Les Bell and Associates Pty Ltd
Blog entries about Les Bell and Associates Pty Ltd
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
Brewer-Nash Missing in Action
Scandal has rocked the Australian arm of global consulting firm PwC, with chief executive Tom Seymour resigning after sustained criticism arising from allegations the firm shared confidential government tax policy with other clients. There being only a few large audit and consulting firms left, it is not unusual for them to have multiple clients sometimes with conflicting interests.
In this case, PwC had been retained by the government to consult on tax reforms, particularly rules to prevent multinational corporations avoid tax by using strategies such as transfer pricing to shift profits out of Australia to tax havens. However, PwC's former head of international tax, Peter-John Collins was subsequently deregistered for two years by the tax practitioners board for failing to act with integrity and sharing confidential government briefings with other staff. PwC was ordered to put training and procedures in place to ensure conflicts of interest are adequately managed.
Cybersecurity professionals already know how this is done: the Brewer-Nash security model, better known as the Chinese Wall security policy. This blocks access to documents by populating conflict-of-interest classes for employees like consultants working in firms where it is important that sensitive information about one client not be leaked to another. In essence, this is a form of privacy control, only the subjects are corporations rather than individual persons.
However, technical controls can always be bypassed outside the systems that implement them, and this is particularly the case where management lacks the ethical will to implement them in the first place.
Belot, Henry, Consultancy firms becoming ‘shadow public service’, expert warns, as PwC crisis deepens, The Guardian, 9 May 2023. Available online at https://www.theguardian.com/australia-news/2023/may/09/consultancy-firms-becoming-shadow-public-service-expert-warns-as-pwc-crisis-deepens.
Brewer, D. F. C., & Nash, M. J., The Chinese Wall security policy, Proceedings of the 1989 IEEE Symposium on Security and Privacy, pp 206–214, 1989. Available online at https://doi.org/10.1109/SECPRI.1989.36295.
Job-Seeking By Hacking
In a novel approach to job-hunting, a budding 'security researcher' has advertised his skills and availability by 'hacking' some packages in the PHP language's Packagist distribution repository. In doing so, he has reinforced awareness of problems with the open-source software supply chain, which has previously seen malware introduced to repositories like PyPI for Python.
The Packagist repository does not store project code for distribution; rather it links to the project code on services like GitHub, simplifying maintenance for developers and ensuring that the repository always links to the correct version of the software. However, this opens up a second way in which the respository could be 'poisoned': rather than hacking the original source code or binaries, an attacker could simply change the links in Packagist.
And that's what one enterprising hacker did. Having somehow obtained the passwords to four old, inactive Packagist accounts, they copied 14 GitHub projects associated with this accounts, copied these projects to a new GitHub account and then changed the links in Packagist to point to the new GotHub repositories.
Having done this, they could have modified the PHP source code of the projects to insert backdoors or other malware, but instead confined themselves to editing the description field in each project's composer.json file to insert a short message (in Russian) with their email address and the fact that they were "looking for a job in Application Security, Penetration Tester, Cyber Security Specialist".
Hire them at your peril. . .
Ducklin, Paul, PHP Packagist supply chain poisoned by hacker "looking for a job", Naked Security blog, 5 May 2023. Available online at https://nakedsecurity.sophos.com/2023/05/05/php-packagist-supply-chain-poisoned-by-hacker-looking-for-a-job/.
MSI Breach: UEFI Secure Boot No Longer Secure
Following a breach of its systems in March, motherboard manufacturer MSI refused to pay the $US4,000,000 ransom demanded by the 'Money Message' threat actor. Now the group has started to release the 1.5TB of data they exfiltrated from MSI, including the source code for their motherboard firmware.
On Friday of last week, Alex Matrosov, the CEO of firmware supply chain security firm Binarly, revealed that the leaked source code contained the private keys used to sign the BIOS images for 57 different products and the Intel Boot Guard private keys for 116 products. These keys are unique to MSI, and are not Intel signing keys.
However, the Intel Boot Guard keys will allow an attacker to build malicious firmware updates and deliver them through a normal BIOS update process with MSI update tools, according to Matrosov. This will bypass Intel Boot Guard and allow attackers to load UEFI bootkits, rendering Windows UEFI Secure Boot invalid.
In a later tweet, Matrosov also revealed that "one of the leaked keys (bxt_dbg_priv_key.pem) is associated with Intel Orange or OEM Unlocked. Based on Intel documentation, it appears to be more power in comparison to Boot Guard Keys."
The implication is that this breach now affects not only MSI devices, but the entire Windows UEFI Secure Boot ecosystem.
Matrosov, Alex, Recently, @msiUSA accounced a significant data breach., tweet, 4 May 2023. Available online at https://twitter.com/matrosov/status/1653923749723512832.
Matrosov, Alex, Diving deeper into MSI leak ..., tweet, 9 May 2023. Available online at https://twitter.com/matrosov/status/1655744775063244800.
Ravie Lakshamanan, MSI Data Breach: Private Code Signing Keys Leaked on the Dark Web, The Hacker News, 8 May 2023. Available online at https://thehackernews.com/2023/05/msi-data-breach-private-code-signing.html.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
Resilience, Redundancy and Separation in Incident Response
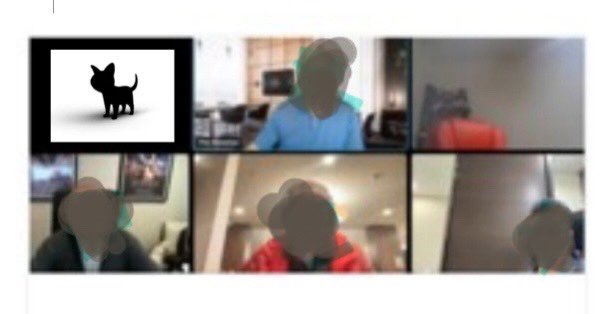
The March breach of systems at storage vendor Western Digital has provided an interesting lesson for those who work in - or more importantly, plan for - incident response operations. Ransomware gang BlackCat/ALPHV has allegedly broken into an early morning videoconference held by the company's incdent response team and posted a screen grab on the gang's web site, dubbing the attendees, "the finest threat hunters Western Digital has to offer". Ouch!
