Les Bell and Associates Pty Ltd
Site blog
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
BlackCat Deploying New Signed Kernel Driver
One of the primary defences against the introduction of malware into systems, especially into the operating system itself, is the checking of digital signatures on installable software such as drivers. However, this defence is steadily weakening as malicious actors abuse Microsoft signing portals, use leaked and stolen certificates or make use of underground services to obtain valid code-signing certificates or Extended Validation certificates that are tied to real identities.
Now Trend Micro reveals details of a February 2023 attack by the BlackCat ransomware group in which they first attempted to deploy a Microsoft-signed driver which had previously been detected by Mandiant and was easily detected. Having failed with this approach, they switched to signing a new driver called ktgn.sys using cross-signing certificates which had been issued by Thawte to BopSoft and by VeriSign to YI ZENG. This allows the driver to be loaded on Windows systems, even when code signing policies are enforced.
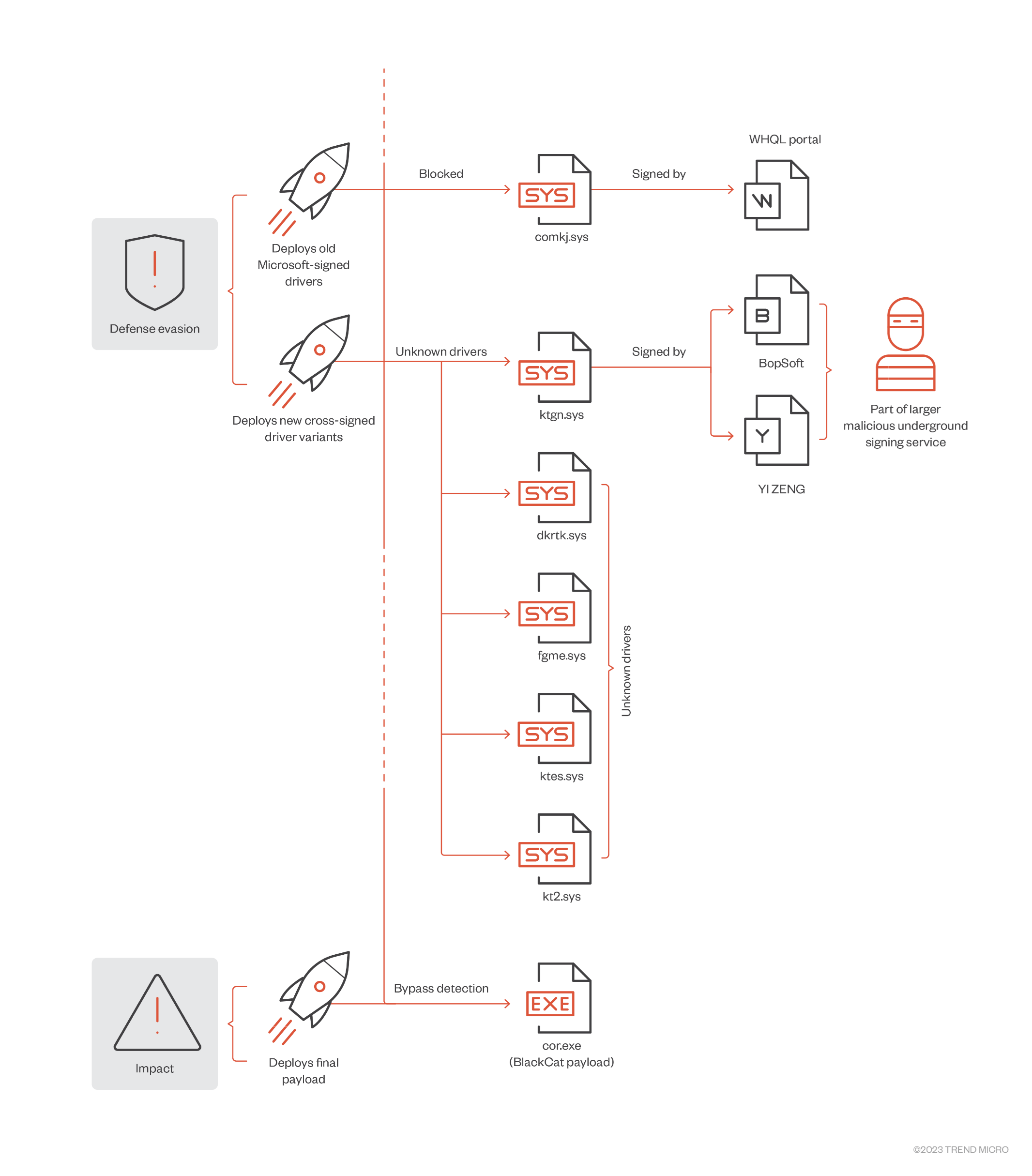
The files dropped by a BlackCat affiliate in the defence evasion phase. (Trend Micro)
The driver was dropped into the user temp directory by a VM-protected user agent, tjr.exe, which then installs the driver with start value = System, so that it will load when the system reboots. The code of the driver is obfuscated but its purpose is to use the IOCTL KillProcess call to kill security-related agent processes and evade detection. Furthermore, it does not register an unload callback process, so it can only be removed by deleting its registry key and rebooting.
The two issuers involved have both now revoked the certificates, but we can expect this technique to be used increasingly by threat actors. The Trend Micro report provides additional detail and recommended mitigation techniques.
