Les Bell and Associates Pty Ltd
Blog entries about Les Bell and Associates Pty Ltd
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
Swedish Companies Fined for Using Google Analytics
In a heads-up for privacy professionals everywhere, the Swedish Authoruty for Privacy Protection (Integritetsskyddsmyndigheten - IMY) has fined two companies for using Google Analytics and warned one, along with two others, to bring their security measures into line with the requirements of the EU GDPR (General Data Protection Regulation).
The decision stems from ongoing concerns held by the EU over invasive US surveillance programs, such as PRISM and UPSTREAM, which could expose the personally identifiable information of EU residents which had been transferred to the US for processing by service providers. The US has attempted to assuage EU fears with the establishment of various compliance programs; initially a set of principles termed Safe Harbor, which was replaced in 2016 by the Privacy Shield framework. This establishes a list of companies to which EU firms could legally transfer PII; the list is maintained by the US Department of Commerce and compliance with its requirements is monitored by the US Federal Trade Commission.
However, in July 2020, the Court of Justice of the European Union declared the EU's Privacy Shield Decision invalid on account of invasive US surveillance, and stipulated stricter requirements for the transfer of data based on standard contract clauses (SCC's) which must provide data subjects a level of protection essentially equivalent to the EU GDPR and the EU Charter of Fundamental Rights. If the standard contract clauses are insufficient to do this, then EU companies which transfer PII to the US must implement additional safeguards to compensate.
Sweden's IMY has audited how four companies transfer personal data to the US via Google Analytics - specifically, a version of Google Analytics from 14 August 2020 - based on complaints from the organisation, None of Your Business (NOYB). IMY considers the data to be personal data because it can be linked with other unique data that is transferred (which is rather the point of targeted advertising analytics). The four companies based their decision to utilise Google Analytics on standard contract clauses, but after audit, IMY decided that none of the companies' additional technical security measures were sufficient.
The four companies involved are:
- Tele2 SA, which was fined 12 million Swedish Krona
- CDON AB, fined 300,000 Swedish Krona
- Coop SA
- Dagens Industri
Tele2 SA had already independently decided to stop using Google Analytics; the other three firms were ordered to stop and to implement adequate data protection mechanisms. This decision aligns with similar steps taken by authorities in Austria, France and Italy; Facebook parent Meta had previously been fined a record $U1.3 billion by the EU. All eyes are now turning to the finalization of a proposed replacement for Privacy Shield, to be called the EU-US Privacy Framework.
IMY, Four companies must stop using Google Analytics, news release, 3 July 2023. Available online at https://www.imy.se/en/news/four-companies-must-stop-using-google-analytics/.
noyb, noyb win: First major fine (€1 million) for using Google Analytics, news release, 3 July 2023. Available online at https://noyb.eu/en/noyb-win-first-major-fine-eu-1-million-using-google-analytics.
Ghostscript Feature Turns Bug, Then Turns Vulnerability
Since the release of the Apple Laserwriter back in the 1980's, the leading page description and graphics language for printers has been PostScript. It turns up everywhere: embedded into printers, but also as the underlying language for PDF, the Portable Document Format, used for document interchange near-universally. It is also an essential component of LaTeX, the technical editing and publishing system used by computer science academics and mathematicians for typesetting their work. In particular, a lot of technical graphics gets generated in the form of Postscript - particularly Encapsulated Postscript (.eps) files. And while there are plenty of PDF viewers to choose from, the majority of academics writing LaTeX will use Ghostscript to render and view .ps and .eps files.
Writing for Sophos' Naked Security blog, Paul Ducklin describes how a long-lived feature of the venerable Ghostscript program turned out to be not just a bug, but an exploitable vulnerability. On UNIX and Linux systems, print processing used to be done using shell scripts that would run a series of small text processing programs to generate whatever format the connected printer required - and to do this, they would pipe the output of one program into the next. This is a fundamental feature of the classic Software Tools concept that underlies UNIX - write small programs that each do one thing, and do it will, and then combine them to accomplish more complex tasks.
The combination is performed by using the I/O redirection features of the shell - that is, > to send the output of a program to a file, < to read the input of a program from a file, and | (the pipe symbol) to connect the output of one program into the input of the next, via an in-memory buffer. And it's not just UNIX that has this ability - Microsoft introduced it into MS-DOS 2.0 in the early 1980's (although being a single-tasking system, DOS had to run one program after the other and faked pipes via temporary files) and it lives on in Windows. Ghostscript is also often used in web applications, to generate downloadable documents from web pages.
It turns out that Ghostscript's PostScript implementation can open and write to files. And, like many UNIX programs, as well as simple file pathnames, it will accept strings that begin with the pipe symbol, |, and continue with a command into which the output will be written. In fact, this can be a complete command line, with options and arguments, etc. (Actually, the string %pipe% can also be used, in Ghostscript).
If you're a security pro, you should by now be thinking of various ways this can be used maliciously. In short, it will allow an innocuous PostScript, EPS or even PDF file to execute commands on the target system. However, this was only realized fairly recently, giving rise to CVE-2023-36664, which is finally fixed in Ghostscript 10.01.2. I say finally because, rushing to get a patch out the door, the maintainers' first attempt only checked for the %pipe% string, and it required a second attempt to also match the | symbol. This is not that unusual when programmers are under pressure to fix a vulnerability.
Ducklin, Paul, Ghostscript bug could allow rogue documents to run system commands, blog post, 4 July 2023. Available online at https://nakedsecurity.sophos.com/2023/07/04/ghostscript-bug-could-allow-rogue-documents-to-run-system-commands/.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
Chinese APT Implants Ancient Trojan Via HTML Smuggling
Check Point Research brings us a report of a Chinese threat actor which is targeting foreign affairs ministries and embassies in a number of European countries - primarily the UK, Czech Republic, Hungary, Slovakia and Ukraine - with the likely goal of cyber-espionage, as indicated by the lure documents in the compaign emails, such as a letter originating from the Serbian embassy in Budapest, and an invitation to a diplomatic conference issued by Hungary's Ministry of Foresign Affairs.
