Les Bell and Associates Pty Ltd
Site blog
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
Opinion
A break from the usual round of news briefs; today I've decided to opine on a common topic for discussion or even debate.
Event or Incident? Or is it a Breach? Definitions, definitions . . .
I was recently amused to read a discussion on a security-related forum about whether or not various things that happened on a network were incidents or events. There was much debate, but not much getting to the heart of the matter, i.e. the security implications which might make definitions useful.
In fact, there are no clear definitions of these terms in the cybersecurity field - in part because it is constantly evolving, but also different because regulators tend to define the terms in ways that make sense for their interests, and also because SIEM product vendors do the same thing for their product interfaces.
We could also usefully add the term, 'breach', here.
In the past, and still today, I have been guided by my experience with aviation safety, where regulators generally have very clear definitions which distinguish between an accident and an incident. (Security, to my mind, is very like safety and quality - they all have to be designed in, and cannot be added as an afterthought.)
Take, for example, the US NTSB, for the terms are defined in USC 49 vol 7 section 830.2:
As used in this part the following words or phrases are defined as follows:
- Aircraft accident means an occurrence associated with the operation of an aircraft which takes place between the time any person boards the aircraft with the intention of flight and all such persons have disembarked, and in which any person suffers death or serious injury, or in which the aircraft receives substantial damage. For purposes of this part, the definition of "aircraft accident" includes "unmanned aircraft accident", as defined herein.
- Incident means an occurrence other than an accident, associated with the operation of an aircraft, which affects or could affect the safety of operations.
The term 'occurrence' is not defined, but it is pretty obviously synonymous with event; there are lots of other occurrences or events, but many or most of them are not safety-related.
The Australian Transportation Safety Bureau used (until recently) slightly more granular definitions (ATSB, 2023):
Accident: an occurrence involving an aircraft where:
- a person dies or suffers serious injury
- the aircraft is destroyed, or is seriously damaged
- any property is destroyed or seriously damaged.
Serious incident: an incident involving circumstances indicating that an accident nearly occurred (ICAO Annex 13).
Incident: an occurrence, other than an accident, associated with the operation of an aircraft which affects or could affect the safety of operation (ICAO Annex 13).
(From 1 January 2023 their definitions have been even more specific, but the intent is the same for our purposes.)
The distinction between accident and incident is very clear. So, in the security world, what's an event?
Our systems log an absolute torrent of events and many of them end up in SIEM databases. One obvious difference is that aviation events tend to be noticed by humans (flight crew or cabin crew) - engine failures, instrument failures and the like generally get pilots' attention quickly - whereas computer systems and networks generate torrents of event information, most of which are not security-related. Nonetheless, they need to be logged, because their security significance might only become apparent later, during incident response and analysis.
Which leaves us with 'breach'. Regulators have historically been more concerned with privacy than with the confidentiality of corporate data, leaving companies free to manage risk as they see fit. So, for example, the Office of the Australian Information Commissioner (OAIC, 2022) says,
A data breach happens when personal information is accessed or disclosed without authorisation or is lost.
That's probably not enough for our purposes. Let's fall back on the CIA triad, which defines the three primary security properties of the information we store and process:
- Confidentiality
- Integrity
- Availability
I'd suggest that if any of these properties is compromised (assuming it is one we are trying to protect) then that counts as a breach. It means that our controls have failed (or if there were no controls, that's a failure of security management, which is itself a control).
We might therefore map the aviation safety terms to infosec terms as follows:
| Safety | Security |
|---|---|
| Accident | Breach; compromise of security property of information |
| (Serious Incident) |
(Repeated incidents; repeated attempts to compromise controls by a persistent adversary) |
| Incident | Incident; compromise or attempted compromise of one or more controls |
| Occurrence | Event |
A breach clearly equates to an accident. It means what we were trying to avoid has, despite our efforts, happened. In risk management terms, it's a loss event. Some inicidents unfortunately escalate into breaches - so every breach is an incident.
An incident is an attempt - successful or not - to defeat one or more controls. It indicates an attack and it requires us to respond - which is, of course, where our incident response plans and playbooks enter the picture. The failure of a single control, or even multiple controls, should not result in a breach, especially if we are employing a strategy of cyber resilience or defence in depth. It might be signalled by an IDS/IPS alert, or the SIEM triggering on events, or even after the fact when a batch process analyses logs.
In other words, we expect to have to activate incident response plans before the Bad Guys have achieved their objectives; penetrating just one or two layers of defences should not allow compromise of an information asset.
I've parenthetically inserted a tentative definition of 'serious incident' in the table above, just for completeness. It might be that, having repelled an intrusion attempt, you find that the same attacker tries again, perhaps with a variation of the TTP's that almost worked for them before. This indicates a persistent attacker running a targeted campaign; you may not have had a breach yet, but it's time to harden the security posture considerably. Alternatively, a 'serious incident' might be the failure of a number of controls indicating an underlying system problem that needs attention: something like poor planning, an inadequate budget or perhaps a lack of attention to security education, training and awareness.
A SIEM captures a lot of event information and allows analysts to correlate them as they investigate incidents. Events have meta-features (timestamp, result, affected resources) and features (IP addresses, email addresses, exploits, etc.) and analysts will use techniques like analytic pivoting to identify the other related events, building up a picture of the adversary's tactics, techniques and procedures and extracting indicators of compromise. SOC level 1 analysts will do the initial work of filtering out non-security related events, while level 2 analysts and threat hunters use more advanced techniques.
I would not be so bold as to claim these definitions as authoritative, but I think they - and the related discussion - are useful. I'm going to try to stick to these definitions in my own writing in future. Incidentally, there are many more useful parallels to be usefully drawn between the worlds of aviation safety and cybersecurity, and I may write some more on this topic in the future.
Australian Transportation Safety Bureau, Occurrence category taxonomy and terminology, web page, January 2023. Available online at https://www.atsb.gov.au/avdata/terminology.
Office of the Australian Information Commissioner, Notifiable data breaches, web page, 2022. Available online at https://www.oaic.gov.au/privacy/notifiable-data-breaches.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
Fortinet Proof-of-Concept Released - Update or Mitigate Now!
