Les Bell and Associates Pty Ltd
Blog entries about Les Bell and Associates Pty Ltd
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
Russian Businessman Convicted in $US90 Million Hacking and Wire Fraud Case
The US DoJ has secured the conviction of a Russian businessman for his part in a sophisticated fraud which involved hacking to gain confidential information about the financial performance of publicly-listed US companies, and then using that information to perform stockmarket trades which netted him and his co-conspirators $US90 million.
Vladislav Klyushin,was charged along with Ivan Ermakov and Nikolai Rumiantcev. Klyushin was owner of M-13, a Moscow-based company which offered penetration testing and "Advanced Persistent Threat (APT) emulation" services and counted as clients “the Administration of the President of the Russian Federation, the Government of the Russian Federation, federal ministries and departments, regional state executive bodies, commercial companies and public organizations”, according to the company web site.
Between January 2018 and September 2020, the three, along with Mikhail Vladomirovich Irzak and Igor Sergeevich Sladkov, repeatedly hacked into the networks of two US-based filing agencies in order to obtain unreleased earnings information such as quarterly and annual filings. Knowing whether a company would meet, exceed or fall short of market expectations for its performance, the conspirators could predict whether its share price would rise or fall following the public earnings announcement, and used this to trade via accounts they opened in Cyprus, Portugal, Russia, the US and elsewhere. Klyushin also invested the money of several investors in this scheme, taking 60% of the profits.
While his co-conspirators remain at large, Klyushin was arrested in Sion, Switzerland in March 2021 and extradited to the US in December of that year. Having been convicted of charges of conspiring to obtain unauthorized access to computers, to commit wire fraid and to commit securities fraud - charges which attract significant jail time and fines - Klyushin will be sentenced on 4 May 2023.
US Attorney's Office for the District of Massachussets, Russian Businessman Found Guilty in $90 Million Hack-to-Trade Conspiracy, press release, 14 December 2023. Available online at https://www.justice.gov/usao-ma/pr/russian-businessman-found-guilty-90-million-hack-trade-conspiracy.
New Dropper Beeps to Avoid Sandbox Detection
Some new malware samples analyzed by Minerva researchers exhibit some interesting techniques, particularly for evading forensic analysis. The samples, which were uploaded to VirusTotal as DLL, GIF or JPG files, were flagged as 'spreader' or 'detect-debug-environment', and appear to be droppers, but are most interesting for their extensive use of evasion techniques.
The malware dropper component creates some registry keys, one of which contains a PowerShell script that uses curl.exe to fetch a DLL and then executes it using regsvr32.exe. This, in turn, injects its malicious payload into a legitimate WWAHost.exe process, using process hollowing. That payload then contacts a C2 server, uploading information about the victim machine and waiting for further commands. Unfortunately, the C2 server was down, which stalled Minerva's analysis, although they did identify a number of commands, many of them as yet unimplemented.
The various stages implement increasing levels of antiforensic evasion techniques, some of them repeated across the stages, including dynamic string deobfuscation, checking the system default language (to avoid infecting 'friendly' nations), checking for the presence of a debugger, using the RDTSC instruction to ensure a minimum number of CPU ticks have occurred since the processor was last reset, manipulating the stack segment register to see if the code is being single-stepped under a debugger, using the CPUID instruction to check for a VMware hypervisor, checking the registry for a VBOX key and - this is the technique that gets the malware its new name - calling the Beep API to delay execution.
Generally, malware uses the Sleep API to delay execution, avoiding detection by sandboxes. However, the Beep API - a holdover from the days of the original IBM PC and PC DOS - generates a simple beep tone on the system speaker and does not return until the sound finishes, achieving the same result in a less obvious way. Hence the monicker, Beep malware.
Zargarov, Natalie, Beepin’ Out of the Sandbox: Analyzing a New, Extremely Evasive Malware, blog post, 13 February 2023. Available online at https://minerva-labs.com/blog/beepin-out-of-the-sandbox-analyzing-a-new-extremely-evasive-malware/.
Pepsi Bottler Hacked, Employee Personal Information Stolen
For almost a month over the Christmas period, hackers had penetrated the systems of Pepsi Bottling Ventures, the largest privately-owned bottler of PepsiCo soft drinks in the US, and were able to exfiltrate personally identifiable information from the network. The breach was discovered on 10 January 2023, but another nine days went by before the company's systems were fully secured.
The information stolen is almost a hacker's wishlist for committing identity fraud:
- Full name and home address
- Financial account information, including passwords, PIN's and access numbers
- State and Federal government-issued ID numbers and drivers licence numbers
- ID card data
- Social security numbers
- Passport information
- Digital signatures
- Employee benefit information, including health insurance claims and medical history
The information stolen seems to relate to company employees; it is not clear whether any customers or business parters are affected.
Cluley, Graham, Gulp! Pepsi hack sees personal information stolen by data-stealing malware, blog post, 15 February 2023. Available online at https://www.bitdefender.com/blog/hotforsecurity/gulp-pepsi-hack-sees-personal-information-stolen-by-data-stealing-malware/.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
Massive Patchday
Whether you know it as 'Patch Tuesday' (in the Western Hemisphere) or 'Patch Wednesday' (for those in the Eastern Hemisphere, closer to the Date Line), today was a massive day for patch releases, with Miscrosoft, the Mozilla Firefox project, Citrix and Adobe all releasing security updates. Enterprise security teams will doubtless be busy testing patches before rolling them out; individual users, crying "Full speed ahead and damn the torpedoes!" will be running Windows Update and checking for updates on other products before rebooting.
| Vendor | Product | Update Reference |
|
|---|---|---|---|
| Microsoft |
Windows 10 versions 20H2, 21H1, 21H2, 22H2 |
KB5022834 | |
|
KB5011836 | ||
| Windows 11 version 22H2 |
KB5022845 |
||
| Mozilla | Firefox 110 |
Security Advisory 2023-05 |
|
| Firefox ESR 102.8 |
Security Advisory 2023-06 |
||
| Citrix |
Citrix Workspace app for Linux | Security Bulletin for CVE-2023-24486 | |
| Citrix Workspace app for Windows | Security Bulletin for CVE-2023-24484 & CVE-2023-24485 | ||
| Citrix Virtual Apps and Desktops | Security Bulletin for CVE-2023-24483 | ||
| Adobe | After Effects |
APSB23-02 | |
| Connect | APSB23-05 | ||
| FrameMaker | APSB23-06 | ||
| Bridge | APSB23-09 | ||
| Photoshop | APSB23-11 | ||
| InDesign | APSB23-12 | ||
| Premiere Rush |
APSB23-14 | ||
| Animate | APSB23-15 | ||
| Substance 3D Stager |
APSB23-16 |
You know what to do. . .
