Les Bell and Associates Pty Ltd
Site blog
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
NIST Selects Algorithm as Lightweight Cryptography Standard
Since 2018, the National Institute of Standards and Technologies has been working with industry and academic researchers in a multi-round review process to select a standard algorithm for protecting information created and transmitted on the Internet of Things.
While some devices on the IoT, such as cloud and fog computing services, have plenty of compute power, others, such as tiny sensors and actuators, have to operate on small batteries for periods of months or years. At the extreme low-power end we find such things as embedded medical devices, stress sensors inside roads and bridges and keyless entry fobs for cars, and these need 'lightweight' cryptographic algorithms which provide an acceptable level of security, but coupled with compact code size and memory usage, low energy consumption and acceptable speed.
The NIST review process started with 57 submissions, which were whittled down to 10 finalists before the final winner was selected. [Reaches for sealed envelope.] And the winner is . . . Ascon, a family of seven different algorithms, of which some or all will become part of the NIST lightweight cryptography standard. Ascon was developed in 2014 by a team of cryptographers from Graz University of Technology, Infineon Technologies, Lamarr Security Research and Radboud University, and had already been selected as the primary choice for lighweight authenticated encryption in the CAESAR competition, so it has a strong pedigree.
Authenticated encryption with associated data (AEAD) assures confidentiality of its encrypted payload, but also assures the authenticity of origin of associated data such as plaintext message headers and routing information. For higher-powered devices, these functions are typically performed by AES (FIPS 197) in Galois Counter Mode (SP 800-38D), but Ascon provides a good replacement for IoT devices. Similarly, while SHA2-256 is a widely-used hashing algorithm, Ascon fits the bill well for low-powered devices.
Uncredited, NIST Selects ‘Lightweight Cryptography’ Algorithms to Protect Small Devices, news release, 7 February 2023. Available online at https://www.nist.gov/news-events/news/2023/02/nist-selects-lightweight-cryptography-algorithms-protect-small-devices.
Multiple XSS Vulnerabilities in Document Management Systems
Rapid7 security researcher Matthew Kienow has duscovered multiple cross-site scripting (XSS) vulnerabilities in on-premises installations of open-source and freemium document management systems from four different vendors. The vulnerabilities and their statuses are listed below
| Vendor | Product | Version | CVE Number |
Patch Status |
|---|---|---|---|---|
| ONLYOFFICE | Workspace | 12.1.0.1760 | CVE-2022-47412 | Unpatched |
| OpenKM | OpenKM | 6.3.12 | CVE-2022-47413 | Unpatched |
| OpenKM | OpenKM | 6.3.12 | CVE-2022-47414 | Unpatched |
| LogicalDOC | LogicalDOC CE/Enterprise | 8.7.3/8.8.2 | CVE-2022-47415 | Unpatched |
| LogicalDOC | LogicalDOC CE/Enterprise | 8.8.2 | CVE-2022-47416 | Unpatched |
| LogicalDOC | LogicalDOC CE/Enterprise | 8.7.3/8.8.2 | CVE-2022-47417 | Unpatched |
| LogicalDOC | LogicalDOC CE/Enterprise | 8.7.3/8.8.2 | CVE-2022-47418 | Unpatched |
| Mayan | Mayan EDMS | 4.3.3 | CVE-2022-47419 | Unpatched |
In general, the XSS vulnerabilities arise because the products are not properly sanitizing and escaping <img> and <script> elements either in the uploaded documents, the in-app messaging system, the document filename field in an upload form or elsewhere in the application.
The Rapid7 blog post provides a full explanation of each vulnerability, along with a simple proof-of-concept which users can try in order to test their own installations. The PoC safely triggers a JavaScript alert() popup, but clearly much more sophisticated exploitation is possible (and the blog post discusses a few).
Mitigation suggestions include not allowing untrusted users to upload documents, but remediation really depends upon fixes being released by the vendors - none of whom had responded in a timely fashion.
Beardsley, Tod, Multiple DMS XSS (CVE-2022-47412 through CVE-20222-47419), blog post, 7 February 2023. Available online at https://www.rapid7.com/blog/post/2023/02/07/multiple-dms-xss-cve-2022-47412-through-cve-20222-47419/.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
Vastaamo Suspect Arrested in France
Regular readers will be familiar with the privacy breach which occurred at Finnish psychotherapy provider Vastaamo in September 2020. The company was infected by ransomware which encrypted their patient records and held them ransom (AFP, 2020). When the company CEO refused to negotiate with the attackers, they responded by releasing sensitive patient records on a Tor network server, and then turned to extorting payments from the patients themselves. It appears that the company's software was only minimally secured and did not comply with Finland's regulations for healthcare records systems. The CEO was terminated and the company subsequently liquidated (Ralston, 2021).
Now comes news (Krebs, 2023) that, following the issue of an arrest warrant in October 2022 for the offences of 1 ) Aggravated computer break-in, offence 2) Aggravated extortion, attempt 3) Aggravated dissemination of information violating personal privacy 4) Extortion 5) Attempt of an extortion 6) Computer break-in 7) Message interception and 8) Falsification of evidence, a suspect has been detained in France.
Aleksanteri Tomminpoika Kivimäki, 25, had uploaded a large archive of patient data to the dark web, but made the mistake of including other files from his own home directory - including the ~/.ssh directory, in which the known_hosts file made particularly interesting reading for investigators. However, his arrest was purely coincidental - French police were responding to a domestic violence report and only identified Kivimäki after he had presented a fake Romanian ID.
It turns out that Kivimäki has a long history of hacking offences, but since most of them were committed while he was still a juvenile, resulting in very light penalties. Apparently he did not learn his lesson, and it seems likely that if, as expected, he is extradited to stand trial in Finland, he will face a much stiffer penalty this time.