Zohdy, Mahmoud, et. al., BlackCat Ransomware Deploys New Signed Kernel Driver, research report, 22 May 2023. Available online at https://www.trendmicro.com/en_us/research/23/e/blackcat-ransomware-deploys-new-signed-kernel-driver.html.
Possible Iranian Threat Actor Targets Saudi Arabia, Middle Eastern States
Still on the topic of kernel driver exploits, Fortinet reports on a campaign which utilises an interesting injection technique via a Windows kernel driver called WinTapix.sys. This driver essentially functions as a loader, making use of a position independent shellcode project called Donut, which can inject .NET assemblies, PE files and other Windows payloads into suitable processes and execute them, passing in any required parameters.
As in the case above, the WinTapix.sys driver is partially protected by virtualization to prevent reverse engineering, but Fortinet's analysts were able to work out the injection process as well as the resultant backdoor, encryption and proxy functionalities the tool provides. Their report provides a comprehensive analysis, IOC's, a mapping to the MITRE ATT&CK matrix and a rather nice graph of the attack flow.
Revay, Geri and Hossein Jazi, WINTAPIX: A New Kernel Driver Targeting Countries in The Middle East, blog post, 22 May 2023. Available online at https://www.fortinet.com/blog/threat-research/wintapix-kernal-driver-middle-east-countries.
Google Wants Higher-Quality Bug Bounty Submissions; Will Pay More
Google has announced a new quality rating system for security vulnerability reports, in an attempt to encourage more research in the higher-impact areas of its Android and Google Device products. The new system will rate vulnerability reports as High, Medium or Low quality based on the level of detail in the submission. The key elements desired are:
- Accurate and detailed description, identifying the product and with enough detail to allow maintainers to understand the issue and get to work on a fix
- Root cause analysis, describing why the issue occurs and what source code needs to be fixed
- Proof-of-concept, demonstrating the vulnerability
- Reproducibility, in the form of a step-by-step procedure which reproduces the vulnerability on an up-to-date device
- Evidence of reachability, demonstrating the type of issue and the level of access or execution obtained
Security researchers may well feel as though they have had their homework submission returned with a lower mark than they were expecting - but Google is now offering bug bounties of up to $15,000 through this program, which should ease the sting a little.
Jacobus, Sarah, New Android & Google Device Vulnerability Reward Program Initiatives, blog post, 17 May 2023. Available online at https://security.googleblog.com/2023/05/new-android-google-device-VRP.html.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
ASX Gives Up On Blockchain
In a final blow to that perennial solution in search of a problem, blockchain technology, the Australian Stock Exchange has announced that it has completely abandoned all attempts to replace its aging CHESS (Clearing House Electronic Subregister System) settlement system with the once-charismatic 'solution'. In November last year, we reported that the ASX had halted the project following an independent review, taking a $A250 million loss in the process.
Now the exchange has stated that it is considering its options to replace CHSS, but that any attempt will not involve blockchain or distributed ledger technology. At a meeting with participants, project director said that, "while we continue to explore all the options, certainly we will need to use a more conventional technology than in the original solution in order to achieve the business outcomes".
New York blockchain tech form Digital Asset had hoped that the project would be resurrected, but those hopes are now dashed.
Kaye, Byron, Australian stock exchange says software overhaul won't involve blockchain, Reuters, 19 May 2023. Available online at https://www.reuters.com/markets/australian-stock-exchange-says-software-overhaul-wont-involve-blockchain-2023-05-19/.
Low Earth Orbit Satellites Vulnerable to Jamming
Few realise the extent to which our lives have been changed by low earth orbit satellites. One obvious example is the disappearance of maps, atlases and street directories for driving; almost everyone has switched to GPS-based navigation systems, which utilise signals from a constellation of satellites continually orbiting the earth.
A more recent innovation is the provision of Internet access via SpaceX's Starlink network of low earth orbit satellites, which have proven popular with RV'ers and users in remote areas, as well as institutions - such as our local council - which are signing up in order to have a backup service in case of outages in terrestrial services.
However, in a world of international tensions, these satellite services are highly vulnerable to attack. Unlike the higher-orbit geostationary satellites, which remain over a fixed position on the earth's surface, low earth orbit communications satellites appear over the horizon, zoom (roughly) overhead and disappear again, meaning that they must frequently hand over their ground station connections to the next satellite of the constellation. This handover introduces delays and opens up more more surface for interference, according to Mark Manulis, professor of privacy and applied cryptography at the Universite of the Federal Armed Forces Cyber Defense Research Institued in Munich.
We have previously seen jamming and spoofing of GPS satellites, affecting shipping in the Black Sea and airliners around the Kaliningrad region, Eastern Finland, the Black Sea and the Eastern Mediterranean area, prior to, but especially since the beginning of, the Russian invasion of Ukraine. While the Starlink satellites transmit at higher power levels, mking them harder to jam than GPS, Elon Musk has already claimed that SpaceX has seen attempts to jam the system. In addition, Russia's defence agencies commissioned a system called Tobol which is intended to counter attempted jamming of their own satellites - indicating that they have already done considerable work in this area.
A report in IEEE Spectrum claims that commercial satellites are nowhere near the level of security found in military satellites, and considerable work is now in progress to remediate this situation.
Laursen, Lucas, Satellite Signal Jamming Reaches New Lows: Starlink and other LEO constellations face a new set of security risks, IEEE Spectrum, 18 May 2023. Available online at https://spectrum.ieee.org/satellite-jamming.