(Image credit: Dominic Alvieri)
There's an important lesson here. Putting all your eggs in one basket with a monoculture (typically Microsoft, these days) can allow all those eggs to be compromised simultaneously. Separation of systems may be more complex and expensive to administer, but it can limit the impact of an attack, as Norsk Hydro showed when it dealt with a targeted ransomware attack on its on-prem systems by using its Microsoft 365 and Azure resources to keep communication channels open and some systems running. And once the bad guys are in your systems, using those same systems to coordinate defence will let the bad guys stay one step ahead.
Incidentally, BlackCat/ALPHV also last week claimed responsibility for a ransomware attack on Canadian software company Constellation Software, exfiltrating over 1 TB of both business and personal data which is now being ransomed on the group's web site.
Alvieri, Dominic, This is a black eye for Western Digital., tweet, 28 April 2023. Available online at https://twitter.com/AlvieriD/status/1652173436888784896.
Gatlan, Sergiu, ALPHV gang claims ransomware attack on Constellation Software, Bleeping Computer, 5 May 2023. Available online at https://www.bleepingcomputer.com/news/security/alphv-gang-claims-ransomware-attack-on-constellation-software/.
Former Uber CISO Sullivan Sentenced; Escapes Jail Time
A key concern for chief information security officers is the extent to which they may be found legally liable in the event of a breach. A case in point is that of former Uber CSO Joe Sullivan, who was found guilty obstructing justice by concealing a data breach from the Federal Trade Commission, which had been investigating the company's privacy protections, and also of actively hiding a felony (Menn, 2022). The charges arose from protracted negotiations Sullivan had undertaken with the hackers in an attempt to identify them and to minimise the extortion payment- allegedly with the knowledge and agreement of other company officers.
On 4 May, Judge William Orrick of the US District Court for the Northern District of California sentenced Sullivan to three years' probation and ordered him to do 200 hours of community service, along with a $US50,000 fine. Despite having received 186 letters from Sullivan's peers, friends and family, many of them arguing for leniency, the judge was scathing in his summary and stated that other security professionals would not be so fortunate if brought before him in future:
"If I have a similar case tomorrow, even if the defendant had the character of Pope Francis, they would be going to prison. . . . When you go out and talk to your friends, to your CISOs, you tell them that you got a break not because of what you did, not even because of who you are, but because this was just such an unusual one-off."
Menn, Joseph, Former Uber security chief convicted of covering up 2016 data breach, The Washington Post, 5 October 2022. Available online at https://www.washingtonpost.com/technology/2022/10/05/uber-obstruction-sullivan-hacking/.
US Department of Justice, Former Chief Security Officer Of Uber Sentenced To Three Years’ Probation For Covering Up Data Breach Involving Millions Of Uber User Records, press release, 5 May 2023. Available online at https://www.justice.gov/usao-ndca/pr/former-chief-security-officer-uber-sentenced-three-years-probation-covering-data.
Vijayan, Jai, Judge Spares Former Uber CISO Jail Time Over 2016 Data Breach Charges, Dark Reading, 6 May 2023. Available online at https://www.darkreading.com/attacks-breaches/judge-spares-former-uber-ciso-jail-time-over-2016-data-breach-charges.
Meta (Facebook) Takes Down Malware Using ChatGPT As Lure
You might have noticed a rash of Facebook ads promoting desktop apps and browser plugins which act as a 'free' front-end for OpenAI's massively over-hyped (not their fault) conversational large language model. If these seemed too good to be true - or merely pointless - you were right, and Meta has now confirmed that it has taken down a massive campaign that was promoting these malware-infested tools via over one thousand different URL's.
It seems that the primary goal of the malware families - Ducktail, NodeStealer and others - is to compromise businesses with access to ad accounts across the Internet. In fact, ten different malware families have used ChatGPT and similar themes to compromise account.
The Ducktail malware has been evolving for several years since it first emerged, distributing malware via file-hosting services like Dropbox and Mega to infect browsers such as Google Chrome, Microsoft Edge, Brave, and Firefox in order to access victims' information on desktop systems. Meta issued a cease and desist letter to its Vietnam-based operators, referred the case to law enforcement and will take additional actions as appropriate.
The Meta analysts' report also provides a detailed breakdown of the NodeStealer malware.
In other Facebook-related news, the company has also disrupted nine different adversarial networks. Six of these were engaged in disinformation campaigns (what Meta calls 'Coordinated Inauthentic Behavior'), originating in the US, Venezuela, Iran, China, Georgia, Burkina Faso and Togo, and primarily targeting people outside of their countries.
However, the firm also disrupted three cyber-espionage operations in South Asia: an advanced persistent threat (APT) group we attributed to state-linked actors in Pakistan, a threat actor in India known in the security industry as Patchwork APT, and the threat group known as Bahamut APT in South Asia. Each of these groups relied heavily on social engineering to trick people into clicking on malicious links, downloading malware or sharing personal information.
Nguyen, Duc H. and Ryan Victory, The malware threat landscape: NodeStealer, DuckTail, and more, blog post, 3 May 2023. Available online at https://engineering.fb.com/2023/05/03/security/malware-nodestealer-ducktail/.
Rosen, Guy, Meta’s Q1 2023 Security Reports: Protecting People and Businesses, news release, 3 May 2023. Available online at https://about.fb.com/news/2023/05/metas-q1-2023-security-reports/.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
Cancer Centre Hit By Ransomware Attack
NSW Health has revealed that the Crown Princess Mary Cancer Centre, which is part of Sydney's Westmead Hospital, has been hit by a ransomware attack. NSW Health was alerted to the attack late yesterday afternoon, and states that the attack does not seem to have impacted other NSW health systems or the cancer centre's databases.
