Les Bell and Associates Pty Ltd
Blog entries about Les Bell and Associates Pty Ltd
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
Extra Chrome Security for Google Workspace Users
Many SME's - and more than a few large ones - use Google Workspace, a SaaS application suite that takes away a lot of the maintenance chores that come with complex desktop software. The Google Workspace applications are accessed via a desktop browser progressive web applications (PWA's) or phone apps, and while Firefox and other browsers will work, there's a natural tendency to use the Chrome browser.
Now an article in the Google Security Blog provides a number of advanced tips for Workspace Administrators on hardening Chrome configurations for their users. To quickly summarize:
- Bring Chrome under Cloud Management
- Enforce built-in protections against Phishing, Ransomware & Malware
- Enable Enterprise Credential Protections in Chrome
- Gain insights into critical security events via Audit Logs, Google Security Center or your SIEM of choice
- Mitigate risk by keeping your browsers up to date with latest security updates
- Ensure employees only use vetted extensions
- Ensure your Google Workspace resources are only accessed from Managed Chrome Browsers with protections enabled
- Enable BeyondCorp Enterprise Threat and Data Protections
Enabling these features effectively turns on a form of EDR in the browser; admins can detect when users enter their corporate credentials into other websites, navigate to malicious sites or download (or upload) malware files, restrict access to highly confidential applications to only users with strong authentication credentials, force automatic updates to Chrome and review the extensions users have installed.
Nair, Kiran, 8 ways to secure Chrome browser for Google Workspace users, blog post, 1 March 2023. Available online at https://security.googleblog.com/2023/03/8-ways-to-secure-chrome-browser-for.html.
Bootkit Bypasses UEFI Secure Boot
One of the great advantages of Windows 11 - and one of the problems it poses for older hardware - is its secure boot facility. Using the keys in the Trusted Platform Module as the root of a chain of trust, it ensures that an unmodified set of operating system files load at boot time and blocks kernel-mode malware such as rootkits. There have previously been a few UEFI bootkits and rootkits, but they generally reside on an easily-discoverable FAT32 disk partition.
But now, there's a bootkit circulating in the wild that can bypass the UEFI Secure Boot feature in fully-patched Windows 11 systems. The bootkit, called BlackLotus, has been selling on hacking forums for $US5,000 since at least October 2022, according to ESET researchers.
The bootkit exploits CVE-2022-21894, a vulnerability that dates back to December 2021 and which was fixed in Microsoft's January 2022 update. However, the affected, validly signed binaries have still not been added to the UEFI revocation list - and BlackLotus takes advantage of this by carrying its own copies of the unpatched binaries.
The resultant bootkit can run on the latest, fully patched Windows 11 systems with UEFI Secure Boot enabled, and can disable security features such as BitLocker, Hypervisor-protected Code Integrity (HVCI - which Windows Device Security refers to as Memory Integrity) and Windows Defender. Once it has installed, the bootkit deplys a kernel driver and an HTTP downloader which communicates with its C2 and can download user-mode or kernel-mode payloads.
ESET's lengthy article provides a full analysis of BlackLotus's operation along with IOC's. Attribution is uncertain, but the fact that the installers do not run if the system locale is one of the Comonwealth of Independent States - i.e. the old Soviet bloc - may well be significant.
Smolár, Martin, BlackLotus UEFI bootkit: Myth confirmed, blog post, 1 March 2023. Available online at https://www.welivesecurity.com/2023/03/01/blacklotus-uefi-bootkit-myth-confirmed/.
Iron Tiger Takes a Bite of Linux
Iron Tiger (APT 27) has been in the cyber-espionage business for over a decade now, using their own custom malware to target foreign embassies in search of intelligence on the government, defence and technology sectors. One of their tools, called SysUpdate, is a versatile backdoor which can manage services, grab screenshots, search for, upload and download files, and execute commands. It uses a complex chain of loaders, probably in an attempt to evade detection.
According to a new report from Trend Micro, it seems that since late 2022, Iron Tiger has deployed a Linux version of SysUpdate, replacing the previously-used C++ class library with the ASIO C++ asynchronous library and producing ELF binaries. It seems likely that they will now produce a version targeting Mac OS. They also added a new C2 protocol, tunneling commands and responses in DNS TXT resource record requests - a feature which has also been seen in at least one sample of the Windows variant.
To date, the Linux variant has only been seen in one compromised victim, a gambling company in the Philippines - an industry which has attracted Iron Tiger before.
Lunghi, Daniel, Iron Tiger’s SysUpdate Reappears, Adds Linux Targeting, blog post, 1 March 2023. Available online at https://www.trendmicro.com/en_us/research/23/c/iron-tiger-sysupdate-adds-linux-targeting.html.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
CISA Adds One Known Exploited Vulnerability
The US Cybersecurity & Infrastructure Security Agency has added another vulnerabilit to its Known Exploited Vulnerabilities Catalog, indicating that it is frequently used in the wild and poses a significant risk. CVE-2022-36537 affects the AutoUploader component of the ZK Java framework, and has a CVSS 3.1 score of 7.5, making it a high risk.
According to CISA, "ZK Framework AuUploader servlets contain an unspecified vulnerability that could allow an attacker to retrieve the content of a file located in the web context. The ZK Framework is an open-source Java framework. This vulnerability can impact multiple products, including but not limited to ConnectWise R1Soft Server Backup Manager".
Affected users should update their software to the latest version immediately.
Uncredited, CISA Adds One Known Exploited Vulnerability to Catalog, alert, 27 February 2023. Available online at https://www.cisa.gov/news-events/alerts/2023/02/27/cisa-adds-one-known-exploited-vulnerability-catalog.
Post-Exploitation Framework Offers Attackers Lots of Options
A new post-exploitation framework - essentially a backdoor on steroids - known as EXFILTRATOR-22, or EX-22 for short, has emerged in underground marketplaces as a service available to threat actors, according to CYFIRMA. Whoever developed the framework is thoroughly familiar with defence evasion and antiforensics techniques, and claims that the tools are completely undetectable by every antivirus and EDR vendor in their promotions via Telegram and YouTube. The claim seems plausible - as of 13 February, the framework still has only 5/70 detections on online sandboxes.
