Les Bell and Associates Pty Ltd
Blog entries about Les Bell and Associates Pty Ltd
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
Golang SAML Library Allowed Authentication Bypass
One of the more popular distributed authentication protocols for web services is SAML, the Security Assertions Markup Language. When a user wants to authenticate to a service provider, she obtains a SAML assertion from her identity provider (to which she has previously authenticated using - probably - multi-factor authentication). She will then relay the SAML assertion to the service provider, which will validate the assertion and - because it trusts the identity provider - will then trust the user.
However, because the SAML assertion passes through the hands of the putative user, who could tamper with it, the assertion must be signed. But a twist in the way SAML assertions are constructed has led to a vulnerability (CVE-2022-41912), discovered by Google's Project Zero, in the crewjam SAML library for the Go programming language. A single SAML XML element can contain multiple assertions, and the crewjam library only validated the signature on the first. An attacker could therefore construct a SAML message containing one signed assertion and one or more unsigned assertions, allowing an authentication bypass awarded a CVSS score of 9.1.
There are no workarounds for this vulnerability - the only fix is to updated to crewjam/saml version 0.4.9 or later.
crewjam, crewjam/saml vulnerable to signature bypass via multiple Assertion elements due to improper authentication, security advisory, 2 December 2022. Available online at https://github.com/advisories/GHSA-j2jp-wvqg-wc2g.
Florida Man Gets 18 Months for Part in SIM Swap, Crypto Heist
A US District Court sentenced a Florida man to 18 months in prison last week for his part in a cryptocurrency theft which netted over $US20 million. US Attorney Damian Williams said,
"Nicholas Truglia and his associates stole a staggeting amount of cryptocurrency from the victim through a complex SIM swap scheme. Nevertheless, today's sentencing goes to show that no matter how sophisticated the crime is, this Office will continue to successfully prosecute those who choose to defraud others."
SIM swapping, also known as phone number porting, allows an attacker to link a victim's phone number to a new Subscriber Identity Module controlled by the attacker. Once this has been done, mTAN's (mobile transaction authentication numbers) and other messages sent to the victim will be received by the attacker, who can use this to access the victim's accounts.
In this case, the attackers were able to obtain access to the vctim's cryptocurrency wallet, and used Truglia's online account to plunder the victim's wallet, converting the proceeds into Bitcoin and then dividing up the loot. Truglia's share amounted to roughly $US673,000. In addition to his 18 month sentence, Truglia, aged 25, was sentenced to 3 years of supervised release, ordered to forfeit $US983,010.72 and further ordered to pay $US20,379,007 in restitution to the victim within 60 days.
Biase, Nicholas, Florida Man Sentenced To 18 Months For Theft Of Over $20 Million In SIM Swap Scheme, press release, 1 December 2022. Available online at https://www.justice.gov/usao-sdny/pr/florida-man-sentenced-18-months-theft-over-20-million-sim-swap-scheme.
Compromised Android Platform Certificates User to Sign Malware
Malware reverse engineer Łukasz Siewierski has discovered a new exploit against Android mobile devices. Android apps are signed with private keys and validated with the matching certificates. In particular, platform certificates (and their keys) are used - by platform vendors like Samsung, LG and others - to sign the 'android' application on the system image, which runs with a highly privileged user ID, android.uid.system, and holds system permissions including permissions to access user data.
Any other application signed with the same certificate can declare that it wants to run with the same user ID, getting the same level of privileged access.
Now it appears that some platform certificates have been leaked or stolen - as long ago as 2016 - and used to sign malware samples. Searching for the SHA2-256's of some of the samples on VirusTotal shows they are backdoors, loaders and various other exploits which remain undetected by most engines. Fortunately, in the last few days, the various affected platform vendors have rotated their keys and issued updates, and Google has also added detections in the Google Play Store as well as their Build Test Suite.
However, the extent to which these signed malware samples spread in the wild is unknown.
antho...@google.com, Issue 100: Platform certificates used to sign malware, APVI issue, 12 November 2022. Available online at https://bugs.chromium.org/p/apvi/issues/detail?id=100.
Siewierski, Łukasz, New AVPI entry: platform certificates used to sign malware, tweet, 1 December 2022. Available online at https://twitter.com/maldr0id/status/1598068216391405568.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
Google Shows Benefits of Memory Safe Languages
Operating systems and high-performance applications (especially for low-powered devices) have traditionally been written in the C and C++ programming languages, which suffer from problems with safe memory management. C, in particular, relies on the programmer correctly matching malloc() (and similar) function calls, which allocate memory blocks, with the corresponding free() calls - something that is particularly tricky in interrupt-driven and multi-threaded code. Forgetting to call free() results in memory leaks and swap file growth, while calling free() more than once on the same pointer will corrupt the heap (or the equivalent structure in the underlying OS). Worse still are use-after-free vulnerabilities - and we haven't yet mentioned buffer overflows, which are probably the most exploited class of vulnerabilities over many decades.
Yet memory-safe languages - Pascal, Ada, Java and others - have been available for decades and only resisted on grounds of efficiency. The most recent and most efficient examples, like Kotlin and Rust, have arrived at a time when processors are so powerful that efficiency is no longer a problem, and so support for Rust is being introduced into the Linux kernel and has already been introduced into the Android mobile OS.
