation", including an earlier release of documents related to UK-US trade.
Although today's disclosures in the British Parliament primarily relate to Star Blizzard's efforts against the UK, the group is known to target other countries in the NATO alliance - principally the US, but also the Baltic states, Scandinavia and Eastern Europe - as well as Ukraine in the lead-up to the invasion there. No surprise, then, that a number of international partners have collaborated with the UK's NCSC to prepare a report on the TTP's employed by Star Blizzard.
The group employs a 'low and slow' approach to profiling their targets, who are generally in academia, defence, government organisations, NGO's, think tanks and, of course, politicians, using open-source resources such as social media and professional networking platforms. In particular, they catalogue the targets' interests and their real-world social or professional targets.
This information is used to create email and social media accounts masquerading as known contacts and industry experts. These may be used to lend credence to spoofed invitations to conferences or industry events as a lure in spear phishing emails, but first, Star Blizzard takes time to build trust through an exchange of benign correspondence, and also favours using personal email addresses in order to bypass controls in place on enterprise networks.
The actual attack is accomplished via spear phishing, typically via a link to a malicious web site or document. Access to this will require the victim to enter their account credentials into an actor-controlled web server running the EvilGinx framework, allowing the threat actor to harvest credentials and session cookies, thereby bypassing multi-factor authentication.
The credentials are then used to log into the victim's email account, from which they can harvest emails and attachments, and also set up mail forwarding rules, allowing them to easily monitor all future correspondence. The NCSC report maps all of the tactics and techniques to the MITRE ATT&CK framework. The mitigations are fairly obvious:
- Good password hygiene (strong passphrases, no password re-use across services)
- Use of phishing-resistant multi-factor authentication (security keys, passkeys when available)
- Enabling email providers' advanced email scanning and protection features
- Disabling mail forwarding rules and reviewing this setting periodically to detect changes
- Finally, the tough one: eternal vigilance by users - being alert for subtle differences in email addresses, such as the use of a generic webmail service when previous correspondence has come from an enterprise domain and checking via an alternative channel such as phone if suspicious
Mason, Rowena, Russian spies targeting UK MPs and media with ‘cyber interference’, The Guardian, 7 December 2023. Available online at https://www.theguardian.com/politics/2023/dec/07/russian-spies-targeting-uk-mps-and-media-with-cyber-interference.
Microsoft Digital Threat Analysis Center, Disrupting SEABORGIUM’s ongoing phishing operations, threat intelligence report, 15 August 2022. Available online at https://www.microsoft.com/en-us/security/blog/2022/08/15/disrupting-seaborgiums-ongoing-phishing-operations/.
NCSC, Russian FSB cyber actor Star Blizzard continues worldwide spear-phishing campaigns, advisory, 7 December 2023. Available online at https://www.ncsc.gov.uk/files/Advisory-Russian-FSB-cyber-actor-star-blizzard-continues-worldwide-spear-sphishing-campaigns.pdf.
Upcoming Courses
- SE221 CISSP Fast Track Review, Sydney, 11 - 15 March 2024
- SE221 CISSP Fast Track Review, Virtual/Online, 13 - 17 May 2024
- SE221 CISSP Fast Track Review, Virtual/Online, 17 - 21 June 2024
- SE221 CISSP Fast Track Review, Sydney, 22 - 26 July 2024
About this Blog
I produce this blog while updating the course notes for various courses. Links within a story mostly lead to further details in those course notes, and will only be accessible if you are enrolled in the corresponding course. This is a shallow ploy to encourage ongoing study by our students. However, each item ends with a link to the original source.
These blog posts are collected at https://www.lesbell.com.au/blog/index.php?user=3. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
The US Cybersecurity & Infrastructure Security Agency is continuing its campaign for software that is secure by design by releasing a new guide aimed at both developers and their C-suites. While developers using systems programming languages like C, C++ and - most of all - assembler are aware of the problems associated with memory management in those languages, fixing those problems has seemed to be an intractable problem.

We've come up with a range of controls to mitigate memory vulnerabilities, from programmer education through code analysis tools to runtime techniques such as stack offset randomization - and yet memory problems remain with us: just last year, Google reported that use-after-free errors accounted for half of the exploitable bugs in the Chrome browser, while about 70 percent of Microsoft CVE's (over the 2006-2018 timeframe) were memory safety vuln's.
Clearly, many of these techniques are not being applied; either they are seen as speed bumps which will slow development and delay product release, or there is no budget, or they are simply overlooked. The most sure-fire way to achieve memory safety is to switch to the use of modern, memory-safe languages such as Go and Rust, but that is an even greater hurdle, requiring programmer retraining, re-tooling and sourcing new libraries and subsystems. This cannot be achieved without senior management backing, which is why CISA's new guide, The Case for Memory Safe Roadmaps: Why Both C-Suite Executives and Technical Experts Need to Take Memory Safe Coding Seriously, is intended for the C-suite as well as developers.
The 23-page guide, which was jointly developed with international partners, provides a comprehensive overview of both current and emerging memory safety techniques, including
- Developer training
- Code coverage
- Secure coding guidelines
- Fuzzing
- SAST/DAST
- Safer language subsets
- Non-executable memory
- Control flow integrity
- Address Space Layout Randomization
- Other compiler mitigations
- Sandboxing
- Hardening memory allocators
- Hardware-based mitigation techniques
It then turns to the case for memory-safe languages, and lays out a strategy for planning the transition to such languages, from language selection through managing staff capabilities and resourcing. It also delves into related issues, such as the requirement for tertiary education in computer science to be updated, and the special considerations for operational technology, low-power and IoT systems.
The Case for Roadmaps
The goal is for software publishers to write and publish their memory safety roadmaps, in line with the secure by design principles of (1) taking ownership of their security outcomes, (2) adopting radical transparency, and (3) taking a top-down approach to developing secure products. Such a roadmap should include:
- Defined phases with dates and outcomes
- A date after which all code will be written solely in a memory-safe language
- Internal developer training and integration plan
- A plan to handle dependencies on libraries - many of them open-source - which are written in C and C++
- A plan to ensure transparency via regular public updates
- A CVE support program plan, with reports that provide detail about coding errors
This is going to require buy-in from senior management and even boards. But this shouldn't be a problem: the widespread publicity associated with breaches attributable to vulnerable software products can be highly damaging. Most security professionals can rattle off a list of brands which have suffered reputation damage in recent months, let alone over the years.
The guide also provides a list of external resources and a brief overview of the major memory-safe languages
CISA, The Case for Memory Safe Roadmaps: Why Both C-Suite Executives and Technical Experts Need to Take Memory Safe Coding Seriously, technical report, 6 December 2023. Available online at https://www.cisa.gov/resources-tools/resources/case-memory-safe-roadmaps.
Upcoming Courses
- SE221 CISSP Fast Track Review, Sydney, 11 - 15 March 2024
- SE221 CISSP Fast Track Review, Virtual/Online, 13 - 17 May 2024
- SE221 CISSP Fast Track Review, Virtual/Online, 17 - 21 June 2024
- SE221 CISSP Fast Track Review, Sydney, 22 - 26 July 2024
About this Blog
I produce this blog while updating the course notes for various courses. Links within a story mostly lead to further details in those course notes, and will only be accessible if you are enrolled in the corresponding course. This is a shallow ploy to encourage ongoing study by our students. However, each item ends with a link to the original source.
These blog posts are collected at https://www.lesbell.com.au/blog/index.php?user=3. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.