CISA Adds Four Known Exploited Vulnerabilities
Meanwhile the Cybersecurity & Infrastructure Security Agency has added four new vulnerabilities to its catalogue of known exploited vulnerabilities (https://www.cisa.gov/known-exploited-vulnerabilities-catalog).
The additions are:
- CVE-2023-21715, a MS Office security feature bypass vulnerability which allows an attacker to trick an authenticated user into letting an Office macro run from an untrusted file
- CVE-2023-22376, a vulnerability in the Windows Common Log File System Driver which allows privilege escalation attacks
- CVE-2023-23529, a type confusion vulnerability in Apple WebKit (present in multiple products) which may allow remote code execution
- CVE-2023-21823, a privilege escalation vulnerability in Microsoft Windows Graphic Component
Check with the relevant vendors for patches.
CISA, CISA Adds Four Known Exploited Vulnerabilities to Catalog, alert, 14 February 2023. Available online at https://www.cisa.gov/uscert/ncas/current-activity/2023/02/14/cisa-adds-four-known-exploited-vulnerabilities-catalog.
Another ICS Security Wakeup Call
A new report from Forescout's Vedere Labs research group provides yet another example of the lagging state of security for Industrial Control Systems (ICS), also referred to as Operational Technology (OT). These systems, which are used in industries ranging from manufacturing and mining to power generation and wastewater treatment, have traditionally been based on unintelligent devices connected via specialized and obscure protocols. However, those unintelligent devices are now based on embedded systems processors which run off-the-shelf operating systems and understand TCP/IP protocols so that they can connect to business systems. Programmable Logic Controllers (PLC's) are a good example - when introduced back in 1968 these were based on simple dedicated logic, but today they use industry-standard processors and embedded OS's such as Android and Linux.
ICS networks are often segmented into 'zones' linked by 'conduits', which are firewall-like controls that understand ICS/SCADA protocols and which form a security perimeter for each zone. PLC's are often used for this purpose, and because ICS security research has focused on compromising such devices and controlling the connected actuators, researchers have not fully considered post-exploitation techniques such as lateral pivoting between zones. That is what Vedere Labs set out to investigate.
The report presents:
- Two new vulnerabilities in Schneider Electric Modicon PLC's, which allow remote code execution and authentication bypass
- An overview of lateral movement techniques using control devices
- A realistic attack scenario which could physically damage a movable bridge
- In-depth discussion and demonstration of remote code execution and laterial movement proof-of-concept using the exploits above
- Conclusions and suggested mitigation techniques
The 41-page report is dense, but makes interesting reading, especially for those with some engineering background. Readers in critical infrastructure enterprises should take note.
Wetzels, Jos, Deep Lateral Movement in OT Networks: When Is a Perimeter Not a Perimeter?, technical report, 13 February 2023. Available online at https://www.forescout.com/resources/l1-lateral-movement-report/.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
Valentine's Day - For the Scammers in Your Life
Yesterday we brought you the US FTC's latest update on the statistics and the favourite lies of romance scammers. This was by way of warning for today's big event, but now comes another warning: Valentine's Day is always accompanies by a wave of scam emails targeting the emotionally vulnerable.
Bitdefender reports that roughly 83% of Valentine-themed spam emails in recent weeks were marked as scams, peaking during the last week. Although scammers predominantly targeted the US (45% of reports), they covered Europe, Asia-Pacific and Australia for good measure - although Ireland, with 7% of reports, seems disproportionately victimized.
Spam email subjects covered a range of lures:
- the perfect romantic rose bear gift is here to ensure your loved one feels truly loved
- up to 93 off canvas sales valentine's day
- spice up your life with a new romance
- 15 bottles of wine to celebrate valentine s day
- confirmation receipt 100 valentine s day gifts
- ukrainian woman are near you date them for valentine
- Gentlemen, Are You Ready For Valentine's Day?
In some cases, the scammers were offering those last-minute or good-value gifts, while others were obviously intended to capture the interest of the lonely and dateless.
The blog post contains a number of samples which might be useful in awareness sessions.
Bîzgă, Alina, What’s love got to do with it? 4 in 5 Valentine’s Day-themed spam emails are scams, Bitdefender Antispam Lab warns, blog post, 14 February 2023. Available online at https://www.bitdefender.com/blog/hotforsecurity/whats-love-got-to-do-with-it-4-in-5-valentines-day-themed-spam-emails-are-scams-bitdefender-antispam-lab-warns/.
Cloudflare Blocks Record HTTP DDoS Attack
Last weekend, DDoS mitigation firm Cloudflare really earned their pay, detecting and mitigating dozes of what they term hyper-volumetric DDoS attacks. The majority of these attacks peaked at around 50 to 70 million HTTP requests per second (rps) with the largest exceeding 71 million rps - the largest such attack reported to date, over 35% higher than the previous record of 46 million rps in June 2022.
For most web servers, every HTTP request will invoke some code - most commonly PHP, but also node.js JavaScript code, .NET or Java. This may in turn invoke other subsystems - middleware, databases, API's on other servers - all committing resources such as memory, CPU cycles and network, and taking time. The objective here is not to consume bandwidth and fill the victim's upstream pipe - it is to consume resources.
In this case, the targeted sites included a gaming provider, cryptocurrency companies, hosting providers and cloud computing platforms; the latter can generally scale well to handle such attacks - but unless customers have quotas in place, they could face massive bills for such attacks. The requests were delivered over HTTP/2 and originated from over 30,000 IP addresses, mostly administered by multiple cloud providers. In light of this and previous attacks from cloud provider addresses, Cloudflare will be providing eligible service providers with a free botnet threat intelligence feed about their own IP address space.
This weekend's activity is no surprise; DDoS attacks have been increasing in size, sophistication and frequency, particularly with the growth of relatively inexpensive DDoS-as-a-service platforms run by cybercriminals. HTTP DDoS attacks have been growing by an average of 79% year on year; even worse, the number of volumetric attacks - those exceeding 100 Gbps - has grown by 67% quarter on quarter, and attacks that last more than three hours has grown by 87% quarter on quarter.
Yoachimik, Omer, Julien Desgats and Alex Forster, Cloudflare mitigates record-breaking 71 million request-per-second DDoS attack, blog post, 14 February 2023. Available online at https://blog.cloudflare.com/cloudflare-mitigates-record-breaking-71-million-request-per-second-ddos-attack/.