Horizon3 researchers have released proof-of-concept code for one of two vulnerabilities disclosed by Fortinet last month. CVE-2022-39952 is an "external control of file name or path" vulnerability (CWE-73) in FortiNAC web server which can allow an unauthenticated attacker to upload files to arbitrary locations on the target system, and thereby achieve remote code execution with root privileges. It therefore merited a CVSS score of 9.2
The affected products are:
- FortiNAC version 9.4.0
- FortiNAC version 9.2.0 through 9.2.5
- FortiNAC version 9.1.0 through 9.1.7
- FortiNAC 8.8 all versions
- FortiNAC 8.7 all versions
- FortiNAC 8.6 all versions
- FortiNAC 8.5 all versions
- FortiNAC 8.3 all versions
and there is no mitigation other than upgrading to the next version (9.4.1, 9.2.6, 9.1.8 or 7.2.0 or above).
The Horizon3 researchers simply compared a vulnerable version with a fixed version, and found that a .jsp (Java Servlet Pages) file had been removed, and perusal of that file and a related shell script quickly gave them the exploit. The technique they used was to create a cron job which executes every minute, creating a reverse shell back to the attacker. Once this was put into a ZIP file and uploaded, within a minute they had a reverse shell as root.
Now the Horizon3 code is up on GitHub, it will quickly be adapted and used in the wild. The time to update is now - or at least, remove that vulnerable .jsp page!
Hanley, Zach, Fortinet FortiNAC CVE-2022-39952 Deep-Dive and IOCs, blog post, 21 February 2023. Available online at https://www.horizon3.ai/fortinet-fortinac-cve-2022-39952-deep-dive-and-iocs/.
New InfoStealer Gains Popularity Rapidly
A malware developer going by the name of Plymouth on Russian-speaking forums has released a new infostealer called Stealc, which he claims to have developed from features of the earlier Vidar, Raccoon, Mars and Redline stealers. As a result, Stealc is very polished and highly functional, making it attractive to cybercriminals.
Researchers at SEKOIA.IO first encountered Stealc in January 2023, and during early February they were able to monitor some of its C2 communications - similar to Vidar and Raccoon - and discover several dozen samples of Stealc in the wild, along with over 40 of its C2 servers, indicating that it did, in fact, achieve rapid popularity.
SEKOIA.IO's technical analysis provides detailed insights into this new stealer. By default, Stealc will extract sensitive information from most web browsers, browser extensions for cryptocurrency wallets, desktop crypto wallets and many other applications including email clients and instant messaging. However, Stealc is highly configurable, tailoring its data collection to customer needs. It also has a more general file grabber which can be customised, based on rules, as well as loader capabilities for more advanced exploitation.
SEKOIA.IO's very detailed blog post details their analysis process, as well as what they found. It also provides MITRE ATT&CK TTP's, IOC's and YARA rules.
Threat & Detection Research Team, Stealc: a copycat of Vidar and Raccoon infostealers gaining in popularity – Part 1, blog post, 20 February 2023. Available online at https://blog.sekoia.io/stealc-a-copycat-of-vidar-and-raccoon-infostealers-gaining-in-popularity-part-1/.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
HardBit 2.0 Ransomware Wants to Know About Your Cyber Insurance
Since first appearing in October of last year, the HardBit ransomware has evolved rapidy, with the latest variant, HardBit 2.0, exhibiting some interesting characteristics, according to security firm Varonis.
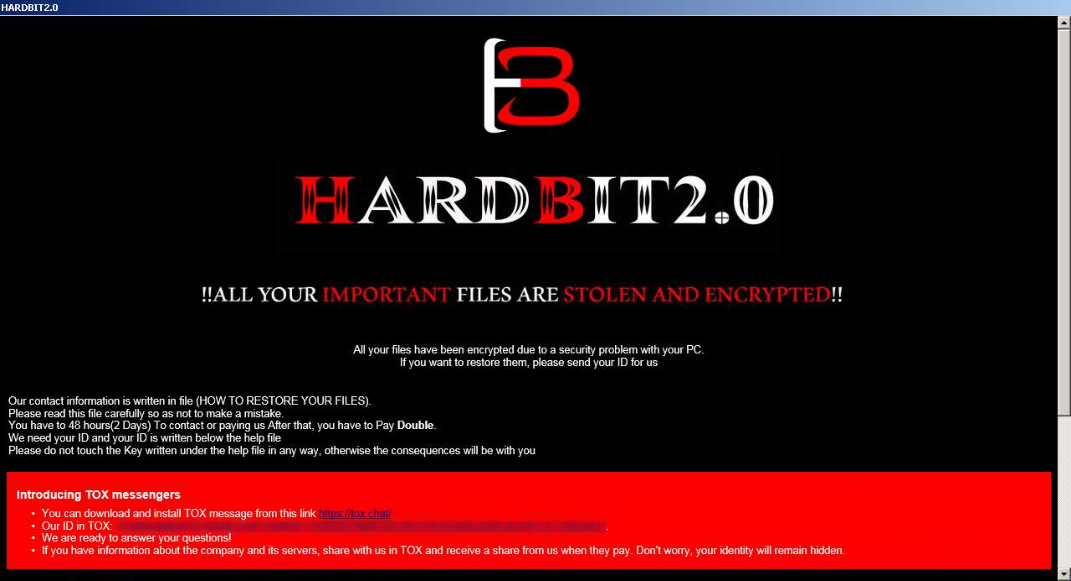
The HardBit ransom note (Varonis)
In many respects, HardBit 2.0 is conventional; after initial infection - the exact mechanism is unknown; possibly an initial access broker is involved - it does the usual things: first, it gathers system information via the Windows Management Instrumentation API, then it disables the Volume Shadow Copy Service (VSS) and deletes any shadow copies. Next, it disables a list of Windows Defender Antivirus features so it can get to work uninterrupted. It also disables up to 86 different services, including backup and recovery tools and security programs, and also persists by copying itself into the Startup folder.
It then sets about the in-situ encryption of target files, finally changing the desktop to a ransom note image and displaying the main ransom note from a .hta file.
What makes HardBit 2.0 particularly interesting is that while it threatens to release sensitive data, its operators do not seem to have a leak site. Another wrinkle is the lack of a fixed ransom amount: instead asking for details of the victim's cyber insurance coverage. In an attempt to paint insurance companies as the bad guys, the ransom note states:
"Insurance companies require you to keep your insurance information secret, this is to never pay the maximum amount specified in the contract or to pay nothing at all, disrupting negotiations.
"The insurance company will try to derail negotiations in any way they can so that they can later argue that you will be denied coverage because your insurance does not cover the ransom amount."
In practice, insurers are generally felt to have a distorting effect in the ransomware market because of their willingness to pay ransom demands, rather than covering any loss and/or costs of recovery. It's possible the HardBit 2.0 operators want to know when they are onto a sure thing.