The campaign - which Check Point have christened 'SmugX' - overlaps with previously-reported activity by the Chinese APT's RedDelta and Mustang Panda, and has been running since at least December 2022. It makes use of HTML smuggling - a technique in which the attackers hide a malicious payload inside HTML documents, enabling it to bypass network controls. Opening one of these documents starts a first stage loader consisting of the following chain of events:
- The embedded payload within some JavaScript code is decoded and saved to a blob with the appropriate filetype (e.g. application/zip)
- Instead of utilizing the HTML <a> element, the JavaScript code dynamically creates it
- A URL object is created from the blob using the createObjectURL function
- The download attribute is set with the desired filename
- Finally, the code invokes the click action, simulating a user clicking on the link, to initiate the file download
- For older browsers, the code employs msSaveOrOpenBlob to save the blob under the desired filename
This then chains to a second stage loader, of which there are two variants. The first uses a ZIP file that contains a malicious LNK file which will run PowerShell code to extract a compressed archive and save it to the %temp% directory. This archive contains three files:
- A legitimate executable - either robotaskbaricon.exe or passwordgenerator.exe - taken from a vulnerable version of the Roboform password manager
- A malicious sideloaded DLL called RoboForm.dll
- The malware payload, in a file called data.dat
The PowerShell code then runs the executable. The DLL sideloading technique allows the malicious code to be run within the context of this apparently legitimate process.
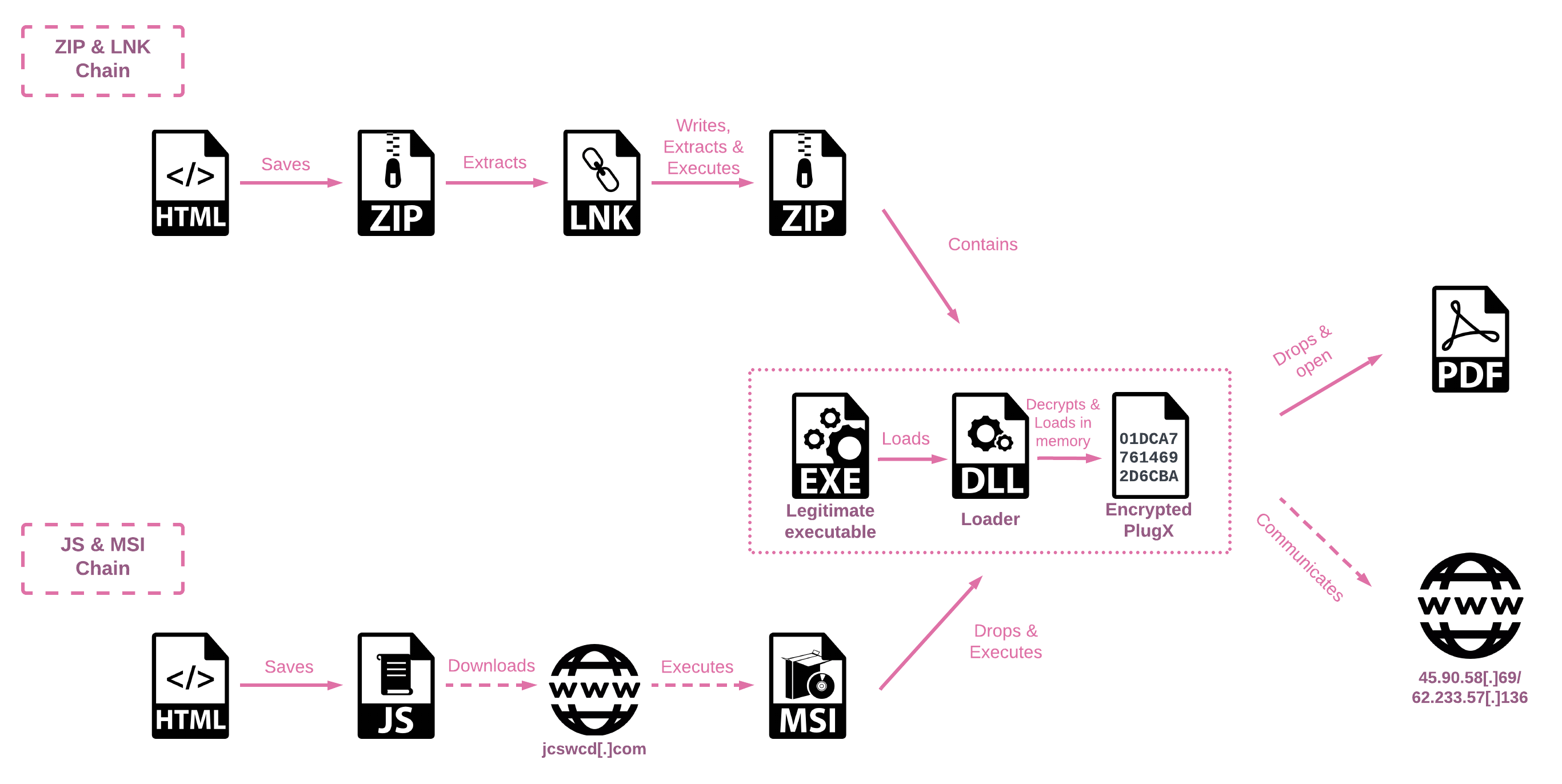
The two infection chains (image credit: Check Point Research)
The second variant of the second-stage loader uses JavaScript, rather than PowerShell, to download a MSI file, but installs the same three files.
The final payload is the PlugX remote access trojan, which has been used by multiple Chinese threat actors since 2008; its long life may be attributed to its modular structure which accommodates a variety of plugins which extend its functionality to include file theft, screen captures, keystoke logging and remote command execution. One notable change in this version is the switch to using RC4 encryption rather than the simple XOR technique used in previous samples.
The use of a variety of HTML smuggling infection chains, coupled with DLL sideloading, seems to have allowed this and perhaps similar campaigns to evade detection.
Check Point Research, Chinese Threat Actors Targeting Europe in SmugX Campaign, report, 3 July 2023. Available online at https://research.checkpoint.com/2023/chinese-threat-actors-targeting-europe-in-smugx-campaign/.