The framework is highly functional, with a wide range of features:
- Reverse shell with elevated privileges, allowing remote command execution
- File download and upload
- Keylogger
- Ransomware functionality
- Screen capture
- Live VNC session, allowing both viewing of user activity and remote control
- Privilege escalation
- Persistence, so that the framework restarts after a reboot
- Lateral movement via a worm which can rapidly infect a large number of nearby devices
- LSASS Dump
- Stealing authentication tokens
In short, this is a very powerful toolkit which will be attractive to cybercriminals, even at quite high subscription rates ($US1000 per month and $5000 for lifetime access), especially in view of the low detection rates, which make it attractive by comparison with tools like Cobalt Strike and Brute Ratel.
According to the CYFIRMA researchers, similarities between EX-22 and both the code and the C2 infrastructure of the LockBit ransomware suggest that the two share the same developers, who are probably based in Asia, most likely SE Asia. Their report provides both a MITRE mapping and IOC's, as well as a detailed analysis.
CYFIRMA Research, EXFILTRATOR-22 - An Emerging Post-Exploitation Framework, February 2023. Available online at https://www.cyfirma.com/outofband/exfiltrator-22-an-emerging-post-exploitation-framework/.
Bitdefender Releases MortalKombat Decryptor
The MortalKombat ransomware spreads through phishing emails and exposed Remote Desktop Protocol (RDP) instances, installing itself via the BAT loader. Once it is running, it encrypts files, adding the unmissable file extension:
..Remember_you_got_only_24_hours_to_make_the_payment_if_you_dont_pay_prize_will_triple_Mortal_Kombat_Ransomware
It also changes the desktop wallpaper to a Mortal Kombat theme and generates a ransom note called HOW TO DECRYPT FILES.txt.
Now Romanian security firm Bitdefender has released a free universal decryptor for the current version of MortalKobat. As well as the usual double-click execution, the decryptor can also be run silently from the command line, making it ideal for scripted repair of larger network infections.
Bitdefender, Bitdefender Releases Decryptor for MortalKombat Ransomware, blog post, 1 March 2023. Available online at https://www.bitdefender.com/blog/labs/bitdefender-releases-decryptor-for-mortalkombat-ransomware/.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
White Hat Arrested; Was Black Hat in Reality
Back in January, Dutch police arrested three men, aged between 18 and 21, in connection with ransomware attacks on thousands of companies, but continued their covert investigation, isolating two of the suspects, before finally laying charges of computer intrusion, data theft, extortion, blackmail and money laundering.
The three typically demanded a ransom of around €100,000, but in some cases as high as €700,000; the prime suspect, a 21-year-old from Zandvoort, earned approximately €2,500,000 in the last few years. Despite victims paying up, in many cases the exfiltrated data was leaked online anyway, demonstrating the futility of paying ransoms - as well as the old saw that there is no honour among thieves.
However, the most intriguing fact is that one of those arrested was reportedly an active member of the Dutch Institute for Vulnerability Disclosure, a government-backed group of ethical hackers. It seems he may have been living something of a double life.
Clueley, Graham, "Ethical hacker" amongst those arrested in Dutch ransomware investigation, blog post, 28 February 2023. Available online at https://www.bitdefender.com/blog/hotforsecurity/ethical-hacker-amongst-those-arrested-in-dutch-ransomware-investigation/.
LastPass Doubly Hacked; Compromised via WFH Engineer
When LastPass discovered an intrusion last August, they thought they had kicked out the attacker and that was the end of the matter. It wasn't.
In a support note posted online, the company has revealed that “the threat actor pivoted from the first incident, which ended on August 12, 2022, but was actively engaged in a new series of reconnaissance, enumeration, and exfiltration activities aligned to the cloud storage environment spanning from August 12, 2022 to October 26, 2022”.
The company was blindsided by the fact that the TTP's and IOC's of the two breaches were different, leading investigators to conclude they were not related. In fact, the attacker had stolen valid credentials from a senior DevOps engineer and was able to subsequently use these to access the company's AWS infrastructure. It was only when AWS GuardDuty Alerts indicated that the attacker was trying to use cloud IAM roles to perform unauthorized activities that they woke up to the second attack.
So, how were those credentials obtained? According to the firm, "this was accomplished by targeting the DevOps engineer’s home computer and exploiting a vulnerable third-party media software package, which enabled remote code execution capability and allowed the threat actor to implant keylogger malware. The threat actor was able to capture the employee’s master password as it was entered, after the employee authenticated with MFA, and gain access to the DevOps engineer’s LastPass corporate vault.
"The threat actor then exported the native corporate vault entries and content of shared folders, which contained encrypted secure notes with access and decryption keys needed to access the AWS S3 LastPass production backups, other cloud-based storage resources, and some related critical database backups."
LastPass called in Mandiant, and has undertaken extensive remedial work, which is detailed on their page. But at root, this demonstrates the risk of hybrid work and telecommuting with employees using personal devices.
Uncredited, Incident 2 – Additional details of the attack, support note, February 2023. Available online at https://support.lastpass.com/help/incident-2-additional-details-of-the-attack.
Hackers Capitalize on ChatGPT Fever
Like everyone else, your humble scribe has tinkered with OpenAI's public test of ChatGPT, the interactive front end to the GPT-3 (Generative Pre-trained Transformer) language model. It's impressive, easily providing me with code to integrate it into Google Chat - code that was almost correct, too.
It's also amusing, because of the confident way it asserts completely incorrect information - I suspect more than a few students will get a nasty surprise when essay submissions are returned to them after marking, as a result - only to back down and apologize when challenged. However, I suspect all this experimenting is teaching us less about artificial intelligence and more about the average human's willingness to believe that whatever comes out of a computer must be correct.