Understanding Hackers Vital, Says Lawyer
A new book from the founding director of Yale University's Cybersecurity Lab, lawyer Scott Shapiro, makes the case that we can only effectively tackle cybercrime if we understand not only how people hack, but why. In "Fancy Bear Goes Phishing", Shapiro examines several case studies such as the hacking of Paris Hilton's T-Mobile Sidekick and the infamous Morris Worm, to extract some important lessons.
In an interview in New Scientist, he explains why he has made available a free online hacking course, and talks about the futility of purely technical defences.
Adam, David, Knowing how to hack will be vital in a cybercrime-filled future, New Scientist, 16 May 2023. Available online at https://www.newscientist.com/article/mg25834390-100-knowing-how-to-hack-will-be-vital-in-a-cybercrime-filled-future/.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
Vuln Exposes KeePass Master Password; PoC Available
A vulnerability in the dialog used by password safe program KeePass to accept the user's master password and decrypt its database allows an attacker to extract that master password. The vulnerability (CVE-2023-32784) allows an attacker to reconstruct the master password from a process memory dump from KeePass version 2 on Windows (version 1.x is unaffected).
Given the difficulty of obtaining that dump remotely, the vulnerability is probably not that severe; if the system is already infected, however, there is a possibility that the intruder could obtain passwords for other systems, sites and applications.
The flaw is in SecureTextBoxEx, a Windows.Forms.TextBox control used to enter passwords. Said its discoverer, vdohney,
"The flaw exploited here is that for every character typed, a leftover string is created in memory. Because of how .NET works, it is nearly impossible to get rid of it once it gets created. For example, when "Password" is typed, it will result in these leftover strings: •a, ••s, •••s, ••••w, •••••o, ••••••r, •••••••d."
vdohney has also created a proof-of-concept which searches the dump for these patterns and offers a likely password character for each position in the password.
The good news is that the KeePass developers have already worked out a fix, which will be in KeePass version 2.54 and should be available in early June. Meanwhile, a workaround is that the PoC does not work if the password is copied and pasted into the form via the clipboard.
Dammit - only yesterday I was recommending KeePass to an audience, and now this happens! 😞
vdohney, Security - Dumping Master Password from Memory, Even When Locked, discussion thread, 1 May 2023. Available at https://sourceforge.net/p/keepass/discussion/329220/thread/f3438e6283/#0829.
vdohney, KeePass 2.X Master Password Dumper (CVE-2023-32784), GitHub project, 5 May 2023. Available online at https://github.com/vdohney/keepass-password-dumper.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
TP-Link Routers Targeted by Chinese APT
Checkpoint researchers have revealed a campaign, aimed at European foreign affairs entities, which they have linked to a Chinese state-sponsored APT they refer to as Camaro Dragon, and which has similar TTP's to a previously-identified APT named Mustang Panda.
The campaign utilises malicious firmware implants for TP-Link routers. The implants have several malicious components including a custom backdoor named Horse Shell which provides the attackers with persistent access and enables lateral movement into compromised networks. This technique, of compromising Internet-facing network devices and modifying their software or firmware, is a long-standing favourite of Chinese APT's.
The Checkpoint article provides an analysis of the Horse Shell backdoor, which is a MIPS32 ELF implant, written in C++. Its main capabilities are:
- A remote shell which allows execution of arbitrary shell commands on the infected device
- File transfer to and from the infected device
- A SOCKS proxy, allowing relay of communication between infected devices
The shell is firmware-agnostic, and can be integrated into the firmware of devices from different vendors, although the exploit which is used for initial access is not yet clear.
Cohen, Itay, Radoslaw Madej, et. al., The Dragon Who Sold His Camaro: Analyzing Custom Router Implant, technical report, 16 May 2023. Available online at https://research.checkpoint.com/2023/the-dragon-who-sold-his-camaro-analyzing-custom-router-implant/.
Four RCE Vulns in Cisco Small Business Series Switches
Cisco has released an advisory warning of four critical RCE vulnerabilities in the web-based user interface of products in their Small Business Series switches. The vulnerabilities are:
- CVE-2023-20159 (CVSS score 9.8): A stack buffer overflow
- CVE-2023-20160 (CVSS score: 9.8): An unauthenticated BSS buffer overflow
- CVE-2023-20161 (CVSS score: 9.8): An unauthenticated stack buffer overflow
- CVE-2023-20024 (CVSS score: 8.6): An unauthenticated heap buffer overflow
The following products are affected:
- 250 Series Smart Switches
- 350 Series Managed Switches
- 350X Series Stackable Managed Switches
- 550X Series Stackable Managed Switches
- Business 250 Series Smart Switches
- Business 350 Series Managed Switches
- Small Business 200 Series Smart Switches
- Small Business 300 Series Managed Switches
- Small Business 500 Series Stackable Managed Switches
The 220 Series and Business 220 Series smart switches are not affected.
Cisco has released free software updates which fix these vulnerabilities, and Cisco customers are advised to update as soon as possible.
Cisco, Cisco Small Business Series Switches Buffer Overflow Vulnerabilities, security advisory, 17 May 2023. Available online at https://sec.cloudapps.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-sg-web-multi-S9g4Nkgv.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
Who Should Attempt the CISSP Exam?
I'm often asked who the CISSP certification is aimed at; my university students typically ask whether they should attempt the certification before or while in their first job, for example (almost certainly not, for the undergraduates - they usually could not meet the experience requirements, while some of the Masters students could).