Google Agrees with DHS/CISA: Companies Need to Step Up
Some readers will think, 'Finally! Somebody gets it!' in response to this story, while others will not like it at all. But the US Department of Homeland Security thinks that tech companies should be held accountable for security vulnerabilities and the consequential breaches - and Google agrees.
In an opinion piece for Foreign Affairs (paywalled), Jen Easterly, Director of the Cybersecurity & Infrastructure Security Agency with the Department of Homeland Security, and Eric Goldstein, Executive Assistant Director, wrote:
“The incentives for developing and selling technology have eclipsed customer safety in importance. […] Americans…have unwittingly come to accept that it is normal for new software and devices to be indefensible by design. They accept products that are released to market with dozens, hundreds, or even thousands of defects. They accept that the cybersecurity burden falls disproportionately on consumers and small organizations, which are often least aware of the threat and least capable of protecting themselves.”
Their argument is that tracking, identifying, arresting and prosecuting cybercriminals such as ransomware operators is only addressing a symptom. In fact, cybercrime remains relatively low-risk, due to cross-border jurisdictional issues and the difficulties of securing convictions. By comparison with armed robbery or even burglary, it's a walk in the park with much higher returns.
Criminal syndicates now operate like businesses, on a massive scale; while some operate at the premium end of the market, developing 0days and exploiting them against highly-defended targets, the majority work in the commodity market, routinely exploiting well-known vulnerabilities that remain unpatched - either because no patch exists, no patching mechanism exists, or patch distribution, testing and deployment is poorly managed.
Add to that rapidly-evolving technology that rewards companies for being first to market with a minimum viable product, and which favours innovative functionality over security. Compounding the problem is a massive market that sells 'solutions' - products and services that aim to add security to complex and fragile systems. The result - well, you can see it every day, and it may well pay your wages.
As Google's blog post points out, the answer is to incentivize companies to pay attention to the security architects' mantras: secure by default and secure by design. We need to shift resources left, from incident response to engineering security into the software development process. I love this quote, which I originally encountered as part of the philosophy of test pilots - who are primarily engineers, not daredevils, and who are to aviation what testers are to software, only with a lot more skin in the game:
"The object of the game, gentlemen, is not to cheat death: the object is not to let him play."
Patrick Poteen, Sgt. U.S. Army
If the software industry doesn't embed this idea culturally as a core value, it is likely that governments - operating collaboratively and internationally - will start to legislate it in ways that we may not want at all.
We're going to have to up our game.
Easterly, Jen and Eric Goldstein, Stop Passing the Buck on Cybersecurity: Why Companies Must Build Safety Into Tech Products, Foreign Affairs, 1 February 2023. Available online at https://www.foreignaffairs.com/united-states/stop-passing-buck-cybersecurity.
Walker, Kent and Royal Hansen, The US Government says companies should take more responsibility for cyberattacks. We agree, blog post, 13 February 2023. Available online at https://security.googleblog.com/2023/02/the-us-government-says-companies-should.html.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
Reddit Breached; Basic MFA Not Much Help
The big news of the weekend was the breach of internal systems at Reddit by an as-yet-unidentified attacker. According to the site, the initial access mechanism was "a sophisticated and highly-targeted phishing attack". However, they then go on to say,
As in most phishing campaigns, the attacker sent out plausible-sounding prompts pointing employees to a website that cloned the behavior of our intranet gateway, in an attempt to steal credentials and second-factor tokens.
In other words, this was a proxy or man-in-the-middle attack which captured a user's password and 2FA token of some kind. They go on to say,
Soon after being phished, the affected employee self-reported, and the Security team responded quickly, removing the infiltrator’s access and commencing an internal investigation. Similar phishing attacks have been recently reported. We’re continuing to investigate and monitor the situation closely and working with our employees to fortify our security skills. As we all know, the human is often the weakest part of the security chain.
Aye, and there's the rub. In this case, the use of a second factor did not prevent the breach, and what detected it was the humble Mark I human eyeball. This illustrates the continued importance of security education, training and awareness; MFA products alone will not solve the problem. Security is a process, not a product.
Reddit's incident disclosure provides the usual advice: set up MFA (yes), change your password frequently (not such a good idea - it leads to weak passwords) and use a password manager (yes). However, I think security architects and developers need to pick up some of the load by a) providing more contextual information and clues in login dialogs, to alert users to spoofing, and b) moving to cryptographic techniques that can detect MitM attacks, like SSH and TLS can.
Fortunately for Reddit and Redditors, only limited data was exfiltrated, and there is nothing - so far - to suggest that users' personal data or credentials have been compromised.
After successfully obtaining a single employee’s credentials, the attacker gained access to some internal docs, code, as well as some internal dashboards and business systems. We show no indications of breach of our primary production systems (the parts of our stack that run Reddit and store the majority of our data).
So far.
u/KeyserSosa, We had a security incident. Here's what we know., Reddit post, 10 February 2023. Available online at https://www.reddit.com/r/reddit/comments/10y427y/we_had_a_security_incident_heres_what_we_know/.
Romance Scammers Analyzed
This is not really enterprise infosec - but it's a conversational morsel that can be used to open that conversation with employees. Remember, employees may not be strongly vested in protecting corporate data - but they have a strong interest in privacy which can cause their ears to prick up. And having talked about ways to spot a romance scammer, you could move the conversation on - to the clues that signal a phishing attack.
The US Federal Trade Commission has released a fascinating article in their Data Spotlight series, this time dealing with romance scammers, and in particular, their favourite lies. The statistics are quite staggering: in 2022, nearly 70,000 people reported a romance scam, and reported losses totaled $US1.3 billion - and that's just in the US alone. The median reported loss was $US4,400, but some will obviously be much higher, and it's worth reflecting that an employee under the pressure of financial loss may turn to fraud or larceny - yet another reason to cover this in security awareness sessions.