Cybercriminals already know this, of course, and are quick to exploit it when any trend goes viral on social media. The latest example, therefore, is ChatGPT. Over the last week, I've repeatedly seen Facebook ads for a ChatGPT app for Windows, which had the curious property of having close to a thousand comments, only none which are visible, even when set to "display all comments".
Security researcher Dominic Alvieri has found fake websites as well as fake ChatGPT apps on the official Google Play store as well as third-party app stores. In most cases, the fake apps infect the victim with infostealers such as Redline, Aurora or Lumina.
These are all fairly obvious to more tech-savvy users, since ChatGPT depends upon massive compute resources, and is only available via its online interface at https://chat.openai.com/.
Constantinescu, Vlad, ChatGPT Apps to Spread Malware, blog post, 24 February 2023. Available online at https://www.bitdefender.com/blog/hotforsecurity/cybercriminals-leverage-fake-chatgpt-apps-to-spread-malware/.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
Autonomous Cyber Defence
As cyber attacks become more prevalent and the consequences of a breach get greater and greater (think of attacks on healthcare, industrial control systems and the Internet of Things), we face increasing manpower shortages. It takes a range of skills across networking, software development, system administration and operations to deal with possible attacks on complex systems, and there simply aren't enough skilled people to go around.
Last week I stumbled across an academic paper which points to the likely future: automated defence using machine learning. The authors are researchers at the US Department of Energy's Pacific
Northwest National Laboratory, which is particularly interested in
techniques to defend industrial controls systems - such as, in
particular, the power grid - against cyber attacks. Their paper first caught my attention because it uses similar techniques to my own research in computational trust, but here they are adapted to cyber defence.
A number of factors have combined to make this automated approach almost practical. Among these is the emergence of an ontology for describing cyber attacks, along with developments in deep learning and, of course, the availability of increasing compute power to solve the problems.
Let's start with the first of these. Attendees at my CISSP courses and university lectures will be familiar with the concept of the cyber intrusion kill chain, first introduced by Lockheed-Martin over a decade ago. This laid out a seven-stage model of a typical sophisticated attack, as attempted by an advanced persistent threat. This influenced the development of MITRE's ATT&CK matrix, which is rather more granular and much more detailed.
This also saw more formalization in the use of terms like Tactics, Techniques and Procedures - tactics are derived from the kill chain's stages and describe high-level activities such as reconnaisance, persistence, C2, collection and exfiltration, while techniques are how the attacker achieves his goal for each tactical stage. In essence, tactics are classes of exploits, like privilege escalation, screen capture or phishing (ATT&CK breaks these down further, with hundreds of sub-techniques). The final level, procedures, equate to the specific exploits which take advantage of vulnerabilities - and these, of course, are now captured in the CVE and CWE databases.
In this model, the attacker works their way along the kill chain, tactic by tactic, using techniques to enable a move to the next stage. In terms of game theory, this is referred to as a stochastic game (or Markov game), in which the entire game is represented by a directed graph, with the probability of transitioning from one state to another state dependent upon the skills and resources of the attacker, versus the skills and resources of the defender. Now take a look at this figure, taken from the paper:
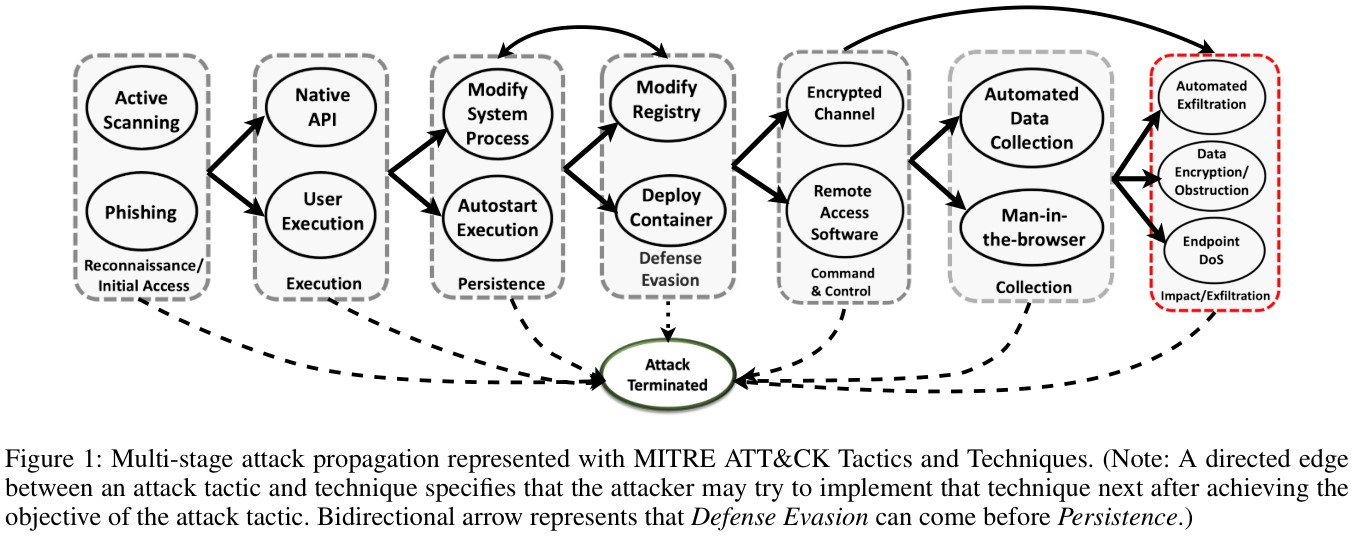
Here, rectangular boxes are tactical stages of an attack, while the ovals within them are techniques that could - if successful - complete that stage and allow the attacker to move on to the next stage.
In their paper, the authors model the behaviour of an automated defender as it tries to block the various stages of the attack. At each stage, the defender does not know which technique the attacker will use next - first of all, the defender may not know all the possible techniques and besides, attackers vary their techniques. Even if it can guess the technique, the specific procedure will be difficult to predict (because of 0day exploits, etc.). In addition, not everything the attacker does may be captured or, if it is, its significance is not known until later.