Primarily, the CISSP is for those who are moving upwards from a technical background in one or a few of the CBK Domains (e.g. network security, security architecture, etc.) into a management or supervisory position where they will need to:
- utilise a broad understanding of the other domains, to which they may already have had some exposure
- supervise technical professionals across all or most domains
- understand how *all* aspects of security need to be covered in balance, and
- communicate - in *both* directions - with senior management, that is, not just advise management.
The last point is probably the key one. Communication to management will mainly involve translating technical assessments of threats, vulnerabilities, etc. into business risk which management can relate to their existing understanding of risk, and this is a key reason why cybersecurity risk assessment processes and risk matrices, etc. should be aligned with the existing risk management processes across the rest of the enterprise.
But it also works the other way: translating senior management business concerns and requirements into technical security requirements. Once managers understand the risks posed to the assets they own, in part due to the business processes they rely upon, it is up to them to decide the level of risk they will accept. This is a business decision, and not one that security professionals are equipped to make.
Although some of this operates at the level of C-suite and board concerns with governance and policy, some of it involves other managers' specific concerns with opportunities presented by new technologies (cloud, apps, machine learning, related privacy issues), etc. as well as managing risks associated with specific business processes or information assets as they change.
In any case, I have found a security governance and management course is of benefit to students and practitioners who are still in the early stages of their career. Many tend to focus tightly on their particular interests or immediate job concerns - typically penetration testing, which is always an attractive aspect of cybersecurity for novices (something I don't understand - long hours, lots of reverse engineering and disassembling code, keeping on top of the latest vulnerabilities and exploits; I'd burn out).
However, a governance and management course helps them put it all in perspective and realise a) that their particular role is far from the only one needed in any large enterprise, let alone the most important one, and b) how their role fits in and the factors which influence the demand for their services. It certainly rounds them out as a professional.
For undergraduate students in cybersecurity, governance, risk and management is sometimes offered as a third-year subject; it's usually found in Masters programs. But for those already in the workforce, or who have not completed a specialist cybersecurity degree, tackling the CISSP - whether by self-study or a course - is probably the best way to get a comprehensive overview of the other areas of the field, how they all fit together, and how they are managed.
All this leads me to conclude that, right now, the CISSP is not of value just to the CISO level, especially in larger enterprises.
A Look Inside the Bulgarian 'Virus Factory'
A fascinating read in The Guardian last week provides an insight into the minds of competitive young virus authors in Bulgaria in the 1980's. These were the heady days of virus development, where curiosity was the driving force, in a search for new techniques to infect the MS-DOS systems of the era. It was a kinder, gentler time, when the massive profits provided by ransomware had not yet become a factor.
Shapiro, Scott J, On the trail of the Dark Avenger: the most dangerous virus writer in the world, The Guardian, 9 May 2023. Available online at https://www.theguardian.com/news/2023/may/09/on-the-trail-of-the-dark-avenger-the-most-dangerous-virus-writer-in-the-world.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
Lithium-Ion Battery Fires Increasingly Common
A CBS News report points to the rising incidence of fires caused by lithium-ion batteries, particularly in dangerous environments such as on board passenger aircraft. According to the CBS News investigation, the FAA verifies that the number of lithium-ion battery fires has jumped by over 42% in the last five years, and since 2021 there has been at least one such incident on a passenger plane somewhere in the US, on average, every week.
However, the article points to a common source of confusion - it is lax in making the important distinction between lithium batteries and lithium-ion batteries - the two terms are used apparently interchangeably in the article. The CISSP examination tests the candidate on physical and environmental security, including fire detection and suppression, and while I cannot say whether the exam question bank has any questions on this particular topic, the increasing prevalence of mobile devices which contain these batteries surely mean that it can only be a matter of time. So here's some key information from the Fire Detection and Suppression page of our CISSP Fast Track Review course wiki.
The first key point is to distinguish between the two types of battery:
- Lithium batteries are long-life, non-rechargeable batteries commonly used in wireless burglar alarm sensors, smoke detectors (usually in AA and AAA cell sizes), and in cameras, some remote controls and key fobs (usually in button-cell sizes such as CR-2032).
- Lithium-ion batteries are rechargeable batteries, commonly used in a variety of sizes and form factors, in mobile phones, tablets, laptops, Bluetooth earbuds and headphones, vapes and many other devices.
Let's dispose of (if you'll pardon the expression) the lithium batteries first. The first, and key, point is that lithium batteries are not rechargable and any attempt to recharge them may well start a fire. They will also overheat and may catch fire if short-circuited, or if exposed to water. In fact, lithium (like potassium) is a combustible metal that burns when exposed to air or even water - readers may remember high-school chemistry demonstrations in which a small pellet of potassium fizzes and burns when dropped into water - it is commonly stored in a jar of mineral oil as a safeguard, as is refined lithium metal.
Obviously, water therefore cannot be used as a suppressant for a lithium battery fire - in fact, adding water will result in a bigger fire - and so a large lithium battery fire should be tackled with a Type D (combustible metals) extinguisher. Unfortunately, these are not commonly found in office environments (yet?).
