Les Bell and Associates Pty Ltd
Blog entries about Les Bell and Associates Pty Ltd
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
Powerful Infostealer for Rent
Since late July, a Russian-speaking malware developer has been offering an extremely sophisticated info stealer, called Erbium, on a dark web forum. The author claims that it is the best on the market, having taken several months to develop, and this is perhaps reflected in the fact that the asking price for one year of the service has gone from $150 to $1,000, including technical support and updates (considerably less than any comparable infostealer).
Erbium has a vast range of capabilities, from system info enumeration to the ability to collect user credentials from web browsers, chat and email programs. It can also capture cryptocurrency wallet information (including login credentials and stored funds) and can collect multi-factor authentication information as well as the content of password safe programs.
The malware uses extensive antiforensic techniques to evade detection, being polymorphic and also using XOR encryption to obfuscate the ErbiumStealer.dll second stage, which it downloads from a C2 server. Its control panel communicates over a Telegram channel. Erbium has now been observed and analyzed by both Cluster25 and Cyfirma.
Cluster25 Threat Intel Team, Erbium InfoStealer Enters the Scene: Characteristics and Origins, blog post, 15 September 2022. Available online at https://blog.cluster25.duskrise.com/2022/09/15/erbium-stealer-a-new-infostealer.
Uncredited, Erbium Stealer Malware Report, technical report, 25 September 2022. Available online at https://www.cyfirma.com/outofband/erbium-stealer-malware-report/.
Europol Hackathon Targets Human Trafficking Networks
A hackathon hosted by the Dutch Police Academy in Apeldoorn on behalf of Europol on 6 September brought together 85 experts from 20 countries to focus on combating criminal networks that use social media, the public web and the dark web to conduct human trafficking for sexual or labour exploitation. It is relatively easy to identify trafficking of drugs or weapons online, but the indicators of online activity in human trafficking are more subtle and challenging, so the investigators gathered criminal intelligence to determine these indicators and, in particular, to target human traffickers attempting to lure Ukrainian refugees.
The traffickers will attempt to hijack social media platforms, online dating apps, advertising and aid platforms, messaging apps, forums and private groups in order to lure their victims while evading detection by law enforcement. The hackathon was a success:
- 114 online platforms monitored in total, of which 30 were related to vulnerable Ukrainian refugees;
- 53 online platforms suspected of links to human trafficking checked, of which 10 were related to vulnerable Ukrainian refugees;
- Five online platforms linked to human trafficking checked, of which four were related to child sexual exploitation on the dark web;
- 11 suspected human traffickers identified, 5 of whom were linked to trafficking of human beings, and specifically to vulnerable Ukrainian citizens;
- 45 possible victims identified, 25 of whom were of Ukrainian nationality;
- 20 platforms with possible links to trafficking of human beings identified for further investigation and monitoring;
- 80 persons/user names checked, out of which 30 were related to possible exploitation of vulnerable Ukrainian citizens.
This is a useful reminder that our work in the online world often has deeper consequences for victims in the real world.
Belanger, Ashley, Hackathon finds dozens of Ukrainian refugees trafficked online, Ars Technical, 23 September 2022. Available online at https://arstechnica.com/tech-policy/2022/09/hackathon-finds-dozens-of-ukrainian-refugees-trafficked-online/.
Damned If You Do, Damned If You Don't
Illustrating the particularly nasty nature of ransomware extortions, the hackers who compromised systems at the Centre Hospitalier Sud Francilien hospital in Corbeil-Essonne near Paris have now responded to the authorities' refusal to pay a ransom demand by leaking patient information online.
The hospital was hit one weekend in August, with all their major systems disabled by LockBit ransomware, requiring patients to be sent elsewhere and major surgeries to be postponed. The attackers demanded payment of $US10 million to unlock the data, and threatened to release all the information they had exfiltrated - which they have now done.
The data includes the French equivalent to social security numbers as well as examination reports, test results and more, and could impact patients but also doctors, staff and employees of partners such as laboratories.
Stahie, Silviu, Hackers Release Stolen Data after French Hospital Refuses to Pay Decryption Ransom, Bitdefender HotForSecurity blog, 27 September 2022. Available online at https://www.bitdefender.com/blog/hotforsecurity/hackers-release-stolen-data-after-french-hospital-refuses-to-pay-decryption-ransom/.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]() Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License.
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
CI/CD Pipelines Exposed Via Source Code Repository Webhooks
A fascinating PoC developed by Cider Security shows how DevOps software deployment pipelines can be compromised by webhooks they expose so that cloud SaaS source code management systems can trigger internal build events.
Enterprises often establish internal built/test/deploy pipelines using automation servers like Jenkins (https://www.jenkins.io/), but make use of cloud-hosted source code repositories like GitHub and GitLab. In order to automatically push commits from the source repository to the deployment pipeline, these systems support webhooks which trigger actions on the automation server by POSTing a request to a RESTful API. But for this to work, the enterprise firewalls must accept inbound HTTP requests from a particular range of IP addresses owned by the repository.