The game starts in an Attack Initiated state, and the attacker's goal is to get through the stages to the Impact/Exfiltration state (in red above). The defender's goal is to get the game to the Attack Terminated state, which will occur if the attacker runs out of techniques to get to the next stage.
After each attacker action (i.e. procedure - attempted exploit), the defender can choose one of three actions. It can either do nothing, it can react by removing all processes that were used by the attacker in his last attack action, or it can act proactively to block a specific set of API calls or operations in order to prevent the next attack action. However, killing processes and blocking API's is bad for business, and therefore incurs some cost, which the defender will attempt to avoid.
The goal of the automated defender is to develop a policy which recommends the optimal action at each state of the game. It does this using a technique called reinforcement learning, in which it earns a reward (computed by a reward function) for each state - the reward is simply a number which is proportional to how desirable that state is. The defender's goal is to maximise its total rewards in the long run, and it will try to develop a policy in order to do that.
The question is, how to develop that policy? In my own research, I used Bayesian networks to 'learn' the policy, but things have moved on since then, particularly with the emergence of deep learning techniques. In this paper, the authors explored four different Deep Reinforcement Learning approaches - a Deep Q-Network approach (DQN) and three different Actor-Critic approaches.
To run their simulations, they used a fairly grunty Alienware machine (16-core i7 processor, 64 GB RAM, three NVidia GM200 graphics cards) - but that's actually not that big; the machine I am typing this on is similar, only based on an i9. Their software is written in Python (of course) and running in a customized OpenAI Gym simulation environment (I ran my simulations in Java and C, for performance - less necessary today). Compared to the cost of standing up and manning a SOC, this setup is a bargain.
I'm not going to do a deep dive into the learning parameters or the algorithms involved - here, I'm just interested in the security aspects. But the results are encouraging. Overall, the Deep Q-Network approach did best against a range of simulated attacks as soon as possible, although it fell behind when defending against a more skilled and persistent adversary (Av3), who is more likely to quickly identify the right action and not give up.
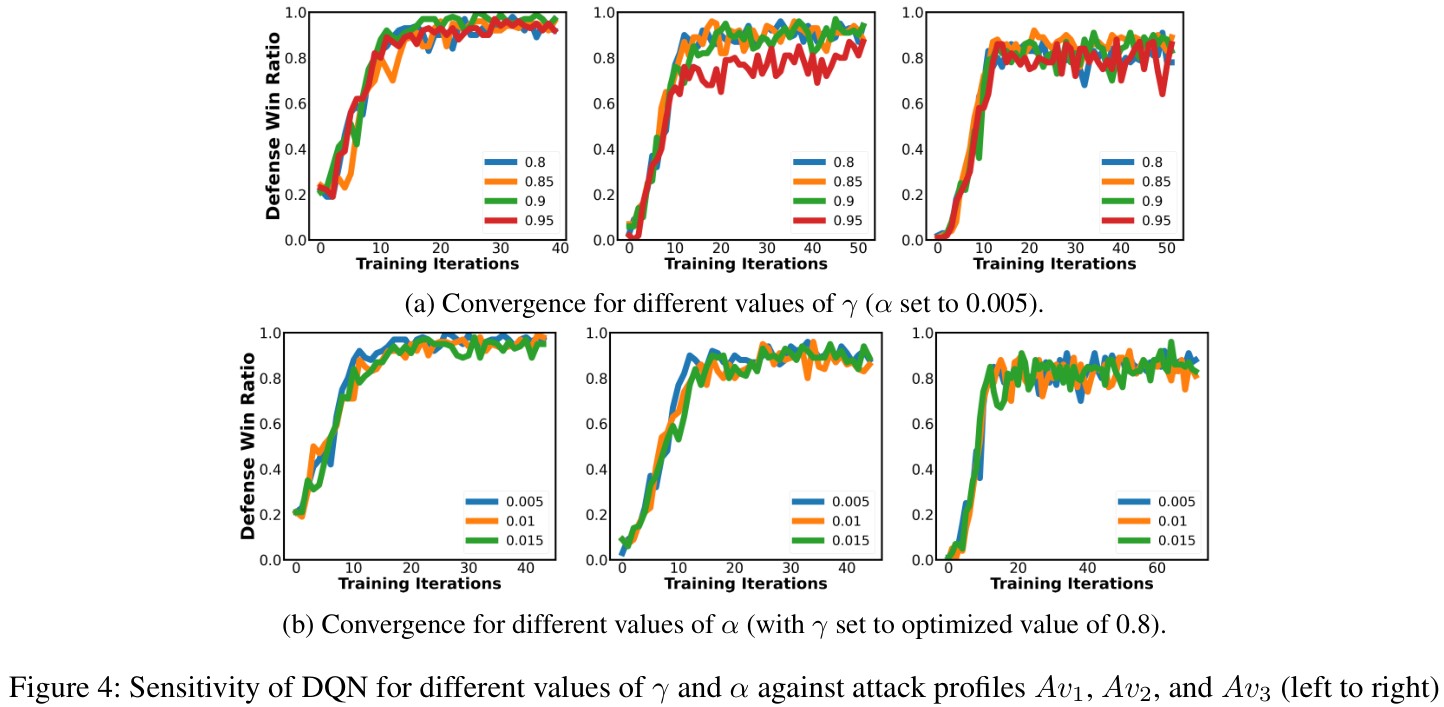
Now, bear in mind this is a simulation based on a relatively small number of tactics and techniques, and modeling the probability of each technique succeeding or failing probabilistically, based on the assumed skill and persistence of the attacker. There were no actual attacks involved, no mining of events from a SIEM, etc - extracting that information from IDS/IPS and SIEM systems is a completely different problem, which others, in both the public and private sectors, are also working on.
But I feel that this type of approach, in which sensors feed event information to a machine learning system which has learned from previous attacks, is likely the way of the future.And bear in mind, this is just one paper, from one group of researchers - there's a lot more going on - but I felt it was worth reporting on, in particular to explain how it relates to other things discussed in our courses.