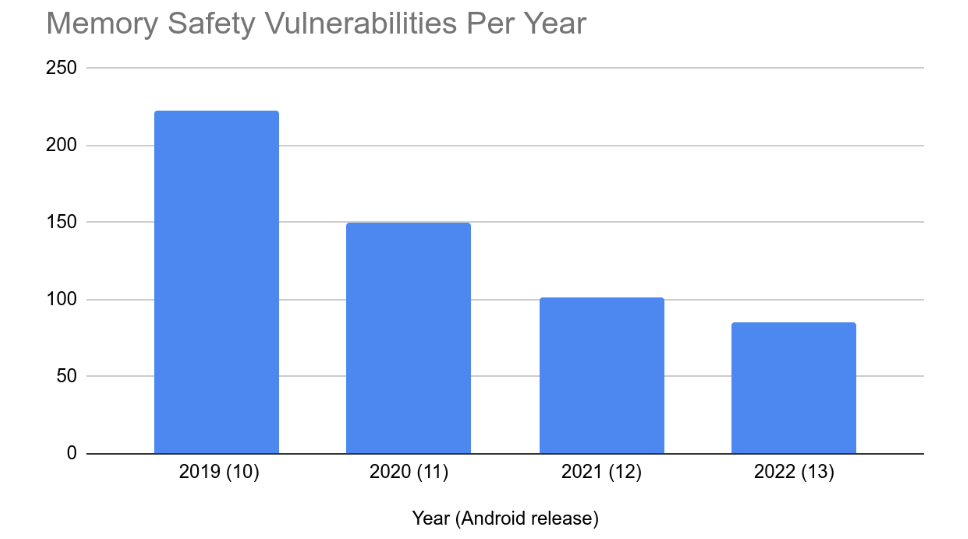 In a blog post, Google provides statistics that show how the introduction of memory-safe languages into Android has dramatically reduced that class of vulnerability. From 2019 to 2022 the annual number of reported memory safety vulnerabilities has gone from 223 down to just 85. It's no coincidence that 2022's Android 13 is the first release where most new code is in a memory safe language, and that 2022 is the first year where the majority of vulnerabilities do not relate to memory safety.
In a blog post, Google provides statistics that show how the introduction of memory-safe languages into Android has dramatically reduced that class of vulnerability. From 2019 to 2022 the annual number of reported memory safety vulnerabilities has gone from 223 down to just 85. It's no coincidence that 2022's Android 13 is the first release where most new code is in a memory safe language, and that 2022 is the first year where the majority of vulnerabilities do not relate to memory safety.
This is good for security; to date, there have been no memory safety vulnerabilities discovered in Android's Rust code.
Of course, this change is not the only contributor to reducing vulnerabilities in Android; the existing C/C++ is being hardened using a variety of tools, although the fact that most of Andoid's API's are implemented in Java also helps. The Google blog post provides some useful ammunition for developers who want to persuade their shops to migrate to memory-safe languages.
Vander Stoep, Jeffrey, Memory Safe Languages in Android 13, Google Security Blog, 1 December 2022. Available online at https://security.googleblog.com/2022/12/memory-safe-languages-in-android-13.html.
CISA Warns of Cuba Ransomware
The FBI and the US Cybersecurity & Infrastructure Security Agency have issued a joint cybersecurity advisory concerning the increased activities of Cuba ransomware operators. Cuba, which is not associated with the Republic of Cuba, was first observed in 2021, and by mid-2022 its operators had compromised over 100 entities worldwide, demanding over $US145 million in ransom payments, of which $US60 million was paid.
Their primary targets are the financial services, government, healthcare, manufacturing and IT sectors, mostly in the US, and their tactics, techniques and procedures have continued to evolve, exploiting new vulnerabilities for initial compromise and then using a variety of tools for privilege escalation. There also seems to be a link between the Cuba threat actors, the Industrial Spy ransomware and the operators of the RomCom remote access trojan, with the Cuba group selling data exfilatrated by their ransomware via Industrial Spy's online market and also deploying the RomCom RAT.
The CISA advisory provides a complete rundown, including IOC's and MITRE ATT&CK techniques.
Uncredited, #StopRansomware: Cuba Ransomware, cybersecurity advisory alert AAA22-335A, 1 December 2022. Available online at https://www.cisa.gov/uscert/ncas/alerts/aa22-335a.
Android Trojan Steals Facebook Logins
While Android security continues to improve (see above), the mobile OS still has its unfair share of trojaned apps which are being disseminated through the Google Play Store as well as stores which permit side-loaded apps. Zimperium zLabs has documented a long-running Android threat campaign, dubbed the Schoolyard Bully Trojan, which has spread to over 300,000 victims, stealing their Facebook credentials.
Disguised as legitimate educational applications providing books on a range of topics, primarily for Vietnamese readers, these apps are trojaned with a Facebook-specific infostealer, grabbing the victims' email, phone number, password, name and Facebook ID. In many cases, naive users re-use the same password for both Facebook and also for financial accounts, making this campaign even more profitable. Despite the Vietnamese language focus, Zimperium found over 300,000 victims across 71 countries.
The campaign's techniques are also interestinmg - the credential theft is achieved via JavaScript injection; the legitimate Facebook login URL has additional, injected, code which extracts the user's credentials and then sends it to the threat actor's Firebase C2 site. The malware also uses native libraries as an evasion technique, getting past the majority of antivirus products, including those which use machine learning, and it encodes the exfiltrated data to hide it from detection mechanisms.
Gupta, Nipun, Schoolyard Bully Trojan Facebook Credential Stealer, blog post, 1 December 2022. Available online at https://www.zimperium.com/blog/schoolyard-bully-trojan-facebook-credential-stealer/.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
LastPass Hit Again
On their web site, LastPass is notifying customers of another security incident which appears to be a follow-up to the previous incident, in August. Back then, an unidentified threat actor was able to gain access to LastPass' development environment, obtaining some source code and technical information. The incident was contained, and no customer data - especially customer password vaults - were accessed.
However, it seems the attackers got something useful. In the latest incident, the firm detected unusual activity within a third-party cloud storage service which is shared by LastPass and its sister company GoTo (GoToMeeting, GoToConnect). Having once again retained the services of Mandiant, the company has determined that an unauthorized party - likely the same threat actor - used information obtained in the earlier breach to gain access to some customer information, although customer passwords will, of course, be encrypted.
It sounds as though cloud access credentials were embeded somewhere in the stolen source - a perennial, and intractable, problem when you need code to access external services. And you can bet that if customer password vaults were stolen, the attackers will be inspecting LastPass' code, looking for implementation flaws in the encryption.