A complicating factor is that automation servers are often seen as well-protected since they are well inside the firewall, but they also have a large number of poorly-maintained plugins and can remain unpatched for long periods. If an attacker can a) find an automation server exposed endpoint and b) get the source repository to send cunningly-crafted payloads, then they have opened a door to brute-force credentials, then execute Jenkins commands. All kinds of interesting possibilities then follow: compromising code deployed to production systems, pivoting to attack other systems or even arbitrary remote command execution.
It's not easy - but Cider have shown that - and how - it can be done. Time to take a closer look at those CI/CD pipelines.
Gil, Omer and Asi Greenholts, How we Abused Repository Webhooks to Access Internal CI Systems at Scale, blog post, 20 September 2022. Available online at https://www.cidersecurity.io/blog/research/how-we-abused-repository-webhooks-to-access-internal-ci-systems-at-scale/.
Morgan Stanley Insecure Asset Disposal Attracts $23 Million Fine
Financial services company Morgan Stanley has been fined $US35 million by the Securities and Exchange Commission for "extensive failures to protect the personal identifying information of approximately 15 million customers". The company agreed to the payment in order to escape a court process which might have had a worse outcome.
In point of fact,, Morgan Stanley didn't actually dispose of the old hard drives and network caching devices itself - it had contracted another company to take care of the tasks. But the company failed to promulgate adequate policies for equipment retirement and data destruction, did not manage the selection of a contractor to perform the task, and had inadequate procedures for assuring secure destruction by the contractor.
Full details are in the administrative proceeding file, linked below, which makes fascinating - and essential - reading.
The lessons are clear:
- You can outsource or delegate responsibility for some security-related functions, but you can't escape accountability and liability
- Device retirement policies should require secure destruction, rather than over-writing and reselling, for media that contains sensitive data, especially PII
- Full-device encryption can aid with compliance, as long as keys are correctly managed
- PII that escapes can show up years later, with expensive consequences
Uncredited, Morgan Stanley Smith Barney to Pay $35 Million for Extensive Failures to Safeguard Personal Information of Millions of Customers, press release, 20 September 2022. Available online at https://www.sec.gov/news/press-release/2022-168.
United States of America v. Morgan Stanley Smith Barney LLC (respondent), Administrative Proceeding File No. 3-21112, 20 September 2022. Available online at https://www.sec.gov/litigation/admin/2022/34-95832.pdf.
Rusian Groups Ramp Up Attacks
As the Russia/Ukraine conflict seems likely to enter a new phase, Ukrainian Defence Intelligence has warned that Russia is preparing massive cyberattacks on critical infrastructure facilities of Ukraine and its allies. Western countries are likely to be collateral damage, if not direct targets, in these campaigns.
Mandiant is tracking multiple self-proclaimed hacktivist groups working for Russia, primarily conducting DDoS attacks and leaking stolen data. Such groups, although claiming independence, seem to be working closely with, or are simply a front for, the Russian state.
The moderators of three Telegram channels - "XaKNet Team", "Infoccentr" and "CyberArmyofRussia_Reborn" - are using GRU-sponsored APT28 (Fancy Bear) tools on Ukrainian victims' networks, leaking their data within 28 hours of wiping activity by APT28.
Meanwhile, Cluster25 researchers have analyzed an infected PowerPoint file which an APT28-affialiated group is using to implant a variant of Graphite malware. The technique exploits a code execution technique which is triggered when the user enters presentation mode and then moves the mouse - this then runs a PowerShell script which downloads and executes a dropper from OneDrive, which in turn downloads and injects the Graphite variant.
Cluster25 Threat Intel Team, In the footsteps of the Fancy Bear: PowerPoint mouse-over event abused to deliver Graphite implants, blog post, 23 September 2022. Available online at https://blog.cluster25.duskrise.com/2022/09/23/in-the-footsteps-of-the-fancy-bear-powerpoint-graphite/.
Defence Intelligence of Ukraine, !! The occupiers are preparing massive cyberattacks ..., tweet 26 September 2022. Available online at https://twitter.com/DI_Ukraine/status/1574324482277363714.
Mandiant Intelligence, GRU: Rise of the (Telegram) MinIOns, blog post, 23 September 2022. Available online at https://www.mandiant.com/resources/blog/gru-rise-telegram-minions.
Russian Botmaster Requests Extradition to the US
The likely operator of the RSOCKS botnet, 36-year-old Russian national Denis Emelyantsev, a.k.a.Denis Kloster, has been arrested in Bulgaria at the request of US authorities, reports Brian Krebs. In a novel twist, he requested, and was granted, extradition to the US, apparently telling the judge, "America is looking for me because I have enormous information and they need it".
A cynical observer might observe that whether or not he has "enormous information", Russian President Vladimir Putin has instituted a massive conscription program, and this might have factored in his decision.