By contrast, a lithium-ion battery fire should be suppressed using a conventional ABC dry-powder extinguisher, although it may not be fully extinguished if thermal runaway continues. If one is available, a fire containment bag can also be used. Immersion in water may also be used - the battery may continue to burn, but the heat will be conducted away and the fire contained. In fact, it is not lithium that is the problem - it is the flammable electrolyte solution in the battery. Where the volume of Li-Ion batteries justify it - e.g. large quantities of Li-Ion batteries are stored in a warehouse - then a specialized F-500 Li-Ion Fire Extinguisher may be installed.
There are several causes of Li-Ion batteries fires. The first is mechanical damage to the battery - i.e. it is bent and broken, for example by being caught in the electrically-driven adjustment mechanisms of an aircraft seat. This is why airline staff warn passengers to ask for help in retrieving phones which have been lost in aircraft seats.
The second cause is a short-circuit, possibly caused by equipment failure, and the fix is to remove the battery from the device before thermal runaway starts. The third cause is overheating - this can be caused by laptop fan failure, an internal dust buildup or operating a laptop on a surface which blocks airflow. For phones, it can be as simple as using navigation functions, which continuously illuminate the screen, while the phone is in direct sunlight on top of a car dashboard.
The final cause is overcharging. Unlike the earlier nickel-cadmium (Ni-Cd) batteries, Li-Ion batteries are very sensitive to overcharging and require the correct charging circuit, which must provide overcharge protection. In general, laptop and cellphone or tablet batteries always contain a charging control circuit which deals with this, but small AA-size Li-Ion cells do not, and nor do some low-cost consumer devices and toys. These, in particular, should never be left to charge unattended, nor in a place where fire could rapidly take hold and spread, e.g. on top of soft furnishings or beneath fabric curtains.
Chase, The Best Fire Extinguisher for Lithium-Ion Batteries - 2022, Firefighter Inside, 2022. Available online at https://firefighterinsider.com/the-best-fire-extinguisher-for-lithium-ion-batteries/.
Martin, Neil, Seven things you need to know about lithium-ion battery safety, UNSW news release, 20 March 2023. Available online at https://newsroom.unsw.edu.au/news/science-tech/seven-things-you-need-know-about-lithium-ion-battery-safety.
Stock, Stephen, Amy Corral, Jose Sanchez and Dilcia Mercedes, Rising number of lithium battery incidents on airplanes worry pilots, flight attendants, CBS News, 8 May 2023. Available online at https://www.cbsnews.com/news/hazardous-materials-airplanes/.These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
Insider Gets Six Years for Extortion Attempt
Developers and especially ecurity professionals are among the most highly privileged insiders in most enterprises, with both high levels of access to many, if not all, systems - including logging and monitoring systems, in the case of secrity pros - plus the skills to both use and abuse them. It makes sense, therefore, to monitor their actions, taking a close look at their activities from time to time, rather than simply assuming they are trustworthy. Because sometimes, it turns out, they aren't.
A case in point is that of Nickolas Sharp, who we reported on back in February. Sharp misused his admin privileges to access his employer's AWS and GitHub accounts, stealing gigabytes of confidential data. To cover his tracks, he changed the log retention policies, altered other files and used a Surfshark VPN service in a failed attempt to conceal his IP address.
Worse, once the breach was discovered, Sharp sent the company an extortion demand for BTC50 and when they refused to pay, he leaked some of the data. However, by now the FBI had raided his home, confiscated his laptop and amassed a lot of evidence but - determined to prove the truth of the old adage that when you're in a hole you should stop digging, Sharp then went on a PR campaign, posing as a whistleblower and causing his employer's stock price to fall by 20% - that's more than a $US4 billion drop in market capitalization.
Sharp eventually pleaded guilty back in February, and his sentence has now been handed down.
U.S. Attorney Damian Williams said: “Nickolas Sharp was paid close to a quarter million dollars a year to help keep his employer safe. He abused that trust by stealing a massive amount of sensitive data, attempting to implicate innocent employees in his attack, extorting his employer for ransom, obstructing law enforcement, and spreading false news stories that harmed the company and anyone who invested into the company. Sharp now faces serious penalties for his callous crimes.”
US District Judge Katherine Polk Failla agreed, handing down a sentence of six years imprisonment, plus three years of supervised release. She also ordered Sharp to pay restitution of $US1,590,487 and to forfeit personal property used, or intended to be used, in connection with these offences. I don't think Sharp's pay in the prison laundry will allow his employer (coyly referred to as "Company-1" in the press release, but we all know who they are . . .) to ever see that $US1.5 million, though.
Biase, Nicholas, Former Employee Of Technology Company Sentenced To Six Years In Prison For Stealing Confidential Data And Extorting Company For Ransom, press release, 10 May 2023. Available online at https://www.justice.gov/usao-sdny/pr/former-employee-technology-company-sentenced-six-years-prison-stealing-confidential.
CISA Issues Papercut Advisory
Last month we brought you news of two critical vulnerabilities, discovered by Trend Micro, in the Papercut print management software. Now, the US Cybersecurity and Infrastructure Security Agency and the FBI have released a joint Cybersecurity Advisory (CSA), providing details of active exploitation of CVE-2023-27350. The FBI observed malicious actors exploit CVE-2023-27350, starting in mid-April 2023 and continuing through the present. In early May 2023, FBI observed a group self-identifying as the Bl00dy Ransomware Gang attempting to exploit vulnerable PaperCut servers in the Education Facilities Subsector. The advisory further provides detection methods for exploitation and details known indicators of compromise (IOCs) related to the group’s activity.