ISC2 Bylaws Voting Resumes
As we reported last week, the International Information Systems Security Certification Consortium - (ISC)2 - ran into difficulties with some of its online systems, specifically the page for making Annual Maintenance Fee payments, but more importantly the page for voting on proposed bylaw amendments.
While I continue to do battle with (ISC)2 over the AMF payment snafu, at least the bylaw voting process has resumed. Members can find a link to the voting page at the top of their dashboard after logging in - https://my.isc2.org/s/dashboard. Before voting, I recommend reading Stephen Mencik's blog posts, at https://smencik1.wordpress.com/2023/06/06/upcoming-by-laws-vote-info-and-recommendation/ and https://smencik1.wordpress.com/2023/06/26/by-laws-voting/.
CISA Vulnerability Summary
The US Cybersecurity and Infrastructure Security Agency has released its vulnerability summary for the week of 26 June. The list is long, but helpfully broken into sections by CVSS severity levels:
- High: vulnerabilities with a CVSS base score of 7.0 - 10.0
- Medium: vulnerabilities with a CVSS base score of 4.0 - 6.9
- Low: vulnerabilities with a CVSS base score of 0.0 - 3.9
So far, I have only skimmed quickly - I will search for anything directly relevant to my needs later - but I'm seeing a lot of WordPress plugins as well as Apple and Android OS's getting mentions. It seems all the usual categories of vulnerabilities keep turning up: use-after-free, directory traversals, Time-of-Check/Time-of-Use, out-of-bounds reads. Sigh - maybe it's time for we humans, creatures of bounded rationality as we are, to give up writing software, we are so bad at it.
CISA, Vulnerability Summary for the Week of June 26, 2023, bulletin, 3 July 2023. Available online at https://www.cisa.gov/news-events/bulletins/sb23-184.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
Active Exploitation of WordPress Plugin
Specialist WordPress security firm Wordfence has reported on active exploitation of an unpatched privilege escalation vulnerability in Ultimate Member, a plugin installed on over 200,000 WordPress sites. The vulnerability has not been properly patched in version 2.6.6, the latest version of the plugin, and Wordfence recommend uninstalling the plugin until a complete patch becomes available.
The Ultimate Member plugin is intended to add easy registration and account management on WordPress sites. Unfortunately, the registration form component performs inadequate sanitization of form keys, making it possible for users to register and set arbitrary metadata on their account - including the wp_capabilities meta value which, if set to 'administrator', blesses an attacker with full capabilities on the site. Although a series of updates have attempted to block this by including a predefined list of banned metadata keys, attackers have found a number of simple ways to bypass this, such as varying the case, including slashes, and URL-encoding the keys.
The result is CVE-2023-3460, which garners a CVSS score of 9.8 (Critical). Wordfence's advisory provides indicators of compromise, and the company has released a firewall rule for their products which will protect customers against exploitation.
Chamberland, Chloe, PSA: Unpatched Critical Privilege Escalation Vulnerability in Ultimate Member Plugin Being Actively Exploited, blog post, 29 June 2023. Available online at https://www.wordfence.com/blog/2023/06/psa-unpatched-critical-privilege-escalation-vulnerability-in-ultimate-member-plugin-being-actively-exploited/.
Avast Releases Akira Decryptor
Anti-malware firm Avast has released a decryptor for the Akira ransomware which appeared in March 2023 and has gone on to attack a variety of industries including education, finance and real estate. Akira's approach to file encryption is interesting - its authors favouring a lightweight, fast approach (using Dan Bernstein's Chacha 2008 stream cipher) that only partially encrypts files in order to render them unusable, rather than performing full encryption. In most respects, it is similar to the earlier Conti ransomware, suggesting a link of some kind between the authors.
For files of 2,000,000 bytes and smaller, the ransomware encrypts the first half of the file, while for larger files, it encrypts four blocks interspersed within the file. In both cases, the encryption uses a random key, and Akira appends a structure which contains the original file size, the malware version number, the type of encryption performed and the random key, encrypted using RSA public-key crypto with a 4096-bit modulus. The extension .akira is then appended to the filename, and an akira_readme.txt ransom note is dropped into each folder.
In order to use Avast's decryptor, a victim must find a matched pair of files - one encrypted, one the pre-ransom unencrypted version - that are as large as possible. The decryption tool will examine these and attempt to extract the decryption key. Once this is found, the decryptor tool can proceed to decrypt all the files on drive, optionally saving backups as it goes (highly recommended).
The Avast researchers do not describe how their key-cracking process works, but I have my suspicions (and my former cryptography students should be able to guess, too 😉).
Of course, the decryptor tool cannot provide any protection against any consequences of information exfiltration threatened in the Akira ransom note - it can only recover lost files.
Avast Threat Research Team, Decrypted: Akira Ransomware, blog post, 29 June 2023. Available online at https://decoded.avast.io/threatresearch/decrypted-akira-ransomware/.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
MITRE Updates Top 25 Most Dangerous Software Vulnerabilities
The Homeland Security Systems Engineering and Development Institute, which is operated for the DHS by MITRE, has released its 2023 Common Weakness Enumeration (CWE) Top 25 Most Dangerous Software Weaknesses. This is calculated by analyzing the last two years' public vulnerability data in the National Vulnerability Data (NVD) - that's 43,996 CVE records - for root cause mappings to CWE weaknesses. The 2023 CWE Top 25 also incorporates updated data for recent CVE records in the database that underlies CISA Known Exploited Vulnerabilities Catalog (KEV).