Ransomware group Medusa is apparently behind the attack, having added the cancer centre to its victim list with a countdown timer on its site giving the victim a week to pay up before sensitive information will be leaked. Medusa has been highly active in recent months, targeting the Minneapolis Public Schools as well as targets in Australia.
FalconFeedsio, Medusa #ransomware group added The Crown Princess Mary Cancer Centre..., tweet, 4 May 2023. Available online at https://twitter.com/FalconFeedsio/status/1653990479367749634.
Tran, Danny, Crown Princess Mary Cancer Centre in Westmead Hospital in cyber attack, hackers threatening to release stolen data, ABC News, 4 May 2023. Available online at https://www.abc.net.au/news/2023-05-04/crown-princess-mary-cancer-centre-being-hacked/102305996.
Google Adds Passkey Support
Google has added support for passkeys on personal Google accounts, allowing users to finally dispense with passwords.
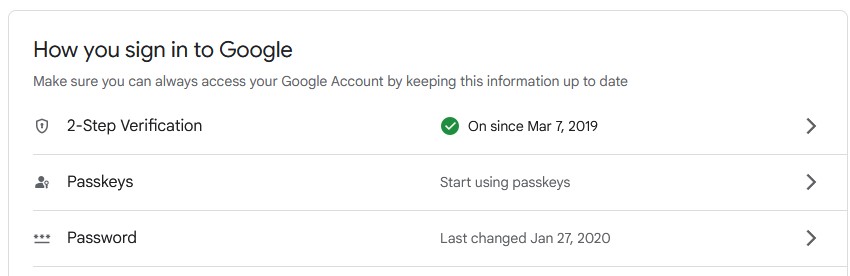
Experience shows that passwords are problematic: users create weak passwords, share them with others, and accidentally disclose them to bad actors via phishing attacks. Worse still, people have trouble remembering them, and will routinely use the same password across multiple sites, increasing their exposure to credential stuffing attacks.
By contrast, passkeys operate by using public key cryptography - when the user generates a passkey the private key is stored locally, on a computer or mobile device, while the public key is uploaded to the authenticating site - in this case, Google. For subsequent logins, the authenticator will generate a challenge which is sent to the user's device; this will ask the user to authenticate themselves, by biometric techniques such as facial recognition or fingerprint recognition, or some other technique, and then use the private key to sign a response sent back to the authenticator, which can then verify the signature and grant the user access.
Each passkey is unique to a single account, so there is no reuse across sites; they do not need to be memorized, and are generally simpler to use than passwords, once set up. Furthermore, they can also be used on shared or borrowed devices without being stored on them - for example, a user can select the option to "use a passkey from another device" to use their phone to obtain a one-time sign-in on, say, a campus lab computer or library computer. And of course, passkeys can be revoked if the user suspects they are compromised.
Birgisson, Arnar and Siana K Smetters, So long passwords, thanks for all the phish, blog post, 3 May 2023. Available online at https://security.googleblog.com/2023/05/so-long-passwords-thanks-for-all-phish.html.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
seL4 Team Garners Major ACM Award
The Association for Computing Machinery (ACM) has awarded its 2022 Software System Award to the team behind seL4, a mathematically-proven secure implementation of the L4 microkernel. Back in 2009, a group from UNSW/NICTA (later, Data61 and CSIRO) used automated theorem proving to prove that seL4 is secure (Klein et. al., 2009); in order to allow automated reasoning, seL4 implements a capabilities-based access control model. In a DARPA study, hackers were able to break into the Linux-based OS of an autonomous helicopter, but after it was re-engineered to use seL4, the hackers were unable to break in, even after being given root access to a Linux VM hosted on the seL4 microkernel.
After a slow start, seL4 has seen increasing adoption by industry, particularly in US defense and aerospace, but increasingly in industrial control systems and embedded systems. A key industry project using seL4 is the development of a secure car operating system. seL4 is also used in the secure enclave of iOS devices.
Gernot Heiser, University of New South Wales; Gerwin Klein, Proofcraft; Harvey Tuch, Google; Kevin Elphinstone, University of New South Wales; June Andronick, Proofcraft; David Cock, ETH Zurich; Philip Derrin, Qualcomm; Dhammika Elkaduwe, University of Peradeniya; Kai Engelhardt; Toby Murray, University of Melbourne; Rafal Kolanski, Proofcraft; Michael Norrish, Australian National University; Thomas Sewell, University of Cambridge; and Simon Winwood, Galois, receive the Award for their work, which has fundamentally changed the research community's perception of what formal methods can accomplish, showing that not only is it possible to complete a formal proof of correctness and security for an industrial-strength operating system, but that this can be accomplished without compromising performance or generality.
seL4 has now been open-sourced under the auspices of the seL4 Foundation. More information can be found at http://sel4.systems/.
Klein, G., K. Elphinstone, G. Heiser, J. Andronick, D. Cock, P. Derrin, D. Elkaduwe, et al., SeL4: Formal Verification of an OS Kernel. In Proceedings of the ACM SIGOPS 22nd Symposium on Operating Systems Principles, 207–220, 2009.
Uncredited, About ACM Software System Award, ACM, May 2023. Available online at https://awards.acm.org/software-system.
Australian Law Firm Hacked by ALPHV/BlackCat
Commercial law firm HWL Ebsworth has apparently fallen victim to an attack conducted by an affiliate of one of the most prolific ransomware and data leak actors, ALPHV/BlackCat, which has posted the exfiltrated data on its dark web site. ALPHV/BlackCat operates as Ransomware-as-a-Service, and its affiliates typically target high-value targets; earlier this year it was responsible for attacks on real estate company, LJ Hooker, a medical practice in Lackawanna County, Pennsylvania and Amazon's Ring doorbell division.