These developments will take SOAR (Security Orchestration, Automation and Response) to a whole new level. Watch this space.
Dutta, A., Chatterjee, S., Bhattacharya, A., and Halappanavar, M., Deep Reinforcement Learning for Cyber System Defense under Dynamic Adversarial Uncertainties, arXiv, 3 February 2023. Available online at https://arxiv.org/abs/2302.01595.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
MA Town Employee Schools Everyone on Cryptomining
Out of Cohasset, Massachussets comes the cautionary tale of Nadeam Nahas, the town's assistant facilities director - now former assistant facilities directory - who has been charged with fraudulent use of electricity and vandalizing a school, after setting up a secret cryptocurrency mining operation in a remote crawl space in the town's Middle/High School.
Apparently, back in December 2021 Nahas's boss, the town's facilities inspector was conducting a routine inspection of the school when he found electrical wires, temporary duct work, and numerous computers that seemed out of place. He contacted the town's IT director, who determined that it was a cryptomining setup, unlawfully using the school's electrical system. I suspect you'd need more than a few computers to compete with ASIC-based mining rigs, so the theft of electricity could well be significant.
The local police were called, and the Coastguard Investigative Service and Department of Homeland Security assisted with safely removing and examining the equipment. A three-month investigation identified Nahas as a suspect, and after a show-cause hearing, a criminal complaint was issued. He resigned from his job in early 2022, and was due to be arraigned yesterday but did not show up and the judge issued a warrant for his arrest.
Ah, crypto. When will people ever learn . . . ?
Uncredited, Police: Crypto mining operation found in school crawl space, AP News, 23 February 2023. Available online at https://apnews.com/article/massachusetts-c59f30e1736c7409e41357f1ae2e7b93.
Cloud Security: All Your Containers Are Belong to Us?
Cloud security firm Sysdig has produced their "2023 Cloud-Native Security and Usage Report' and the contents make sobering reading. The report is based on "data gathered from billions of containers, thousands of cloud accounts, and hundreds of applications" operated by Sysdig's customers, so it is based on what DevOps people are doing, rather than what they say they are doing.
The two biggest threats to cloud security continue to be misconfigurations and vulnerabilities - which are an increasing threat because they are being introduced into supply chains in ever-greater numbers. Sysdig found that 87% of container images running in production have critical or high severity vulnerabilities.
This suggests that 'shift-left' strategies, which attempt to improve code quality and detect and eliminate vulnerabilities earlier in the software development life cycle (an increasingly nebulous concept in itself) are not working and that enterprises need runtime security technologies. Sysdig cite the example of Falco, a Cloud Native Computing Foundation (CNCF) open-source project they originally created, which helps organizations detect runtime threats across clouds, containers, hosts and Kubernetes environments.
On the up side, it seems that paying attention to supply-chain security will pay off handsomely, allowing developers to focus their remediation efforts on only those vulnerable packages loaded at runtime, which is only 15% of the critical or high severity packages - this seems to be yet another example of the Pareto rule.
In other findings, there is a lot of talk about zero trust, but not much action. The fact that 90% of granted privileges are not used indicates that developers and admins are not applying the principle of least privilege. In practice, 58% of identities are not humans - they are service accounts and often have not been used for over 90 days, or are expired test accounts or third-party accounts which should have been revoked.
Sysdig, Inc., Sysdig 2023 Cloud-Native Security and Usage Report, technical report, January 2023. Available online at https://sysdig.com/2023-cloud-native-security-and-usage-report/.
One Year On, Ukraine Still Not Wiped, Despite Massive Efforts
It's been one year since the beginning of Russia's little adventure in Ukraine. While TV news reports focus on the conventional kinetic warfare - lord knows, it's spectacular enough, and costly in human terms - there has been, of course, a similar cyberwar taking place across the borderless space of the Internet.
Russian state-sponsored threat actors have a long history of unleashing cyber-attacks on the country's former satellites - long-term infosec wonks will remember the 2007 attacks on Estonia's parliament, government ministries and media organizations, and who can forget 2017's NotPetya, a wiper aimed at Ukraine's tax revenues, but which claimed victims all over the world as collateral damage?
Now three security firms - ESET, Fortinet and Mandiant - have all independently found that, in 2022, Ukraine was targeted by more samples of wiper malware than in any previous year - in fact, more than in any year, anywhere. Fortinet counted 16 different 'families' of wiper malware, compared to one or two in previous years, indicating that Russia has assigned a much larger number of developers to wiper development in an attempt to get ahead of Ukraine's hardened defences.
And, just as we saw with NotPetya, these variants are spreading and causing collateral damage around the world, not just directly but as a consequence of other hackers reusing them in 25 different countries, according to Fortinet. However, Russia seems to have traded quality for quantity as it increased its efforts - many of the newly-developed wipers are relatively crude and will be easier to detect and deal with.
Greenberg, Andy, Ukraine Suffered More Data-Wiping Malware Last Year Than Anywhere, Ever, Wired, 22 February 2023. Available online at https://www.wired.com/story/ukraine-russia-wiper-malware/.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
Opinion
A break from the usual round of news briefs; today I've decided to opine on a common topic for discussion or even debate.
Event or Incident? Or is it a Breach? Definitions, definitions . . .
I was recently amused to read a discussion on a security-related forum about whether or not various things that happened on a network were incidents or events. There was much debate, but not much getting to the heart of the matter, i.e. the security implications which might make definitions useful.
In fact, there are no clear definitions of these terms in the cybersecurity field - in part because it is constantly evolving, but also different because regulators tend to define the terms in ways that make sense for their interests, and also because SIEM product vendors do the same thing for their product interfaces.
We could also usefully add the term, 'breach', here.
In the past, and still today, I have been guided by my experience with aviation safety, where regulators generally have very clear definitions which distinguish between an accident and an incident. (Security, to my mind, is very like safety and quality - they all have to be designed in, and cannot be added as an afterthought.)