Toubba, Karim, Notice of Recent Security Incident, blog post, 30 November 2022. Available online at https://blog.lastpass.com/2022/11/notice-of-recent-security-incident/.
MD5 Considered Harmful
The Commission Nationale de l'Informatique et des Libertés (the data protection regulator in France) has handed down a decision which should give software developers everywhere pause to consider their code. The regulator fined energy company Électricité de France (EDF) €600,000 over customer privacy issues. Part of the judgement dealt with routine privacy matters such as sending commercial emails, data collection for undefined purposes and unreliable handling of data access and deletion requests.
But the final part dealt specifically with insecure handling of passwords. Generally-accepted good practice says that passwords should be salted and then hashed using a suitably strong digest algorithm - and EDF claimed that it was doing this. However, in reality it was still storing the passwords of over 25,000 customers as unsalted MD5 hashes.
MD5, which produces a 128-bit digest, is deprecated by virtually all regulators and standards authorities (as is SHA-1, which produces a 160-bit digest). But it was the lack of salt that really troubled the French regulator, especially since, while they had now adopted SHA2-512 for later passwords, they still had 2.4 million SHA2-512 unsalted digests. Although EDF had cleaned up their act and were now both salting and hashing correctly, they were still fined.
My advice (and it's what I've taught in university courses): at the very least, make use of language facilities for password salting and hashing, such as PHP's password_hash() and password_verify() functions, which randomly salt a password and hash it with the bcrypt (or optionally, argon2) hash function. Better still, use PBKDF2 (Password-Based Key Derivation Function 2) which will apply a user-specified number of iterations of the chosen hash function, and also incorporates salt. By choosing a large number of iterations, we increase the work factor for both users and attackers - but since users normally only enter their password once, they will barely notice the delay, while attackers trying brute force and dictionary attacks will really be slowed down.
Ducklin, Paul, Serious Security: MD5 considered harmful - to the tune of $600,000, blog post, 30 November 2022. Available online at https://nakedsecurity.sophos.com/2022/11/30/serious-security-md5-considered-harmful-to-the-tune-of-600000/.
New Backdoor Exploits Old Redis Vulnerability
Researchers at cloud security firm Aqua Security have observed a new piece of malware which attempted to exploit one of their honeypots using CVE-2022-0543, a vulnerability in the Redis in-memory database. Redis is widely deployed on web servers, particularly for page caching, although it has many other applications where a high-performance non-relational database is required. CVE-2022-0543 is a vulnerability in the Debian (and Ubuntu) library for the Lua scripting language engine which is a core component of Redis.
By connecting to a vulnerable Redis server, the attacker is able to execute Redis commands which effectively clone a Redis server that contains a shared library, exp_lin.so, which contains the exploit. Once this is loaded, the attacker is able to escape the Lua scripting engine sandbox and execute arbitrary commands - one of which downloads the new malware, named Redigo.
The malware, which as the name suggests is written in the Go programming language, mimics the Redis communications protocol to connect to its C2 server, after which the victim turns into a Redis client with the attacker becoming the server. The commands sent to the infected machine indicate that the goal is to exploit the Redis server itself, rather than the underlying host.
Aqua's report provides a full analysis with IOC's - useful since, being a new malware sample, VirusTotal did not identify Redigo. A bigger question, however, is why new malware is appearing for a vulnerability that was patched back in February - clearly, attackers are still finding victims, which indicates poor vulnerability management processes.
Yaakov, Nitzan and Ofek Itach, Aqua Nautilus Discovers Redigo - New Redis Backdoor Malware, threat alert, 1 December 2022. Available online at https://blog.aquasec.com/redigo-redis-backdoor-malware.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
Google Threat Analysis Group Uncovers Commercial Spyware
Google's Threat Analysis Group (TAG) has detailed an exploitation framework which they uncovered when an anonymous submitter disclosed three bugs to the Chrome bug reporting program. The bugs, each accompanied by instructions and a source code archive, are:
- Heliconia Noise: a web framework for deploying an exploit for a Chrome renderer bug followed by a sandbox escape
- Heliconia Soft: a web framework which deploys a PDF containing a Windows defender exploit
- Files: a set of Firefix exploits for Linux and Windows
The vulnerabilities were patched by the respective vendors in 2021 and early 2022, but were likely used as 0days prior to that. The first two exploits end with a launcher DLL that fetches the exploitation agent from a URL and then launches it - they were supplied with a dummy agent called agent_simple and it is likely that, in reality, this will be replaced by a customized agent.
Heliconia Noise includes a pre-commit cleaning script which checks that the produced binaries do not contain sensitive strings, such as the project name, developer names, etc. Ironically, this script leaks all of these, including the name of the company behind this project, Variston IT. Variston Information Technology is a small Barcelona-based company which, it claims, offers "tailor made Information Security Solutions". From these exploits, it seems that Variston has joined the ranks of NSO Group, Cytrox and others in offering commercial spyware.
Lecigne, Clement and Benoit Sevens, New details on commercial spyware vendor Variston, blog post, 30 November 2022. Available online at https://blog.google/threat-analysis-group/new-details-on-commercial-spyware-vendor-variston/.
North Korean Backdoor Uses Google Drive for C2
ESET researchers have reported on a newly-analyzed backdoor called Dolphin, deployed by North Korean group APT37 (ScarCruft, Reaper) against targets in South Korea. First detected in early 2021, Dolphin was used in a watering-hole attack on a South Korean online newspaper, in that case being deployed as the final stage of the attack via an Internet Explorer exploit and some shellcode which loaded another APT37 backdoor called BLUELIGHT. Most attacks ended with BLUELIGHT, but ESET discovered that, on selected targets, BLUELIGHT was then used to download and chain to Dolphin.
While BLUELIGHT can exfiltrate selected files upon command, Dolphin extends this capability to active searching of drives and the exfiltration of files with extensions of interest. Backdoor initially reports some basic information about the victim system (name, username, OS version, local and external IP addresses, installed security products, check for debugger and other tools such as Wireshark) and then downloads commands, issued by its operators, from Google Drive storage, executing them and uploading the results.