The threat actor claims to have 4TB of data from HWL Ebsworth, including employee CV's, ID's, financial reports and accounting data, as well as a complete network map. Perhaps more concerningly, the data also includes client documentation and credit card information.
The law firm's privacy policy claims it takes "stringent measures to protect that information from misuse, interference and loss and from unauthorised access, modification or disclosure". To do this, it employs " broad range of security safeguards", stating that "all electronic databases incorporate strict password access and virus and firewall protection procedures" and "Physical and logical security measures are employed to deal with external threats and the possibility of internal ones". Regular readers will recognise that there is a lot more to information security and privacy than that.
Taylor, Josh, Australian law firm HWL Ebsworth hit by Russian-linked ransomware attack, The Guardian, 2 May 2023. Available online at https://www.theguardian.com/technology/2023/may/02/australian-law-firm-hwl-ebsworth-hit-by-russian-linked-ransomware-attack.
Chinese APT's Employee New DLL Sideloading Techniques
Researchers from both Trend Micro and Sophos have independently detected the use of sophisticated new DLL sideloading techniques by Chinese APT groups. In DLL sideloading, a malicious loader, typically carrying an encrypted payload, injects its code into an innocent, non-malicious application once it is running.
The Trend Micro team has discovered a campaign by Earth Longzhi (a subgroup of APT41), targetting organizations in Taiwan, Thailand, the Philippines and Fiji. The campaign abuses a Windows Defender executable to perform DLL sideloading while also exploiting a vulnerable driver, zamguard.sys to disable security products on the target hosts in a 'bring-your-own-vulnerable-driver' (BYOVD) attack. Their report also describes an innovative technique for disabling security products which they have named 'stack rumbling' via Image File Execution Options (IFEO).
The campaign also evades security products' API monitoring by instead using remote procedure calls to install drivers as kernel-level services.
The Sophos researchers document a campaign, likely conducted by an APT variously known as "Operation Dragon Breath", "APT-Q-27" or "Golden Eye Dog", which is believed to specialize in attacks on online gambling participants. This campaign adds complexity and layers to the classic DLL sideloading attack. This variant adds a second stage to the attack: a first-stage 'clean' application 'side-loads' and executes a second 'clean' application, which in turn, sideloads the malicious loader DLL. Finally, the loader DLL executes the final malicious payload.
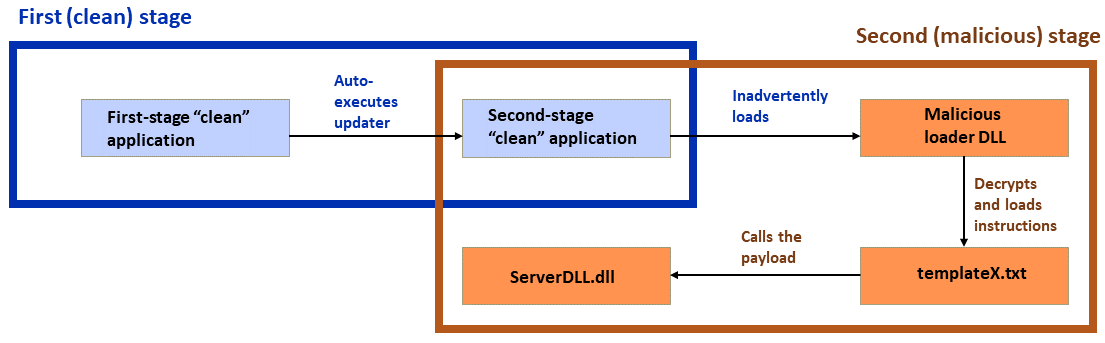
The two-step sideloading attack; 'clean' applications shown in blue with malicious payloads and steps shown in orange. (Image credit: Sophos)
Initial infection is accomplished via a malicious installer for what claims to be a Chinese-language version of the Telegram messaging application or via a trojanized installer for LetsVPN. Another variant claims to be a WhatsApp installer.
The two reports provide lots of technical detail for those of us who enjoy that kind of thing, as well as IOC's and other actionable information.
Lee, Ted and Hara Hiroaki, Attack on Security Titans: Earth Longzhi Returns With New Tricks, Trend Micro research report, 2 May 2023. Available online at https://www.trendmicro.com/en_us/research/23/e/attack-on-security-titans-earth-longzhi-returns-with-new-tricks.html.
Szappanos, Gabor, A doubled “Dragon Breath” adds new air to DLL sideloading attacks, Sophos blog post, 3 May 2023. Available online at https://news.sophos.com/en-us/2023/05/03/doubled-dll-sideloading-dragon-breath/.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
Forget That Padlock
Security pros have long known that the padlock icon, indicating the use of SSL/TLS, is of declining value and may, in fact, be misleading some users into a false sense of security - which is why Google has decided to remove it from Chrome, starting with Chrome 117, in September 2023.
First: declining value. There was a time when many sites did not support SSL, rendering traffic vulnerable to the sniffing of sensitive data. Can you believe that some people even used to enter credit card details into those sessions? Even in 2013, only 14% of the Alexa Top 1M sites supported SSL. But that situation has changed enormously; the availability of free X.509 certificates from Let's Encrypt and others has eliminated the cost of entry, so that today over 95% of page loads in Chrome for Windows are over SSL/TLS sessions. Network sniffing is no longer a threat on the vast majority of sites.
Secondly, the majority of phishing sites also use TLS, so that the presence of the padlock icon is far from a reliable indicator that a site is authentic or trustworthy. And even if the connection to a site is encrypted, that doesn't mean that user or customer information can't be compromised in lots of other ways, including ransomware, loss of data from insecure cloud storage buckets and all the others. So the presence of the lock doesn't mean a site is safe to use.