The Varonis blog post provides a comprehensive analysis, including indicators of compromise.
Hill, Jason, HardBit 2.0 Ransomware, blog post, 20 February 2023. Available online at https://www.varonis.com/blog/hardbit-2.0-ransomware.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
GoDaddy cPanel Shared Hosting Compromised
Web hosting company and domain registrar GoDaddy has disclosed an attack which has been intermittently redirecting users away from customer web sites. Upon investigation, GoDaddy's admins found the intermittent redirects were happening on seemingly random websites hosted on their cPanel shared hosting servers and were not easily reproducible, even on the same website.
Further investigation uncovered malware, installed by an unauthorized third party who had gained access to servers in the company's cPanel hosting environment. The company claims that "this incident was carried out by a sophisticated and organized group targeting hosting services like GoDaddy. According to information we have received, their apparent goal is to infect websites and servers with malware for phishing campaigns, malware distribution and other malicious activities".
It is unclear how many customers were affected, but previous breach, in November 2021, affected up to 1.2 million customers of the firm's 'Managed WordPress' platform, while the login credentials of approximately 28,000 hosting customers were compromised in March 2020, according to the company's SEC 10-K filing.
Uncredited, Statement on recent website redirect issues, news release, 16 February 2023. Available online at https://aboutus.godaddy.net/newsroom/company-news/news-details/2023/Statement-on-recent-website-redirect-issues/default.aspx.
Twitter Disables SMS Verification (Unless You Want to Pay to Be Insecure)
For several years now, NIST and others have deprecated the use of SMS text messages as a form of account verification. Also known as mTAN's (mobile Transaction Authentication Numbers), these are six-digit numbers which are texted to the user's number in order to verify their logins.
However, these have always been a weak second factor mechanism for authentication. Phone numbers can be ported - all the attacker needs is a little social engineering, dumpster diving or mailbox theft to get the necessary identity paperwork. Phones can be lost or stolen, and text messages intercepted by other means. And most importantly, a one-time code can be intercepted using a proxy or man-in-the-middle phishing attack.
Now Twitter has announced that it will disable the use of SMS verification from 20 March 2023 - except for Twitter Blue customers, who are paying to display that blue mark, and can apparently pay to be lax about security, too.
Seriously, folks: switch to either an authenticator app (Authy, Google Authenticator, etc.) or - better still - a security key such as a YubiKey.
Twitter Inc., An update on two-factor authentication using SMS on Twitter, blog post, 15 February 2023. Available online at https://blog.twitter.com/en_us/topics/product/2023/an-update-on-two-factor-authentication-using-sms-on-twitter.
Apple OK's Security Keys, Too
And while I'm on the topic: Apple has now added support for security keys for Apple ID accounts, too, replacing six-digit security codes for the same reasons.
To use use security keys for your Apple ID, you'll need to be running iOS 16.3, iPadOS 16.3, or macOS Ventura 13.2 (or later) and have two-factor authentication enabled. You'll also need at least two FIDO security keys - these can connect using NFC, USB-C or USB-A, using a Lightning-to-USB-C for phones. You may also need to update any old browser versions.
Uncredited, About Security Keys for Apple ID, support note, 5 February 2023. Available online at https://support.apple.com/en-us/HT213154.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
New Mirai Variant Recruits FreePBX, IP Cameras, Routers and More to Botnet
Palo Alto Networks Unit 42 researchers have produced a report on a new variant of the Mirai botnet, which they have labeled V3G4. The malware is able to infect a victim system using any one of the following vulnerabilities:
- CVE-2012-4869: FreePBX Elastix Remote Command Execution Vulnerability
- Gitorious Remote Command Execution Vulnerability
- CVE-2014-9727: FRITZ!Box Webcam Remote Command Execution Vulnerability
- Mitel AWC Remote Command Execution Vulnerability
- CVE-2017-5173: Geutebruck IP Cameras Remote Command Execution Vulnerability
- CVE-2019-15107: Webmin Command Injection Vulnerability
- Spree Commerce Arbitrary Command Execution Vulnerability
- FLIR Thermal Camera Remote Command Execution Vulnerability
- CVE-2020-8515: DrayTek Vigor Remote Command Execution Vulnerability
- CVE-2020-15415: DrayTek Vigor Remote Command Injection Vulnerability
- CVE-2022-36267: Airspan AirSpot Remote Command Execution Vulnerability
- CVE-2022-26134: Atlassian Confluence Remote Code Execution Vulnerability
- CVE-2022-4257: C-Data Web Management System Command Injection Vulnerability
Once initial access has been gained the malware then uses either the wget or curl commands to download and install the bot, making the infected machine part of the botnet. Once it is running, the bot also examines the system process list and will attempt to kill any rival malware, including other Mirai variants, and then connects to its C2 server using simple XOR encryption with multiple different key strings.
The Unit 42 advisory contains a full analysis as well as IOC's.
Lei, Chao, Zhibin Zhang, Cecilia Hu and Aveek Das, Mirai Variant V3G4 Targets IoT Devices, blog post, 15 February 2023. Available online at https://unit42.paloaltonetworks.com/mirai-variant-v3g4/.
Singapore Researchers Track Sidewinder AP Around South Asia
A new report from Singapore-based Group-IB details the 2021 activities of an advanced persistent threat group called SideWinder, which appears to be based in India, and is also known as Rattlesnake, Hardcore Nationalist (HN2) and T-APT4. Between June and November, SideWinder attacked 61 different government, military, law enforcement and other organizations in Afghanistan, Bhutan, Myanmar, Nepal, and Sri Lanka. Group-IB has also been able to link SideWinder to two other groups, Baby Elephant and Donot.
Like many other groups, Sidewinder primaril gains initial access via a malicious phishing email campaign which contains either a malicious attachment or a URL which in turn downloads a malicious payload - either a reverse shell, a remote access trojan or an infostealer. Sidewinder has developed its own tools for this pupose, such as SideWinder.RAT.b and SideWinder.StealerPy - the latter a custom infostealer designed to gather the user's Chrome browsing history, browser-saved credentials, and a range of filetypes. Like many other groups, SideWinder has switched to using the Telegram messaging app for information exfiltration, because of its convenience.
Kupin, Dmitry, Molted skin: APT SideWinder 2021 campaign that targeted over 60 companies in the Asia-Pacific, press release, 15 February 2023. Available online at https://www.group-ib.com/media-center/press-releases/sidewinder-apt-report/.