AFP, 'Shocking' hack of psychotherapy records in Finland affects thousands, The Guardian, 27 October 2020. Available online at https://www.theguardian.com/world/2020/oct/26/tens-of-thousands-psychotherapy-records-hacked-in-finland.
Krebs, Brian, Finland's Most-Wanted Hacker Nabbed in France, Krebs on Security blog, 5 February 2023. Available online at https://krebsonsecurity.com/2023/02/finlands-most-wanted-hacker-nabbed-in-france/.
Ralston, William, They Told Their Therapists Everything. Hackers Leaked It All, Wired, 4 May 2021. Available online at https://www.wired.com/story/vastaamo-psychotherapy-patients-hack-data-breach/.
CISA Releases ESXiArgs Ransomware Recovery Script
The Cybersecurity & Infrastructure Security Agency has released a recovery script for organizations that have fallen victim to ESXiArgs ransomware infecting their VMware ESXi servers. ESXiArgs encrypts configuration files, making virtual machines unusable. CISA recommends organizations impacted by ESXiArgs evaluate the script and guidance provided in the Github project's README file to determine if it is fit for attempting to recover access to files in their environment.
The ESXiArgs exploit was first disclosed by CERT-FR in an alert on 3 February entitled "Exploitation campaign of a vulnerability affecting VMware ESXi". According to CERTFR, the exploit affects unpatched VMware ESXi servers, specifically:
- ESXi 7.x versions earlier than ESXi70U1c-17325551
- ESXi versions 6.7.x earlier than ESXi670-202102401-SG
- ESXi versions 6.5.x earlier than ESXi650-202102101-SG
VMWare claims that the vulnerability (CVE-2021-21974), is a heap overflow in the OpenSLP code of ESXi, and was patched back in February 2021.
CERT-FR, [MàJ] Campagne d’exploitation d’une vulnérabilité affectant VMware ESXi, Bulletin D'Alerte, 3 February 2023. Available online at https://www.cert.ssi.gouv.fr/alerte/CERTFR-2023-ALE-015/.
CISA, ESXiArgs-Recover, github project, 8 February 2023. Available online at https://github.com/cisagov/ESXiArgs-Recover.
Dutch Police Dismantle Exclu Secure Messaging Service
The Dutch police, who have previously demonstrated considerable skill in infiltrating criminal networks, have racked up another win by breaking into the Exclu encrypted messaging service and ultimately dismantling it. Exclu, which had an estimated 3,000 users, was first investigated by German authorities in June 2020, and they shared their intelligence with their Dutch colleagues. This allowed them to intercept the communications of criminal networks for a period of five months.
During the culminating action last week, 1,200 police officers were deployed; 45 people were arrested in the Netherlands and Belgium, including the administrators and owners of Exclu and 79 locations in the Netherlands, Germany and Poland were searched. Two drug laboratories were dismantled, 300,000 ecstasy tables and 20 firearms were seized along with 200 phones which will be forensically examined. €5.5 million was also confiscated.
Eurojust, New strike against encrypted criminal communications with dismantling of Exclu tool, press release, 6 February 2023. Available online at https://www.eurojust.europa.eu/news/new-strike-against-encrypted-criminal-communications-dismantling-exclu-tool.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
Former Ubiquiti Engineer Pleads Guilty to Data Theft, Extortion
A former employee at network form Uniquiti has pleaded guilty to allegations of stealing confidential data, extorting a ransom and causing the publication of misleading news articles. Nickolas Sharp misused his admin privileges to access the company's AWS and GitHub accounts, stealing gigabytes of confidential data. To cover his tracks, he changed the log retention policies, altered other files and used a Surfshark VPN service - but did not realise that an Internet outage at his home had exposed his real IP address.
Once the breach was discovered, Sharp was one of those tasked with remediating it - but he simultaneously sent an extortion demand to his employer, demanding payment of BTC50 - which, at that time, was approximately $US2 million - to return the data and disclose a purported backdoor, and when the company refused to pay, he leaked some of the data.
However, by now the FBI had tracked his IP address and executed a search warrant at his home in Portland, OR. He denied all involvement and stated that he had not previously used Surfshark - only to be confronted with records showing that he had set up a Surfshark account six months before the breach. To this, he claimed that someone else must have used his PayPal account.
Proving the truth of the old adage that when you're in a hole, you should stop digging, Sharp then contacted various tech news outlets, posing as a whistleblower and claiming that Ubiquiti had been hacked by an unknown actor who had gained root privileges. The publication of these stories caused Ubiquiti's stock price to fall by 20% - a drop of over $US4 billion in market capitalization.
Having pleaded guilty to one count of transmitting a program to a protected computer that intentionally caused damage, one count of wire fraud, and one count of making false statements to the FBI, Sharp now faces up to 35 years in prison. His actual sentence will be handed down in May.
Biase, Nicholas, Former Employee Of Technology Company Pleads Guilty To Stealing Confidential Data And Extorting Company For Ransom, press release, 2 February 2023. Available online at https://www.justice.gov/usao-sdny/pr/former-employee-technology-company-pleads-guilty-stealing-confidential-data-and.
OpenSSH 9.2/9.2p1 Released
The OpenSSH project has released OpenSSH 9.2/9.2p1, which fixes a number of security bugs. Prime among them is CVE-2023-25136, a pre-authentication double-free memory fault, which first appeared in 9.1 and is not believed to be exploitable. Double-free faults occur when a programmer calls malloc() (or equivalent) to allocate memory once, but then somehow calls free() twice - potentially allowing remote code execution
The vulnerabilitiy occurs in the unprivileged pre-auth process which is subject to a chroot() and is further sandboxed by the OpenSSH privilege separation architecture - although the main sshd runs with root privileges, a new connection causes a forked child to change to the effective UID of the connecting user.
The vulnerability was first disclosed by Mantas Mikulenas, who discovered it when an old version of PuTTY caused the child sshd process to crash with a "seccomp violation" error. The new version is available from the OpenSSH mirrors, and binaries for different platforms should flow through repositories shortly.