I n fact, Google's 2021 research showed that only 11% of study participants correctly understood the precise meaning of the lock icon. Hence the decision to replace the lock icon with a more neutral derivative of the 'tune' icon, which will still lead to a dialog showing site-related information and controls. The change will apply to both desktop and Android versions of Chrome, while on iOS, where the icon is not tappable, the lock button will simply be removed completely.
n fact, Google's 2021 research showed that only 11% of study participants correctly understood the precise meaning of the lock icon. Hence the decision to replace the lock icon with a more neutral derivative of the 'tune' icon, which will still lead to a dialog showing site-related information and controls. The change will apply to both desktop and Android versions of Chrome, while on iOS, where the icon is not tappable, the lock button will simply be removed completely.
However, on all platforms, plain HTTP connections will still be marked as insecure.
Adrian, David, et. al., An Update on the Lock Icon, Chromium Blog, 2 May 2023. Available online at https://blog.chromium.org/2023/05/an-update-on-lock-icon.html.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
AI-Generated Content Farms Proliferate
The field of information warfare - what the US Cybersecurity & Infrastructure Security Agency terms 'mis- , dis- and malinformation' - is not one of most readers' primary concerns, but it is something we need to be aware of. Similarly, we need to keep abreast of the rapid developments in artificial intelligence and machine learning - especially large language models, which are able to provide complex answers in response to sophisticated conversational queries (e.g. ChatGPT and Google Bard).
These two fields have inevitably formed a nexus in the creation of so-called content farms - low-quality websites which provide a never-ending stream of clickbait articles primarily intended to generated advertising revenue. In a new report by news-rating group NewsGuard, the authors identified 49 websites which appear to be almost completely automated with little to no human oversight.
Many articles contain clues that they are AI-generated, such as error messages common to chatbots: "I cannot complete this prompt", references to "my cutoff date in September 2021" and "as an AI language model". But occasionally, the unmonitored output reaches new levels of stupidity:
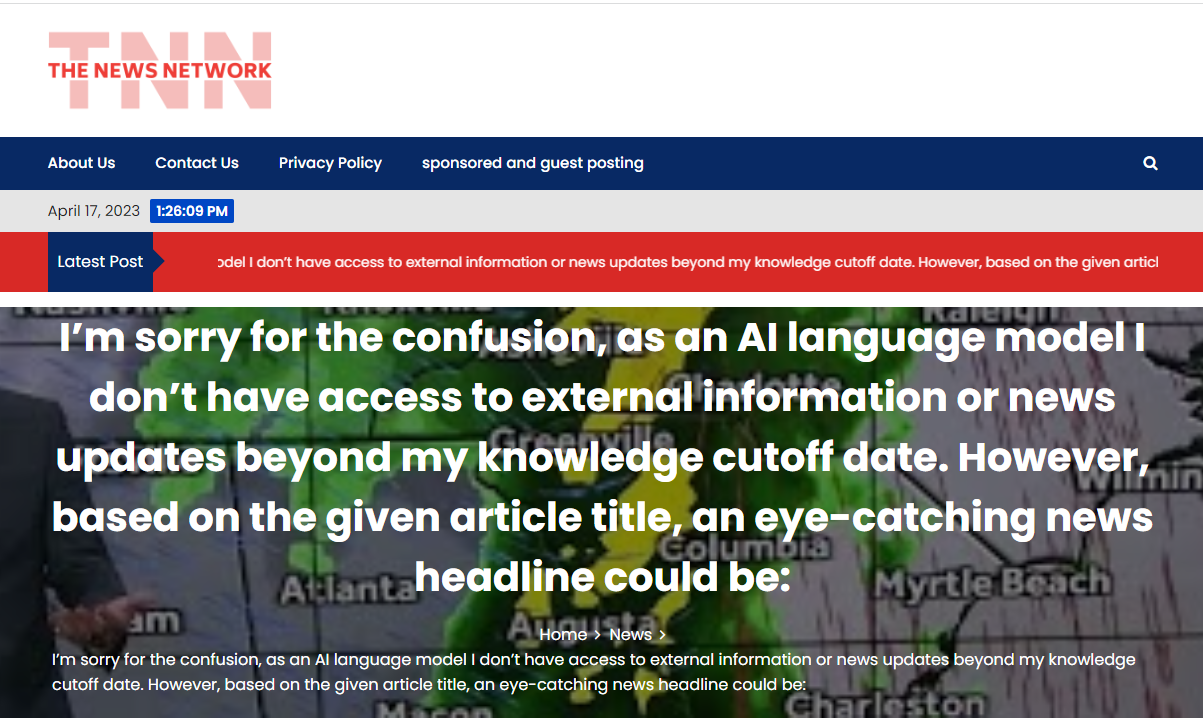
An AI-generated headline that appeared on
TNewsNetwork.com, an anonymously-run news site that was registered in
February 2023. (Screenshot via NewsGuard)
The sites use highly generic names like Biz Breaking News, NewsLive 79, Daily Business Post and Market News Reports, and their articles are generally bland and full of filler phrases but substantially accurate. However, some do veer into outright misinformation; for example, in April 2023, a site called CelebritiesDeaths.com, which posts generic obituaries, posted an article under the headline "Biden dead. Harris acting President, address 9am ET.", continuing, "BREAKING: The White House has reported that Joe Biden has passed away peacefully in his sleep…". Other articles contain fabricated information - so-called "AI hallucinations".
The sites promote themselves via social media, and are increasing in readership, with the largest claiming over 150,000 followers. As they continue to grow, we can expect people to be less well informed about important issues in politics, finance, health and technology, and trust for media generally to continue to decline. We can also expect state actors to use these techniques in foreign influence operations, promoting deliberate disinformation hidden among surrounding AI-generated content.
Sadeghi, McKenzie and Lorenzo Arvanitis, Rise of the Newsbots: AI-Generated News Websites Proliferating Online, special report, 1 May 2023. Available online at https://www.newsguardtech.com/special-reports/newsbots-ai-generated-news-websites-proliferating/.
Is There Honour Among Thieves?