Trend Micro Uncovers New Tools and Campaign: Earth Yako
Meanwhile, Trend Micro researchers have been busy analyzing the tactics, techniques and procedures used in several attacks which targeted academics and think-tank members in Japan during 2021. Terming the attacks "Earth Yako", the researchers believe they are part of a campaign called Operation RestyLink or EneLink. A number of new malware tools were observed in these attacks:
- MirrorKey: An in-memory dynamic link library (DLL) loader
- TransBox: A backdoor abusing the Dropbox API
- PlugBox: A Dropbox API-based backdoor with a couple of capabilities
- Dulload: A generic loader
- PULink: A dropper of ShellBox written in C++/CLR, capable of achieving persistence
- ShellBox: Another Dropbox API-based stager written in C#
The initial attack vector is once again spearphishing, with a URL inducing the victim to download a .zip or .iso package, which in turn contains a link to a malicious Microsoft Word template. In some cases, the vicim machine is infected with Cobalt Strike.
Based on the tools and TTP's, it is not possible to definitely attribute Earth Yako to any particular group - it could be North Korean, Chinese or Russian in origin.
Trend Micro's report includes a detailed analysis and IOC's.
Hiroaki, Hara, Yuka Higashi and Masaoki Shoji, Invitation to a Secret Event: Uncovering Earth Yako’s Campaigns, blog post, 16 February 2023. Available online at https://www.trendmicro.com/en_us/research/23/b/invitation-to-secret-event-uncovering-earth-yako-campaigns.html.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
Russian Businessman Convicted in $US90 Million Hacking and Wire Fraud Case
The US DoJ has secured the conviction of a Russian businessman for his part in a sophisticated fraud which involved hacking to gain confidential information about the financial performance of publicly-listed US companies, and then using that information to perform stockmarket trades which netted him and his co-conspirators $US90 million.
Vladislav Klyushin,was charged along with Ivan Ermakov and Nikolai Rumiantcev. Klyushin was owner of M-13, a Moscow-based company which offered penetration testing and "Advanced Persistent Threat (APT) emulation" services and counted as clients “the Administration of the President of the Russian Federation, the Government of the Russian Federation, federal ministries and departments, regional state executive bodies, commercial companies and public organizations”, according to the company web site.
Between January 2018 and September 2020, the three, along with Mikhail Vladomirovich Irzak and Igor Sergeevich Sladkov, repeatedly hacked into the networks of two US-based filing agencies in order to obtain unreleased earnings information such as quarterly and annual filings. Knowing whether a company would meet, exceed or fall short of market expectations for its performance, the conspirators could predict whether its share price would rise or fall following the public earnings announcement, and used this to trade via accounts they opened in Cyprus, Portugal, Russia, the US and elsewhere. Klyushin also invested the money of several investors in this scheme, taking 60% of the profits.
While his co-conspirators remain at large, Klyushin was arrested in Sion, Switzerland in March 2021 and extradited to the US in December of that year. Having been convicted of charges of conspiring to obtain unauthorized access to computers, to commit wire fraid and to commit securities fraud - charges which attract significant jail time and fines - Klyushin will be sentenced on 4 May 2023.
US Attorney's Office for the District of Massachussets, Russian Businessman Found Guilty in $90 Million Hack-to-Trade Conspiracy, press release, 14 December 2023. Available online at https://www.justice.gov/usao-ma/pr/russian-businessman-found-guilty-90-million-hack-trade-conspiracy.
New Dropper Beeps to Avoid Sandbox Detection
Some new malware samples analyzed by Minerva researchers exhibit some interesting techniques, particularly for evading forensic analysis. The samples, which were uploaded to VirusTotal as DLL, GIF or JPG files, were flagged as 'spreader' or 'detect-debug-environment', and appear to be droppers, but are most interesting for their extensive use of evasion techniques.
The malware dropper component creates some registry keys, one of which contains a PowerShell script that uses curl.exe to fetch a DLL and then executes it using regsvr32.exe. This, in turn, injects its malicious payload into a legitimate WWAHost.exe process, using process hollowing. That payload then contacts a C2 server, uploading information about the victim machine and waiting for further commands. Unfortunately, the C2 server was down, which stalled Minerva's analysis, although they did identify a number of commands, many of them as yet unimplemented.
The various stages implement increasing levels of antiforensic evasion techniques, some of them repeated across the stages, including dynamic string deobfuscation, checking the system default language (to avoid infecting 'friendly' nations), checking for the presence of a debugger, using the RDTSC instruction to ensure a minimum number of CPU ticks have occurred since the processor was last reset, manipulating the stack segment register to see if the code is being single-stepped under a debugger, using the CPUID instruction to check for a VMware hypervisor, checking the registry for a VBOX key and - this is the technique that gets the malware its new name - calling the Beep API to delay execution.
Generally, malware uses the Sleep API to delay execution, avoiding detection by sandboxes. However, the Beep API - a holdover from the days of the original IBM PC and PC DOS - generates a simple beep tone on the system speaker and does not return until the sound finishes, achieving the same result in a less obvious way. Hence the monicker, Beep malware.
Zargarov, Natalie, Beepin’ Out of the Sandbox: Analyzing a New, Extremely Evasive Malware, blog post, 13 February 2023. Available online at https://minerva-labs.com/blog/beepin-out-of-the-sandbox-analyzing-a-new-extremely-evasive-malware/.
Pepsi Bottler Hacked, Employee Personal Information Stolen
For almost a month over the Christmas period, hackers had penetrated the systems of Pepsi Bottling Ventures, the largest privately-owned bottler of PepsiCo soft drinks in the US, and were able to exfiltrate personally identifiable information from the network. The breach was discovered on 10 January 2023, but another nine days went by before the company's systems were fully secured.
The information stolen is almost a hacker's wishlist for committing identity fraud:
- Full name and home address
- Financial account information, including passwords, PIN's and access numbers
- State and Federal government-issued ID numbers and drivers licence numbers
- ID card data
- Social security numbers
- Passport information
- Digital signatures
- Employee benefit information, including health insurance claims and medical history
The information stolen seems to relate to company employees; it is not clear whether any customers or business parters are affected.