The scammers have developed a short list of buttons they can push to get their payout, and the article lists the most popular:
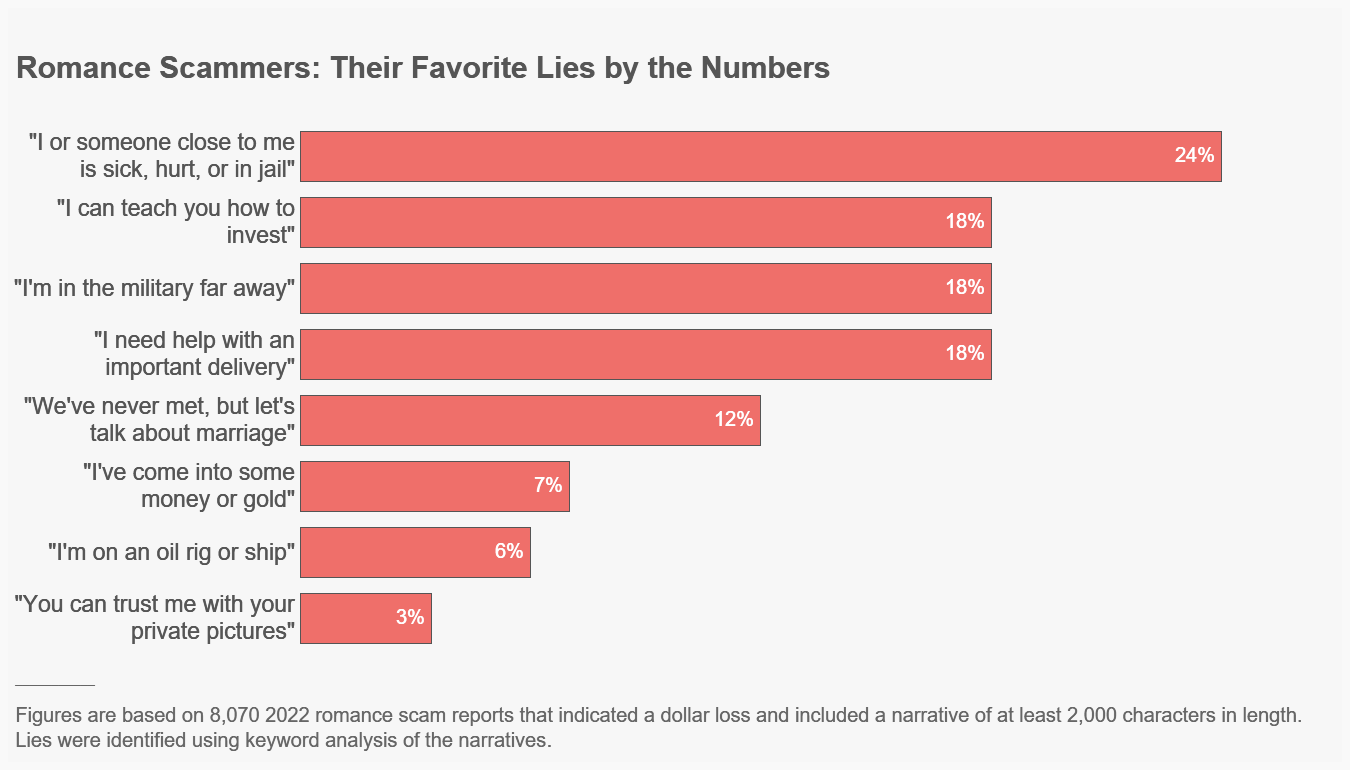
Of course, the scammers also need a way - preferably a non-reversible way - to transfer their ill-gotten gains. Gift cards are a perennial favourite, but for larger amounts, cryptocurrencies are now the method of choice, followed by bank wire transfers:
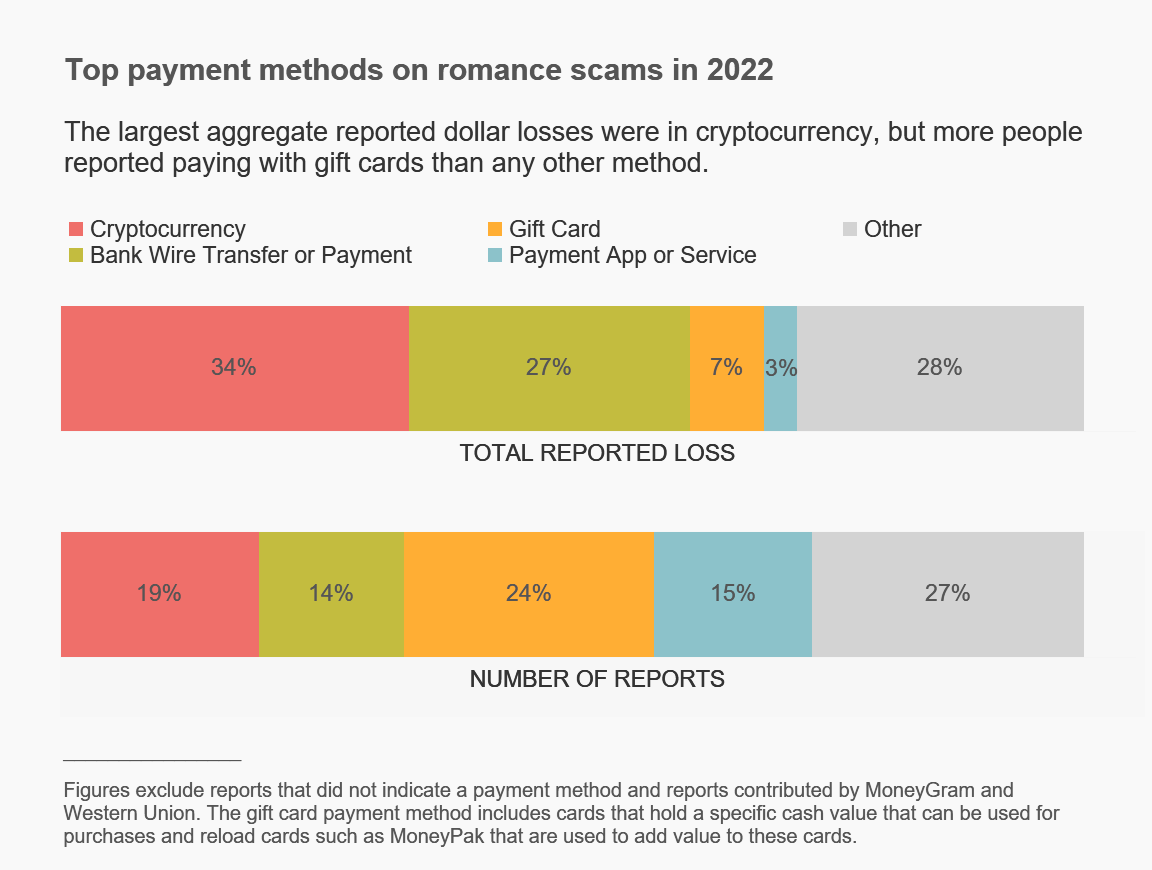
The FTC article contains a lot of other clues; this could easily be worked up into an internal newsletter piece or even a 'lunch-and-learn' session.