Krebs, Brian, Accused Russian RSOCKS Botmaster Arrested, Requests Extradition to U.S., blog post, 23 September 2022. Available online at https://krebsonsecurity.com/2022/09/accused-russian-rsocks-botmaster-arrested-requests-extradition-to-u-s/.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]() Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License.
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
Uber & Rockstar GTA Hacker Arrested
The City of London Police has revealed that it has arrest a 17-year-old teenager from Oxfordshire on suspicion of hacking. It is believed that the real-world identity hacker, who went by the handles 'teapot' and 'teapotuberhacker', was outed in an online forum, giving the police the information they needed to act.
If this is correct, the teenager also hacked Microsoft, Rockstar Games and Uber and may well be 'White' or 'Breachbase', the ringleader of the Lapsus$ extortion group. This group has mainly employed social engineering attacks on employee accounts for initial access, but then employs increasingly sophisticated technical techniques for lateral movement. They have also attempted to recruit privileged insiders at telcos, tech companies and callcenters, bribing them to provide VPN or Citrix credentials.
City of London Police, On the evening of Thursday 22 September ..., tweet, 23 September 2022. Available online at https://twitter.com/CityPolice/status/1573281533665972225.
Flashpoint Team, What We Know About the 'Grand Theft Auto VI' Data Breach, blog article, 23 September 2022. Available online at https://flashpoint.io/blog/grand-theft-auto-6-data-breach/.
Optus Data Breach Resonates
The massive data breach of Australian telco continues to resonate, with ongoing implications for the telco, its customers and regulators. The hacker behind the breach has apparenty now demanded a $US 1 million ransom - which, considering the number of records, amounts to just over 10c per record. Local journalist Jeremy Kirk has been in touch with the alleged hacker and confirmed the authenticity of a sample of the data with the affected customers.
The hacker claims that they obtained access via an API endpoint which required no authentication - a classic function-level authorization vulnerability - enumerating a field called 'contactid' to access customer records sequentially.
Because the customer data contains so much information that can be used for identity theft, the Government is considering changes to privacy laws which will speed the disclosure of such information to banks so that the financial institutions can apply additional monitoring and controls on the accounts of the affected customers. Considering that it is the existing privacy laws that prevent this type of disclosure, the government might wish to pause for reflection on the Law of Unintended Consequences before pushing through any half-baked ideas.
Belot, Henry, Australian Federal Police monitoring dark web amid allegations stolen Optus data may be sold online, ABC News, 24 September 2022. Available online at https://www.abc.net.au/news/2022-09-24/afp-monitoring-dark-web-for-stolen-optus-data-sold-online/101471256.
Kirk, Jeremy, UPDATE: I reached the person who claims to have hacked Optus, tweet, 24 September 2022. Available online at https://twitter.com/jeremy_kirk/status/1573652986437726208.
Speers, David and Andrew Greene, Federal government to unveil new security measures following massive Optus data breach, ABC News, 25 September 2022. Available online at https://www.abc.net.au/news/2022-09-25/new-security-measures-to-be-unveiled-following-optus-data-breach/101472364.
XSS, CSRF Vulns in Netlify JavaScript Library
Web sites built with the Netlify development platform are vulnerable to cross-site scripting (XSS) and cross-site request forgery (CSRF) attacks, due to a cache poisoning vulnerability (CVE-2022-39239), say researchers. The vulnerability allows attackers to use specially crafted headers which cause the cache handler to load and return arbitrary images - which could include scalable vector graphics (SVG) files carrying embedded malicious scripts.
The vulnerability is due to improper URL parsing in the unjs/ufo library which is, in turn, used by the @netlify/ipx library. This is installed by default on many Netlify installations.
Netlify versions prior to 1.2.3 are vulnerable, and customers are - obviously - urged to update and redeploy sites to clear caches.
Curry, Sam, Exploiting Web3's Hidden Attack Surface: Universal XSS on Netlify's Next.js Library, blog post, 21 September 2022. Available online at https://samcurry.net/universal-xss-on-netlifys-next-js-library/.
Course Updates
Course materials updated in the last few days:
Updated Lecture Slides
Updated CISSP CBK wiki pages:
- CBK Wiki/RESTful API
- CBK Wiki/Simple Object Access ProtocolCBK Wiki/XML-RPC
- CBK Wiki/Broken Object-Level Authorization
- CBK Wiki/JSON Web Token
- CBK Wiki/Federated Identity Management Systems
- CBK Wiki/Software Development for Mobile Devices
- CBK Wiki/Excessive Data Exposure
- CBK Wiki/Sensitive Data Exposure
- CBK Wiki/Broken Function-Level Authorization
- CBK Wiki/Injection Attacks
- CBK Wiki/Lack of Resources and Rate Limiting
- CBK Wiki/Mass Assignment
- CBK Wiki/Improper Web API Asset Management
- CBK Wiki/Insufficient Logging and Monitoring
- CBK Wiki/API Security
- CBK Wiki/API key
- CBK Wiki/Broken User Authentication
- CBK Wiki/Web Application Security
- CBK Wiki/Cross-Site Request Forgery
- CBK Wiki/Polymorphism
- CBK Wiki/Inheritance
- CBK Wiki/Encapsulation
- CBK Wiki/Object-Oriented Concepts and Security
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]() Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License.