Cluley, Graham, Gulp! Pepsi hack sees personal information stolen by data-stealing malware, blog post, 15 February 2023. Available online at https://www.bitdefender.com/blog/hotforsecurity/gulp-pepsi-hack-sees-personal-information-stolen-by-data-stealing-malware/.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
Massive Patchday
Whether you know it as 'Patch Tuesday' (in the Western Hemisphere) or 'Patch Wednesday' (for those in the Eastern Hemisphere, closer to the Date Line), today was a massive day for patch releases, with Miscrosoft, the Mozilla Firefox project, Citrix and Adobe all releasing security updates. Enterprise security teams will doubtless be busy testing patches before rolling them out; individual users, crying "Full speed ahead and damn the torpedoes!" will be running Windows Update and checking for updates on other products before rebooting.
| Vendor | Product | Update Reference |
|
|---|---|---|---|
| Microsoft |
Windows 10 versions 20H2, 21H1, 21H2, 22H2 |
KB5022834 | |
|
KB5011836 | ||
| Windows 11 version 22H2 |
KB5022845 |
||
| Mozilla | Firefox 110 |
Security Advisory 2023-05 |
|
| Firefox ESR 102.8 |
Security Advisory 2023-06 |
||
| Citrix |
Citrix Workspace app for Linux | Security Bulletin for CVE-2023-24486 | |
| Citrix Workspace app for Windows | Security Bulletin for CVE-2023-24484 & CVE-2023-24485 | ||
| Citrix Virtual Apps and Desktops | Security Bulletin for CVE-2023-24483 | ||
| Adobe | After Effects |
APSB23-02 | |
| Connect | APSB23-05 | ||
| FrameMaker | APSB23-06 | ||
| Bridge | APSB23-09 | ||
| Photoshop | APSB23-11 | ||
| InDesign | APSB23-12 | ||
| Premiere Rush |
APSB23-14 | ||
| Animate | APSB23-15 | ||
| Substance 3D Stager |
APSB23-16 |
You know what to do. . .
CISA Adds Four Known Exploited Vulnerabilities
Meanwhile the Cybersecurity & Infrastructure Security Agency has added four new vulnerabilities to its catalogue of known exploited vulnerabilities (https://www.cisa.gov/known-exploited-vulnerabilities-catalog).
The additions are:
- CVE-2023-21715, a MS Office security feature bypass vulnerability which allows an attacker to trick an authenticated user into letting an Office macro run from an untrusted file
- CVE-2023-22376, a vulnerability in the Windows Common Log File System Driver which allows privilege escalation attacks
- CVE-2023-23529, a type confusion vulnerability in Apple WebKit (present in multiple products) which may allow remote code execution
- CVE-2023-21823, a privilege escalation vulnerability in Microsoft Windows Graphic Component
Check with the relevant vendors for patches.
CISA, CISA Adds Four Known Exploited Vulnerabilities to Catalog, alert, 14 February 2023. Available online at https://www.cisa.gov/uscert/ncas/current-activity/2023/02/14/cisa-adds-four-known-exploited-vulnerabilities-catalog.
Another ICS Security Wakeup Call
A new report from Forescout's Vedere Labs research group provides yet another example of the lagging state of security for Industrial Control Systems (ICS), also referred to as Operational Technology (OT). These systems, which are used in industries ranging from manufacturing and mining to power generation and wastewater treatment, have traditionally been based on unintelligent devices connected via specialized and obscure protocols. However, those unintelligent devices are now based on embedded systems processors which run off-the-shelf operating systems and understand TCP/IP protocols so that they can connect to business systems. Programmable Logic Controllers (PLC's) are a good example - when introduced back in 1968 these were based on simple dedicated logic, but today they use industry-standard processors and embedded OS's such as Android and Linux.
ICS networks are often segmented into 'zones' linked by 'conduits', which are firewall-like controls that understand ICS/SCADA protocols and which form a security perimeter for each zone. PLC's are often used for this purpose, and because ICS security research has focused on compromising such devices and controlling the connected actuators, researchers have not fully considered post-exploitation techniques such as lateral pivoting between zones. That is what Vedere Labs set out to investigate.
The report presents:
- Two new vulnerabilities in Schneider Electric Modicon PLC's, which allow remote code execution and authentication bypass
- An overview of lateral movement techniques using control devices
- A realistic attack scenario which could physically damage a movable bridge
- In-depth discussion and demonstration of remote code execution and laterial movement proof-of-concept using the exploits above
- Conclusions and suggested mitigation techniques
The 41-page report is dense, but makes interesting reading, especially for those with some engineering background. Readers in critical infrastructure enterprises should take note.
Wetzels, Jos, Deep Lateral Movement in OT Networks: When Is a Perimeter Not a Perimeter?, technical report, 13 February 2023. Available online at https://www.forescout.com/resources/l1-lateral-movement-report/.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
Valentine's Day - For the Scammers in Your Life
Yesterday we brought you the US FTC's latest update on the statistics and the favourite lies of romance scammers. This was by way of warning for today's big event, but now comes another warning: Valentine's Day is always accompanies by a wave of scam emails targeting the emotionally vulnerable.
Bitdefender reports that roughly 83% of Valentine-themed spam emails in recent weeks were marked as scams, peaking during the last week. Although scammers predominantly targeted the US (45% of reports), they covered Europe, Asia-Pacific and Australia for good measure - although Ireland, with 7% of reports, seems disproportionately victimized.
Spam email subjects covered a range of lures:
- the perfect romantic rose bear gift is here to ensure your loved one feels truly loved
- up to 93 off canvas sales valentine's day
- spice up your life with a new romance
- 15 bottles of wine to celebrate valentine s day
- confirmation receipt 100 valentine s day gifts
- ukrainian woman are near you date them for valentine
- Gentlemen, Are You Ready For Valentine's Day?
In some cases, the scammers were offering those last-minute or good-value gifts, while others were obviously intended to capture the interest of the lonely and dateless.
The blog post contains a number of samples which might be useful in awareness sessions.
Bîzgă, Alina, What’s love got to do with it? 4 in 5 Valentine’s Day-themed spam emails are scams, Bitdefender Antispam Lab warns, blog post, 14 February 2023. Available online at https://www.bitdefender.com/blog/hotforsecurity/whats-love-got-to-do-with-it-4-in-5-valentines-day-themed-spam-emails-are-scams-bitdefender-antispam-lab-warns/.
Cloudflare Blocks Record HTTP DDoS Attack
Last weekend, DDoS mitigation firm Cloudflare really earned their pay, detecting and mitigating dozes of what they term hyper-volumetric DDoS attacks. The majority of these attacks peaked at around 50 to 70 million HTTP requests per second (rps) with the largest exceeding 71 million rps - the largest such attack reported to date, over 35% higher than the previous record of 46 million rps in June 2022.