Mantas M., Bug 3522 - Crash with "free(): double free detected" with old clients, bug report, 15 January 2023. Available online at https://bugzilla.mindrot.org/show_bug.cgi?id=3522.
Uncredited, OpenSSH 9.2/9.2p1 (2023-01-02), release note, 2 February 2023. Available online at https://www.openssh.com/releasenotes.html.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
2048-bit RSA Cracking Within Reach?
Most contemporary public-key cryptosystems are based on so-called trspdoor functions, which are special cases of one-way functions - functions which are easy to compute one way, but hard to reverse. There are two problems in widespread use: first, integer multiplication, for which the reverse problem, factorization of large composite integers, rapidly becomes very inefficient as the numbers get larger. This is the basis of the RSA public-key cryptosystem.
The second example is the discrete logarithm problem: raising an integer \(g\) to a power \(x\) is very fast, but the reverse - figuring out what power \(x\) a given integer, \(g\), was raised to in order to obtain a specified value \(h\) (finding the logarithm to the base \(g\) of \(h\)), is inefficient. In practice, we make both of these problems much harder by using modular arithmetic. This is the basis of the Diffie-Hellman key agreement protocol as well as the Elgamal cryptosystem.
The generation of RSA public and private keys starts by finding two large prime numbers, \(p\) and \(q\), and multiplying them to produce a large composite modulus \(N\), which becomes part of the public key. RSA would be broken if an attacker could quickly factorize \(N\).
For years, we have known that increases in compute power would therefore progressively weaken RSA. We have also known that improved factorization algorithms would further weaken it. And most of all, we have feared that the development of practical quantum computers could break it.
A new preprint paper which escaped my attention at the time suggests that a team of Chinese scientists may have taken advantage of all these possibilities to develop a technique which brings cracking of 2048-bit RSA keys within reach. In their paper, the researchers used quantum approximation algorithms, running on a quantum computer with 10 superconducting qubits, in combination with a classical lattice reduction algorithm, to factor integers up to 48 bits in size.
But what makes this result particularly interesting - or concerning - is that the algorithm is sublinear in the number of qubits required: \(\mathcal{O}(2N/\log{N})\). The authors suggest that their algorithm could therefore break a 2048-bit RSA modulus using a 372-qubit quantum computer. This is very much more practical than the millions of qubits that would be required by more straightforward approaches such as Shor's algorithm (because of the overhead of error correction).
Now, quantum computers of that size already exist in the public sphere - IBM's Osprey, for example is a 433-qubit machiine. And we do not know what exists inside the data centers of communications intelligence agencies world-wide; anyone who has a larger computer with the capability of breaking public-key crypto is obviously not going to talk about it.
My back-of-an-envelope calculations indicate that a 3072-bit RSA modulus - the smallest recommended for the NSA's Commercial National Security Algorithm Suite - could be cracked by a 531-qubit machine, while a 4096-bit RSA modulus would require a 683-qubit machine.
I do not believe the sky is falling - yet. However, I think this is something of a wake-up call - first, to users who are still using relatively small (1024-bit or 2048-bit) RSA keys, but also to security architects and regulators who have not yet started to prepare for the adoption of post-quantum cryptographic schemes. Personally, I long ago moved to 3072-bit RSA keys and subsequently to elliptic curve keys, which are not vulnerable to this particular attack. But I think it is now time to give serious consideration to a post-quantum escape plan.
Yan, Bao, et al, Factoring integers with sublinear resources on a superconducting quantum processor, arXiv preprint, 23 December 2022. Available online at http://arxiv.org/abs/2212.12372.
Collins, Hugh, IBM Unveils 400 Qubit-Plus Quantum Processor and Next-Generation IBM Quantum System Two, press release, 9 November 2022. Available online at https://newsroom.ibm.com/2022-11-09-IBM-Unveils-400-Qubit-Plus-Quantum-Processor-and-Next-Generation-IBM-Quantum-System-Two.
MITRE Releases Cyber-Resilience Design Tool
The pendulum of cybersecurity fashion is starting to swing away from playing whack-a-mole with vulnerabilities via pen-testing, then the same game with the remaining vulnerabilities via incident response, towards engineering cyber-resilient systems which are harder and will both slow intruders down and limit their abilities to penetrate further. This approach has most recently been advocated by NIST's Ron Ross and his team, in SP 800-160 volume 2, Developing Cyber-Resilient Systems: A Systems Security Engineering Approach.
Now, MITRE has joined the party, with a new tool called the Cyber Resiliency Engineering Framework (CREF) Navigator. Rather similar to MITRE's ATT&CK and D2FEND databases, the CREF Navigator provides a useful visualization of the various techniques which can be used to develop cyber-resilient systems, and maps them to the corresponding ATT&CK Tactics and Techniques, as well as the ATT&CK Mitigations and their effect on the adversary actions.
The CREF Navigator is organized around four fundamental goals:
- Anticipate: informed preparedness for adversity
- Withstand: Continue essential mission or business functions despite adversity
- Recover: Restore mission or business functions during and after adversity
- Adapt: Modify mission or business functions, and/or supporting capabilities, to prepare for predicted changes in the technical, operational or threat environments.
The four goals are supported by eight underlying objectives, such as Prevent or Avoid, Prepare, Constrain, Understand and Re-Architect. The techniques are many and varied, such as dynamic reconfiguration, redundancy by means of backup & restore, spare capacity or replication, and various forms of deception.
As well as the Navigator, there is also an Inspector, which allows further drilling down, and Map, which shows the relationships between Goals, Objectives and Techniques. Finally, a Visualizer shows relationships both within CREF and also between ATT&CK and CREF.