The top 25 are:
- Out-of-bounds Write CWE-787
- Improper Neutralization of Input During Web Page Generation ('Cross-site Scripting') CWE-79
- Improper Neutralization of Special Elements used in an SQL Command ('SQL Injection') CWE-89
- Use After Free CWE-416
- Improper Neutralization of Special Elements used in an OS Command ('OS Command Injection') CWE-78
- Improper Input Validation CWE-20
- Out-of-bounds Read CWE-125
- Improper Limitation of a Pathname to a Restricted Directory ('Path Traversal') CWE-22
- Cross-Site Request Forgery (CSRF) CWE-352
- Unrestricted Upload of File with Dangerous Type CWE-434
- Missing Authorization CWE-862
- NULL Pointer Dereference CWE-476
- Improper Authentication CWE-287
- Integer Overflow or Wraparound CWE-190
- Deserialization of Untrusted Data CWE-502
- Improper Neutralization of Special Elements used in a Command ('Command Injection') CWE-77
- Improper Restriction of Operations within the Bounds of a Memory Buffer CWE-119
- Use of Hard-coded Credentials CWE-798
- Server-Side Request Forgery (SSRF) CWE-918
- Missing Authentication for Critical Function CWE-306
- Concurrent Execution using Shared Resource with Improper Synchronization ('Race Condition') CWE-362
- Improper Privilege Management CWE-269
- Improper Control of Generation of Code ('Code Injection') CWE-94
- Incorrect Authorization CWE-863
- Incorrect Default Permissions
CWE-276
There are a couple of new entrants in the list: 22. Improper Privilege Management shot up from 29th position last year, while 24. Incorrect Authorization moved from #28. Also rocketing up the charts were 4. Use After Free (last year's #7, but known to account for around half the bugs in the Chrome browser) and 11. Missing Authorization, which rose from the #16 position.
Looking at the list, it's not exactly comforting to see old favourites are still with us after many, many years - including, in top position, Out-of-bounds Write, a.k.a. the Buffer Overflow and its various close relatives, which has been with us since at least the 1960's, if not before. Perhaps the adoption of memory-safe languages like Rust into development, including in the kernels of both Linux and Windows, will see this wizened old character handed a gold watch and pensioned off into retirement.
Likewise, the appearance of XSS and SQL Injection just below this (and Command Injection just a little lower) is more than a bit disturbing. Clearly, we need to do a better job of educating programmers, rather than checking them for a pulse and then turning them loose to copy-and-paste code fragments from StackOverflow. We should also be using static analysis a lot more - many of the entries in the Top 25 can easily be caught this way.
The CWE Top 25 Most Dangerous Software Weaknesses can be found at https://cwe.mitre.org/top25/. Essential reading for most developers (along with the various OWASP Top 10's), I'd say - and could be the basis of some profitable management discussions as well as some 'lunch-and-learn' sessions.
CISA, 2023 CWE Top 25 Most Dangerous Software Weaknesses, news alert, 29 June 2023. Available online at https://www.cisa.gov/news-events/alerts/2023/06/29/2023-cwe-top-25-most-dangerous-software-weaknesses.
All Is Not Well in CISSP-Land
Disturbing developments continue at the International Information Systems Security Certification Consortium (ISC)2 - the gatekeeper of the 'gold standard' certification for security pro's, the CISSP. Last year's board election saw over 80 candidates nominated to take part in the election - but a behind-closed-doors, undocumented 'selection process' run by the then-current board resulted in only six candates being put on the election slate to fill the six open positions. The result was an election in name only - it really didn't matter how the membership voted. And the bar for write-in candidates - of whom there were several - made it impossible for any of them to get the necessary votes for election.
A little later, the board proposed a number of changes to the Bylaws that would have further consolidated its powers and stifled the voices of the members. Unsurprisingly, these were voted down by the members, with veteran member Stephen Mencik working tirelessly to point out the problems and, eventually, proposing an alternative set of of amendments that seemed, to those members discussing them, to be a much better way forward.
Unsurprisingly, the board reacted very negatively to this, accusing Stephen of violating an NDA (he hadn't, as best we can determine) and making various other threats. Early this month, the board conducted a webinar - at an ungodly hour, as far as most of a global membership are concerned - to explain their response and their proposed way forward with a new vote on the Bylaws amendments.
I strongly urge all current CISSP's to read Stephen's blog commentary on this webinar, at https://smencik1.wordpress.com/2023/06/06/upcoming-by-laws-vote-info-and-recommendation/. There are several problems with their proposed voting process - not least of them that the member petition called for a vote on each of the proposed amendments individually, while the Bylaws Committee has set up a procedure whereby members must vote for either the petition's alternative bylaw amendments as a block, the board's proposals as a block, or neither of these.
In any case, voting opened on June 20th.
And closed a few hours later.
Members received an email which read, in part:
A vulnerability has been identified in our bylaws voting platform. We hold the integrity of our member voting paramount and have suspended voting until a secure environment is restored. No data were compromised.
We will provide updates when available. All members will have an opportunity to vote prior to the August 1, 2023, Special Meeting. To ensure the integrity of the results, all members will be asked to resubmit their vote.
Since then: silence. One has to wonder about a vulnerability in the voting platform of the organization that operates the self-proclaimed 'gold standard' in infosec.
Stephen has blogged about this also, at https://smencik1.wordpress.com/2023/06/26/by-laws-voting/, and I would urge reading it, as well as other entries at https://smencik1.wordpress.com/.
I cannot say I am entirely surprised at this snafu - your humble scribe has been encountering his own difficulties with the (ISC)2 web site. The end of June marks the time to pay my Annual Maintenance Fees (AMF) in order to continue to be a member in good standing (and thereby, of course, vote in Great Bylaws Controversy of 2022/23). So, earlier this week, I dutifully logged in to the site, entered my credit card details and submitted payment. In response, I was greeted with a payment confirmation page that had blank fields for payment date, receipt number, order summary, payment amount and balance. The promised emailed receipt did not turn up, either.
So I contacted their customer service, a.k.a. member support, to be told that no, payment had not gone through. So, late the following day, after checking my credit card history and seeing no transaction, I tried again - with the same result, a blank confirmation and no receipt.
The next morning - and I wish I could say I was surprised - the credit card account showed a transaction for the first (apparently unsuccessful) payment attempt. I advised member support only to be told that, no, the transaction had not gone through.
"Yet", I replied. "The operative word here is 'yet'" - with no response from member support. And sure enough, the second payment attempt was also successful, with the transaction turning up in my credit card account this morning. I wouldn't be surprised if a third turns up tomorrow.
But still, the "member dashboard" at (ISC)2 shows my AMF as still outstanding, on this last day of my membership year, despite my now having paid it twice.
I cannot but laugh at the declaration at the bottom of the broken (ISC)2 payment confirmation page:
"(ISC)² has been issued an attestation of compliance from a qualified security assessor (QSA) from the Payment Card Industry (PCI). Our payment operations are validated to follow best practices to increase controls around cardholder data to reduce credit card fraud."