For most web servers, every HTTP request will invoke some code - most commonly PHP, but also node.js JavaScript code, .NET or Java. This may in turn invoke other subsystems - middleware, databases, API's on other servers - all committing resources such as memory, CPU cycles and network, and taking time. The objective here is not to consume bandwidth and fill the victim's upstream pipe - it is to consume resources.
In this case, the targeted sites included a gaming provider, cryptocurrency companies, hosting providers and cloud computing platforms; the latter can generally scale well to handle such attacks - but unless customers have quotas in place, they could face massive bills for such attacks. The requests were delivered over HTTP/2 and originated from over 30,000 IP addresses, mostly administered by multiple cloud providers. In light of this and previous attacks from cloud provider addresses, Cloudflare will be providing eligible service providers with a free botnet threat intelligence feed about their own IP address space.
This weekend's activity is no surprise; DDoS attacks have been increasing in size, sophistication and frequency, particularly with the growth of relatively inexpensive DDoS-as-a-service platforms run by cybercriminals. HTTP DDoS attacks have been growing by an average of 79% year on year; even worse, the number of volumetric attacks - those exceeding 100 Gbps - has grown by 67% quarter on quarter, and attacks that last more than three hours has grown by 87% quarter on quarter.
Yoachimik, Omer, Julien Desgats and Alex Forster, Cloudflare mitigates record-breaking 71 million request-per-second DDoS attack, blog post, 14 February 2023. Available online at https://blog.cloudflare.com/cloudflare-mitigates-record-breaking-71-million-request-per-second-ddos-attack/.
Google Agrees with DHS/CISA: Companies Need to Step Up
Some readers will think, 'Finally! Somebody gets it!' in response to this story, while others will not like it at all. But the US Department of Homeland Security thinks that tech companies should be held accountable for security vulnerabilities and the consequential breaches - and Google agrees.
In an opinion piece for Foreign Affairs (paywalled), Jen Easterly, Director of the Cybersecurity & Infrastructure Security Agency with the Department of Homeland Security, and Eric Goldstein, Executive Assistant Director, wrote:
“The incentives for developing and selling technology have eclipsed customer safety in importance. […] Americans…have unwittingly come to accept that it is normal for new software and devices to be indefensible by design. They accept products that are released to market with dozens, hundreds, or even thousands of defects. They accept that the cybersecurity burden falls disproportionately on consumers and small organizations, which are often least aware of the threat and least capable of protecting themselves.”
Their argument is that tracking, identifying, arresting and prosecuting cybercriminals such as ransomware operators is only addressing a symptom. In fact, cybercrime remains relatively low-risk, due to cross-border jurisdictional issues and the difficulties of securing convictions. By comparison with armed robbery or even burglary, it's a walk in the park with much higher returns.
Criminal syndicates now operate like businesses, on a massive scale; while some operate at the premium end of the market, developing 0days and exploiting them against highly-defended targets, the majority work in the commodity market, routinely exploiting well-known vulnerabilities that remain unpatched - either because no patch exists, no patching mechanism exists, or patch distribution, testing and deployment is poorly managed.
Add to that rapidly-evolving technology that rewards companies for being first to market with a minimum viable product, and which favours innovative functionality over security. Compounding the problem is a massive market that sells 'solutions' - products and services that aim to add security to complex and fragile systems. The result - well, you can see it every day, and it may well pay your wages.
As Google's blog post points out, the answer is to incentivize companies to pay attention to the security architects' mantras: secure by default and secure by design. We need to shift resources left, from incident response to engineering security into the software development process. I love this quote, which I originally encountered as part of the philosophy of test pilots - who are primarily engineers, not daredevils, and who are to aviation what testers are to software, only with a lot more skin in the game:
"The object of the game, gentlemen, is not to cheat death: the object is not to let him play."
Patrick Poteen, Sgt. U.S. Army
If the software industry doesn't embed this idea culturally as a core value, it is likely that governments - operating collaboratively and internationally - will start to legislate it in ways that we may not want at all.
We're going to have to up our game.
Easterly, Jen and Eric Goldstein, Stop Passing the Buck on Cybersecurity: Why Companies Must Build Safety Into Tech Products, Foreign Affairs, 1 February 2023. Available online at https://www.foreignaffairs.com/united-states/stop-passing-buck-cybersecurity.
Walker, Kent and Royal Hansen, The US Government says companies should take more responsibility for cyberattacks. We agree, blog post, 13 February 2023. Available online at https://security.googleblog.com/2023/02/the-us-government-says-companies-should.html.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
Reddit Breached; Basic MFA Not Much Help
The big news of the weekend was the breach of internal systems at Reddit by an as-yet-unidentified attacker. According to the site, the initial access mechanism was "a sophisticated and highly-targeted phishing attack". However, they then go on to say,
As in most phishing campaigns, the attacker sent out plausible-sounding prompts pointing employees to a website that cloned the behavior of our intranet gateway, in an attempt to steal credentials and second-factor tokens.
In other words, this was a proxy or man-in-the-middle attack which captured a user's password and 2FA token of some kind. They go on to say,
Soon after being phished, the affected employee self-reported, and the Security team responded quickly, removing the infiltrator’s access and commencing an internal investigation. Similar phishing attacks have been recently reported. We’re continuing to investigate and monitor the situation closely and working with our employees to fortify our security skills. As we all know, the human is often the weakest part of the security chain.
Aye, and there's the rub. In this case, the use of a second factor did not prevent the breach, and what detected it was the humble Mark I human eyeball. This illustrates the continued importance of security education, training and awareness; MFA products alone will not solve the problem. Security is a process, not a product.
Reddit's incident disclosure provides the usual advice: set up MFA (yes), change your password frequently (not such a good idea - it leads to weak passwords) and use a password manager (yes). However, I think security architects and developers need to pick up some of the load by a) providing more contextual information and clues in login dialogs, to alert users to spoofing, and b) moving to cryptographic techniques that can detect MitM attacks, like SSH and TLS can.
Fortunately for Reddit and Redditors, only limited data was exfiltrated, and there is nothing - so far - to suggest that users' personal data or credentials have been compromised.
After successfully obtaining a single employee’s credentials, the attacker gained access to some internal docs, code, as well as some internal dashboards and business systems. We show no indications of breach of our primary production systems (the parts of our stack that run Reddit and store the majority of our data).
So far.
u/KeyserSosa, We had a security incident. Here's what we know., Reddit post, 10 February 2023. Available online at https://www.reddit.com/r/reddit/comments/10y427y/we_had_a_security_incident_heres_what_we_know/.