Dolphin's commands give it extensive capabilities apart from file exfiltration. It can also search connected portable devices such as smartphones, using the Windows Portable Device API, perform screenshots and keylogging, download and execute shellcode, run aribtrary shell commands and perform credential stealing. Another interesting trick found in some versions is to downgrade the security of a user's Google account, by enabling IMAP access to GMail and then enabling "less secure app access", presumably to backdoor the Google account.
The ESET report provides a full analysis of the evolution of Dolphin, as well as MITRE ATT&CK techniques and IOC's.
Jurčacko , Filip, Who's swimming in South Korean waters? Meet ScarCruft's Dolphin, blog post, 30 November 2022. Available online at https://www.welivesecurity.com/2022/11/30/whos-swimming-south-korean-waters-meet-scarcrufts-dolphin/.
China-related Cyberespionage Campaign Targets Philippines - Also SE Asia, Asia-Pacific, US and Europe
Mandiant Managed Defense has lifted the lid on a cyberespionage campaign being run in the Philippines by a Chinese nexus group tracked as UNC4191. Although the campaign leveraged USB devices to infect machines in the Philippines, the targeted organizations were based in other locations around the world.
After initial infection via the USB's, the threat actor used legitimately-signed binaries to side-load malware, including three new families Mandiant named MISTCLOAK, DARKDEW and BLUEHAZE. This would lead to deployment of a renamed NCAT binary which created a reverse shell on the victim's system, gaining the thread actor backdoor access. The malware would also replicate itself by infecting any new USB drives plugged into the system.
Timestamps in binaries date back to September 2021, indicating that this campaign may have been running for some time, especially considering the self-propagating nature of the malware. The range of both public- and private-sector entities targeted suggest that the campaign objective is collection of intelligence related to China's political and commercial interests.
The Mandiant report provides a full analysis, including YARA rules and IOC's.
Tomcik, Ryan, John Wolfram, Tommy Dacanay and Geoff Ackerman, Always Another Secret: Lifting the Haze on China-nexus Espionage in Southeast Asia, blog post, 28 November 2022. Available online at https://www.mandiant.com/resources/blog/china-nexus-espionage-southeast-asia.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
![]() Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
Crypto Exchange Breached
I've been ignoring the litany of bad news surrounding cryptocurencies: declining values, rugpulls, collapsing exchanges and all the rest - but I couldn't resist this one.
Canadian crypto exchange Coinsquare, which claims to be "Canada's trusted platform to securely buy, sell and trade Bitcoin, Ethereum, and more", has emailed customers to notify them that it had discovered a "data incident" in which an unauthorized third party accessed a customer database which contains customer names, email addresses, residential addresses, phone numbers, dates of birth, device IDs, public wallet addresses, transaction history, and account balances".
Coinsquare's email stated - just as many other recently-breached companies have - that "No passwords were exposed. We have no evidence any of this information was viewed by the bad actor". If we have learned one thing from all the recent breaches, it is that many companies have inadequate monitoring of the traffic exiting their networks, so that information exfiltration goes undetected.
I'd suggest taking a wait-and-see approach on this one.
Munawa, Frederick, Major Canadian Crypto Exchange Coinsquare Says Client Data Breached, Coindesk, 27 November 2022. Available online at https://www.coindesk.com/tech/2022/11/26/major-canadian-crypto-exchange-coinsquare-says-client-data-breached/.
CISA Adds Two New Exploited Vulnerabilities
On Monday, the US Cybersecurity & Infrastructure Security Agency added two new vulnerabilities to its Known Exploited Vulnerabilities Catalog, indicating that they were now being exploited in the wild.
One is the heap buffer overflow vulnerability in the Google Chrome GPU process (CVE-2022-4135) which we covered last Saturday, and for which Google rushed out an update.
The other is an as-yet-unspecified vulnerability in Oracle Fusion Middleware Access Manager; the OpenSSO Agent can easily be exploited to grant an unauthenticated attacker network access and take over the Access Manager. The vulnerability (CVE-2021-35587) has a CVSS 3.1 base score of 9.8 (CVSS Vector: CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H).
The vulnerability impacts versions 11.1.2.3.0, 12.2.1.3.0 and 12.2.1.4.0, which should be updated as soon as possible - it already should have been, since Oracle issued a Critical Patch Update in January 2022, following disclosure by Jangggg of VNPT and peterjson - Security Engineering - VNG Corporation. Which raises the question: why, one year on, is CISA seeing active exploitation?
CISA, Known Exploited Vulnerabilities Catalog, web page, 28 November 2022. Available online at https://www.cisa.gov/known-exploited-vulnerabilities-catalog.
Killnet Brags of Starlink and whitehouse.gov DDoS Attacks
Trustwave reports that the Russian state-linked threat actor, Killnet, claims to have launched successful DDoS attacks against a number of targets in the US and UK.
The group claims that on November 18, it, along with several other hacker groups, ran a DDoS attack against Starlink, the SpaceX-operated satellite Internet access provider - presumably as retribution for the company's provision of ground stations to Ukraine. Starlink's 3,00 low-earth orbit satellites provide high-bandwidth, low-latency Internet access - ideal for use by Ukrainian defending forces. The claim is supported by a Reddit thread in which users complained that they could not log in to their Starlink accounts.
The previous day, the group also claims, they ran a 30-minute attack on the official site of the White House, whitehouse.gov (which they claimed had 'military state protection against DDOS'!), and a few days later they DDoS'ed the site of the Prince of Wales, princeofwales.gov.uk, promising future attacks against other UK government, financial and healthcare sites. Again,the motivation appears to be those countries' support for Ukraine
SpiderLabs Research, Killnet Claims Attacks Against Starlink, Whitehouse.gov and United Kingdom Websites, blog post, 23 November 2022. Available online at https://www.trustwave.com/en-us/resources/blogs/spiderlabs-blog/killnet-claims-attacks-against-starlink-whitehousegov-and-united-kingdom-websites/.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
![]() Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
GitHub, PyPi Used to Spread Malicious Python Packages to Naive Users
We have previously reported on attempts to poison the software supply chain via the creation of trojaned Python packages on GitHub and promoted via the PyPi package repository. Generally, this method relies on naive developers making use of the packages in their projects and thereby infecting unsuspecting victims.