I've been told by another CISSP that his AMF payment was initially blocked by his own bank as they saw (ISC)2's payment processing as too risky. I've now raised a dispute with my own bank for the duplicate payment; I imagine that won't do much for their reputation either.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
CISA & NSA Release Guidance on Defending CI/CD Pipelines
The US Cybersecurity & Infrastructure Security Agency, together with the NSA, has released an information sheet - of 23 pages - on defending the Continuous Integration / Continuous Delivery (CI/CD) environments that form an essential part of DevOps and DevSecOps.
CI/CD sits at the confluence of a number of factors: the switch to cloud environments, deployment of applications using containers and Platform-as-a-Service architectures, and the application of automation and orchestration throughout the software development lifecycle. It provides a largely straight path from the source code repository where developers check in their code, through the build, test and deployment phases right into production.
As threat actors find it harder and harder to compromise production systems, so they have shifted their attention to the earlier steps in the software supply chain, prefering to compromise source code repositories and the other steps in the CI/CD pipeline. After helpfully defining terms - not every security pro has a development background, unfortunately, and those who do often left the field before the advent of DevOps - the 'sheet' moves on to enumerating the threats (based on the OWASP Top 10 CI/CD Security Risks) and the relevant attack surfaces, including:
- Insecure code
- Poisoned pipeline execution
- Insufficient pipeline access controls
- Insecure system configuration
- Usage of third-party services
- Exposure of secrets
This is followed by three interesting scenarios, and then suggested mitigations to harden CI/CD environments, such as:
- Using recommened cryptography
- Minimize the use of long-term credentials
- Signing the CI/CD configuration and verifying it throughout the process
- Requiring a second programmer to review and approve code as part of the check-in process
- Implementing the principle of least privilege for CI/CD access
- Carefully securing secrets, tokens and keys, including ensuring none are left embedded in code
- Proactively patching and updating CI/CD tools and the underlying systems
- Implementing security scanning tools such as static and dynamic testing early in the C/CD process
- Restricting untrusted libraries and tools
- Quickly removing temporary resources such as VM's and Kubernetes clusters after use
- Implementing software bill of materials (SBOM) and software composition analysis (SCA)
- Architecting, building and testing for resiliency
An appendix maps the various CI/CD threats to the MITRE ATT&CK framework tactics as well as a the D3FEND countermeasures. The information sheet also provides many links to additional guidance documents. I'd say this information sheet is required reading for the many information assurance pros whose developers have been tardy in inviting them to the DevOps party. Time to replace that with DevSecOps!
NSA and CISA, Defending Continuous Integration/Continuous Delivery (CI/CD) Environments, cybersecurity information sheet, June 2023. Available online at https://www.cisa.gov/news-events/alerts/2023/06/28/cisa-and-nsa-release-joint-guidance-defending-continuous-integrationcontinuous-delivery-cicd and https://media.defense.gov/2023/Jun/28/2003249466/-1/-1/0/CSI_DEFENDING_CI_CD_ENVIRONMENTS.PDF.
Second Thoughts About AI?
The AI hype cycle is finally dying down, as more and more stories surface of embarrassing AI disasters such as the one that befell a lawyer who filed a ChatGPT-written document citing non-existent cases. Now, a new survey from Malwarebytes has revealed the initial enthusiasm for ChatGPT has faded, with 81% of respondents concerned about possible security and safety risks, 63% not trusting the information it produces and 51% wanting to see work on it paused while regulations catch up.
If you are familiar with Gartner's hype cycle, you probably agree: we've fallen from the Peak of Inflated Expectations to the Trough of Disillusionment.
As an AI enthusiast from the early 1970's (in the Department of Cybernetics at the University of Reading) I'd say that's unfortunate: the sins of commercial large language models (LLM's) should not be transferred to the many less ambitious and less spectacular applications of machine learning and AI that are making continuous incremental progress. In large part, the inflated expectations were inevitable as the public, who do not understand the internal operation of transformers and generative LLM's, poked and prodded at the beast and were amazed when it produced lucid and articulate responses. Surely something that speaks so fluidly - and at length, too! - must actually be intelligent!
Sorry - no.
When put to work on a bounded and high-quality corpus of traning material - for example, a database of legislation and regulations - such programs can do an excellent job of tasks such as summarization and abstraction as well as answering questions which demand only limited inference. I can see them being incredibly useful in GRC applications, for example, where they could spare analysts many hours of boring reading and searching to determine the consequences of various proposed actions.
Where ChatGPT and its ilk fall down is in two areas. Firstly, they train on the public world wide web (as it existed in 2021, in the case of GPT-3). And the web is notoriously full of misinformation, disinformation and outright malinformation. And secondly, being limited purely to statistical processing of words - knowing synonyms, how frequently words appear, how often they appear in various combinations, etc. - and not their meanings, LLM's can't tell fact from fiction, so happily treat the two the same way.
And when processing case law or academic papers, for example, the LLM's record things like the types of names that appear in case titles (some companies, some inviduals, etc.) and the styles of paper titles, author names and their related institutions, reference styles, etc.. When spinning words around to create output, they will quite happily pick relevant words and spin them into plausible-sounding cases and papers - a process referred to as AI hallucination.
This process is likely to get worse, as the use of generative LLM's by news aggregation sites, and especially disinformation sites, rapidly increases on the web. As other LLM's train on this data, so a feedback loop will develop in which AI trains on AI-generated text. Can you spell, garbage in, garbage out?
A recent paper by Shumailov et. al. (with Ross Anderson, of "Security Engineering fame, as one of the co-authors) addresses this very topic, finding that "model-generated content in training causes irreversible defects in the resulting models, where tails of the original content distribution disappear. We refer to this effect as Model Collapse and show that it can occur in Variational Autoencoders, Gaussian Mixture Models and LLMs. We build theoretical intuition behind the phenomenon and portray its ubiquity amongst all learned generative models".
In short, LLM's have their place, and as long as they stay in it and aren't unleashed to roam the world wide web, they are going to perform valuable work, including in security-related areas such as compliance assurance, software development (essentially a transformation problem from problem specification to executable code), automated malware analysis (explicating what machine code does and is likely intended to achieve), etc. But let's keep our expectations in check, mmmkay?