Uncredited, Getting Started, web documentation, undated. Available online at https://crefnavigator.mitre.org/gettingStarted.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
Google Search Returns Malicious Loaders for Malware Attacks
Researchers at SentinelLabs have identified a series of virtualized .NET malware loaders which are being distributed via malicious ads placed through Google and displayed in search results. The researchers encounter these loaders while investigating malvertising attacks; all that was required was a simple Google search for "Blender 3D" and the ads were returned.
The loaders are implemented in .NET and use vitualization, based on the KoiVM virtualizing protector, to obfuscate their implementation and execution. Although SentinelLabs dubbed these loaders MalVirt, it seems likely that they are related to the KoiVM loader detected a few months ago by K7 Security Labs. The MalVirt malware applies an unusual level of anti-analysis and anti-detection techniques to its payloads, which include a feature-rich infostealer from the Formbook family that is capable of keylogging, screenshot theft, theft of web and other credentials and staging of other malware.
The Formbook malware is more commonly delivered as malmail attachments; switching to malverts is a response to the default blocking of MS Office VBA (Visual Basic for Applications) macros. While popular with criminal groups, it has also been used by state-affiliated groups, as reported by Ukraine's CERT.
Milenkoski, Aleksandar and Tom Hegel, MalVirt | .NET Virtualization Thrives in Malvertising Attacks, blog post, 2 Februart 2023. Available online at https://www.sentinelone.com/labs/malvirt-net-virtualization-thrives-in-malvertising-attacks/.
Threat Actors Use Visual Studio Tools for Office to Deploy Malware
There are many other responses to Microsoft's default blocking of VBA macros: wrapping them in .ZIP and similar archives, or even .ISO images, so that the wrapper would carry the Mark of the Web, but the macro would not, or using shortcut (.LNK) files. Now, Deep Instinct researchers have uncovered a new technique: using Microsoft's Visual Studio Tools for Office (VSTO) to develop Office Add-Ins.
VSTO allows these Office application extensions to be written using .NET, and also enables the creation of Office documents which will deliver and execute them. Even better, an Office Add-In can be associated with a specific Office application and once it is installed, the Add-In will load and execute every time that application is launched - no need for persistance workarounds like creating scheduled tasks!
A VSTO Add-In can be packaged along with the Office document used to run it, but can also be fetched from a remote host when the document is opened. The latter technique is more difficult for the attacker; they would have to sign the Add-In using a trusted certificate, for example. The Deep Instinct researchers provide a proof-of-concept which can deliver a Meterpreter payload.
Vilkomir-Preisman, Shaul, No Macro? No Worries. VSTO Being Weaponized by Threat Actors, blog post, 2 February 2023. Available online at https://www.deepinstinct.com/blog/no-macro-no-worries-vsto-being-weaponized-by-threat-actors.
Traffic Light Control Software Vulnerable; Could Cause Gridlock
Last week's eight industrial control systems advisories from the Cybersecurity & Infrastructure Security Agency were mostly routine, but one has caused more than the usual level of activity, largely because of the (lack of) response from the vendor concerned. According to a report in The Stack, Econolite's traffic light controller software carries a critical vulnerability (CVE-2023-0452) with a CVSS score of 9.8. The vulnerability relates to CWE-328: Use of Weak Hash, and - you guessed it - it's our old friend MD5 again, turning where it shouldn't: an authentication subsystem. In fact, this can lead to unauthenticated access to a configuration file.
According to the report, the Econolite software is used by over 400 agencies to control lights at over 57,000 intersections, although not all are Internet-accessible. Even with access, an attacker can really only adjust the timing on the lights, prioritizing traffic in one direction and causing long tailbacks in the other; fortunately it is apparently not possible to turn all lights green simultaneously.
The biggest concern, however, is that Econolite has not responded in any way to the CISA advisory and has not released a patch for the problem, unlike the firms behind the other seven vulnerabilities of the week.
Targett, Ed, Critical controller bug could trigger traffic chaos: Software vendor ignores CISA outreach, The Stack, 27 January 2023. Available online at https://thestack.technology/econolite-traffic-controller-vulnerability-cisa-ics/.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
ESET Releases APT Activity Report for 2022
Security software and services firm ESET has released its APT Activity Report T3 2022, covering the last three months of the year. The report summarises the campaigns of threat actors affiliated with several states: China, Iran, North Korea and Russia (not that one should imagine for a moment that other countries don't have similar groups).
Not unexpectedly, the primary target of Russian-linked groups was Ukraine, against which they deployed an array of wipers and ransomware - for example, the notorious Sandworm group reappeared, this time with a new wiper targeting the Ukrainian energy sector (always a favourite Russian target in winter - it was also the target of Russian missile attacks this time).
Meanwhile, the Pandas - the China-aligned groups - seemed to shift their focus even more towards Europe, although some groups such as LuckyMouse and MirrorFace are continuing to target the S.E. Asian region, hitting companies in Hong Kong and also running a spearphishing campaign against Japanese political entities. The Iranian groups were more concerned with the Middle East, of course - primarily Israel and Israeli companies' overseas operations.
North Korean APT's are focused on financial rewards, targeting cryptocurrency firms and exchanges - a useful workaround for a country beset by financial sanctions.
The report provides a useful technical overview of the various campaigns with lots of links to more detailed reports, along with lists of targeted countries and regions, as well as industry sectors.
Boutin, Jean-Ian, ESET APT Activity Report T3 2022, blog post, 31 January 2023. Available online at https://www.welivesecurity.com/2023/01/31/eset-apt-activity-report-t3-2022/.
ImageMagick Vulns Lead to DoS, Arbitrary File Disclosure
One of the all-time-great secret tools of command line ninjas is the ImageMagick program suite, which can be used from the command line to convert graphic file formats and resize images without a whole lot of mousing around. The command-line nature of the ImageMagick convert utility means that is often used on web servers to downsize uploaded high-resolution images 'on the fly', so as to not waste bandwidth for viewers who will only see a smaller version on the final page anyway.