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
Exchange Servers Compromised For Spamming
Microsoft is warning of an attack which compromises cloud-hosted Exchange servers by installing a malicious OAuth application which then enables the attacker to send spam emails which appear to be from the victim's domain.
Initial access is achieved by a credential stuffing attack, based on a dump of existing credentials, in order to gain access to an admin account which did not have multi-factor authentication enabled (which would have prevented the attack). Once this was achieved, the attacker probably ran a PowerShell script to register a new application, grant it the Exchange.ManageAsApp permission with admin consent, give it global admin and Exchange admin roles and then add some credentials which will allow them to maintain control.
This app was then used to create a new inbound connector and transport rules in Exchange. This allowed the threat actor to then conduct a high-volume spam campaign, intended to trick recipients into providing credit card details and signing up for a recurring subscription service - a fairly obvious scam, but one that still works well enough.
Microsoft 365 Defender Research Team, Malicious OAuth application used to compromise email servers and spread spam, blog article, 22 September 2022. Available online at https://www.microsoft.com/security/blog/2022/09/22/malicious-oauth-applications-used-to-compromise-email-servers-and-spread-spam/.
NSA, CISA Advise on OT & ICS Defence
The National Security Agency and Cybersecurity & Infrastructure Security Agency have issued a joint alert providing guidance on security for Operational Technology (OT) and Industrial Control Systems (ICS). These systems monitor and control industrial processes - power stations, refineries, steel mills, but also air conditioning plant for office buildings, ovens for small bakeries and water treatment plants - which collectively are essential to . . . everything. Disrupting their operation can lead to outcomes from mild annoyance through political and economic gains to physical destruction and loss of life.
The alert provides guidance on the TTP's and overall game plan of threat actors targeting OT/ICS, as well as a suggested approach to the development of mitigation strategies.
NSA/CISA, Control System Defense: Know the Opponent, Alert AA22-265A, 22 September 2022. Available online at https://www.cisa.gov/uscert/ncas/alerts/aa22-265a.
Zoho ManageEngine Exploit in the Wild
A remote command execution vulnerability (CVE-2022-35405) in Zoho ManageEngine Access Manager Plus (version 4302 and earlier), Password Manager Pro (version 12100 and earlier) and PAM360 (version 5500 and earlier) is being actively exploited in the wild and has been added to CISA's Known Exploited Vulnerabilities Catalog.
The insecure object deserialization vulnerability, in a Java XMLRPC parser, is of critical severity, and customers are advised to updated their installations as soon as possible.
Uncredited, ManageEngine PAM360, Password Manager Pro, and Access Manager Plus remote code execution vulnerability, security advisory, September 2022. Available online at https://www.manageengine.com/products/passwordmanagerpro/advisory/cve-2022-35405.html.
Metador Mystery Threat Actor
Researchers at SentinelLabs have discovered a previously-unseen threat actor which is primarily targeting telcos, ISP's and universities in the Middle East and Africa. The group, which they christened 'Metador', has deployed sophisticated malware which makes use of antiforensics techniques to evade detection and LOLbins to deploy malware directly into memory.
The origin of the malware is unclear - linguistic analysis points to multiple developers speaking both English and Spanish, with references to British pop punk lyrics and Argentinian political cartoons - but since the cyberespionage is focused on the Middle East and Africa, it is possible the development of the malware was contracted out by a state agency.
Guerrero-Saade, Juan Andrés et. al., The Mystery of Metador | An Unattributed Threat Hiding in Telcos, ISPs, and Universities, technical report, 22 September 2022. Available online at https://www.sentinelone.com/labs/the-mystery-of-metador-an-unattributed-threat-hiding-in-telcos-isps-and-universities/.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]() Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License.
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
German General Data Retention Rule Violates EU Law
Attempts by European governments to proactively collect data in case it turns out to be useful in counter-terrorism investigations have taken a serious hit, with the European Union's Court of Justice ruling that such blanket collection of data can only be done in circumstances where there is a serious threat to national security.
The ruling illustrates the tension between governments' desire to make use of massive data collection and analytics in the name of national security and public safety, and citizens increasing concerns over personal privacy, especially in light of several countries' swing towards authoritarianism.
The ruling is the result of a case brought by Deutsche Telekom and ISP SpaceNet AG, challenging the German data retention law. Of course, the tech companies are less motivated by concerns for their customers' privacy and more by the burdensome costs of collecting and storing all that data.