Shunailov, Ilia, The Curse of Recursion: Training on Generated Data Makes Models Forget, arXiv preprint, 31 May 2023. Available online at https://arxiv.org/abs/2305.17493v2.
Stockley, Mark, 81% concerned about ChatGPT security and safety risks, Malwarebytes survey shows, blog post, 27 June 2023. Available online at https://www.malwarebytes.com/blog/news/2023/06/chatgpt.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
New Process Injection Technique Can Bypass Detection by EDR Products
An increasingly common technique used by malware authors to evade detection is process injection. This replaces the code of an existing, trusted system process with malicious code, injected by the attacker. Because the code is executing within the context of a trusted process, it will be hard for security tools to detect it, and in some cases the technique allows completely file-less exploitation, leaving behind no artifacts on the victim's disk to be examined by malware analysts.
A new process injection technique developed by researchers at Israeli security firm Security Joes is able to evade detection by endpoint detection and response (EDR) applications. The new technique, which its developers call "Mockingjay", does not use Windows API calls such as VirtualAlloc(), VirtualAllocEx(), WriteProcessMemory() and others, which EDR applications typically hook as a means of detecting and blocking their use.
Instead, their new technique leverages a vulnerable dynamic link library - one which possesses a default Read/Write/Execute (RWX) memory section, which can then be abused to inject the desired code. Since the DLL already has RWX memory, this eliminates the need to make calls to memory allocation API's or NtWriteVirtualMemory() and NtProtectVirtualMemory(), which are also closely monitored by EDR software.
The researchers wrote a tool to search the entire Windows filesystem in search of such a DLL, and found one: msys-2.0.dll, which is part of Visual Studio 2022 Community Edition. This DLL has 16 KB of available RWX available - an ideal space for code injection and execution.
The next step was to find a method that could leverage this without making the monitored API calls. Their first approach is to load the vulnerable DLL directly and then find the RWX memory area, using the LoadLibraryW() and GetModuleInformation() system calls. In a proof-of-concept, this was then used to run code, based on the Hell's Gate technique, to create a system call stub and then jump directly into system API's in order to unhook the EDR hooks and allow further activity without observation.
A second approach is to perform process injection on a remote process, again relying on the RWX memory section in msys-2.0.dll. It turns out that this DLL is commonly used by applications that require POSIX emulation, such as GNU utilities, some of which are found in Visual Studio 2022 Community Edition. For their proof-of-concept, the researchers successfully injected code into the ssh.exe (Secure Shell) process, causing it to load yet another DLL which created a reverse shell to a remote machine. The only limitation of this technique is that targeted DLL (in this case msys-2.0.dll) cannot use Address Space Layout Randomization (ASLR) as this would require dyanmic resolution of the address of the RWX memory section.
The Security Joes blog article contains a detailed write-up which is effectively a well-written tutorial on process injection techniques. It also provides some recommendations on detection techniques.
Peixoto, Thiago, Felipe Duarte and Ido Naor, Process Mockingjay: Echoing RWX In Userland To Achieve Code Execution, blog post, 27 June 2023. Available online at https://www.securityjoes.com/post/process-mockingjay-echoing-rwx-in-userland-to-achieve-code-execution.
Europol Investigation Leads to 6,558 Arrests
Back in 2020, French and Dutch police forces were able to infiltrate the operations of EncroChat, an encrypted mobile messaging service that offered its users - mainly criminals - hardened Android phones with just the features they needed: strong encryption, rapid device erasure with a specific PIN or remote deletion by the EncroChat help desk and a tamper-proof boot process. Despite the high price of both the device and its subscription service, EncroChat sold like hot cakes, with tens of thousands of users world wide.
The Joint Investigation Team established by the French and Dutch authorities with assistance from Eurojust and Europol was able to intercept, share and analyse over 115 million criminal conversations, by over 60,000 users. Based on the accumulated statistics from the many countries who used the shared data over the next three years, the results are:
- 6,558 suspects arrested, including 197 High Value Targets
- 7,134 years of imprisonment of convicted criminals up to now
- €739.7 million in cash seized
- €154.1 million frozen in assets or bank accounts
- 30.5 million drug pills seized
- 103.5 tonnes of cocaine seized
- 163.4 tonnes of cannabis seized
- 3.3 tonnes of heroin seized
- 971 vehicles seized
- 271 estates or homes seized
- 923 weapons seized, as well as 21 750 rounds of ammunition and 68 explosives
- 83 boats and 40 planes seized
The investigation, conducted at Europol's headquarters under the name "Operational Task Force EMMA", also prevented violent attacks, attempted murders, large-scale drug importations and corruption. And while many of EncroChat's customers fled to another service called SkyECC, this was also penetrated and dismantled in 2021.
All in all, an impressive result.
Europol, Dismantling encrypted criminal EncroChat communications leads to over 6 500 arrests and close to EUR 900 million seized, news release, 27 June 2023. Available online at https://www.europol.europa.eu/media-press/newsroom/news/dismantling-encrypted-criminal-encrochat-communications-leads-to-over-6-500-arrests-and-close-to-eur-900-million-seized.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
Chinese APT Targets Critical Infrastructure, OT
Researchers at managed security provider Crowdstrike have released on an incident involving a Chinese-nexus threat actor which they track as VANGUARD PANDA (also known as Volt Typhoon). The cyber-espionage group consistently targets Zoho ManageEngine ADSelfService Plus in order to obtain initial access, after which they deploy webshells and make use of living-off-the-land techniques to avoid leaving behind detectable artifacts which could be used as IOC's.