Take, for example, the US NTSB, for the terms are defined in USC 49 vol 7 section 830.2:
As used in this part the following words or phrases are defined as follows:
- Aircraft accident means an occurrence associated with the operation of an aircraft which takes place between the time any person boards the aircraft with the intention of flight and all such persons have disembarked, and in which any person suffers death or serious injury, or in which the aircraft receives substantial damage. For purposes of this part, the definition of "aircraft accident" includes "unmanned aircraft accident", as defined herein.
- Incident means an occurrence other than an accident, associated with the operation of an aircraft, which affects or could affect the safety of operations.
The term 'occurrence' is not defined, but it is pretty obviously synonymous with event; there are lots of other occurrences or events, but many or most of them are not safety-related.
The Australian Transportation Safety Bureau used (until recently) slightly more granular definitions (ATSB, 2023):
Accident: an occurrence involving an aircraft where:
- a person dies or suffers serious injury
- the aircraft is destroyed, or is seriously damaged
- any property is destroyed or seriously damaged.
Serious incident: an incident involving circumstances indicating that an accident nearly occurred (ICAO Annex 13).
Incident: an occurrence, other than an accident, associated with the operation of an aircraft which affects or could affect the safety of operation (ICAO Annex 13).
(From 1 January 2023 their definitions have been even more specific, but the intent is the same for our purposes.)
The distinction between accident and incident is very clear. So, in the security world, what's an event?
Our systems log an absolute torrent of events and many of them end up in SIEM databases. One obvious difference is that aviation events tend to be noticed by humans (flight crew or cabin crew) - engine failures, instrument failures and the like generally get pilots' attention quickly - whereas computer systems and networks generate torrents of event information, most of which are not security-related. Nonetheless, they need to be logged, because their security significance might only become apparent later, during incident response and analysis.
Which leaves us with 'breach'. Regulators have historically been more concerned with privacy than with the confidentiality of corporate data, leaving companies free to manage risk as they see fit. So, for example, the Office of the Australian Information Commissioner (OAIC, 2022) says,
A data breach happens when personal information is accessed or disclosed without authorisation or is lost.
That's probably not enough for our purposes. Let's fall back on the CIA triad, which defines the three primary security properties of the information we store and process:
- Confidentiality
- Integrity
- Availability
I'd suggest that if any of these properties is compromised (assuming it is one we are trying to protect) then that counts as a breach. It means that our controls have failed (or if there were no controls, that's a failure of security management, which is itself a control).
We might therefore map the aviation safety terms to infosec terms as follows:
| Safety | Security |
|---|---|
| Accident | Breach; compromise of security property of information |
| (Serious Incident) |
(Repeated incidents; repeated attempts to compromise controls by a persistent adversary) |
| Incident | Incident; compromise or attempted compromise of one or more controls |
| Occurrence | Event |
A breach clearly equates to an accident. It means what we were trying to avoid has, despite our efforts, happened. In risk management terms, it's a loss event. Some inicidents unfortunately escalate into breaches - so every breach is an incident.
An incident is an attempt - successful or not - to defeat one or more controls. It indicates an attack and it requires us to respond - which is, of course, where our incident response plans and playbooks enter the picture. The failure of a single control, or even multiple controls, should not result in a breach, especially if we are employing a strategy of cyber resilience or defence in depth. It might be signalled by an IDS/IPS alert, or the SIEM triggering on events, or even after the fact when a batch process analyses logs.
In other words, we expect to have to activate incident response plans before the Bad Guys have achieved their objectives; penetrating just one or two layers of defences should not allow compromise of an information asset.
I've parenthetically inserted a tentative definition of 'serious incident' in the table above, just for completeness. It might be that, having repelled an intrusion attempt, you find that the same attacker tries again, perhaps with a variation of the TTP's that almost worked for them before. This indicates a persistent attacker running a targeted campaign; you may not have had a breach yet, but it's time to harden the security posture considerably. Alternatively, a 'serious incident' might be the failure of a number of controls indicating an underlying system problem that needs attention: something like poor planning, an inadequate budget or perhaps a lack of attention to security education, training and awareness.
A SIEM captures a lot of event information and allows analysts to correlate them as they investigate incidents. Events have meta-features (timestamp, result, affected resources) and features (IP addresses, email addresses, exploits, etc.) and analysts will use techniques like analytic pivoting to identify the other related events, building up a picture of the adversary's tactics, techniques and procedures and extracting indicators of compromise. SOC level 1 analysts will do the initial work of filtering out non-security related events, while level 2 analysts and threat hunters use more advanced techniques.
I would not be so bold as to claim these definitions as authoritative, but I think they - and the related discussion - are useful. I'm going to try to stick to these definitions in my own writing in future. Incidentally, there are many more useful parallels to be usefully drawn between the worlds of aviation safety and cybersecurity, and I may write some more on this topic in the future.
Australian Transportation Safety Bureau, Occurrence category taxonomy and terminology, web page, January 2023. Available online at https://www.atsb.gov.au/avdata/terminology.
Office of the Australian Information Commissioner, Notifiable data breaches, web page, 2022. Available online at https://www.oaic.gov.au/privacy/notifiable-data-breaches.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
Fortinet Proof-of-Concept Released - Update or Mitigate Now!
Horizon3 researchers have released proof-of-concept code for one of two vulnerabilities disclosed by Fortinet last month. CVE-2022-39952 is an "external control of file name or path" vulnerability (CWE-73) in FortiNAC web server which can allow an unauthenticated attacker to upload files to arbitrary locations on the target system, and thereby achieve remote code execution with root privileges. It therefore merited a CVSS score of 9.2
The affected products are:
- FortiNAC version 9.4.0
- FortiNAC version 9.2.0 through 9.2.5
- FortiNAC version 9.1.0 through 9.1.7
- FortiNAC 8.8 all versions
- FortiNAC 8.7 all versions
- FortiNAC 8.6 all versions
- FortiNAC 8.5 all versions
- FortiNAC 8.3 all versions
and there is no mitigation other than upgrading to the next version (9.4.1, 9.2.6, 9.1.8 or 7.2.0 or above).