Now comes the disclosure of two 0day vulnerabilities discovered by Mexican security firm Metabase Q:
- CVE-2022-44267 - A DoS vulnerability triggered when parsing a PNG image with a filename consisting of a single dash ("-")
- CVE-2022-44268 - An information disclosure vulnerability that could be exploited to read arbitrary files from a server when parsing an image
Like many command-line utiliities, the ImageMagick programs will interpret a filename argument of '-' as a reference to the standard input stream (stdin), rather than an actual file (in *ix systems, files and devices are treated the same way anyway). Since web site image processing is usually based on actual files, there will be no data on stdin, and the process will block, waiting for input. Of course, that will affect only that thread or process, rather than the entire web server or system, but if that '-' was embedded on every page . . .
The second vulnerability could be more severe; it abuses the structure of a PNG file to get ImageMagick to read and incorporate an arbitrary file into the output image. Metabase Q's proof-of-concept, for example, retrieves the content of /etc/passwd, which could conceivably enumerate some user and system accounts, although it would have to be a really old system to contain password hashes. But other files, some considerably more sensitive, could be retrieved this way.
The vulnerabilities exist in ImageMagick versions up to and including 7.1.0-49; they were fixed in version 7.1.0-52, which was released in November 2022 and should have percolated through repositories by now and have been updated by switched-on site admins. I'll still be using my updated ImageMagick.
Gonzales, Bryan, ImageMagick: The hidden vulnerability behind your online images, blog post, undated. Available online at https://www.metabaseq.com/imagemagick-zero-days/.
Google Expands Fuzzer Reward Program
Since 2017, Google has run an OSS-Fuzz Reward Program to encourage the use of fuzz testing in the open source community. Lest you think this is an obscure little corner of software testing, let me point out there is money in it: the OSS-Fuzz Reward Program has awarded over $US600,000 to over 65 different contributors for their assistance.
Now, Google has announced many new types of rewards which expand the scope of the program, covering contributions such as integration of new sanitizers to find new vulnerabilities, notable FuzzBench integrations, and project fuzzing coverage increase. The total possible rewards for a project integration has increased by 50% to $US30,000, depending on the criticality of the project.
The firm has also continued to add new language support and tools to the OpenSSF FuzzIntrospector tool, which was integrated into OSS-Fuzz last year.
Chang, Oliver, Taking the next step: OSS-Fuzz in 2023, blog post, 1 February 2022. Available online at https://security.googleblog.com/2023/02/taking-next-step-oss-fuzz-in-2023.html.
OpenAI Escalates Arms Race With Itself
Your humble scribe counts himself lucky to have retired from academia just as artificial intelligence tools like ChatGPT have made it possible for students to submit realistic essays that were not written by the student himself (nor by a for-hire essay-writing service). Detecting automated plagiarism of this kind can be quite tricky; those who have played with ChatGPT - which must be all of us, by now - know that its output reads easily, although a sequence of conversations will reveal a certain underlying structure that never varies.
The main drawback of ChatGPT is the fact that it was pre-trained in 2021 and is not aware of developments since then. It also has a nasty characteristic that is a dead giveaway: it will cite non-existent papers and will confess, when pushed, that it lied. Given time, though, both of these will be overcome. But even in the meantime, it will take a human marker far longer to investigate possible plagiarism than a student would do in creating it. How, then, to detect AI-written submissions?
OpenAI to the rescue! The firm has, inevitably, trained a classifier to distinguish between human-written and AI-generated text from a variety of providers. It's not very good yet; in testing it accurately categorized 26% of AI-written text as "likely AI-written" but incorrectly categorized 9% of human-written text as being the work of an AI (false positives). However, this represents a significant improvement over the previous classifier.
Of course, the classifier has to be trained on a corpus consisting of pairs of AI- and human-written text on the same topic; something that is expensive to arrange, especially on some topic areas, and could conceivably be gamed to bias the classifier. And reliability will be much lower when applied to topics that the classifier has not been trained on.
It was inevitable that one solution to a problem posed by AI would be AI, even if this puts OpenAI into an arms race with itself. But at least the firm is engaging with educators and others to discuss these problems, via a feedback form and other resources.
Kirchner, Jan Hendrik, Lama Ahmad, Scott Aaronson and Jan Leike, New AI classifier for indicating AI-written text, blog post, 31 January 2023. Available online at https://openai.com/blog/new-ai-classifier-for-indicating-ai-written-text/.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
More Baseband Management Controller Vulns Threaten Server Supplies
Last month we wrote about vulnerabilities in the AMI MegaRAC Baseboard Management Controller software, posing a risk to servers from many manufacturers including DELL EMC, HP Enterprise, and Lenovo. Now security firm Eclypsium, who found and disclosed three vulnerabilities, has updated its advisory to add two new vulnerabilities which it had not disclosed, in order to allow AMI to develop mitigations.
The new vulnerabilities are:
- CVE-2022-26872 (CVSS score: 8.3) - Password reset interception via API
- CVE-2022-40258 (CVSS score: 5.3) - Weak password hashes for Redfish and API
The AMI security advisory is somewhat uninformative, but NVD classifies the first vulnerability as a weak password recovery mechanism for forgotten passwords, while the second seems to relate to the use of weak hashing algorithms - specifically, MD5 with a single global salt. Customers should check with their server vendors to see whether they have released an update to address these issues - several already have.
Babkin, Vlad, Supply Chain Vulnerabilities Put Server Ecosystem at Risk, blog post, 5 December 2022. Available online at https://eclypsium.com/2022/12/05/supply-chain-vulnerabilities-put-server-ecosystem-at-risk/.
VBA Macros Install Monero Cryptominer
A new report from Fortiguard Labs researcher Xiaopeng Zhang explains how an unidentified threat actor is using malicious Visual Basic for Applications (VBA) macros to install the ever-popular XMRig cryptominer, hijacking the victim's computer to mine Monero cryptocurrency.