In this particular incident, Crowdstrike's Falcon Complete managed-detection-and-response was triggered by suspicious reconnaissance commands - such as listing processes, testing network connectivity, gathering user and group information, and using WMI to enumerate domain trust and DNS zones - executed under an Apache Tomcat web application server running ManageEngine ADSelfService Plus. The use of these commands indicated a familiarity with the target environment, as the commands were executed rapidly and used specific internal hostnames and passwords:
cmd /C "tasklist /svc"
cmd /C "ping -n 1 [redacted]"
cmd /C "ping -n 1 -a [redacted]"
cmd /C "net group "domain controllers" /dom"
cmd /C "net use \\[redacted]\admin$ REDACTED /u:[redacted]"
cmd /C "dir \\[redacted]\c$\Users"
cmd /C "wmic /node:[redacted] /user:[redacted] /password:"<removed>" process call create "cmd /c nltest /DOMAIN_TRUSTS >>C:\Users\[redacted]\AppData\Local\[redacted].tmp""
cmd /C "dir \\[redacted]\c$\users\[redacted]\AppData\Local\Temp\[redacted].tmp"
cmd /C "type \\[redacted]\c$\users\[redacted]\AppData\Local\Temp\[redacted].tmp"
cmd /C "wmic /node:[redacted] /user:[redacted] /password:"<removed>" process call create "cmd /c Dnscmd . /EnumZones >>C:\Users\[redacted]\AppData\Local\Temp\[redacted].tmp""
cmd /C "dir \\[redacted]\c$\users\[redacted]\AppData\Local\Temp\[redacted].tmp"
cmd /C "type \\[redacted]\c$\users\[redacted]\AppData\Local\Temp\[redacted].tmp"
At this point the Crowdstrike team quickly quarantined and triaged the host, notifying the impacted customer while analysing the Apache Tomcat access logs. This revealed multiple POST requests to the file /html/promotion/selfsdp.jspx which, upon analysis, turned out to be a webshell capable of running arbitrary commands by using the /C option of the classic Windows shell, cmd.exe and the ProcessBuilder class. It also attempted to masquerade as part of ManageEngine ADSelfService Plus, using that as its page title and adding legitimate links to help desk software. In fact, selfsdp.jspx will match the EncryptJSP YARA rule provided in a May CISA advisory on Volt Typhoon.
However, a lot of red flags remained: for example, the use of hostnames above indicated a lot of prior reconnaisance and enumeration and the inclusion of passwords indicated that admin accounts had already been compromised - likely before the Falcon Complete sensor had been installed. In fact, the selfsdp.jspx webshell had been written to disk almost six months before the Falcon sensor was installed, and examination of the Apache Tomcat logs correlated its installation with an HTTP POST request to /html/error.jsp - but that file no longer existed, indicating its deletion in an attempt to evade detection and analysis. A lot of related log entries had also vanished - on one day, the entire first 12 hours of the access log had gone.
To cut a long story short - Crowdstrike's blog article provides the full details - the threat actor eventually slipped up. .jsp and .jspx pages - Java Server Pages - contain scriptlets of Java code which are extracted to create .java Java source code files and then compiled into the corresponding .class bytecode files for execution. This is done by a component of Apache Tomcat - the Jasper 2 JSP engine - which places the .java and .class files in a separate directory structure, and while the intruder cleaned up the log files and other artifacts, they missed these.
One of them, ListName_jsp.java, in turn deployed a backdoored version of the tomcat-websocket.jar Apache Tomcat library incorporating a webshell. This was then timestamped to match the timestamp on the original tomcat-websocket.jar file so that it would appear not to have been replaced (although obviously a filesystem verification program would detect its changed digest value).
The Crowdstrike blog article makes fascinating reading and includes some recommendations for detection and mitigation of this attack, which is just one of many the firm has seen against US-based critical infrastructure.
CISA, People's Republic of China State-Sponsored Cyber Actor Living off the Land to Evade Detection, cybersecurity advisory AA23-144a, 24 May 2023. Available online at https://www.cisa.gov/news-events/cybersecurity-advisories/aa23-144a.
Falcon Complete Team, Business as Usual: Falcon Complete MDR Thwarts Novel VANGUARD PANDA (Volt Typhoon) Tradecraft, blog post, 22 June 2023. Available online at https://www.crowdstrike.com/blog/falcon-complete-thwarts-vanguard-panda-tradecraft/.
Cozy Bear At It Again
In a series of tweets, Microsoft Threat Intelligence has reported a rise in credential attack activity by the Russian state-sponsored APT29, a.k.a. Cozy Bear and NOBELIUM, which the Redmondites track as Midnight Blizzard (I wish they would stick to bears and pandas - it makes life a lot easier!). The attacks target governments, IT service providers, NGO's, defense contractors and critical manufacturing, using a variety of password spray, brute force and token theft techniques, as well as session replay attacks using stolen session credentials likely acquired via illicit sale in dark web markets or Telegram channels.
In this campaign the threat actor is using residential proxy services to hide the real source of their attacks. Residential proxies are a low-cost or free proxies provided by a variety of service providers - I have even seen home users being invited to install proxy servers under the pretext that it will get them additional bandwidth (it won't) or in return for a small income. The problem is that the main purpose of such proxies is to disguise the source of online activities for a variety of dodgy or disreputable activities (which means that home users who naively install them are likely to see their IP addresses blacklisted), although they do have a few legitimate uses, especially in states which restrict their citizens' access to information.
APT29's use of residential proxies for a brief period before moving on also makes it harder for defenders to distinguish these attacks from legitimate traffic and block them.
Microsoft Threat Intelligence, "Microsoft has detected increased credential attack activity...", Twitter thread, 22 June 2023. Available online at https://twitter.com/MsftSecIntel/status/1671579358031486991.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
GIFShell Attack Exploits Teams; Exfiltrates Data Through MS Servers
A new exfiltration technique allows attackers who compromise Microsoft Teams users to exfiltrate data through Microsoft's own servers, making the exfiltration hard to spot by endpoint security products and firewalls, since it looks like legitimate Teams traffic.
The technique, named GIFShell, uses a reverse shell that delivers malicious commands via base64 encoded GIF files in Teams, and exfiltrates the output, also as GIF's, via the Teams infrastructure. The attacker must first somehow convince a user to install a malicious backdoor that executes commands and uploads the results via a GIF URL to a Teams webhook. The backdoor scans the Teams logs for messages with a GIF, extracts the base64 encoded commands and executes them, converting the output to base64 text which is used as the filename for a remote GIF embedded in a Microsoft Teams Survey card that is submitted to the attacker's public webhook.
Microsoft has acknowledged the GIFShell attack, but will not issue a fix, stating that no security boundaries were bypassed, this being a post-exploitation technique.