Cybersecurity and Infrastructure Security Agency and FBI, Malicious Actors Exploit CVE-2023-27350 in PaperCut MF and NG, Cybersecurity Advisory AA23-131A, 11 May 2023. Available online at https://www.cisa.gov/news-events/cybersecurity-advisories/aa23-131a.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
Tutorial Covers Three Types of XSS Attack
A rather nice little piece from Trend Micro's DevOps Resource Center provides an introduction to the three types of cross-site scripting (XSS) attacks:
- Reflected cross-site scripting attack
- Stored cross-site scripting attack
- Document Object Model (DOM) cross-site scripting attack
Each of these works on the same basic principle: the threat actor inserts a malicious script into a web site - something that should be impossible if the site was performing rigorous sanitization of untrusted user input. When a victim visits the site, the script is triggered, usually downloading some malware which can then perform malicious actions on the victim's computer.
A good introduction for web developers, and about the right level of detail for CISSP exam candidates.
Trend Micro DevOps Resource Center, 3 Types of Cross-Site Scripting (XSS) Attacks, web page, 11 May 2023. Available online at https://www.trendmicro.com/en_us/devops/23/e/cross-site-scripting-xss-attacks.html.
Multiple Groups Target VMware ESXi With Ransomware
Researchers at SentinelLabs have identified 10 (yes, you read that right - ten) ransomware families, all based on the source code for Babuk, which was leaked in September 2021. Babuk was one of the earliest ransomware programs to target VMware ESXi, and when one of its developers leaked the source code for its different versions - a C++ version to attack Linux systems including ESXi, a Go language version for NAS devices and a C++ version for Windows - it allowed less skilled threat actors to adapt the code for use in their own campaigns
At first, few groups did this, however, although a few Windows derivatives did appear. But during the second half of 2022 and the beginning of 2023, things heated up, and SentinelLabs has now identified ten different ransomware families based on the Babuk source code, based on the reappearance of grammatically odd strings in the code, as well as similar file naming conventions.
SentinelLabs identified overlap between the Babuk code and ESXi lockers attributed to Conti and REvil, and also found they shared unique function name and features with the leaked Conti Windows locker source code. Apart from these two major ransomware players, smaller operators such as Ransom House's Mario have also made use of the Babuk code. This code reuse makes attribution of captured malware samples much more difficult.
The SentinelLabs report provides a full run-down of the various different derivatives, complete with comparisons of code segments. It is likely to be of most interest to malware analysts, but also provides some indicators of compromise.
Delamotte, Alex, Hypervisor Ransomware | Multiple Threat Actor Groups Hop on Leaked Babuk Code to Build ESXi Lockers, blog post, 11 May 2023. Available online at https://www.sentinelone.com/labs/hypervisor-ransomware-multiple-threat-actor-groups-hop-on-leaked-babuk-code-to-build-esxi-lockers/.
Concerns Ramp Up Over Supply Chain Attacks
The recent breach of motherboard manufacturer MSI, together with previous high-profile supply chain attacks such as SolarWinds, 3CX and others, has led to increasing concern on the part of CISO's. The Money Message ransomware gang has leaked private keys it obtained from MSI, allow malware developers to sign malicious firmware updates; if these could be inserted into the supply chain and pushed to customers, the result would be undetected very-low-level infections of millions of systems. Although there is no evidence that this has happened - so far - the possibility is concerning, if not alarming.
This concern is reflected in several recent surveys of security and IT professionals, and the message is clear: although the sky is not falling, we need to escalate efforts to secure the software supply chain.
Goodin, Dan, Leak of MSI UEFI signing keys stokes fears of “doomsday” supply chain attack, Ars Technica, 11 May 2023. Available online at https://arstechnica.com/information-technology/2023/05/leak-of-msi-uefi-signing-keys-stokes-concerns-of-doomsday-supply-chain-attack/.
Roberts, Paul, The surveys speak: supply chain threats are freaking people out, The Security Ledger, 10 May 2023. Available online at https://securityledger.com/2023/05/the-surveys-speak-supply-chain-threats-are-freaking-people-out/.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
Five Eyes, NATO, Take Down Snake P2P Cyber-espionage Network
Multiple agencies around the Western world have announced the dismantling of a massive peer-to-peer spyware network which has been operated for the last 20 years by the Russian FSB (Federal Security Service). The Snake malware was operated by the FSB's Center 16, better known as the APT group Turla or Venomous Bear, and has been detected in over 50 countries across North and South America, Europe, Africa, Asia and Australia, infecting systems in education, media and small businesses to act as relay nodes for encrypted traffic while the main targets for information-gathering implants were government networks, research facilities and journalists as well as some critical infrastructure sectors (government, financial services, critical manufacturing and telecommunications).
Snake is probably the most sophisticated cyber-espionage tool in the FSB's arsenal; it is extremely stealthy - both in the way it infects systems and in its obfuscated communications - and has an extremely elegant modular architecture which allows development and interoperability of new and updated components across multiple operating system platforms. It also demonstrates high-quality software engineering design and implementation, containing surprisingly few bugs given its complexity.
Development of Snake began in late 2003, with initial operations conducted in 2004; its initial name, "Urobouros", is particularly appropriate as since then it has undergone many cycles of redevelopment and upgrade. It is run from an FSB facility in Ryazan, Russia - as indicated by activity increasing during working hours there - as well as from an FSB Center 16-occupied building in Moscow. Over the last 20 years, however, various agencies have been monitoring its operations and collecting samples and have seen it evolve and spin off a range of other implants and related tools such as Carbon (a.k.a. Cobra) and another implant called ComRAT or Chinch.