Three different Excel documents were discovered, each of which carries a VBA project which, when the spreadsheet is opened, will cause Excel to pop up the usual security warning about macros having been disabled. Of course, we all know what many users will do in response to this: they will click the "Enable Content" button. The spreadsheet in fact encourages this through a nice trick: it displays a blurred graphic, tricking the user into thinking the image will clear if the content is enabled.
Once the VBA code is running, it downloads a binary executable from a C2 server, saving it to the system Templates folder and renaming it before executing it. Like the VBA code itself, this binary is obfuscated, but deobfuscation reveals it to be a .Net executable which, in turn, carries a gzip-compressed .Net DLL. This is extracted in memory and then loaded, before being executed. This code is also extensively obfuscated and also contains functions to detect tampering at runtime, making it very difficult to analyse, but the code is a malware loader and installer, with the payload in the .Net module.
The next stage is to gain persistence, which is done by create a task in TaskScheduler, before loading and decoding its configuration block and initiating communication with the C2 server. After uploading information gathered from the victim system - CPU type, current user name, etc. - the malware receives commands, typically to download further files from Microsodt OneDrive. The first of these is used to perform process hollowing, replacing the code of an innocuous-looking AddInProcess.exe with the content of the second, which is the xmrig.exe cryptominer.
It is a long and convoluted process, most of which is intended to obscure the nature of the attack and prevent analysis.
Zhang, Xiaopeng, Analyzing Malware Code that Cryptojacks System to Mine for Monero Crypto, blog post, 31 January 2023. Available online at https://www.fortinet.com/blog/threat-research/malicious-code-cryptojacks-device-to-mine-for-monero-crypto.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
KeePass Vulnerability Allows Plaintext Export of Entire Password Database
Many security professionals use the KeePass open-source password manager - it is free, lightweight and versatile, while not exposing a large attack surface. However, a newly-revealed vulnerability (CVE-2023-24055) suggests that some caution might be necessary, at least until a fix or workaround appears.
KeePass is configured by the KeePass.config.xml file in the program directory. If an attacker can edit this file, they can add a trigger which will export the password database when it is initially opened, without the user being asked to confirm this - it will happen invisibly in the background. The view of the KeePass developers is that if an attacker has that level of access to the machine, it is game over already - but our view is that this represents a significant privilege escalation which will gain the attacker access to many other systems.
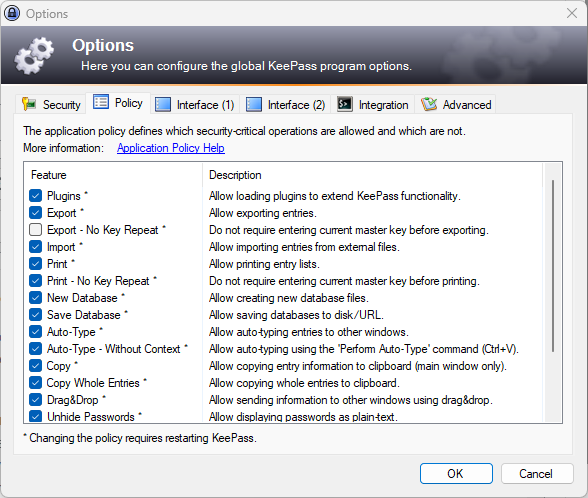
One suggestion is to use "Tools" -> "Options" -> "Policy" and then deselect "Export - No Key Repeat", but the same argument makes this suggestion moot: an attacker who has that level of access to the machine can disable that setting and execute the attack. Perhaps the best approach for the time being, especially for those who must allow others access to a shared system, is to run the Portable version of KeePass off a USB key. A write-protected KeePass.config.enforced.xml file is another option. But in all these cases, a sophisticated attack can bypass these measures.
With PoC code now available, expect a KeePass database export feature to be added to many infostealers.
Chris, If an attacker modifies the xml config file . . ., discussion thread, 28 December 2022. Available online at https://sourceforge.net/p/keepass/discussion/329220/thread/a146e5cf6b/.
QNAP Pushes Update to Fix SQL Injection Remote Code Execution Vulnerability
NAS vendor QNAP has warned customers to update their devices' firmware in order to fix a critical remote code execution vulnerability (CVE-2022-27596). The vulnerability, which has a CVSS 3.1 score of 9.8, seems to relate to improper sanitization of special elements in SQL (CWE-89).
Users are urged to update to QTS 5.0.1.2234 build 20221201 or later (5.0.1.2248 seems to be current) or QuTS hero h5.0.1.2248 build 20221215 or later. Most users who have automatic firmware update checks enabled and log in to their devices regularly will already have updated, so this is mainly a reminder for those who let the months go by, lulled into a tranquil state by the reliability of NAS devices in typical SME settings.
Uncredited, Vulnerability in QTS and QuTS hero, security advisory, 30 January 2023. Available online at https://www.qnap.com/en/security-advisory/qsa-23-01.
Microsoft Reminds Sleepy Exchange Admins: Patch!
In a similar vein, Microsoft's Exchange Team has blogged, reminding admins that it is critical to keep Exchange servers updated; this shouldn't really be necessary, as Exchange has proved to be fertile ground for attackers in recent years - remember ProxyShell, ProxyNotShell, ProxyOracle and all the rest? - and Exchange admins really ought to be in a permanently paranoid and jittery state.
As Redmond's reminder points out, this means installing the latest available Cumulative Update (CU) and Security Update (SU) on all Exchange servers as well as on Exchange Management Tools workstations. The problem is that email access is so critical in an always-connected, 24 x 7 x 52 world that admins find it hard to schedule even brief downtime.
Additional Exchange controls are a good idea, including enabling Windows Extended Protection, which mitigates MitM attacks, as well as enabling certificate signing of PowerShell serialization payloads. Attackers love to use PowerShell in Exchange attacks, especially for exploiting Active Directory. The blog post provides lots of other useful tips.