Chee, Foo Yun, Germany's blanket data retention law is illegal, EU top court says, Reuters, 20 September 2022. Available online at https://www.reuters.com/technology/indiscriminate-data-retention-is-illegal-eu-top-court-says-2022-09-20/.
Enhancements in Windows 11 22H2 Security Baseline
Microsoft has released their security configuration baseline settings for Windows 11 22H2, adding a number of security improvements. Top of these has to be additional hardware-based protection against stack-smashing and return-oriented/jump-oriented programming attacks for machiines that use Intel's Control-flow Enforcement Technology or similar shadow stacks. The new feature, called Kernel Mode Hardware-enforced Stack Protection, also requires Virtualization Based Protection of Code Integrity (HVCI) to be enabled.
Other enhancements include enhanced phishing protection, including detection of the reuse of enterprise passwords on other applications or web sites and credential theft protection by blocking the loading of custom security support and authentication providers into the Local Security Authority Subsystem Service (LSASS) - a technique used by some credential stealers. The update also allows Administrator accounts to be locked in the event of brute-force attacks.
The new baseline can be downloaded using the Microsoft Security Compliance Toolkit found at https://www.microsoft.com/en-us/download/details.aspx?id=55319.
Munck, Rick, Windows 11, version 22H2 Security baseline, Microsoft Security Baselines Blog, 20 September 2022. Available online at https://techcommunity.microsoft.com/t5/microsoft-security-baselines/windows-11-version-22h2-security-baseline/ba-p/3632520.
EU Proposes Stricter Regulation of Software and IoT Devices
Back to the EU, which has laid out its proposals for a new regulation, called the Cyber Resilience Act, which will regulate security of both digital hardware and software products. The legislators claim that an estimated annual cost of €5.5 trillion is down to two major problems with these products:
- A low level of cybersecurity, stemming from widespread vulnerabilities and no way to patch them, and
- Insufficient understanding and access to security information by users, leading them to choose insecure products and use them in an insecure fashion.
The Act will broaden the scope of existing legislation to cover non-embedded software and some hardware products which are not currently in scope, and aims to encourage the development of secure prodycts and a market in which purchasers are adequately informed to take cybersecurity into account when selecting and using products.
Uncredited, Cyber Resilience Act, Policy and Legislation proposal, 15 September 2022. Available online at https://digital-strategy.ec.europa.eu/en/library/cyber-resilience-act.
Australia Plans Restrictions on Online Content
Still on the subject of proposed legislation, Australian enterprises may find themselves unexpectedly affected by changes in the industry codes relating to the Online Safety Act. The changes are intended to regulate what is described - and determined - by the eSafety Commissioner as "harmful online content". This is broken up into "Class 1" material, which is essentially material that would be refused classification under the National Classification Scheme, and "Class 2", which would be X18+ or R18+ materials. Class 1 is further subdivided, according to the nature of the offensive material.
Industry groups point to several problems with this approach. First, the classification scheme is - perhaps by necessity - somewhat vague, and can encompass some materials which are legal to create, distribute and possess. Secondly, while classification is definitely done for movies released to theatres, it is not practical to do this for every piece of material floating around the Internet.
Furthermore, the use of automated approaches to the detection of harmful content could seriously impact privacy, while manual review could prove even worse.
Bogle, Ariel, Australia's changing how it regulates the internet - and no-one's paying attention, ABC News, 21 September 2022. Available online at https://www.abc.net.au/news/science/2022-09-21/internet-online-safety-act-industry-codes/101456902.
Domain Shadowing Borrows Reputation for C2 Servers
Palo Alto Networks' Unit 42 researchers have documented a new tactic employed by cybercriminals in order to maintain their C2 domains by borrowing the reputation of legitimate enterprises. The tactic works by compromising the domain name servers of a legitimate business and then creating malicious subdomains. Because the legitimate domain names have existed for some years, they have established a good reputation in threat intelligence databases, and because this tactic does not affect the enterprise's other systems, it is likely to pass completely unnoticed.
Unit 42 built an automated pipeline which uses machine learning to analyze passive DNS traffic logs, detecting over 12,000 such shadowed domains between late April and late June of this year. Of these, only 200 were marked as malicious by vendors in VirusTotal. In one example, the operators of a phishing campaign had shadowed domains in the AU and US TLD's, and their shadowed domains had IP addresses located in Russia.
Szurdi, Janos, Rebekah Houser abd Daping Liu, Domain Shadowing: A Stealthy Use of DNS Compromise for Cybercrime, technical report, 21 September 2022. Available online at https://unit42.paloaltonetworks.com/domain-shadowing/.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]() Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License.
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
GTA VI Videos Leaked, Source Code Stolen
The company behind the incredibly popular Grand Theft Auto series of video games, Rockstar Games, has announced that a threat actor was able to access and download confidential information from their systems, including early development footage of the next edition of the game. The video clips were leaked to a gamer forum by someone calling themselves "teapotuberhacker", suggesting an (unsubstantiated) link to last week's Uber breach, although the material has now been removed. The hacker is demanding a substantial ransom for return of source code and threatening to leak more if not paid.