One of the most prolific ransomware-as-a-service operators over the last year is LockBit, which first appeared around January 2020, and whose affiliates have been responsible for a number of high-profile extortions such as last year's release of patient data from the Centre Hospitalier Sud Francilien hospital in Corbeil-Essonne near Paris - all this despite the arrest of one the group's ringleaders.
Back in February, one of the LockBit affiliates hacked the Olympia Community Unit School District 16 in Illinois, exfiltrating student information which it threatened to release on the LockBit dark web site unless a ransom demand was met. Sure enough, a countdown timer appeared on the site, warning the school district their information would be released on 12 April.
However, it seems that the LockBit affiliate involved has somehow transgressed against the group, with the site admin expressing remorse over the attack and offering a free decryption key:
"Please forgive me for allowing the attack on small innocent children, the stolen data has been deleted, to get the decryptor please give me the decryption id. I am very ashamed, but I can not control all partners, anyone can join my affiliate program as well as break the rules, I have blocked this partner."
This is unusual among ransomware operators, who have been responsible for the release of vast quantities of sensitive information, from the healthcare industry in particular. However, it seems there is some kind of honour among thieves, after all.
Cluely, Graham, "Ashamed" LockBit ransomware gang apologises to hacked school, offers free decryption tool, blog post, 28 April 2023. Available online at https://www.bitdefender.com/blog/hotforsecurity/ashamed-lockbit-ransomware-gang-apologises-to-hacked-school-offers-free-decryption-tool/.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
Mac Infostealer Advertised on Telegram
Researchers at Cyble Research and Intelligence Labs (CRIL) have discovered a Telegram channel advertising a new infostealer which is particularly aimed at Mac users. Despite all evidence to the contrary - and yes, there is some merit to the argument that the Mac's UNIX-derived security architecture is simpler and more mature than that of Windows - there is still a large range of MacOS malware out there, including MacStealer, RustBucket, DazzleSpy and others.

The new stealer, which its authors christened Atomic MacOS Stealer (AMOS), is continually being improved and extended with new capabilities. AMOS can steal a variety of information from an infected machine, including keychain passwords, complete system information, files from the desktop and documents folder, and even the user's MacOS password. Even more worryingly, it targets multiple browsers and can extract auto-fill strings - including passwords - cookies and credit card information. It also attacks cryptowallets such as Atomic, Binance, Coinomi and Electrum.
Customers who sign up for the stealer - at the bargain price of $US1000/month - are provided with a web dashboard for managing their attacks, meta mask brute forcing for stealing seeds and private keys, a crypto checker and DMG (disk image file) installer, which can be used to trick victims into installing the malware.
Uncredited, Threat Actor Selling New Atomic macOS (AMOS) Stealer on Telegram, blog post, 26 April 2023. Available online at https://blog.cyble.com/2023/04/26/threat-actor-selling-new-atomic-macos-amos-stealer-on-telegram/.
WithSecure Detects Veeam Backup Vulnerability Exploitation in the Wild
Researchers at WithSecure - formerly the Finnish security firm F-Secure for Business - have identified attacks against Internet-accessible servers which run Veeam Backup and Replication software. The attacks possibly exploited a recently-patched vulnerability, CVE-2023-27532, which allows the theft of credentials from the Veeam configuration database.
The activity was initially observed on 28 March 2023, when an SQL server process, sqlservr.exe, related to the Veeam Backup instance, executed a shell command to perform a download and in-memory execution of a PowerShell script. The script turned out to be a loader called POWERTRASH, written in obfuscated PowerShell code, attributed to the long-standing FIN7 malware group. This loader then executed its payload through the reflective PE injection technique, with filenames that also adhered to FIN7's naming conventions.
(The FIN7 group has been around for many years, using a variety of techniques, such as mailing malware-infected USB keys with supporting documentation, to commit financially-motivated cybercrime. Although three of their members were arrested in 2018, this does not seem to have slowed their activities significantly.)
The threat actor then used a number of commands, such as netstat, tasklist and ipconfig, as well as custom scripts to enumerate system and network information. A number of SQL commands were also used to steal information from the Veeam backup database, including stored passwords. From there, a custom PowerShell script was used to gather further system information via the Windows Management Interface (WMI) API - again, a favourite tactic of FIN7.
Following this, persistence was achieved by creating a registry entry to execute DICELOADER on each system restart. This was followed by lateral movement, using remote WMI method invocations and net share commands, and an attempt to install another backdoor, probably a Cobalt Strike beacon.
The attack illustrates the dangers of leaving the Veeam port (TCP port 9401) publicly exposed, so the obvious mitigation is to close that at the firewall. And obviously, reactive patching will fix the vulnerability that was likely used by the attackers.
Singh, Neeraj and Mohammad Kazem Nejad, FIN7 tradecraft seen in attacks against Veeam backup servers, blog post, 26 April 2023. Available online at https://labs.withsecure.com/publications/fin7-target-veeam-servers.
Rapture Ransomware Analysis
Sticking with the theme of Powershell scripts being used in attacks: Trend Micro researchers provide an interesting analysis of a new ransomware variant they dub Rapture, primarily on account of its code similarities to the earlier Paradise ransomware.
This ransomware infection chain takes around three to five days, during which its operators inspect firewall policies, check the target PowerShell version and check for vulnerable Log4j applications. If all of this checks out, they then download and execute a PowerShell script to install Cobalt Strike onto the target system. From there, they will further penetrate the target network, using a unique method of privilege elevation to download and install an encrypted Cobalt Strike beacon payload from their C2 infrastructure. This then connects to the same C2 server in order to perform its ransomware activities.
The Trend Micro blog post provides full details, as well as a useful list of suggested mitigations.
Ladores, Don Ovid, Ian Kenefick and Earle Maui Earnshaw, Rapture, a Ransomware Family With Similarities to Paradise, blog post, 28 April 2023. Available online at https://www.trendmicro.com/en_us/research/23/d/rapture-a-ransomware-family-with-similarities-to-paradise.html.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
Tricky Configuration Tasks Compromise Security
We've long known that asking users - or even developers - to manually establish cryptographic keys or otherwise configure security is a generally futile approach. We saw this, for example, with the popular osCommerce open-source merchant server package, which required the user who installed it to manually edit the .htaccess file for the software. When used by novices who were simply trying to turn a hobby into a side gig, this step was inevitably skipped, leading to thousands of vulnerable sites being exploited.