The Horizon3 researchers simply compared a vulnerable version with a fixed version, and found that a .jsp (Java Servlet Pages) file had been removed, and perusal of that file and a related shell script quickly gave them the exploit. The technique they used was to create a cron job which executes every minute, creating a reverse shell back to the attacker. Once this was put into a ZIP file and uploaded, within a minute they had a reverse shell as root.
Now the Horizon3 code is up on GitHub, it will quickly be adapted and used in the wild. The time to update is now - or at least, remove that vulnerable .jsp page!
Hanley, Zach, Fortinet FortiNAC CVE-2022-39952 Deep-Dive and IOCs, blog post, 21 February 2023. Available online at https://www.horizon3.ai/fortinet-fortinac-cve-2022-39952-deep-dive-and-iocs/.
New InfoStealer Gains Popularity Rapidly
A malware developer going by the name of Plymouth on Russian-speaking forums has released a new infostealer called Stealc, which he claims to have developed from features of the earlier Vidar, Raccoon, Mars and Redline stealers. As a result, Stealc is very polished and highly functional, making it attractive to cybercriminals.
Researchers at SEKOIA.IO first encountered Stealc in January 2023, and during early February they were able to monitor some of its C2 communications - similar to Vidar and Raccoon - and discover several dozen samples of Stealc in the wild, along with over 40 of its C2 servers, indicating that it did, in fact, achieve rapid popularity.
SEKOIA.IO's technical analysis provides detailed insights into this new stealer. By default, Stealc will extract sensitive information from most web browsers, browser extensions for cryptocurrency wallets, desktop crypto wallets and many other applications including email clients and instant messaging. However, Stealc is highly configurable, tailoring its data collection to customer needs. It also has a more general file grabber which can be customised, based on rules, as well as loader capabilities for more advanced exploitation.
SEKOIA.IO's very detailed blog post details their analysis process, as well as what they found. It also provides MITRE ATT&CK TTP's, IOC's and YARA rules.
Threat & Detection Research Team, Stealc: a copycat of Vidar and Raccoon infostealers gaining in popularity – Part 1, blog post, 20 February 2023. Available online at https://blog.sekoia.io/stealc-a-copycat-of-vidar-and-raccoon-infostealers-gaining-in-popularity-part-1/.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
HardBit 2.0 Ransomware Wants to Know About Your Cyber Insurance
Since first appearing in October of last year, the HardBit ransomware has evolved rapidy, with the latest variant, HardBit 2.0, exhibiting some interesting characteristics, according to security firm Varonis.
The HardBit ransom note (Varonis)
In many respects, HardBit 2.0 is conventional; after initial infection - the exact mechanism is unknown; possibly an initial access broker is involved - it does the usual things: first, it gathers system information via the Windows Management Instrumentation API, then it disables the Volume Shadow Copy Service (VSS) and deletes any shadow copies. Next, it disables a list of Windows Defender Antivirus features so it can get to work uninterrupted. It also disables up to 86 different services, including backup and recovery tools and security programs, and also persists by copying itself into the Startup folder.
It then sets about the in-situ encryption of target files, finally changing the desktop to a ransom note image and displaying the main ransom note from a .hta file.
What makes HardBit 2.0 particularly interesting is that while it threatens to release sensitive data, its operators do not seem to have a leak site. Another wrinkle is the lack of a fixed ransom amount: instead asking for details of the victim's cyber insurance coverage. In an attempt to paint insurance companies as the bad guys, the ransom note states:
"Insurance companies require you to keep your insurance information secret, this is to never pay the maximum amount specified in the contract or to pay nothing at all, disrupting negotiations.
"The insurance company will try to derail negotiations in any way they can so that they can later argue that you will be denied coverage because your insurance does not cover the ransom amount."
In practice, insurers are generally felt to have a distorting effect in the ransomware market because of their willingness to pay ransom demands, rather than covering any loss and/or costs of recovery. It's possible the HardBit 2.0 operators want to know when they are onto a sure thing.
The Varonis blog post provides a comprehensive analysis, including indicators of compromise.
Hill, Jason, HardBit 2.0 Ransomware, blog post, 20 February 2023. Available online at https://www.varonis.com/blog/hardbit-2.0-ransomware.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
GoDaddy cPanel Shared Hosting Compromised
Web hosting company and domain registrar GoDaddy has disclosed an attack which has been intermittently redirecting users away from customer web sites. Upon investigation, GoDaddy's admins found the intermittent redirects were happening on seemingly random websites hosted on their cPanel shared hosting servers and were not easily reproducible, even on the same website.
Further investigation uncovered malware, installed by an unauthorized third party who had gained access to servers in the company's cPanel hosting environment. The company claims that "this incident was carried out by a sophisticated and organized group targeting hosting services like GoDaddy. According to information we have received, their apparent goal is to infect websites and servers with malware for phishing campaigns, malware distribution and other malicious activities".
It is unclear how many customers were affected, but previous breach, in November 2021, affected up to 1.2 million customers of the firm's 'Managed WordPress' platform, while the login credentials of approximately 28,000 hosting customers were compromised in March 2020, according to the company's SEC 10-K filing.
Uncredited, Statement on recent website redirect issues, news release, 16 February 2023. Available online at https://aboutus.godaddy.net/newsroom/company-news/news-details/2023/Statement-on-recent-website-redirect-issues/default.aspx.
Twitter Disables SMS Verification (Unless You Want to Pay to Be Insecure)
For several years now, NIST and others have deprecated the use of SMS text messages as a form of account verification. Also known as mTAN's (mobile Transaction Authentication Numbers), these are six-digit numbers which are texted to the user's number in order to verify their logins.
However, these have always been a weak second factor mechanism for authentication. Phone numbers can be ported - all the attacker needs is a little social engineering, dumpster diving or mailbox theft to get the necessary identity paperwork. Phones can be lost or stolen, and text messages intercepted by other means. And most importantly, a one-time code can be intercepted using a proxy or man-in-the-middle phishing attack.