However, a new campaign is attracting the victims directly, targeting the victims via a viral TikTok craze. A TikTok filter called "Invisible Body" removes the body of a video's subject, replacing it with a blurred contour image, and a trending craze, "Invisible Challenge", dares people to film themselves naked, then post the resultant "Invisible Body"-processed video.
This is where the cunning attacker comes in: via TikTok videos, he offers some software called "unfilter" which claims to be able to remove the "Invisible Body" filter effect. His videos have attracted over a million views inside just a few days, and over 30,000 people have responded by following the instructions to join a Discord server which, in turn sends an automated message asking the victim to 'star' a GitHub repository (boosting its apparent popularity) and download the malicious Python package. This carries the WASP stealer, which will plunder Discord accounts, passwords, crypto wallets, credit cards and other files from the victim's computer.
Be careful what you ask for; if it seems too good to be true . . .
Nachson, Guy and Tal Folkman, Attacker Uses a Popular TikTok Challenge to Lure Users Into Installing Malicious Package, blog post, 28 November 2022. Available online at https://checkmarx.com/blog/attacker-uses-a-popular-tiktok-challenge-to-lure-users-into-installing-malicious-package/.
Baseboard Management Controllers Bring Vulnerabilities to Internet of Things
Basedboard management controllers are system-on-a-chip devices originally intended for remote monitoring and management of computers; they have long been a feature of mainframes (where they were much larger boards) but over the last decade or so have made their way into server motherboards, where they provide low-level functionality such as network access to a hardware console, BIOS reflashing, power control, etc.
However, these chips are now finding their way into Internet of Things (IoT) and Operational Technology (OT) devices, where they are used to provide network services such as a web-based management dashboard. Taiwanese manufacturer Lanner Inc., which specialises in embedded applications, sells the IAC-AST2500A, a BMC-based expansion card with firmware based on AMI's MegaRAC SP-X, which is also used in popular servers.
A new report from network security specialist Nozomi Networks details thirteen vulnerabilities in the web interface of this card, not all of them remediated as of this date. They include command injections, stack-based buffer overflows, broken access control, session fixation, username enumeration and others, and several of them can be chained to permit remote code execution.
Uncredited, Vulnerabilities in BMX Firmware Affect OT/IoT Device Security - Part 1, blog post, 22 November 2022. Available online at https://www.nozominetworks.com/blog/vulnerabilities-in-bmc-firmware-affect-ot-iot-device-security-part-1/.
Meta Cops Large Fine for Facebook Data Scraping Breach
The Irish Data Protection Commission (DPC) has announced the conclusion of its investigation of Meta Platforms Ireland Limited (MPIL) in relation to the release of the personal information of 533 million Facebook users. The DPC has imposed a fine of €265 million, along with a range of specific corrective measures.
The breach, which occurred in early 2020, exposed personal information such as the Facebook ID, name, gender, relationship status, occupation, email addressand phone number of each user, and was accomplished using a data scraper to mine and then correlate data from Facebook Search, the Facebook Messenger Contact Importer and the Instagram Contact Importer between May 2018 and September 2019. The data was then made available via a hacker forum.
The DPC found that MPIL had infringed two clauses of Article 25 of the EU General Data Protection Regulation:
- Taking into account the state of the art, the cost of implementation and the nature, scope, context and purposes of processing as well as the risks of varying likelihood and severity for rights and freedoms of natural persons posed by the processing, the controller shall, both at the time of the determination of the means for processing and at the time of the processing itself, implement appropriate technical and organisational measures, such as pseudonymisation, which are designed to implement data-protection principles, such as data minimisation, in an effective manner and to integrate the necessary safeguards into the processing in order to meet the requirements of this Regulation and protect the rights of data subjects.
- The controller shall implement appropriate technical and organisational measures for ensuring that, by default, only personal data which are necessary for each specific purpose of the processing are processed. 2That obligation applies to the amount of personal data collected, the extent of their processing, the period of their storage and their accessibility. 3In particular, such measures shall ensure that by default personal data are not made accessible without the individual’s intervention to an indefinite number of natural persons.
The Data Protection Commission is a key enforcement agency for the GDPR, since so many multinational tech companies base their European operations in Ireland.
Uncredited, Data Protection Commission announces decision in Facebook "Data Scraping" Inquiry, press release, 28 November 2022. Available online at https://www.dataprotection.ie/en/news-media/press-releases/data-protection-commission-announces-decision-in-facebook-data-scraping-inquiry.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
![]() Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
EUROPOL Coordinated Action Brings Down Caller ID Spoofing Site
Caller ID spoofing isn't particularly difficult, but it was made even easier by a site called iSpoof wihch allowed criminals to anonymously make spoofed calls impersonating banks, government agencies and retail companies, send recorded messages and - perhaps most significantly - intercept time-based one-time passwords or mTAN's. Now, following an investigation initiated by the Metropolitan Police in the UK, police forces in Europe, Australia, the US, Ukraine, Canada and other countries have simultaneously arrested 142 suspects, including the main administrator of the web site, and shut it down.
The investigation revealed that the website had earned over €3.7 mllion from its fee-paying criminal customers in just 16 months. However, victims in the UK alone had lost £43 million to the scams operated through the site, and worldwide losses were in excess of £100 million (€115 million).
Said Europol Executive Director, Ms Catherine De Bolle:
The arrests today send a message to cybercriminals that they can no longer hide behind perceived international anonymity. Europol coordinated the law enforcement community, enriched the information picture and brought criminal intelligence into ongoing operations to target the criminals wherever they are located. Together with our international partners, we will continue to relentlessly push the envelope to bring criminals to justice.