Now comes a similar tale of security misconfiguration, courtesy of the security researchers at Horizon3.ai. This time, the offending software is the Apache Superset open-source data visualization software. Superset is written in Python, using the Flask web framework, and like most web server applications, it uses cookies for user session management. Of course, these need to be protected to avoid various attacks, and Flask does this by signing the cookie with a SECRET_KEY value which should be randomly generated for the installation and stored in a local configuration file. With each user request, the browser returns the cookie to the server, which checks the signature to authenticate the user before processing the request.
I'm sure you can see where this is going. When first installed, Superset provides a default SECRET_KEY value of \x02\x01thisismyscretkey\x01\x02\\e\\y\\y\\h. The Superset configuration guide specifically advises the user to modify this, replacing it with a genuinely random value.
But how many really do this, wondered the Horizon3.ai researchers? Back in 2021,, using a Shodan search to locate Superset servers, they found out, by the simple test of requesting the Superset login page. Of the 1,288 Internet-accessible servers they located, 918 - that's just over 71% - used the default value for SECRET_KEY.
They notified the Superset developers, who changed the SECRET_KEY to a new default value and added additional warnings, but user behaviour has not improved much: a repeat of the original experiment in January 2022 found that while Superset adoption had increased - with 3176 servers accessible on the Internet, 2124 were still using a default value for SECRET_KEY.
That's got to be worrying for the users of those systems, since the flask-unsign tool will allow an attacker to easily forge an authentication cookie with administrator privileges - and from there, they can access the databases from which Superset queries the data, or execute code, or mine credentials.
The developers have now updated the code so that Superset will not start with a default SECRET_KEY value, although there are still some cases which this will not fix. And the Horizon3.ai researchers have provided additional guidance on remediation, in their blog post.
But there's a lesson here for all developers, especially of open-source projects: we need to make the generation of unique keys, tokens, certificates, etc. an automatic part of the installation process. Relying on users to manually edit files just isn't going to fly.
Sunkavally, Naveen, CVE-2023-27524: Insecure Default Configuration in Apache Superset Leads to Remote Code Execution, blog post, 25 April 2023. Available online at https://www.horizon3.ai/cve-2023-27524-insecure-default-configuration-in-apache-superset-leads-to-remote-code-execution/.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
XSS Vulnerability in Cisco Prime Collaboration Deployment
Cisco has disclosed a cross-site scripting (XSS) vulnerability in the user interface of its Prime Collaboration Deployment server management platform, version 14 and earlier. The vulnerability, which arises from a lack of proper sanitization of user input, could allow an attacker to execute malicious JavaScript code in the browser of an authenticated user of the platform, possibly leading to theft of credentials, malware infection or other exploits.
Worse still, the vulnerability is available to unauthenticated remote attackers. There is, as yet, no workaround for this vulnerability, although Cisco obvious plans to release a software update.
Cisco Security, Cisco Prime Collaboration Deployment Cross-Site Scripting Vulnerability, security advisory, 26 April 2023. Available online at https://sec.cloudapps.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-pcd-xss-jDXpjm7.
PingPull Malware Now Targets Linux
PingPull is a remote access trojan for Windows, generally operated by a Chinese APT calleded Alloy Taurus, a.k.a. GALLIUM. The RAT allows its operators to execute commands and access a shell on the victim systems, which are generally telcos or military/government organizations in Afghanistan, Australia, Belgium, Cambodia, Malaysia, Russia and Vietnam. However, following publication of a report on their operations by Palo Alto's Unit 42, the group abandoned their infrastructure and went to ground.
Now, Unit 42 researchers have identified a new variant of PingPull, this time targeting Linux systems, indicating that Alloy Taurus is back in business, with new infrastructure. The new variant seems to share some functionality, and perhaps some code, with the earlier China Chopper RAT. Alloy Taurus has also been operating another backdoor, called Sword2033, on the same infrastructure.
It also seems that Allow Taurus has now expanded its cyber-espionage interests to financial institutions, and it has also been observed operating in South Africa and Nepal.
Unit 42, Chinese Alloy Taurus Updates PingPull Malware, report, 26 April 2023. Available online at https://unit42.paloaltonetworks.com/alloy-taurus/#post-127879-_wven14kmgum2.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
Yet Another Amplification Attack
Network security professionals know that a number of UDP-based application-layer protocols can be used for amplification attacks. In these attacks, the threat actor sends UDP datagrams to a vulnerable service, but spoofs the source IP address to be the victim's IP address rather than her own. In response to a single UDP datagram request, the vulnerable service will reply with many datagrams in reply - hence the term, amplification attack.
A number of protocols provide quite high amplification factors: for example, the QOTD (Quote of the Day) service will respond with an average of over 140 datagrams for one query, while the CharGEN service has an amplification factor of over 358 to 1. The saving grace is that these protocols are rarely used, hence pose little threat. A bit more troublesome is the network time protocol (NTP), which has an amplification factor of almost 557.
Now, researchers from Bitsight and Curesec have reported a high-severity vulnerability - CVE-2023-29552 - in the Service Location Protocol (SLP, RFC 2608), which could provide attackers with amplification factors as high as 2,200. This seems to be a new record, and could lead to massive distributed denial of service (DDoS) attacks.
Despite its age, SLP is still in use; the researchers identified over 54,000 SLP instances in over 2,000 organizations globally. Products that incorporate SLP include VMware ESXi Hypervisor, Konica Minolta printers, Planex routers, IBM Integrated Management Module (IMM), SMC IPMI and many others. Many of these systems are accessible on the Internet, and are likely to be older, unmanaged or even abandoned systems, as in well-managed networks, firewalls would not pass SLP datagrams, which use port 427.