As cybersecurity and incident response companies have reported on Snake's tactics, techniques and procedures (TTP's), so its developers have implemented new techniques to evade detection, such as fragmenting and encrypting its network traffic, making it challenging for intrusion detection systems - both host- and network-based - to spot.
The FSB operators typically obtain initial access to external-facing infrastructure nodes on a network, and from there pivot to the internal network, using other tools and TTP's to conduct additional exploitation operations. After establishing a foothold on a target network, they typically enumerate the network and use a variety of tools such as keyloggers and network sniffers to obtain user and administrator credentials and access domain controllers, as well as spreading laterally to other networks.
After mapping out a network and getting admin credentials for various domains, the operators generally commence regular data collection operations, mostly using lightweight remote-access tools. They sometimes deploy a small remote reverse shell to enable interactive operations and function as a backup access vector, maintaining a minimal presence while avoiding detection.
The main heavyweight implant comprises stacks of loosely-coupled components which connect via well-designed interfaces; for example its network protocols separate its encryption layer from its transport layer, which could be its custom HTTP protocol or its raw TCP socket protocol. This way, the operators can choose the best network transport protocol to fit into the target environment without detection, yet still preserve the full functionality of the implant, as all the other layers, right up to its command processing code - the 'application' layer - are completely agnostic to what transport is used.
Despite being implemented in the C programming language, the code exhibits very few of the memory management and other bugs common to development in that language, as well as selection of good algorithms. This not to say that it is perfect, however, and a basic error - creating a prime number of only 128 bits in size - signficantly weakened the Diffie-Hellman key agreement component of its encryption layer, while rushed deployment led developers to sometimes compile and link its binaries with debugging symbol tables included - allowing researchers to identify function names, strings and developer comments, thereby gaining insights into its communications protocols and inner workings.
From this initial foothold, various agencies were able to monitor Snake, decrypting and decoding its C2 communications. Ultimately the FBI was able to develop a tool called PERSEUS which establishes a session with the Snake implant on a particular computer and issues commands that instruct the implant to disable itself, effectively overwriting its own components, without affecting the infected host or its legitimate applications. Having obtained authorization from a Federal court, the FBI commenced Operation MEDUSA, which dismantled the Snake network on infected systems within the US.
The US agencies involved - the FBI, the NSA, US Cyber Command's Cyber National Mission Force and the Cybersecurity & Infrastructure Agency - have collaborated with the UK's National Cyber Security Centre, Canada's Centre for Cyber Security abd Communications Security Establishment, the Australian Cyber Security Centre and the New Zealand National Cyber Security Centre, and those agencies will presumably take appropriate actions in their own jurisdictions. In addition, the FBI and US State Department are also providing information to local authorities in other countries where Snake-infected computers have been located.
The agencies have also issued a 48-page joint cybersecurity advisory, which makes fascinating reading, as you might expect, with a full analysis of Snake's communication and application layers, as well as the implant operation. Of course, the advisory also contains suggestions for detection, mitigation and prevention, including a plugin for the Volatility memory analysis framework which will scan all processes, looking for the Snake user mode component having been injected into a process.
Marzulli, John, Justice Department Announces Court-Authorized Disruption of the Snake Malware Network Controlled by Russia's Federal Security Service, press release, 9 May 2023. Available online at https://www.justice.gov/usao-edny/pr/justice-department-announces-court-authorized-disruption-snake-malware-network.
NSA Media Relations, U.S. Agencies and Allies Partner to Identify Russian Snake Malware Infrastructure Worldwide, press release, 9 May 2023. Available online at https://www.nsa.gov/Press-Room/Press-Releases-Statements/Press-Release-View/Article/3389044/us-agencies-and-allies-partner-to-identify-russian-snake-malware-infrastructure/.
Cybersecurity & Infrastructure Security Agency, Hunting Russian Intelligence “Snake” Malware, cybersecurity advisory AA23-129A, 9 May 2023. Available online at https://www.cisa.gov/news-events/cybersecurity-advisories/aa23-129a.
Uncredited, UK and allies expose Snake malware threat from Russian cyber actors, news release, 9 May 2023. Available online at https://www.ncsc.gov.uk/news/uk-and-allies-expose-snake-malware-threat-from-russian-cyber-actors.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
Research Shows Substantial Rise in NSW Cybercrime Reports
Research by the NSW Bureau of Crime Statistics and Research shows that reports of cybercrime have increased by 42% in the three years to June 2022. This is based on data from the Australian Cyber Security Centre's ReportCyber Application Platform (RCAP), which is only one of several different reporting systems, not counting direct reports to state police forces, suggesting that there is a pressing need to integrate these systems in order to permit more comprehensive analysis (but see below).
Based on the RCAP data, all cyber offense categories - cyber-enabled fraud, identity theft, cyber-enabled abuse, online image abuse, and device offences - increased, with the exception of abuse. The biggest increases were seen in device offences such as malware, especially ransomware (117%), followed by fraud (95% - no surprise there) and identity crime (35%). 89% of the reporting victims were individuals; 53% were male and 87% were over 25 years of age.