Uncredited, Action against criminal website that offered 'spoofinf' services to fraudsters: 142 arrests, press release, 24 November 2022. Available online at https://www.europol.europa.eu/media-press/newsroom/news/action-against-criminal-website-offered-%E2%80%98spoofing%E2%80%99-services-to-fraudsters-142-arrests.
ConnectWise XSS Vulnerability Allows Scammers to Masquerade As Legit
Tech support scams are one of the banes of modern world. Often run out of call centres in India and targetting the elderly and more vulnerable, these scams work by convincing the victim to download and install a remote access tool (whether knowingly or via trojaned download), handing control to the scammer so they can 'fix a malware infection' - in practice, they will do anything from demanding payment to fix a concocted 'infection' to plundering the victim's bank account.
The scammers will use any of several remote access tools, including TeamViewer, AnyDesk, LogMeIn or ConnectWise. Rather than pay for licensed copies of the software, the scammers will rely on the free trial version - often a good indication that the operation is not legitimate: for example, ConnectWise adds a prominent advisory message on the main page of all trial or free accounts.
However, as revealed by Guardio Labs, the customization features of this page - used by legitimate companies to brand their tech support portals - contains a cross-site scripting vulnerability which allows the scammers to disable the trial version advisory that would warn victims, by adding some JavaScript code to set the advisory message visibility property to 'hidden'. In fact, not only can scammers hide the advisory, they can use the customization features to masquerade as a legitimate tech support portal.
Guardio notified ConnectWise, who fixed the XSS vulnerability and completely removed the customization feature for trial and free accounts.
Tal, Nati, XSS Vulnerability Found in ConnectWise Remote Acces Platform With Great Potential For Misuse by Scammers, blog post, 24 November 2022. Available online at https://labs.guard.io/xss-vulnerability-found-in-connectwise-remote-access-platform-with-great-potential-for-misuse-by-scammers-a0773da2aacf.
Preventing Remote Code Execution Vulnerabilities
The increased exposure of RESTful and other API's on the public Internet has led to an increase in exploits such as Log4Shell and WannaCry which are able to perform remote code execution. These exploits make use of inadequate input sanitization, bugs in parsing libraries and even buffer overflows, not so much in the developers' own code - although that happens - but increasingly in libraries and frameworks which programmers make use of for standard functionality.
An article in Dark Reading summarizes a number of useful techniques that developer and admins can make use of in DevSecOps environments to proactively reduce the risk of RCE vulnerabilities. The major techniques are:
- Continuously run software composition analysis tools on your code base - for example, OWASP dependency-check for Java, or commercial tools like Snyk and Mend can report vulnerable third-party libraries
- Use static analysis security test (SAST) tools - e.g. Bandit for Python, GoSec for Golang or cross-language tools like SonarQube and SemGrp
- Avoid default error messages - these may provide useful linformation (such as stack traces) to attackers
- Configure everything as code - and use tools such as KICS and Checkov to scan configuration files for vulnerabilities before deployment
- Do not run code on native machines, and apply the Principle of Least Privilege - use containers and maintain a narrow set of permissions and privileges for each
- Employ dynamic analysis security test tools - e.g. ZAP to scan API's for vulnerabilties
Many of these tools can be integrated into the DevSecOps pipeline. Of course, all the usual secure coding guidelines also apply.
Manor-Liechtman, Gabriel, How Development Teams Should Respond to Text4Shell, Dark Reading, 24 November 2022. Available online at https://www.darkreading.com/dr-tech/how-development-teams-should-respond-to-text4shell.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
![]() Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
Google Rushes Out Patch for Chrome 0Day Vulnerability
Google has released an update for the Windows, Mac and Linux versions of the Chrome browser in order to mitigate CVE-2022-4135, a heap buffer overflow in Chrome's GPU Process. This vulnerability is being exploited in the wild, but details are scarce, since Google will restrict access to the details until a majority of users have updated their systems, especially if other projects depend upon it.
Bommana, Prudhvikumar, Stable Channel Update for Desktop, blog post, 24 November 2022. Available online at https://chromereleases.googleblog.com/2022/11/stable-channel-update-for-desktop_24.html.
Interpol Cracks Down on Online Fraud
A major international operation stared by INTERPOL in late June has now culminated in the arrest of almost 1,000 suspects who were allegedly engaged in a wide range of online scams and money laundering. At the same time, virtual assets worth $US129,975,440 were seized.
Opeeration HAECHI III specifically targeted vishing (voice phishing), romance scams, sextortion, investment fraud and money laundering associated with illegal online gambling, and was coordinated by INTERPOL's Financial Crime and Anti-Corruption Centre, involving 30 countries: Australia, Austria, Brunei, Cambodia, Cote d’Ivoire, France, Ghana, Hong Kong (China), India, Indonesia, Ireland, Japan, Korea, Kyrgyzstan, Laos, Malaysia, Maldives, Nigeria, Philippines, Poland, Romania, Singapore, Slovenia, South Africa, Spain, Sweden, Thailand, United Arab Emirates, United Kingdom, and the United States.
The investigators saw several new trends in financial crime, such as an increase in fraudulent investment schemes committed via instant messaging apps combined with cryptocurrency payments. In another case, the Austrian and Indian National Central Bureaus of INTERPOL identified a group of scammers who had been impersonating INTERPOL officers, relieving victims of $US159,000 via financial institutions, crypto exchanges and online gift cards. The Indian authorities raided the scammers' call centre, seizing four cryptocurrency wallets and other evidence.
The operation highlights the international nature of online cybercrime, and the need for cross-border cooperation by authorities.
Uncredited, Cyber-enabled financial crime: USD 130 million intercepted in global INTERPOL police operation, news release, 24 November 2022. Available online at https://www.interpol.int/News-and-Events/News/2022/Cyber-enabled-financial-crime-USD-130-million-intercepted-in-global-INTERPOL-police-operation.
RansomExx Gets Rusty
The RansomExx ransomware has been around since 2018, operated by a threat actor called DefrayX or Hive0091. The same group is also behind the PyXie malware, Vatet loader and Defray ransomware.