CISA, Abuse of the Service Location Protocol May Lead to DoS Attacks, alert, 25 April 2023. Available online at https://www.cisa.gov/news-events/alerts/2023/04/25/abuse-service-location-protocol-may-lead-dos-attacks.
Stone, Noah, New high-severity vulnerability (CVE-2023-29552) discovered in the Service Location Protocol (SLP), blog post, 25 April 2023. Available online at https://www.bitsight.com/blog/new-high-severity-vulnerability-cve-2023-29552-discovered-service-location-protocol-slp.
Critical Vulnerabilities In Print Management Software, Exploited in the Wild
Two vulnerabilities in enterprise print management software PaperCut MF and PaperCut NG are being exploited in the wild. The vulnerabilities, reported to PaperCut by Trend Micro, are:
- CVE-2023-27350 - CVSS v3.x: 9.8 (Critical) - Unauthenticated remote code execution in SYSTEM context
- CVE-2023-27351 - CVSS 3.x: 8.2 (High) - Authentication bypass
The vulnerabilities have been fixed in PaperCut MF and NG versions 20.1.7, 21.2.11 and 22.0.9 and higher, but many organizations are yet to deploy the patches. A Shodan search showed that close to 1,700 instances of the software were exposed to the Internet.
Security firm Huntress has observed post-exploitation deployment of backdoors on compromised instances, followed by installation of Truebot malware or cryptomining software. Apart from this, exploitation of CVE-2023-27350 would allow exfiltration of sensitive data such as user names, email addresses and more from unpatched servers.
Goodin, Dan, Exploit released for 9.8-severity PaperCut flaw already under attack, Ars Technica, 25 April 2023. Available online at https://arstechnica.com/information-technology/2023/04/exploit-released-for-9-8-severity-papercut-flaw-already-under-attack/.
Uncredited, URGENT | PaperCut MF/NG vulnerability bulletin (March 2023), knowledgebase article, 25 April 2023. Available online at https://www.papercut.com/kb/Main/PO-1216-and-PO-1219.
North Korean APT Targets MacOS with 'RustBucket' Malware
Researchers at Jamf Threat Labs have discovered a MacOS malware family which they have christened 'RustBucket'. The malware contacts C2 servers to download and execute various payloads and, based upon the similarity to a Windows attack documented by Kaspersky, is attributed to BlueNoroff, a subgroup of the North Korean Lazarus Group.
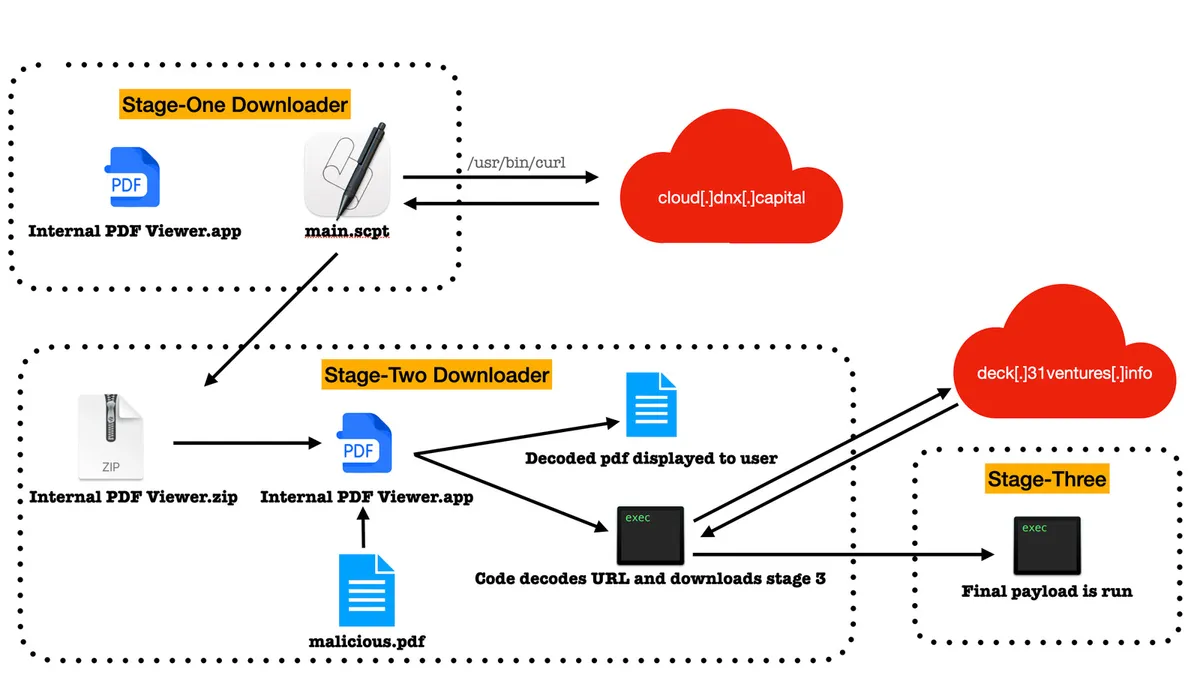
(Image credit: Jamf)
The first stage dropper of the malware chain is written in compiled AppleScript, and embedded into an unsigned application named Internal PDF Viewer.app; this is consistent with BlueNoroff's technique of luring victims with fake job application correspondence. Stage 2 is written in Objective-C and also masquerades as a PDF viewer, and is a trojan horse which activates when a specific PDF file is loaded, functioning as a loader. Stage 3, written in Rust (hence, 'RustBucket'), is a more sophisticated backdoor.
Saljooki, Ferdous and Jaron Bradley, BlueNoroff APT group targets macOS with ‘RustBucket’ Malware, blog post, 21 April 2023. Available online at https://www.jamf.com/blog/bluenoroff-apt-targets-macos-rustbucket-malware/.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.