Romance Scammers Analyzed
This is not really enterprise infosec - but it's a conversational morsel that can be used to open that conversation with employees. Remember, employees may not be strongly vested in protecting corporate data - but they have a strong interest in privacy which can cause their ears to prick up. And having talked about ways to spot a romance scammer, you could move the conversation on - to the clues that signal a phishing attack.
The US Federal Trade Commission has released a fascinating article in their Data Spotlight series, this time dealing with romance scammers, and in particular, their favourite lies. The statistics are quite staggering: in 2022, nearly 70,000 people reported a romance scam, and reported losses totaled $US1.3 billion - and that's just in the US alone. The median reported loss was $US4,400, but some will obviously be much higher, and it's worth reflecting that an employee under the pressure of financial loss may turn to fraud or larceny - yet another reason to cover this in security awareness sessions.
The scammers have developed a short list of buttons they can push to get their payout, and the article lists the most popular:
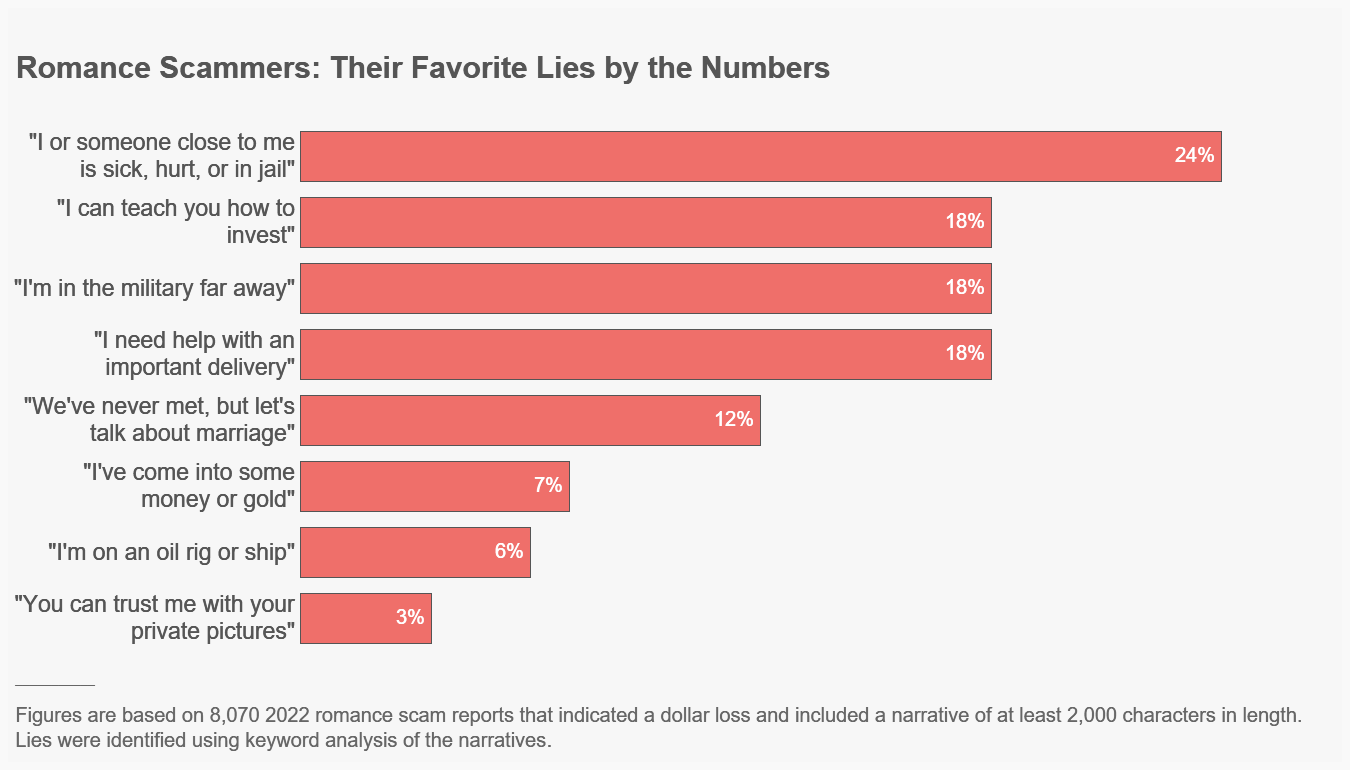
Of course, the scammers also need a way - preferably a non-reversible way - to transfer their ill-gotten gains. Gift cards are a perennial favourite, but for larger amounts, cryptocurrencies are now the method of choice, followed by bank wire transfers:
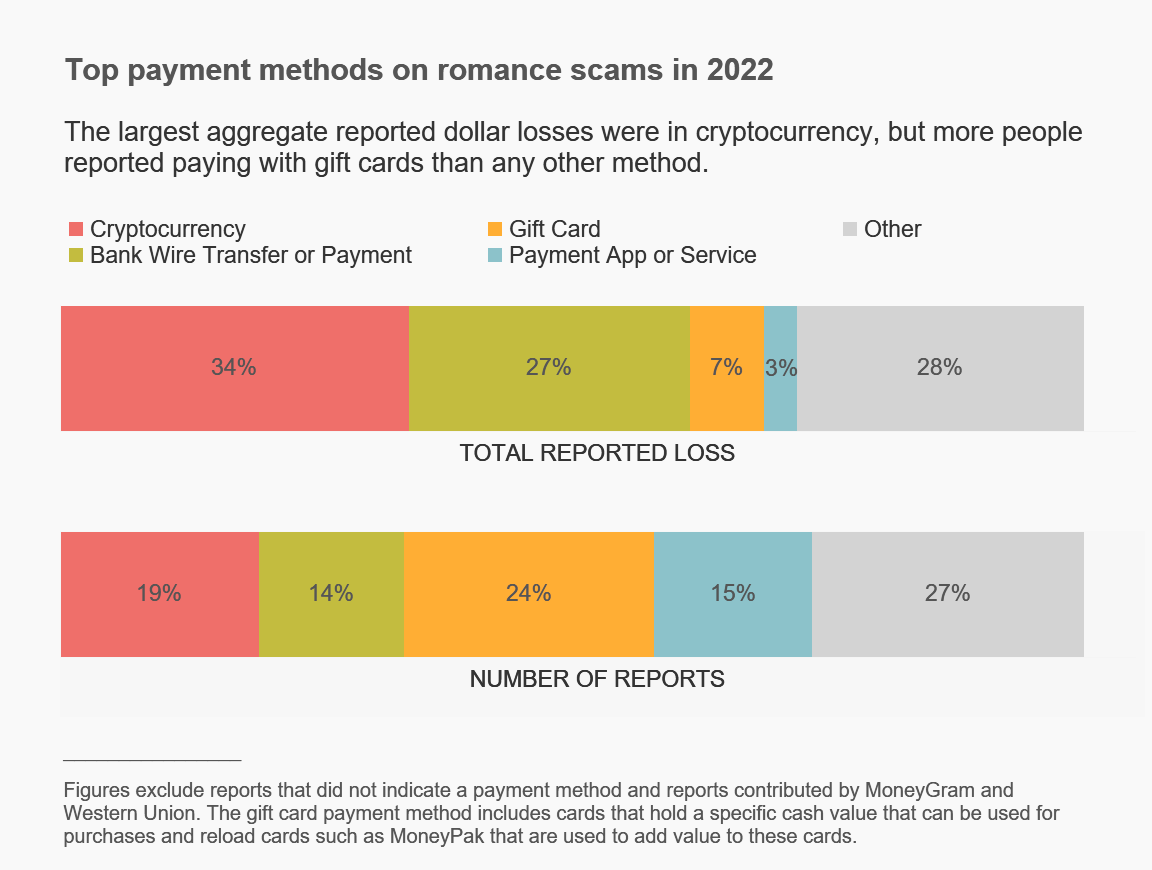
The FTC article contains a lot of other clues; this could easily be worked up into an internal newsletter piece or even a 'lunch-and-learn' session.