Now Twitter has announced that it will disable the use of SMS verification from 20 March 2023 - except for Twitter Blue customers, who are paying to display that blue mark, and can apparently pay to be lax about security, too.
Seriously, folks: switch to either an authenticator app (Authy, Google Authenticator, etc.) or - better still - a security key such as a YubiKey.
Twitter Inc., An update on two-factor authentication using SMS on Twitter, blog post, 15 February 2023. Available online at https://blog.twitter.com/en_us/topics/product/2023/an-update-on-two-factor-authentication-using-sms-on-twitter.
Apple OK's Security Keys, Too
And while I'm on the topic: Apple has now added support for security keys for Apple ID accounts, too, replacing six-digit security codes for the same reasons.
To use use security keys for your Apple ID, you'll need to be running iOS 16.3, iPadOS 16.3, or macOS Ventura 13.2 (or later) and have two-factor authentication enabled. You'll also need at least two FIDO security keys - these can connect using NFC, USB-C or USB-A, using a Lightning-to-USB-C for phones. You may also need to update any old browser versions.
Uncredited, About Security Keys for Apple ID, support note, 5 February 2023. Available online at https://support.apple.com/en-us/HT213154.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
New Mirai Variant Recruits FreePBX, IP Cameras, Routers and More to Botnet
Palo Alto Networks Unit 42 researchers have produced a report on a new variant of the Mirai botnet, which they have labeled V3G4. The malware is able to infect a victim system using any one of the following vulnerabilities:
- CVE-2012-4869: FreePBX Elastix Remote Command Execution Vulnerability
- Gitorious Remote Command Execution Vulnerability
- CVE-2014-9727: FRITZ!Box Webcam Remote Command Execution Vulnerability
- Mitel AWC Remote Command Execution Vulnerability
- CVE-2017-5173: Geutebruck IP Cameras Remote Command Execution Vulnerability
- CVE-2019-15107: Webmin Command Injection Vulnerability
- Spree Commerce Arbitrary Command Execution Vulnerability
- FLIR Thermal Camera Remote Command Execution Vulnerability
- CVE-2020-8515: DrayTek Vigor Remote Command Execution Vulnerability
- CVE-2020-15415: DrayTek Vigor Remote Command Injection Vulnerability
- CVE-2022-36267: Airspan AirSpot Remote Command Execution Vulnerability
- CVE-2022-26134: Atlassian Confluence Remote Code Execution Vulnerability
- CVE-2022-4257: C-Data Web Management System Command Injection Vulnerability
Once initial access has been gained the malware then uses either the wget or curl commands to download and install the bot, making the infected machine part of the botnet. Once it is running, the bot also examines the system process list and will attempt to kill any rival malware, including other Mirai variants, and then connects to its C2 server using simple XOR encryption with multiple different key strings.
The Unit 42 advisory contains a full analysis as well as IOC's.
Lei, Chao, Zhibin Zhang, Cecilia Hu and Aveek Das, Mirai Variant V3G4 Targets IoT Devices, blog post, 15 February 2023. Available online at https://unit42.paloaltonetworks.com/mirai-variant-v3g4/.
Singapore Researchers Track Sidewinder AP Around South Asia
A new report from Singapore-based Group-IB details the 2021 activities of an advanced persistent threat group called SideWinder, which appears to be based in India, and is also known as Rattlesnake, Hardcore Nationalist (HN2) and T-APT4. Between June and November, SideWinder attacked 61 different government, military, law enforcement and other organizations in Afghanistan, Bhutan, Myanmar, Nepal, and Sri Lanka. Group-IB has also been able to link SideWinder to two other groups, Baby Elephant and Donot.
Like many other groups, Sidewinder primaril gains initial access via a malicious phishing email campaign which contains either a malicious attachment or a URL which in turn downloads a malicious payload - either a reverse shell, a remote access trojan or an infostealer. Sidewinder has developed its own tools for this pupose, such as SideWinder.RAT.b and SideWinder.StealerPy - the latter a custom infostealer designed to gather the user's Chrome browsing history, browser-saved credentials, and a range of filetypes. Like many other groups, SideWinder has switched to using the Telegram messaging app for information exfiltration, because of its convenience.
Kupin, Dmitry, Molted skin: APT SideWinder 2021 campaign that targeted over 60 companies in the Asia-Pacific, press release, 15 February 2023. Available online at https://www.group-ib.com/media-center/press-releases/sidewinder-apt-report/.
Trend Micro Uncovers New Tools and Campaign: Earth Yako
Meanwhile, Trend Micro researchers have been busy analyzing the tactics, techniques and procedures used in several attacks which targeted academics and think-tank members in Japan during 2021. Terming the attacks "Earth Yako", the researchers believe they are part of a campaign called Operation RestyLink or EneLink. A number of new malware tools were observed in these attacks:
- MirrorKey: An in-memory dynamic link library (DLL) loader
- TransBox: A backdoor abusing the Dropbox API
- PlugBox: A Dropbox API-based backdoor with a couple of capabilities
- Dulload: A generic loader
- PULink: A dropper of ShellBox written in C++/CLR, capable of achieving persistence
- ShellBox: Another Dropbox API-based stager written in C#
The initial attack vector is once again spearphishing, with a URL inducing the victim to download a .zip or .iso package, which in turn contains a link to a malicious Microsoft Word template. In some cases, the vicim machine is infected with Cobalt Strike.
Based on the tools and TTP's, it is not possible to definitely attribute Earth Yako to any particular group - it could be North Korean, Chinese or Russian in origin.
Trend Micro's report includes a detailed analysis and IOC's.
Hiroaki, Hara, Yuka Higashi and Masaoki Shoji, Invitation to a Secret Event: Uncovering Earth Yako’s Campaigns, blog post, 16 February 2023. Available online at https://www.trendmicro.com/en_us/research/23/b/invitation-to-secret-event-uncovering-earth-yako-campaigns.html.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.