Fletcher, Emma, Romance scammers' favorite lies exposed, blog post, 9 February 2023. Available online at https://www.ftc.gov/news-events/data-visualizations/data-spotlight/2023/02/romance-scammers-favorite-lies-exposed.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
OpenSSL Project Issues Security Advisory
The OpenSSL Prject has released a security advisory to address multiple vulnerabilities affecting OpenSSL versions 3.0.0, 2.2.2, and 1.0.2. An attacker could exploit some of these vulnerabilities to obtain sensitive information.
The most serious vuln (CVE-2023-0286) could allow an attacker to read memory contents or DoS the server. However, it requires the attacker to provide both an X.509 certificate chain and CRL, and is really only likely to affect applications which have implemented their own functionality for retrieving CRL's.
The remaining vulnerabilities are classified as moderate, and involve a timing side channel in RSA decryption (CVE-2022-4304), a read buffer overrun in certificate verification (CVE-2022-4203), a use-after-free in a helper function for streaming ASN.1 data (CVE-2023-0215), a double-free in PEM file handling (CVE-2022-4450), an invalid pointer dereference triggered by malformed PKCS7 data (CVE-2023-0216), a NULL dereference when validating a DSA public key (CVE-2023-0217) and another NULL dereference during PKCS7 data verification (CVE-2023-0401).
The obvious mitigation is proactive patching with the appropriate updated version of OpenSSL, which should be percolating through distribution repositories.
OpenSSL Project, OpenSSL Security Advisory [7th February 2023], security advisory, 7 February 2023. Available online at https://www.openssl.org/news/secadv/20230207.txt.
North Korean Ransomware Targets Healthcare Sector
Various agencies, including the NSA, FBI, CISA and South Korean intelligence services, have jointly issued a Cybersecurity Advisory to highlight continuing ransomware attacks by the Democratic People's Republic of Korea (DPRK - in other words, North Korea) against the healthcare and public health sector. Although their primary concerns are the US and South Korean governments and health sectors, it seems unlikely the DPRK would confine their activities to just those countries.
Beset by currency sanctions, the DPRK views ransomware payments via cryptocurrencies as a good way to fund its other activities. The healthcare sector is particularly at risk, as both denial of access to patient data via encryption and leaking of exfiltrated patient data can be particularly damaging for both patients and compromised organization. Imprecations to never pay a ransom are all very well, but . . .
The advisory updates one that was previously issued, adding TTP's and IOC's for two new ransomware campaigns called Maui and H0lyGh0st. While the technical details are of interest to some of us, for most, the key information is a list of suggested mitigations - all of which would be considered good practice in most environments. These include authenticating and encrypting network sessions with TLS, implementing the principle of least privilege, hardening systems by disabling unnecessary admin interfaces and implementing multi-layer network segmentation by trust level.
CISA, #StopRansomware: Ransomware Attacks on Critical Infrastructure Fund DPRK Malicious Cyber Activities, Alert AA23-040A, 9 February 2023. Available online at https://www.cisa.gov/uscert/ncas/alerts/aa23-040a.
Infostealer Lures Victims with Fake Jobs
Trend Micro researchers recently discovered an infostealer campaign which targets Eastern Europeans in the cryptocurrency industry, luring them with fake jobs. The victims are enticed, via phishing or social media, into download and unpacking a RAR archive which contains two files: Interview questions.txt, a Cyrillic-charset text file, and Interview conditions.word.exe. That last filename is an obvious red flag to tech-savvy users - but we're talking about the crypto business here, remember?
When the user opens that malware file, it kicks off a first-stage loader for the Enigma infostealer, which is a derivative of the Stealerium open-source stealer/clipper/keylogger. This first stage begins registration and downloads a second-stage payload. It uses two C2 servers: the first uses Telegram to deliver payloads, send commands and a heartbeat, while the second is used for DevOps and logging purposes, using the Amadey C2 control panel, which is popular in Russian hacker forums. It seems that this malware is under continuous rapid development, hence the extensive logging.
The first, second and third stage loaders are encrypted and heavily obfuscated, using multiple techniques, to resist reverse engineering - for example, human-readable function names are replaced with hash values, rendering the code hard to understand. The second stage attempts to disable Microsoft Defender (possible if the victim's user account has admin privileges), then downloads and runs the third stage, which in turn downloads, decompresses and executes the final stealer.
The stealer configures itself then sets to work, stealing user information, tokens and passwords from Chrome, Edge, Outlook, Telegram, Signal, OpenVPN and other applications, as well as capturing screenshots and extracting clipboard content. It then exfiltrates this via Telegram.
The Trend Micro blog post contains a link to IOC's, as well as some obvious mitigations.
Zahravi, Aliakbar and Peter Girnus, Enigma Stealer Targets Cryptocurrency Industry with Fake Jobs, blog post, 9 February 2023. Available online at https://www.trendmicro.com/en_us/research/23/b/enigma-stealer-targets-cryptocurrency-industry-with-fake-jobs.html.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
NIST Selects Algorithm as Lightweight Cryptography Standard
Since 2018, the National Institute of Standards and Technologies has been working with industry and academic researchers in a multi-round review process to select a standard algorithm for protecting information created and transmitted on the Internet of Things.
While some devices on the IoT, such as cloud and fog computing services, have plenty of compute power, others, such as tiny sensors and actuators, have to operate on small batteries for periods of months or years. At the extreme low-power end we find such things as embedded medical devices, stress sensors inside roads and bridges and keyless entry fobs for cars, and these need 'lightweight' cryptographic algorithms which provide an acceptable level of security, but coupled with compact code size and memory usage, low energy consumption and acceptable speed.
The NIST review process started with 57 submissions, which were whittled down to 10 finalists before the final winner was selected. [Reaches for sealed envelope.] And the winner is . . . Ascon, a family of seven different algorithms, of which some or all will become part of the NIST lightweight cryptography standard. Ascon was developed in 2014 by a team of cryptographers from Graz University of Technology, Infineon Technologies, Lamarr Security Research and Radboud University, and had already been selected as the primary choice for lighweight authenticated encryption in the CAESAR competition, so it has a strong pedigree.
Authenticated encryption with associated data (AEAD) assures confidentiality of its encrypted payload, but also assures the authenticity of origin of associated data such as plaintext message headers and routing information. For higher-powered devices, these functions are typically performed by AES (FIPS 197) in Galois Counter Mode (SP 800-38D), but Ascon provides a good replacement for IoT devices. Similarly, while SHA2-256 is a widely-used hashing algorithm, Ascon fits the bill well for low-powered devices.