Fletcher, Emma, Romance scammers' favorite lies exposed, blog post, 9 February 2023. Available online at https://www.ftc.gov/news-events/data-visualizations/data-spotlight/2023/02/romance-scammers-favorite-lies-exposed.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
OpenSSL Project Issues Security Advisory
The OpenSSL Prject has released a security advisory to address multiple vulnerabilities affecting OpenSSL versions 3.0.0, 2.2.2, and 1.0.2. An attacker could exploit some of these vulnerabilities to obtain sensitive information.
The most serious vuln (CVE-2023-0286) could allow an attacker to read memory contents or DoS the server. However, it requires the attacker to provide both an X.509 certificate chain and CRL, and is really only likely to affect applications which have implemented their own functionality for retrieving CRL's.
The remaining vulnerabilities are classified as moderate, and involve a timing side channel in RSA decryption (CVE-2022-4304), a read buffer overrun in certificate verification (CVE-2022-4203), a use-after-free in a helper function for streaming ASN.1 data (CVE-2023-0215), a double-free in PEM file handling (CVE-2022-4450), an invalid pointer dereference triggered by malformed PKCS7 data (CVE-2023-0216), a NULL dereference when validating a DSA public key (CVE-2023-0217) and another NULL dereference during PKCS7 data verification (CVE-2023-0401).
The obvious mitigation is proactive patching with the appropriate updated version of OpenSSL, which should be percolating through distribution repositories.
OpenSSL Project, OpenSSL Security Advisory [7th February 2023], security advisory, 7 February 2023. Available online at https://www.openssl.org/news/secadv/20230207.txt.
North Korean Ransomware Targets Healthcare Sector
Various agencies, including the NSA, FBI, CISA and South Korean intelligence services, have jointly issued a Cybersecurity Advisory to highlight continuing ransomware attacks by the Democratic People's Republic of Korea (DPRK - in other words, North Korea) against the healthcare and public health sector. Although their primary concerns are the US and South Korean governments and health sectors, it seems unlikely the DPRK would confine their activities to just those countries.
Beset by currency sanctions, the DPRK views ransomware payments via cryptocurrencies as a good way to fund its other activities. The healthcare sector is particularly at risk, as both denial of access to patient data via encryption and leaking of exfiltrated patient data can be particularly damaging for both patients and compromised organization. Imprecations to never pay a ransom are all very well, but . . .
The advisory updates one that was previously issued, adding TTP's and IOC's for two new ransomware campaigns called Maui and H0lyGh0st. While the technical details are of interest to some of us, for most, the key information is a list of suggested mitigations - all of which would be considered good practice in most environments. These include authenticating and encrypting network sessions with TLS, implementing the principle of least privilege, hardening systems by disabling unnecessary admin interfaces and implementing multi-layer network segmentation by trust level.
CISA, #StopRansomware: Ransomware Attacks on Critical Infrastructure Fund DPRK Malicious Cyber Activities, Alert AA23-040A, 9 February 2023. Available online at https://www.cisa.gov/uscert/ncas/alerts/aa23-040a.
Infostealer Lures Victims with Fake Jobs
Trend Micro researchers recently discovered an infostealer campaign which targets Eastern Europeans in the cryptocurrency industry, luring them with fake jobs. The victims are enticed, via phishing or social media, into download and unpacking a RAR archive which contains two files: Interview questions.txt, a Cyrillic-charset text file, and Interview conditions.word.exe. That last filename is an obvious red flag to tech-savvy users - but we're talking about the crypto business here, remember?
When the user opens that malware file, it kicks off a first-stage loader for the Enigma infostealer, which is a derivative of the Stealerium open-source stealer/clipper/keylogger. This first stage begins registration and downloads a second-stage payload. It uses two C2 servers: the first uses Telegram to deliver payloads, send commands and a heartbeat, while the second is used for DevOps and logging purposes, using the Amadey C2 control panel, which is popular in Russian hacker forums. It seems that this malware is under continuous rapid development, hence the extensive logging.
The first, second and third stage loaders are encrypted and heavily obfuscated, using multiple techniques, to resist reverse engineering - for example, human-readable function names are replaced with hash values, rendering the code hard to understand. The second stage attempts to disable Microsoft Defender (possible if the victim's user account has admin privileges), then downloads and runs the third stage, which in turn downloads, decompresses and executes the final stealer.
The stealer configures itself then sets to work, stealing user information, tokens and passwords from Chrome, Edge, Outlook, Telegram, Signal, OpenVPN and other applications, as well as capturing screenshots and extracting clipboard content. It then exfiltrates this via Telegram.
The Trend Micro blog post contains a link to IOC's, as well as some obvious mitigations.
Zahravi, Aliakbar and Peter Girnus, Enigma Stealer Targets Cryptocurrency Industry with Fake Jobs, blog post, 9 February 2023. Available online at https://www.trendmicro.com/en_us/research/23/b/enigma-stealer-targets-cryptocurrency-industry-with-fake-jobs.html.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.