Johnson, Mic, Understanding the Microsoft Teams Vulnerability: The GIFShell Attack, Latest Hacker News, 20 June 2023. Available online at https://latesthackingnews.com/2023/06/20/understanding-the-microsoft-teams-vulnerability-the-gifshell-attack/.
Verizon 2023 DBIR Available
From the "Dammit - we meant to post this weeks ago" department: Verizon's annual Data Breach Investigations Report is always an interesting read, and we go hunting for it every April/May, when it usually appears. This year's appeared a few weeks ago and is, as usual, very informative. Some interesting factoids:
- 83% of breaches involved external actors, with the majority of attacks financially-motivated, while 19% involved internal actors (sometimes unintentionally though misuse or human error)
- 24% of all breaches involved ransomware; it was used in 62% of incidents committed by organized crime and 59% of financially-motivated incidents
- 50% of all social engineering incidents used pretexting - scenrios invented to trick the victim into giving up information or doing something to enable a breach
- 74% of breaches involve human facors: errors, privilege misuse, theft of credentials or social engineering
- 95% of breaches are financially motivated
It certainly seems like we could obtain high returns from increased efforts in the human factors (education, training and awareness) aspects of our business.
Uncredited, 2023 Data Breach Investigations Report, Verizon, 2023. Available online at https://www.verizon.com/business/en-au/resources/reports/dbir/.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
NSA Issues Guidance on BlackLotus
The National Security Agency has issued a mitigation guide for the BlackLotus bootkit. We reported on BlackLotus back in March, following an initial report from ESET, although the malware had been available since at least October 2022. It works by exploiting CVE-2022-21894, a vulnerability which was fixed by Microsoft in their January 2022 updates. However, the affected binaries were not added to the UEFI Secure Boot Deny List Database (DBX), and BlackLotus works by carrying its own copies of those older binaries - a technique referred to as "Baton Drop"
The NSA guide recommends a number of actions:
- Update recovery media and activate optional mitigations
- Harden defensive policies
- Monitor device integrity measurements and boot configuration
- Customize UEFI Secure Boot
It is important to bear in mind that BlackLotus is not a firmware implant, but a bypass of the secure boot process, and it can be removed or quarantined. Currently, it is only known to affect Windows 10 and 11;, but fixes are also available for Windows 8.1. Although BlackLotus does contain some Linux boot binaries, Linux is not one of its targets. Linux admins can defend their systems by removing the Microsoft Windows Production CA 2011 certificate from Secure Boot's DB.
National Security Agency, BlackLotus Mitigation Guide, cybersecurity information, ver 1.0, June 2023. Available online at https://media.defense.gov/2023/Jun/22/2003245723/-1/-1/0/CSI_BlackLotus_Mitigation_Guide.PDF.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
Apple Issues Urgent Patches for 0days
Apple has issued urgent patches for two vulnerabilities in the iOS and iPadOS mobile device operating systems, in response to claims the vulnerabilities are being exploited in the wild.
The vulnerabilities are
- CVE-2023-32434: Integer overflow in the kernel due to inadequate input violation
- CVE-2023-32439: Type confusion in Webkit
The vulnerabilities were used by an implant, discovered by Kaspersky Researchers and claimed to be part of a campaign which they have named Operation Triangulation. CVE-2-23-32434 is used during initial exploitation, in order to gain root privileges before deploying the implant in memory - as a result, the implant cannot survive a reboot, and the attackers have to install it again by sending an iMessage with a malicious attachment. If the device is not rebooted, the implant normally removes itself after 30 days, although this can be extended.
Once running, the implant communicates with its C2 server via a RESTful HTTPS API, implemented with the Protobuf library. All traffic takes the form of key-value pairs, encrypted with either 3DES or RSA. The implant sends heartbeat messages, while the C2 server sends any of 24 commands for
- Interacting with the filesystem (creation, modification, exfiltration and removal of files)
- Interacting with processes (listing and terminating them)
- Dumping the victim’s keychain items, which can be useful for harvesting victim credentials
- Monitoring the victim’s geolocation
- Running additional modules, which are Mach-O executables loaded by the implant. These executables are reflectively loaded, with their binaries stored only in memory
The implant is written in Objective-C, which leaves some debugging information, such as the names of class members and methods, in the generated binary. Curiously, many of the resources accessed and operations performed by the implant are given database-related names - for example, a directory is referred to as a table, while a file is called a record, and the C2 server is a DB server - which led the Kaspersky researchers to name the implant TriangleDB.
Kucherin, Georgy, Leonid Bezvershenko and Igor Kuznetsov, Dissecting TriangleDB, a Triangulation spyware implant, blog post, 21 June 2023. Available online at https://securelist.com/triangledb-triangulation-implant/110050/.
Useful Ransomware Educational Resources
With ransomware being seen by the business community as one of the biggest, if not the biggest, current security threat, it is important to keep ourselves and our business principals well-informed about its evolution. A couple of useful resources have appeared in the last couple of days to assist with this.
First, Sophos has started to release a three-part documentary series entitled "Think You Know Ransomware?", compiled from over 100 hours of interviews with cybercriminals, security experts, industry analysts and policy makers. The first episode, "Origins of Cybercrime" is now available, with episodes 2 and 3 due for release over the next two weeks.
Meanwhile, at the Infosecurity Europe conference, Richard de la Torre, marketing manager at Bitdefender, gave a talk on the myths and misconceptions which surround ransomware. In his talk he describes how proactive defenders are making use of threat intelligence to prevent or disrupt attacks, as well as increasingly using decryptors to recover data. However, as de la Torre points out, ransomware operators are now putting much more effort into information exfiltration, taking time to stealthily move throughout the victim's networks, identifying the most valuable datasets as well as discovering whether they have cyber insurance.
Sophos, Think You Know Ransomware?, documentary series, June 2023. Available online at https://www.sophos.com/en-us/content/ransomware-documentary.
Raywood, Dan, Ransomware Misconceptions Abound, To the Benefit of Attackers, Dark Reading, 22 June 2023. Available online at https://www.darkreading.com/vulnerabilities-threats/ransomware-misconceptions-abound-to-the-benefit-of-attackers.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.