The Exchange Team, Protect Your Exchange Servers, blog post, 26 January 2023. Available online at https://techcommunity.microsoft.com/t5/exchange-team-blog/protect-your-exchange-servers/ba-p/3726001.
MD5 Lives On To Bite Samba Users
An interesting article by Paul Ducklin for Sophos' Naked Security blog makes a plea for cryptographic agility - the somewhat obvious idea that we must be willing to abandon old cryptoprimitives as the prove weak. This is an especially important notion given the possibility that someone, somewhere - who will never let on that they have it, for obvious reasons - builds a quantum computer that is able to break the most popular public-key cryptoprimitives.
That day does not seem to be upon us quite yet, but older algorithms are vulnerable to attacks using classical computer hardware, especially GPU's, and a leading example is the birthday paradox attack on the older hash algorithms, such as MD5. The complexity of a birthday paradox attack is \(2^{n/2}\) operations, where \(n\) is the length of the digest, in bits.
Now, MD5 produces a 128-bit digest, which means that a birthday paradox attack can be achieved in only \(2^{64}\) - or approximately \(1.85 \times 10^{19}\) - attempts. This might seem like a large number, but it's not - and it can be cut down massively using a technique called a chosen-prefix collision, which works by making slight changes to initially-identical strings to quickly find two different strings which still produce the same digest value. This process takes only seconds.
Some authentication code in Samba is a holdover from the days of Windows 2000, when Microsoft introduced the use of RC4 encryption with an MD5 HMAC (hash-based message authentication code). The vulnerability arises from the use of a single round of MD5 to compute a digest over the data to be authenticated before calculating the HMAC over that; an attacker who knows the plaintext data can create another set of plaintext which will generate the same digest value, and insert that into the data stream without being detected. Somebody probably inserted this extra digest calculation in an attempt to improve authentication security, not realising that it actually weakened the protocol.
Since most systems have this old HMAC-MD5 authentication disabled, it was never detected as a serious problem, but attackers could negotiate the authentication protocol down and make use of this - hence CVE-2022-38023, which was fixed by Microsoft in November last year, and which could allow an attacker to insert malicious packets into the SMB protocol and achieve a privilege escalation attack. The whole sad tale is a lesson that keeping old versions of protocols around for backward compatibility can lead to disaster (which is why it is so important to configure web servers to not allow the older versions of the TLS and SSL protocols).
Ducklin, Paul, Serious Security: The Samba logon bug caused by outdated crypto, blog post, 30 January 2023. Available online at https://nakedsecurity.sophos.com/2023/01/30/serious-security-the-samba-logon-bug-caused-by-outdated-crypto/.
Stevens, Marc, Arjen Lenstra and Benne de Weger, Vulnerability of software
integrity and code signing applications to chosen-prefix collisions for
MD5, web page, 30 November 2007. Available online at https://www.win.tue.nl/hashclash/SoftIntCodeSign/.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
We're back! Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
IAPP Report Highlights Challenges for Responsible Use of AI
The latest Privacy and AI Governance Report from the International Association of Privacy Professionals (IAPP) explores the state of artificial intelligence (AI) governance through interviews with stakeholders in the tech, life sciences, telecommunications, banking, staffing and retail industries in North America, Europe and Asia. The interviews focused on where the stakeholders' organizations stood on five areas: governance, risk, processes, tools and skills.
The results show that formulating and deploying clear governance guidelines for the responsible use of AI is a challenging and complex task; the most mature organizations have rolled out responsible practices, but constitute only 20% of organizations surveyed. 10% of responding organizations have not yet formulated responsible AI guidelines, with the remainder in the process of including responsible AI in the governance or 'about to start' doing so.
The use of AI exposes enterprises to a whole new risk landscape. Perhaps the most obvious risk is bias in AI which results in harm to individuals, with consequent fines and judgements. This is further complicated by the changing regulatory environment, which has led to a lack of legal clarity surrounding the use of AI systems.
However, in 80% of organizations, guidelines for ethical use of AI consist only of high-level policy statements and strategic objectives, with no clear plan for how these can be achieved. While some tools do exist for addressing privacy and ethical risks of AI, the selection of these is difficult, as the field is rapidly evolving and lacks robust concepts and definitions.
Koerner, Katharina, and Jake Frazier, Privacy and AI Governance Report, International Association of Privacy Professionals, January 2023. Available online at https://iapp.org/media/pdf/resource_center/privacy_ai_governance_report.pdf.
DOJ Disrupts Hive Ransomware Variant
The US Department of Justice has revealed that, since July 2022, the FBI has penetrated the networks of the Hive ransomware group, captured its decryption keys and offered them to over 1,300 victims worldwide, so that they were spared paying up to $US130 million in ransoms. It also announced that, in coordination with German law enforcement (the German Federal Criminal Police and Reutlingen Police Headquarters-CID Esslingen) and the Netherlands National High Tech Crime Unit, it has seized control of the servers and websites that Hive uses to communicate with its members, disrupting Hive's ability to attack and extort victims.
Like many other ransomware developers, the Hive group offered ransomware-as-a-service (RaaS). The core group maintained the core software as well as the web infrastructure for C2 and payment processing, while recruiting affiliates who would perform initial compromise and deployment in exchange for 80% of the proceeds. The Hive developers also operated the Hive Leak Site, which would publish data exfiltrated from victims who refused to pay the extortion demand.
Uncredited, U.S. Department of Justice Disrupts Hive Ransomware Variant, press release, 26 January 2023. Available online at https://www.justice.gov/opa/pr/us-department-justice-disrupts-hive-ransomware-variant.
Mimic Ransomware Uses Old Conti Code, Everything DLL API
Researchers from Trend Micro have discovered and analysed a new piece of ransomware which is partly based on old code from the Conti ransomware, as well as abusing the API's of a Windows local search engine tool called Everything. The new ransomware, christened Mimic, targets Russian and English-speaking users.