The videos are claimed to be from a Slack channel used by Rockstar's developers, and the initial breach seems to have been achieved by yet another MFA push deluge - again, similar to the Uber breach. However, Uber is pointing the finger at a different threat actor - see the next story.
Rockstar Games, A Message from Rockstar Games, tweet, 19 September 2022. Available online at https://twitter.com/RockstarGames/status/1571849091860029455.
teapotuberhacker, Hi, Here are 90 fottage/clips from GTA 6, forum post, 18 September 2022. Available online at https://gtaforums.com/topic/985481-gta-6-americas-leak-90-mp4-footagevideos/#comments.
Uber Details Response to Breach
An update from Uber provides more detail on last week's breach, claiming that initial access was achieved when the threat actor used an external contractor's password - likely purchased on the dark web after it was exfiltrated by malware - and coupled this with a deluge of MFA approval requests, to which the contractor eventually succumbed.
Uber's investigations are still continuing, but the company claims that its production systems, which store customer information, were not accessed, and that the attacker did not make any unauthorized changes to their source code. Uber also says that no customer data stored with cloud providers had been accessed.
Uber attributes the attack to the Lapsu$ group, who have previously conducted similar attacks on Cisco, Microsoft and Okta, among others.
Uber Team, Security Update, news release, 19 September 2022. Available online at https://www.uber.com/newsroom/security-update/.
Browser Spell-Checkers Hijack Passwords
Google's Chrome and Microsoft's Edge browsers are both potentialy exposing user passwords by sending them to Google and Microsoft. The exposure occurs when "Enhanced spell check" is enabled, or when Edge's MS Editor is used, in which case any sensitive data entered into form fields will be sent to the vendors' servers, including passwords, if the user clicks on "show password".
This is an obscure, corner-case vulnerability, but users who wish to protect themselves should ensure that this feature is disabled:
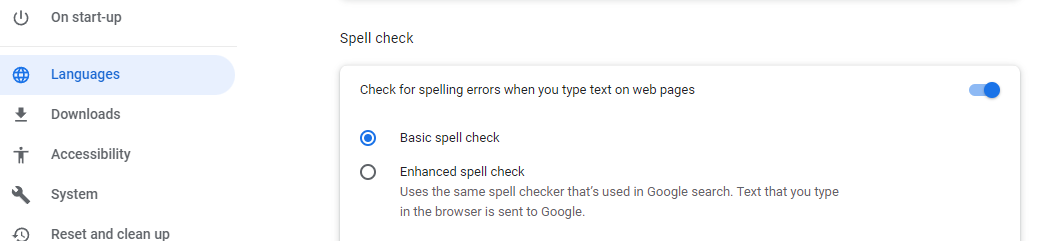
otto-js Research Team, Chrome & Edge Enhanced Spellcheck Features Expose PII, Even Your Passwords, news article, 16 September 2022. Available online at https://www.otto-js.com/news/article/chrome-and-edge-enhanced-spellcheck-features-expose-pii-even-your-passwords.
GhostSec Hacks Hotel Swimming Pool
ICS hacking group GhostSec has struck again, according to specialist security firm Otorio, who reported last week on the group's compromises of Berghof PLC devices. This time, the pro-Palestinian hacktivists breached a ProMinent AegisII controller, which continuously measures and controls conductivity abd biocide levels in water - but they did not identify the victim.
Otorio searched for Aegis II controllers on Israeli public IP addresses and successfuly identified the right one, which is managing a hotel swimming pool. Yet again, the breach was due to a password not being changed from the default.
Krivobokov, David, GhostSec Strikes Again in Israel Alleging Water Safety Breach, blog post, 14 September 2022. Available online at https://www.otorio.com/blog/ghostsec-strikes-again-in-israel-seeking-to-impact-swimming-pools/.
Massive Breach of NY Emergency Medical Service
A threat actor, believed to be the Hive ransomware group, has exfiltrated sensitive data, including patient information, from New York medical tranport provider Empress Emergency Medical Services. In a notice to customers, the EMS provider confirms that some of its systems were encrypted and that an "unauthorized party ... copied a small subset of files", revealing that those files contained patient names, dates of service, insurance information and, in some cases, social security numbers.
However, it seems that the breach was much larger than this, totaling 280 GB of contract information, internal budgets and plans, employee and customer info (the latter including email and physical addresses, passport information and more) and the contents of various databases.
Truță, Filip, Hackers Steal 280 GB of Data from NY Emergency Medical Service - Phone Numbers, Passports, SSNs, and More, Bitdefender blog, 19 September 2022. Available online at https://www.bitdefender.com/blog/hotforsecurity/hackers-steal-280gb-of-data-from-ny-emergency-medical-service-phone-numbers-passports-ssns-and-more/.