Now, like many other malware developers, DefrayX has switched their development from the C++ programming language to Rust. Although the Rust programming language has garnered attention from systems programmers because it is memory safe, it is drawing increased attention from malware developers because it can produce statically-linked stand-alone binaries and - perhaps more importantly - it has much lower detection rates when scanned by antivirus tools. Its large and complex binaries also make them harder for malware analysts to reverse engineer.
The new variant of RansomExx, dubbed RansomExx2, has similar functionality to its C++ progenitor - it is a command-line program which requires a list of directories to encrypt, passed as command-line arguments, and then performs encyption with AES-256 and wraps the AES keys with RSA encryption. IBM X-Force Threat Researchers have provided a comprehensive write-up on a sample.
Hammond, Charlotte, RansomExx Upgrades to Rust, blog post, 22 November 2022. Available online at https://securityintelligence.com/posts/ransomexx-upgrades-rust/.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
Aviation Industry A Ransomware Target?
A few days ago we wrote about the Daixin Team's attack on AirAsia, whose network they dismissively complained was so badly managed they were embarrassed to exploit it. However, Cyble has compiled a list of recent ransomware attacks on airlines around the world. Although not naming the airlines, they seem to be generally smallish, domestic or budget carriers in several countries:
- Malaysia
- Thailand
- Portugal
- Kuwait
Doubtless there are others which have gone unreported. And even the larger carriers are not immune - British Airways suffered an embarrassing supply-chain attack which resulted in the theft of customer credit card details.
The aviation industry was badly affected by COVID lockdowns which required budgets to be slashed. However, airlines also are custodians of a lot of sensitive data - some of it personal, some of it operational - and some systems with real safety implications, all of it highly interconnected to external systems and contractors. The fact that times are tough is not a good reason to drop your guard, unfortunately.
Uncredited, Aviation Industry Facing Ransomware Headwinds, blog post, 23 November 2022. Available online at https://blog.cyble.com/2022/11/23/aviation-industry-facing-ransomware-headwinds/.
Microsoft Warns of IoT Supply Chain Problems
In a blog post, Microsoft's Security Threat Intelligence team warn of a threat affecting Internet of Things (IoT) devices and operational technology (OT) networks which they may expose.
As security professionals are aware, IoT devices are often manufactured at low cost for a mass market, designed by engineers who focus on electronics and sensor technology and who rely on pre-packaged software in the form of operating systems, subsystems and programming languages for the system-on-a-chip controllers embedded into their designs. Just take a look at online tutorials for Raspberry Pi and similar devices, which generally rely on high-level Python code to read sensor inputs and control outputs, with the assumption that the underlying layers of the stack are a) reliable and b) secure.
The latter assumption, especially, is often invalid. In the particular case which triggered the blog post, an intrusion into electrical grid critical infrastructure in India, the initial intrusion point was an IoT device, and specifically an embedded web server, which is commonly used to provide either a user interface or API for devices. In this particular case, the server was the Boa web server, supplied as part of a software development kit for IoT devices, such as those provided by RealTek. The problem is that development and support of the Boa web server ceased in 2005. While patches for the Realtek SDK are available, they may not get through the entire supply chain to the final, shipped devices - let along to network owners and oeprators who acquire them.
Microsoft's blog post provides a list of recommended mitigations, primarily aimed at network operators - the IoT device designers seem to be a lost cause. . .
Castleman, Adam, et. al., Vulnerable SDK components lead to supply chain risks in IoT and OT environments, blog post, 22 November 2022. Available online at https://www.microsoft.com/en-us/security/blog/2022/11/22/vulnerable-sdk-components-lead-to-supply-chain-risks-in-iot-and-ot-environments/.
San Francisco Cops Seek Permission for Robots to Use Deadly Force
A little beyond the usual remit of security defenders, this story: the San Francisco Police Department is petitioning the city's Board of Supervisors for permission to deploy robots which are capable of killing suspects that officers believe are so dangerous that the "risk fo loss of life to members of the public or officers is imminent and outweighs any other force option available to SFPD".
Police forces now often use remote-controlled robots for tasks such as inspecting suspected explosive devices; as well as carrying cameras and manipulators, such robots can also fire a blank shotgun shell into a device in an attempt to harmlessly destroy the device, if not the robot as well. And such robots could also conceivably fire a live round. YouTube already has several videos which show robot dogs discharging automatic weapons at targets.
Unsurprisingly, this proposal is meeting with significant opposition. After all, what could possibly go wrong?
Tarantola, A., San Francisco police seek permission for its robots to use deadly force, Engadget, 23 November 2022. Available online at https://www.engadget.com/san-francisco-police-seek-permission-for-its-robots-to-use-deadly-force-183514906.html.
Fake VPN Apps Catch Android Users
Extensive advertising campaigns featuring masked, hoodie-wearing bad guys, coupled with the desire to access geo-restricted content, has motivated many individual consumers and SME operators to install virtual private network (VPN) client software, although for many cloud-hosted applications there is little to suggest that VPN's provide much additional security than the use of standard TLS everywhere.
Now ESET researchers warn of a campaign targeting Android device users with a fake SecureVPN web site which hosts a trojaned Android app. The threat actor behind this campaign is the Bahamut cyberespionage APT, which has been active since at least 2017, targeting victims in the Middle East and South Asia with spearphishing lures. This particular campaign and the associated malware appeared first in early 2022, hosted on a simple web site created with a free web template. The malicious domain was named thesecurevpn[.]com, playing on the legitimate product's domain at securevpn.com.
The fake VPN malware shares code with the earlier SecureChat campaign run by Bahamut; once it is installed it can exfiltrate a range of sensitive data from the victim's device, including contacts, SMS messages, device location, device accounts, recorded phone calls, device info including installed apps and a list of files on external storage. It can also extract information about cals made using a range of popular messaging apps including Facebook Messenger, Viber, WhatsApp, Telegram, WeChat and others.