Analysis shows that Mimic is deployed as a dropper which unpacks several files, including a 7zip executable which is used to extract the malware payload from a password-protected archive called Everything64.dll - the genuine Everything search functionality is in Everything32.dll. After extracting its files, it copies them to a random directory under %LocalAppData% and renames the ransomware binary to bestplacetolive.exe.
Mimic seems to be highly capable; it can bypass UAC, disable Windows Defender, prevent system shutdown, prevent itself being killed, disable Windows telemetry, disable sleep mode, terminate multiple applications and services, and delete shadow copies. As it runs, it queries the Everything_SetSearchW() function to selectively match or avoid files for encryption, and it adds a .QUIETPLACE extension to the files that it encrypts.
Trend Micro's report includes suggested mitigations, as well as IoC's.
Morales, Nathaniel, Earle Maui Earnshaw, Don Ovid Ladores, Nick Dai and Nathaniel Gregory Ragasa, New Mimic Ransomware Abuses Everything APIs for its Encryption Process, blog post, 26 January 2023. Available online at https://www.trendmicro.com/en_us/research/23/a/new-mimic-ransomware-abuses-everything-apis-for-its-encryption-p.html.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
Software Supply Chain Poisoned By Phishing Campaigns
Research performed jointly by application security testing firm Checkmarx and open-source supply chain security firm Illustria has brought to light a massive campaign which targets naive end users with compromised packages containing links to phishing campaigns. The threat actors behind the campaign, which appears to be highly automated, published over 144,000 packages to the NuGet, NOM and PyPi repositories - the vast majority to NuGet.
The names of the packages mostly relate to hacking, cheats and free resources, for example "free-steam-codes-generator" and "yalla-ludo-diamond-hack". Victims were also promised increased social media followers or likes. The descriptions of all the packages also contained links to phishing sites - perhaps an attempt to increase the SEO ranking of the phishing sites by linking them to legitimate sites like NuGet.
Over 65,000 unique URL's in 90 domains were used to host realistic and well-designed web pages, with some even including fake interactive chatbots that appeared to be delivering the cheats, but generally the victims were asked to perform a 'human verification' process that led them through a maze of sites which asked them social engineering questions, finally redirecting to legitimate ecommerce sites with referral ID's - so that if the victim makes a purchase, the threat actors will earn a commission.
Harush, Jossef, How 140k NuGet, NPM, and PyPi Packages Were Used to Spread Phishing Links, blog post, 14 December 2022. Available online at https://checkmarx.com/blog/how-140k-nuget-npm-and-pypi-packages-were-used-to-spread-phishing-links/.
Microsoft Reclassifies SPNEGO Vuln as Critical - Patch Now
SPNEGO is the Simple and Protected Negotiation Protocol - part of the 'plumbing' that goes around Active Directory, Kerberos and similar authentication protocols to allow negotiation of the security mechanism to be used. In the Windows world, it is used by application protocols like SMB (Server Message Block) and RDP (Remote Desktop Protocol), among others, so select the appropriate authentication mechanism from those supported by a client and a server.
Also in the Windows world, it is the subject of a vulnerability which Microsoft patched back in September. At that point, CVE-2022-37958 was categorised as an invormation disclosure vulnerability. However, IBM X-Force Red Security researcher Valentina Palmiotti discovered that the vulnerability could allow unauthenticated attackers to remotely execute code.
Successful exploitation might require multiple attempts, and so its CVSS 'exploit complexity' rates as High, meaning that with all other categories at the highest level, the overall CVSS score of this vulnerability is 8.1, and Microsoft has reclassified the vulnerability as 'Critical'. In order to give users time to patch, IBM will not release full technical details until at least April 2023.
Thompson, Chris, Critical Remote Code Execution Vulnerability in SPNEGO Extended Negotiation Security Mechanism, IBM Security Intelligence blog, 13 December 2022. Available online at https://securityintelligence.com/posts/critical-remote-code-execution-vulnerability-spnego-extended-negotiation-security-mechanism/.
GitHub Requires 2FA From March 2023
During 2023 GitHub is going to gradually roll out a requirement for developers to use two factor authentication. Over the year, distinct groups of users will be required to enable 2FA; the gradual rollout will enable GitHub to make adjustments as larger groups are enrolled to 2FA later in the year.
The exact criteria GitHub will use to allocate membership in these groups will not be made public, but broadly the criteria are:
- Users who published GitHub or OAuth apps or packages
- Users who created a release
- Users who are Enterprise and Organization administrators
- Users who contributed code to repositories deemed critical by npm, OpenSSF, PyPI, or RubyGems
- Users who contributed code to the approximate top four million public and private repositories
Users will start receiving reminders 45 days before the 2FA deadline, and will have a week to enroll, after which they will be blocked from accessing GitHub until 2FA is enabled.
Swanson, John, Raising the bar for software security: next steps for GitHub.com 2FA, blog post, 14 December 2022. Available online at https://github.blog/2022-12-14-raising-the-bar-for-software-security-next-steps-for-github-com-2fa/.
Examples of Cloud Credential Abuse
A short article from Palo Alto Networks' Unit 42 provides a couple of examples of how attackers are able to leverage stolen cloud service API credentials to pursue objectives such as phishing, cryptomining and data theft.
Alon, Dror, Compromised Cloud Compute Credentials: Case Studies From the Wild, blog post, 8 December 2022. Available online at https://unit42.paloaltonetworks.com/compromised-cloud-compute-credentials/.
Saturday Funny
No comment about the dangers of the Internet of Things is required; just see https://twitter.com/vxunderground/status/1603508551569252360. Shodan.io FTW!
Happy Holidays!
This will be the last security news headlines blog post for 2022, as we take a break for the holiday season. We'll be back in January, although we may post before then if there are any major news events. Until then, we wish all readers a happy holidays season!
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.