The majority (71%) of reports were closed by police in RCAP with no further investigation undertaken. Fraud and online image abuse (OIA) were the most likely offence categories to be referred to police for further investigation (at above 40%). Device offences were the least likely to be referred to police at 5%. This may well be because victims know the attackers are based overseas in countries where they are unlikely to be apprehended - if, indeed, any investigation is done at all.
Reports were more likely to be referred to police when the incident involved a victim aged 17 years or younger, the suspect was known to the victim, money was lost, or an online image abuse offence was indicated. Most OIA reports (84%) were referred to police within 7 days compared to just 42% of identity crime reports. In the vast majority of cases, victims do not know any details about the offender and many of those who do, report that the suspected perpetrator resides overseas. This makes it near impossible for local and federal police agencies to prosecute offenders and undermines the deterrent value of any criminal sanctions prescribed for these offences.
All in all, the report makes depressing reading in light of the high cost of police follow-up, coupled with the low probability of successful action, let alone restorative justice for victims. Add to this the wide range of exploits and vulnerabilities, coupled with the susceptibility of many people to social engineering, and the onus really has to remain on strengthening individuals and their systems in order to prevent their exploitation, rather than retrospective policing actions.
Klauzner, Ilya and Amy Pisani, Trends and Characteristics of Cybercrime in NSW, bureau brief, 9 May 2023. Available online at https://www.bocsar.nsw.gov.au/Pages/bocsar_publication/Pub_Summary/BB/BB165-Summary-Cybercrime-in-NSW.aspx.
Commonwealth Budget Adds $A85 Million for Anti-Scam Measures
Meanwhile, at the Federal level, the 2023 Budget released by Treasurer Jim Chalmers includes some allocations for tackling online scams and cybercrime. The major announcement is the establishment of a national anti-scam centre, at a cost of $A58 million, to share scam data across both government and private sectors, and to "establish public-private sector Fusion Cells to target specific scam issues" (I'm not sure what 'Fusion Cells' are, but they sound very cool and will doubtless eliminate all scamming 😉).
An additional $A17 million will be spent over four years to identify and take down phishing websites and investment scams (this sounds rather broad, and if not restricted in scope somehow, I suspect a lot more than $A17 million will be required).
Finally, $A10 million has been allocated for an SMS sender ID registry in an attempt to stop criminals impersonating government and industry names in smishing attacks. To be honest, I can't see that having much effect at all.
Visontay, Elias, Federal budget 2023: winners and losers summary, The Guardian, 9 May 2023. Available online at https://www.theguardian.com/australia-news/2023/may/09/budget-2023-winners-and-losers-summary-who-will-benefit-is-better-worse-off-federal-labor-australia-government-.
News from the World of DDoS
Quite a bit of action in the DDoS world this week, with Fortinet researchers providing details of two botnets and some good news from the US DoJ.
First, FortiGuard Labs has reported on a new version of a botnet first observed in February, but now infecting unpatched wireless access points via a vulnerability (CVE-2023-25717 - CVSS score 9.8) in the Ruckus Wireless Admin panel. The botnet, christened 'AndoryuBot', targets this remote code execution vulnerability to gain initial access, and then downloads a script for further propagation. After initialization, it connects to its C2 server via the SOCKS protocol and waits for commands to launch a DDoS attack, using any of 12 different methods.
Admins running Ruckus Wireless Admin Panel v 10.4 or older should apply the patches released several months ago; older versions which are beyond end-of-life will not get a fix.
In a second report, FortiGuard Labs describes new samples of the RapperBot campaign, which has been active since June 2022, primarily targeting IoT devices, primarily by brute-forcing weak or default SSH or telnet (!) credentials. Once compromised, the devices are used for DDoS attacks.
However, the new variant adds some new functionality, primarily in its C2 protocol, and also adds an SSH public key to compromised devices as a way of remaining persistent should the device be rebooted. Perhaps the most interesting twist is the addition of a Monero cryptomining capability into the bot, whereas previous versions would execute a separate cryptominer.
Finally, the US Department of Justice continues to make progress in shutting down DDoS-for-hire services, also referred to as 'booter' sites. This week, the DoJ seized 13 more Internet domains associated with these services, most of them reincarnations of domains which had been seized during a previous seizure back in December. For example, one of the domains seized this week, cyberstress.org, seems to be the same service as was previously operating as cyberstress.org.
In conjunction with these domain seizures, the Justice Department also announced that four defendants, who had been charged in late 2022 in Los Angeles, have now pleased guily to federal charges, admitting that they operated or participated in the operation of booter services. They will be sentenced this (northern) summer.
Lin, Cara, AndoryuBot – New Botnet Campaign Targets Ruckus Wireless Admin Remote Code Execution Vulnerability (CVE-2023-25717), blog post, 8 May 2023. Available online at https://www.fortinet.com/blog/threat-research/andoryubot-new-botnet-campaign-targets-ruckus-wireless-admin-remote-code-execution-vulnerability-cve-2023-25717.
Salvio, Joie and Roy Tay, RapperBot DDoS Botnet Expands into Cryptojacking, blog post, 9 May 2023. Available online at https://www.fortinet.com/blog/threat-research/rapperbot-ddos-botnet-expands-into-cryptojacking.
Mrozek, Thom, Federal Authorities Seize 13 Internet Domains Associated with ‘Booter’ Websites that Offered DDoS Computer Attack Services, press release, 8 May 2023. Available online at https://www.justice.gov/usao-cdca/pr/federal-authorities-seize-13-internet-domains-associated-booter-websites-offered-ddos.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.