ESET's report provides a full analysis including MITRE ATT&CK techniques and other IOC's.
Stefanko, Lukas, Bahamut cybermercenary group targets Android users with fake VPN apps, 23 blog post, 23 November 2022. Available online at https://www.welivesecurity.com/2022/11/23/bahamut-cybermercenary-group-targets-android-users-fake-vpn-apps/.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
![]() Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
Defenders Gift Bad Guys Yet Another Tool
Beware the Law of Unintended Consequences, goes the old saying. In the early days of pen-testing, we used to develop our own exploits or collect them from 'underground' sites. Then came Metasploit, and suddenly the skill level required to perform the more routine testing dropped significantly. Newer tools like Cobalt Strike and Brute Ratel made post-exploitation red team activities easier, too. But the unintended consequence is that over the last few years, threat actors have got their hands on these tools, and they are making life easier for the attackers, too.
Now, a new report from Proofpoint Threat Research points out the risk of this happening again. In late 2021, UK-based consulting firm MDSec released Nighthawk, which they bill as "the most advanced and evasive command-and-control framework available on the market". According to Proofpoint's report, based on their observation of an initial deployment of the framework in September 2022, Nighthawk uses a variety of antiforensics and evasion techniques which make it particularly stealthy - for example, its loader is encrypted but even once running, embedded strings are encoded with a simple algorithm and decrypted on the fly, so that they exist in memory for only a very short period of time, making detection more difficult.
Similarly, the main Nighthawk payload uses a simple substitution cipher on its strings, but uses a much longer list of evasion techniques, some of them disclosed by MDSec, but others not. For example, the tool unhooks the DLL load notification registration of security products and other process instrumentation callbacks, and also self-encrypts in order to evade process memory scans.
Although it is - as with many of these tools - subject to client vetting and export controls, there is no way that threat actors will not take a close interest in this and similar post-exploitation frameworks, making it likely that, sooner or later, we will see cracked versions fall into their hands. Proofpoint's analysis is a hint to detection vendors to start working on this threat now. - as we reported yesterday, Google has started doing this with Cobalt Strike.
Rausch, Alexander, et. al., Nighthawk: An Up-and-Coming Pentest Tool Likely to Gain Threat Actor Notice, blog post, 22 November 2022. Available online at https://www.proofpoint.com/us/blog/threat-insight/nighthawk-and-coming-pentest-tool-likely-gain-threat-actor-notice.
Russian Gangs Have Been Busy, Moving from Scams to Infostealing
Yesterday we reported on the evolution of the Aurora infostealer and now, a new report from Singapore-based Group-IB provides a high-level view of the groups that use this and other stealers.
Group-IB has tracked how low-level online scammers have shifted to a more dangerous - and, presumably, profitable - scheme of distributing infostealers. Their operations are coordinated via Telegram groups, where they are directed to drive traffic to sites which impersonate well-known companies and brands, and induce their victims to download malware.
The figures are impressive: 34 Russian-speaking groups are distributing a variety of stealers - primarily Racoon and Redline - under the stealer-as-a-service model, in order to obtain credentials for a range of services, mainly gaming accounts on Steam and Roblox, as well as Amazon and PayPal accounts and even crypto wallet information. In the first seven months of 2022. their roughly 200 members infected over 890,000 devices and stole over 50 million passports, mainly in the US, Brazil, India, Germany and Indonesia.
They also managed to acquire over two billion cookies, 113,204 crypto wallets and over 100,000 payment cards, representing a total value approaching $US6 million if sold on the cybercriminal underground.
Uncredited, Professional stealers: opportunistic scammers targeting users of Steam, Roblox, and Amazon in 111 countries, press release, 23 November 2022. Available online at https://www.group-ib.com/media-center/press-releases/professional-stealers/.
Pro-Kremlin Group Brings Down EU Parliament Site
The English-language web site of the European Parliament (at https://www.europarl.europa.eu/portal/en) was disrupted earlier today by a distributed denial of service attack.
"The availability of @Europarl_EN website is currently impacted from outside due to high levels of external network traffic. This traffic is related to a DDOS attack (Distributed Denial of Service) event.", tweeted Jaume Dauch, Director General for Communication and Spokesperson of the European Parliament.
According to Roberta Metsola, President of the European Parliament, a pro-Kremlin group had claimed responsibility, likely as a response to the Parliament having proclaimed Russia as a state sponsor of terrorism.
The site is now operating normally.
Duch, Jaume, "The availability of @Europarl_EN website ...", Tweet, 24 November 2022. Available online at https://twitter.com/jduch/status/1595433790809284614.
Metsola, Roberta, "The @Europarl_EN is under a sophisticated cyberattack.", Tweet, 24 November 2022. Available online at https://twitter.com/EP_President/status/1595443471518777345.
Monero Mining Apparently Still Profitable
While sales of GPU chips have apparently tanked due to Ethereum's switch to proof-of-stake and the general collapse of cryptocurrency markets, it seems that there is still money to be made in mining the Monero cryptocurrency - especially if you are mining at no cost to yourself, using lots of other people's machines.
Cyble Research and Intelligence Labs reports on an a number of phishing campaigns which are targeting gamers and others who use tools like MSI Afterburner to overclock and tweak their GPU's. The phishing emails direct the victims to approximately 50 different fake Afterburner download sites from which they obtain a malicious installer. This drops and executes a file names browser_assistant.exe which injects itself and downloads an encoded XMR Miner binary from a GitHub repository, then injects it into explorer.exe.
Finally, the malware starts mining, using all the GPU resources of the victim's machine and degrading its performance, while depositing the coins it mines into the threat actor's wallet address - a nice little earner, as they say. Cyble's report provides a full breakdown, mapping to MITRE ATT&CK Techniques and IOC's.
Uncredited, Fake MSI Afterburner Sites Delivering Coin-Miner, blog post, 23 November 2022. Available online at https://blog.cyble.com/2022/11/23/fake-msi-afterburner-sites-delivering-coin-miner/.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
![]() Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.