VMware Releases 2022 Global Incident Response Threat Support
Virtualization (and more) vendor VMware has released its Global Incident Response Threat Report for 2022, delivering 8 "Key Findings":
- Lateral movement is the new battleground - 1 in 10 respondents said they account for at least half of all attacks
- Deepfake attacks shot up 14 percent - 66 percent of respondents witnessed them in the past 12 months
- Cyberattacks have increased since Russia invaded Ukraine - reported 65% of respondents
- Zero-day exploits were encountered by 62% of respondents - up 11% since last year
- Nearly one quarter of attacks now compromise API security - these have emerged as a promising endpoint for exploitation
- Nearly 60% of respondents experienced a ransomware attack in the past 12 months
- 87% of respondents say they are able to disrupt a cybercriminals activities sometimes or often
- Burnout and stress remain a critical issue - although down slightly since last year
Uncredited, Global Incident Response Threat Report, 2022, VMware Inc., September 2022. Available online at https://www.vmware.com/content/dam/learn/en/amer/fy23/pdf/1553238_Global_Incident_Response_Threat_Report_Weathering_The_Storm.pdf.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]() Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License.
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
Universal LockerGoga Decryptor Now Available
The LockerGoga ransomware has long wreaked havoc around the world, most notably in a famous targeted attack on Norsk Hydro in 2019. The ransomware operator, who was detained in October 2021 and is now awaiting trial, was part of a larger cybercrime group that infected over 1,800 people and enterprises in 71 countries, causing an estimated $US 104 million of damage.
Now, a joint effort between security firm Bitdefender, Europol, the NoMoreRansom Project, the Zurich Public Prosecutor's Office and the Zurich Cantonal Police has led to the release of a universal decryptor for LockerGoga.
LockerGoga renames encrypred files by adding a '.locked' extension to the filename. Victims who see this can download the new tool for free from Bitlocker and follow the steps in a tutorial to recover their files.
Uncredited, Bitdefender Releases Universal Lockergoga Decryptor in Cooperation with Law Enforcement, blog post, 16 September 2022. Available online at https://www.bitdefender.com/blog/labs/bitdefender-releases-universal-lockergoga-decryptor-in-cooperation-with-law-enforcement.
LastPass Development Environment Compromised
Password safe service provider LastPass disclosed last month that it had suffered a security breach, and has now revealed the extent of the damage. A forensic investigation performed in conjunction with incident response firm Mandiant has revealed that the threat actor was able to obtain access to the LastPass development environment for four days during August, after which their activities were curtailed.
The attacker was not able to gain access to customer data and especially their password vaults, which in any case are encrypted under a passphrase-derived key not stored in the LastPass systems; physical separation of the development environment kept that data safe. The next question is, was the source code integrity compromised? After extensive analysis, the LastPass investigators have concluded there was no injection of malicious code. And it's doubtful that having access to the source will reveal a significant vulnerability which the attackers can exploit (Kerchoff's Second Principle, and all that).
Access to the environment was obtained via compromise of a developer account, including an MFA bypass, although the exact mechanism by which this was achieved was not determined - possibly this was another case of MFA push bombardment.
Toubba, Karim, Notice of Recent Security Incident, blog article, 15 September 2022. Available online at https://blog.lastpass.com/2022/08/notice-of-recent-security-incident/.
Growing Botnet Tries to Break Bitcoin Elliptic Curve Crypto
Specialist container security firm Aqua has discovered - using its honeypots - a new botnet which seems to be run by a threat actor called TeamTNT, which had been lying low in recent months. The attackers are scanning for misconfigured Docker daemons, and deploying a container image which then downloads a shell script to update the image and then clone a mysterious GitHub project set up by TeamTNT.
The container becomes a node in a distributed cracking project directed against the SECP256K1 Elliptic Curve encryption used to sign Bitcoin transactions. This will require an enormous amount of compute power, but since the threat actor isn't paying for it, that's not their problem. And with some quite powerful cloud containers, it will be interesting to see if they can pull it off. The odds are against it, however.
Morag, Assaf, Threat Alert: New Malware in the Cloud by TeamTNT, blog article, 15 September 2022. Available online at https://blog.aquasec.com/new-malware-in-the-cloud-by-teamtnt.
Crypto Documentary Series
File under 'light entertainment': A new documentary series looks into the history of code-breaking of all kinds - from deciphering early language text to breaking the encryption of black phones used by criminals.
The first episode focuses on Elizabeth Smith Friedman, who worked for the US War Department and the US Navy (her husband, William Friedman, was also a legendary cryptanalyst who ran the Army's Signal Intelligence Service and was late the chief cryptologist for the fledgling NSA). During the Prohibition years, Elizabeth Friedman worked for the US Coastguard, decrypting the radio messagesof bootleggers and smugglers - and being the mother of young children, was a pioneer of working from home.