Uncredited, NIST Selects ‘Lightweight Cryptography’ Algorithms to Protect Small Devices, news release, 7 February 2023. Available online at https://www.nist.gov/news-events/news/2023/02/nist-selects-lightweight-cryptography-algorithms-protect-small-devices.
Multiple XSS Vulnerabilities in Document Management Systems
Rapid7 security researcher Matthew Kienow has duscovered multiple cross-site scripting (XSS) vulnerabilities in on-premises installations of open-source and freemium document management systems from four different vendors. The vulnerabilities and their statuses are listed below
| Vendor | Product | Version | CVE Number |
Patch Status |
|---|---|---|---|---|
| ONLYOFFICE | Workspace | 12.1.0.1760 | CVE-2022-47412 | Unpatched |
| OpenKM | OpenKM | 6.3.12 | CVE-2022-47413 | Unpatched |
| OpenKM | OpenKM | 6.3.12 | CVE-2022-47414 | Unpatched |
| LogicalDOC | LogicalDOC CE/Enterprise | 8.7.3/8.8.2 | CVE-2022-47415 | Unpatched |
| LogicalDOC | LogicalDOC CE/Enterprise | 8.8.2 | CVE-2022-47416 | Unpatched |
| LogicalDOC | LogicalDOC CE/Enterprise | 8.7.3/8.8.2 | CVE-2022-47417 | Unpatched |
| LogicalDOC | LogicalDOC CE/Enterprise | 8.7.3/8.8.2 | CVE-2022-47418 | Unpatched |
| Mayan | Mayan EDMS | 4.3.3 | CVE-2022-47419 | Unpatched |
In general, the XSS vulnerabilities arise because the products are not properly sanitizing and escaping <img> and <script> elements either in the uploaded documents, the in-app messaging system, the document filename field in an upload form or elsewhere in the application.
The Rapid7 blog post provides a full explanation of each vulnerability, along with a simple proof-of-concept which users can try in order to test their own installations. The PoC safely triggers a JavaScript alert() popup, but clearly much more sophisticated exploitation is possible (and the blog post discusses a few).
Mitigation suggestions include not allowing untrusted users to upload documents, but remediation really depends upon fixes being released by the vendors - none of whom had responded in a timely fashion.
Beardsley, Tod, Multiple DMS XSS (CVE-2022-47412 through CVE-20222-47419), blog post, 7 February 2023. Available online at https://www.rapid7.com/blog/post/2023/02/07/multiple-dms-xss-cve-2022-47412-through-cve-20222-47419/.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
Vastaamo Suspect Arrested in France
Regular readers will be familiar with the privacy breach which occurred at Finnish psychotherapy provider Vastaamo in September 2020. The company was infected by ransomware which encrypted their patient records and held them ransom (AFP, 2020). When the company CEO refused to negotiate with the attackers, they responded by releasing sensitive patient records on a Tor network server, and then turned to extorting payments from the patients themselves. It appears that the company's software was only minimally secured and did not comply with Finland's regulations for healthcare records systems. The CEO was terminated and the company subsequently liquidated (Ralston, 2021).
Now comes news (Krebs, 2023) that, following the issue of an arrest warrant in October 2022 for the offences of 1 ) Aggravated computer break-in, offence 2) Aggravated extortion, attempt 3) Aggravated dissemination of information violating personal privacy 4) Extortion 5) Attempt of an extortion 6) Computer break-in 7) Message interception and 8) Falsification of evidence, a suspect has been detained in France.
Aleksanteri Tomminpoika Kivimäki, 25, had uploaded a large archive of patient data to the dark web, but made the mistake of including other files from his own home directory - including the ~/.ssh directory, in which the known_hosts file made particularly interesting reading for investigators. However, his arrest was purely coincidental - French police were responding to a domestic violence report and only identified Kivimäki after he had presented a fake Romanian ID.
It turns out that Kivimäki has a long history of hacking offences, but since most of them were committed while he was still a juvenile, resulting in very light penalties. Apparently he did not learn his lesson, and it seems likely that if, as expected, he is extradited to stand trial in Finland, he will face a much stiffer penalty this time.
AFP, 'Shocking' hack of psychotherapy records in Finland affects thousands, The Guardian, 27 October 2020. Available online at https://www.theguardian.com/world/2020/oct/26/tens-of-thousands-psychotherapy-records-hacked-in-finland.
Krebs, Brian, Finland's Most-Wanted Hacker Nabbed in France, Krebs on Security blog, 5 February 2023. Available online at https://krebsonsecurity.com/2023/02/finlands-most-wanted-hacker-nabbed-in-france/.
Ralston, William, They Told Their Therapists Everything. Hackers Leaked It All, Wired, 4 May 2021. Available online at https://www.wired.com/story/vastaamo-psychotherapy-patients-hack-data-breach/.
CISA Releases ESXiArgs Ransomware Recovery Script
The Cybersecurity & Infrastructure Security Agency has released a recovery script for organizations that have fallen victim to ESXiArgs ransomware infecting their VMware ESXi servers. ESXiArgs encrypts configuration files, making virtual machines unusable. CISA recommends organizations impacted by ESXiArgs evaluate the script and guidance provided in the Github project's README file to determine if it is fit for attempting to recover access to files in their environment.
The ESXiArgs exploit was first disclosed by CERT-FR in an alert on 3 February entitled "Exploitation campaign of a vulnerability affecting VMware ESXi". According to CERTFR, the exploit affects unpatched VMware ESXi servers, specifically:
- ESXi 7.x versions earlier than ESXi70U1c-17325551
- ESXi versions 6.7.x earlier than ESXi670-202102401-SG
- ESXi versions 6.5.x earlier than ESXi650-202102101-SG
VMWare claims that the vulnerability (CVE-2021-21974), is a heap overflow in the OpenSLP code of ESXi, and was patched back in February 2021.
CERT-FR, [MàJ] Campagne d’exploitation d’une vulnérabilité affectant VMware ESXi, Bulletin D'Alerte, 3 February 2023. Available online at https://www.cert.ssi.gouv.fr/alerte/CERTFR-2023-ALE-015/.
CISA, ESXiArgs-Recover, github project, 8 February 2023. Available online at https://github.com/cisagov/ESXiArgs-Recover.
Dutch Police Dismantle Exclu Secure Messaging Service
The Dutch police, who have previously demonstrated considerable skill in infiltrating criminal networks, have racked up another win by breaking into the Exclu encrypted messaging service and ultimately dismantling it. Exclu, which had an estimated 3,000 users, was first investigated by German authorities in June 2020, and they shared their intelligence with their Dutch colleagues. This allowed them to intercept the communications of criminal networks for a period of five months.
During the culminating action last week, 1,200 police officers were deployed; 45 people were arrested in the Netherlands and Belgium, including the administrators and owners of Exclu and 79 locations in the Netherlands, Germany and Poland were searched. Two drug laboratories were dismantled, 300,000 ecstasy tables and 20 firearms were seized along with 200 phones which will be forensically examined. €5.5 million was also confiscated.
Eurojust, New strike against encrypted criminal communications with dismantling of Exclu tool, press release, 6 February 2023. Available online at https://www.eurojust.europa.eu/news/new-strike-against-encrypted-criminal-communications-dismantling-exclu-tool.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
Former Ubiquiti Engineer Pleads Guilty to Data Theft, Extortion
A former employee at network form Uniquiti has pleaded guilty to allegations of stealing confidential data, extorting a ransom and causing the publication of misleading news articles. Nickolas Sharp misused his admin privileges to access the company's AWS and GitHub accounts, stealing gigabytes of confidential data. To cover his tracks, he changed the log retention policies, altered other files and used a Surfshark VPN service - but did not realise that an Internet outage at his home had exposed his real IP address.
Once the breach was discovered, Sharp was one of those tasked with remediating it - but he simultaneously sent an extortion demand to his employer, demanding payment of BTC50 - which, at that time, was approximately $US2 million - to return the data and disclose a purported backdoor, and when the company refused to pay, he leaked some of the data.
However, by now the FBI had tracked his IP address and executed a search warrant at his home in Portland, OR. He denied all involvement and stated that he had not previously used Surfshark - only to be confronted with records showing that he had set up a Surfshark account six months before the breach. To this, he claimed that someone else must have used his PayPal account.
Proving the truth of the old adage that when you're in a hole, you should stop digging, Sharp then contacted various tech news outlets, posing as a whistleblower and claiming that Ubiquiti had been hacked by an unknown actor who had gained root privileges. The publication of these stories caused Ubiquiti's stock price to fall by 20% - a drop of over $US4 billion in market capitalization.
Having pleaded guilty to one count of transmitting a program to a protected computer that intentionally caused damage, one count of wire fraud, and one count of making false statements to the FBI, Sharp now faces up to 35 years in prison. His actual sentence will be handed down in May.
Biase, Nicholas, Former Employee Of Technology Company Pleads Guilty To Stealing Confidential Data And Extorting Company For Ransom, press release, 2 February 2023. Available online at https://www.justice.gov/usao-sdny/pr/former-employee-technology-company-pleads-guilty-stealing-confidential-data-and.
OpenSSH 9.2/9.2p1 Released
The OpenSSH project has released OpenSSH 9.2/9.2p1, which fixes a number of security bugs. Prime among them is CVE-2023-25136, a pre-authentication double-free memory fault, which first appeared in 9.1 and is not believed to be exploitable. Double-free faults occur when a programmer calls malloc() (or equivalent) to allocate memory once, but then somehow calls free() twice - potentially allowing remote code execution
The vulnerabilitiy occurs in the unprivileged pre-auth process which is subject to a chroot() and is further sandboxed by the OpenSSH privilege separation architecture - although the main sshd runs with root privileges, a new connection causes a forked child to change to the effective UID of the connecting user.
The vulnerability was first disclosed by Mantas Mikulenas, who discovered it when an old version of PuTTY caused the child sshd process to crash with a "seccomp violation" error. The new version is available from the OpenSSH mirrors, and binaries for different platforms should flow through repositories shortly.
Mantas M., Bug 3522 - Crash with "free(): double free detected" with old clients, bug report, 15 January 2023. Available online at https://bugzilla.mindrot.org/show_bug.cgi?id=3522.
Uncredited, OpenSSH 9.2/9.2p1 (2023-01-02), release note, 2 February 2023. Available online at https://www.openssh.com/releasenotes.html.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
2048-bit RSA Cracking Within Reach?
Most contemporary public-key cryptosystems are based on so-called trspdoor functions, which are special cases of one-way functions - functions which are easy to compute one way, but hard to reverse. There are two problems in widespread use: first, integer multiplication, for which the reverse problem, factorization of large composite integers, rapidly becomes very inefficient as the numbers get larger. This is the basis of the RSA public-key cryptosystem.
The second example is the discrete logarithm problem: raising an integer \(g\) to a power \(x\) is very fast, but the reverse - figuring out what power \(x\) a given integer, \(g\), was raised to in order to obtain a specified value \(h\) (finding the logarithm to the base \(g\) of \(h\)), is inefficient. In practice, we make both of these problems much harder by using modular arithmetic. This is the basis of the Diffie-Hellman key agreement protocol as well as the Elgamal cryptosystem.
The generation of RSA public and private keys starts by finding two large prime numbers, \(p\) and \(q\), and multiplying them to produce a large composite modulus \(N\), which becomes part of the public key. RSA would be broken if an attacker could quickly factorize \(N\).
For years, we have known that increases in compute power would therefore progressively weaken RSA. We have also known that improved factorization algorithms would further weaken it. And most of all, we have feared that the development of practical quantum computers could break it.
A new preprint paper which escaped my attention at the time suggests that a team of Chinese scientists may have taken advantage of all these possibilities to develop a technique which brings cracking of 2048-bit RSA keys within reach. In their paper, the researchers used quantum approximation algorithms, running on a quantum computer with 10 superconducting qubits, in combination with a classical lattice reduction algorithm, to factor integers up to 48 bits in size.
But what makes this result particularly interesting - or concerning - is that the algorithm is sublinear in the number of qubits required: \(\mathcal{O}(2N/\log{N})\). The authors suggest that their algorithm could therefore break a 2048-bit RSA modulus using a 372-qubit quantum computer. This is very much more practical than the millions of qubits that would be required by more straightforward approaches such as Shor's algorithm (because of the overhead of error correction).
Now, quantum computers of that size already exist in the public sphere - IBM's Osprey, for example is a 433-qubit machiine. And we do not know what exists inside the data centers of communications intelligence agencies world-wide; anyone who has a larger computer with the capability of breaking public-key crypto is obviously not going to talk about it.
My back-of-an-envelope calculations indicate that a 3072-bit RSA modulus - the smallest recommended for the NSA's Commercial National Security Algorithm Suite - could be cracked by a 531-qubit machine, while a 4096-bit RSA modulus would require a 683-qubit machine.
I do not believe the sky is falling - yet. However, I think this is something of a wake-up call - first, to users who are still using relatively small (1024-bit or 2048-bit) RSA keys, but also to security architects and regulators who have not yet started to prepare for the adoption of post-quantum cryptographic schemes. Personally, I long ago moved to 3072-bit RSA keys and subsequently to elliptic curve keys, which are not vulnerable to this particular attack. But I think it is now time to give serious consideration to a post-quantum escape plan.
Yan, Bao, et al, Factoring integers with sublinear resources on a superconducting quantum processor, arXiv preprint, 23 December 2022. Available online at http://arxiv.org/abs/2212.12372.
Collins, Hugh, IBM Unveils 400 Qubit-Plus Quantum Processor and Next-Generation IBM Quantum System Two, press release, 9 November 2022. Available online at https://newsroom.ibm.com/2022-11-09-IBM-Unveils-400-Qubit-Plus-Quantum-Processor-and-Next-Generation-IBM-Quantum-System-Two.
MITRE Releases Cyber-Resilience Design Tool
The pendulum of cybersecurity fashion is starting to swing away from playing whack-a-mole with vulnerabilities via pen-testing, then the same game with the remaining vulnerabilities via incident response, towards engineering cyber-resilient systems which are harder and will both slow intruders down and limit their abilities to penetrate further. This approach has most recently been advocated by NIST's Ron Ross and his team, in SP 800-160 volume 2, Developing Cyber-Resilient Systems: A Systems Security Engineering Approach.
Now, MITRE has joined the party, with a new tool called the Cyber Resiliency Engineering Framework (CREF) Navigator. Rather similar to MITRE's ATT&CK and D2FEND databases, the CREF Navigator provides a useful visualization of the various techniques which can be used to develop cyber-resilient systems, and maps them to the corresponding ATT&CK Tactics and Techniques, as well as the ATT&CK Mitigations and their effect on the adversary actions.
The CREF Navigator is organized around four fundamental goals:
- Anticipate: informed preparedness for adversity
- Withstand: Continue essential mission or business functions despite adversity
- Recover: Restore mission or business functions during and after adversity
- Adapt: Modify mission or business functions, and/or supporting capabilities, to prepare for predicted changes in the technical, operational or threat environments.
The four goals are supported by eight underlying objectives, such as Prevent or Avoid, Prepare, Constrain, Understand and Re-Architect. The techniques are many and varied, such as dynamic reconfiguration, redundancy by means of backup & restore, spare capacity or replication, and various forms of deception.
As well as the Navigator, there is also an Inspector, which allows further drilling down, and Map, which shows the relationships between Goals, Objectives and Techniques. Finally, a Visualizer shows relationships both within CREF and also between ATT&CK and CREF.
Uncredited, Getting Started, web documentation, undated. Available online at https://crefnavigator.mitre.org/gettingStarted.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
Google Search Returns Malicious Loaders for Malware Attacks
Researchers at SentinelLabs have identified a series of virtualized .NET malware loaders which are being distributed via malicious ads placed through Google and displayed in search results. The researchers encounter these loaders while investigating malvertising attacks; all that was required was a simple Google search for "Blender 3D" and the ads were returned.
The loaders are implemented in .NET and use vitualization, based on the KoiVM virtualizing protector, to obfuscate their implementation and execution. Although SentinelLabs dubbed these loaders MalVirt, it seems likely that they are related to the KoiVM loader detected a few months ago by K7 Security Labs. The MalVirt malware applies an unusual level of anti-analysis and anti-detection techniques to its payloads, which include a feature-rich infostealer from the Formbook family that is capable of keylogging, screenshot theft, theft of web and other credentials and staging of other malware.
The Formbook malware is more commonly delivered as malmail attachments; switching to malverts is a response to the default blocking of MS Office VBA (Visual Basic for Applications) macros. While popular with criminal groups, it has also been used by state-affiliated groups, as reported by Ukraine's CERT.
Milenkoski, Aleksandar and Tom Hegel, MalVirt | .NET Virtualization Thrives in Malvertising Attacks, blog post, 2 Februart 2023. Available online at https://www.sentinelone.com/labs/malvirt-net-virtualization-thrives-in-malvertising-attacks/.
Threat Actors Use Visual Studio Tools for Office to Deploy Malware
There are many other responses to Microsoft's default blocking of VBA macros: wrapping them in .ZIP and similar archives, or even .ISO images, so that the wrapper would carry the Mark of the Web, but the macro would not, or using shortcut (.LNK) files. Now, Deep Instinct researchers have uncovered a new technique: using Microsoft's Visual Studio Tools for Office (VSTO) to develop Office Add-Ins.
VSTO allows these Office application extensions to be written using .NET, and also enables the creation of Office documents which will deliver and execute them. Even better, an Office Add-In can be associated with a specific Office application and once it is installed, the Add-In will load and execute every time that application is launched - no need for persistance workarounds like creating scheduled tasks!
A VSTO Add-In can be packaged along with the Office document used to run it, but can also be fetched from a remote host when the document is opened. The latter technique is more difficult for the attacker; they would have to sign the Add-In using a trusted certificate, for example. The Deep Instinct researchers provide a proof-of-concept which can deliver a Meterpreter payload.
Vilkomir-Preisman, Shaul, No Macro? No Worries. VSTO Being Weaponized by Threat Actors, blog post, 2 February 2023. Available online at https://www.deepinstinct.com/blog/no-macro-no-worries-vsto-being-weaponized-by-threat-actors.
Traffic Light Control Software Vulnerable; Could Cause Gridlock
Last week's eight industrial control systems advisories from the Cybersecurity & Infrastructure Security Agency were mostly routine, but one has caused more than the usual level of activity, largely because of the (lack of) response from the vendor concerned. According to a report in The Stack, Econolite's traffic light controller software carries a critical vulnerability (CVE-2023-0452) with a CVSS score of 9.8. The vulnerability relates to CWE-328: Use of Weak Hash, and - you guessed it - it's our old friend MD5 again, turning where it shouldn't: an authentication subsystem. In fact, this can lead to unauthenticated access to a configuration file.
According to the report, the Econolite software is used by over 400 agencies to control lights at over 57,000 intersections, although not all are Internet-accessible. Even with access, an attacker can really only adjust the timing on the lights, prioritizing traffic in one direction and causing long tailbacks in the other; fortunately it is apparently not possible to turn all lights green simultaneously.
The biggest concern, however, is that Econolite has not responded in any way to the CISA advisory and has not released a patch for the problem, unlike the firms behind the other seven vulnerabilities of the week.
Targett, Ed, Critical controller bug could trigger traffic chaos: Software vendor ignores CISA outreach, The Stack, 27 January 2023. Available online at https://thestack.technology/econolite-traffic-controller-vulnerability-cisa-ics/.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.