Cracking the Code airs in Australia on Sunday evenings at 9:20 pm on SBS Viceland, and is also available via SBS on Demand. It is probably available via streaming services elsewhere.
Johnson, Travis, Mysteries and secret messages are unlocked in 'Cracking The Code', SBS program guide, 15 September 2022. Available online at https://www.sbs.com.au/guide/article/2022/09/15/mysteries-and-secret-messages-are-unlocked-cracking-code.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]() Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License.
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
Starbucks Singapore Breached
The personal details of 200,000 customers of Starbucks in Singapore have been offered for sale in an online forum. For $SGD3,500, the buyer will get a highly-exploitable collection of names, user ID's, birthdates, email addresses, phone numbers and more.
The company claims that credit card details have not been breached but that customers should reset their passwords, and warns them to be alert for social engineering attacks.
Cluely, Graham, Starbucks Singapore warns customers after hacker steals data, offers it for sale on underground forum, Bitdefender HotForSecurity blog, 17 September 2022. Available online at https://www.bitdefender.com/blog/hotforsecurity/starbucks-singapore-warns-customers-after-hacker-steals-data-offers-it-for-sale-on-underground-forum/.
More Info on Uber Hack
More information continues to emerge on last week's major breach of rideshare company Uber. The initial breach was apparently accomplished by spamming an Uber employee with MFA push authentication requests for over an hour, then contacting him on WhatsApp, claiming to be from Uber IT and telling him the only way to stop the requests was to accept it - which he did. This technique is referred to as 'push fatigue'.
This got the attacker VPN credentials and access to Uber's intranet, but what happened next should send shivers down the spine of any infosec pro: the attacker found a network share containing PowerShell scripts which contained the hardcoded username and password of a system administrator. Having obtained the keys to the castle, the attacker was able to get more credentials and access many of Uber's systems, including Amazon Web Services and Google Workspace environments.
Leyden, John, Uber hack linked to hardcoded secrets spotted in powershell script, The Daily Swig, 16 September 2022. Available online at https://portswigger.net/daily-swig/uber-hack-linked-to-hardcoded-secrets-spotted-in-powershell-script.
Vijayan, Jai, Attacker Apparently Didn't Have to Breach a Single System to Pwn Uber, Dark Reading, 17 September 2022. Available online at https://www.darkreading.com/attacks-breaches/attacker-apparently-didnt-breach-single-system-pwn-uber.
Multiple Vulns in Web Application Firewall
We rely on external controls such as firewalls to reduce our risk, but that doesn't happen in a straightforward fashion, as security software (and appliances) brings its own vulnerabilities. The latest example is the WAPPLES web application firewall from Korean vendor Penta Security Systems. In a blog post, security researcher Konstantin Burov lists multiple very basic errors in this product, which is sold either as a VM image for cloud deployment or as an appliance.
The vulnerabilities are absolute classics, ranging from the same keys being used across multiple machines, for both the self-signed SSL certificates in the web UI and SSH server, through a system account with a predefined password and varoius privilege escalation vulns to remote command execution via a default CouchDB configuration. Almost all of these are very basic configuration errors - in many cases, it is possible for an admin to fix these settings and reconfigure the system - although an update to the current version of the product will also provide fixes.
Burov, Konstantin, WAPPLES Web Application Firewall Multiple Vulnerabilities, blog post, 12 September 2022. Available online at https://medium.com/@_sadshade/wapples-web-application-firewall-multiple-vulnerabilities-35bdee52c8fb.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]() Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License.
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
Uber Hacked, Bug Bounty Submissions Disclosed
Rideshare company Uber seems to be in an invidious position after an unidentified hacker gained access to its internal systems, including its AWS console, VMware ESXi VM's, Google Workspace dashboard, its AD domain and - probably most damaging - the submissions to its bug bounty program, which it runs through HackerOne.
The attacker was definitely not stealthy, posting comments on bug bounty submissions and broadcasting a message announcing the hack via an employee's Slack account. It seems like the hacker gained access via a social engineering attack which obtained an employee's credentials and pivoted from there, gaining access to many of Uber's internal systems - then posting screenshots to confirm this.
Having download all the bug bounty submissions before this, it seems likely that the hacker will either makes use of them in future, or - more likely - auction them off to the highest bidder. The security team at Uber are likely to have their hands full for the foreseeable future. Meanwhile, there is no word on whether customer credentials or financial data were exposed.
Abrams, Lawrence, Uber hacked, internal systems breached and vulnerability reports stolen, Bleeping Computer, 16 September 2022. Available online at https://www.bleepingcomputer.com/news/security/uber-hacked-internal-systems-breached-and-vulnerability-reports-stolen/.
vx-underground, Update: A Threat Actor claims ..., Tweet, 16 September 2022. Available online at https://twitter.com/vxunderground/status/1570597582417821703.
Uber Comms, We are currently responding . . ., Tweet, 16 September 2022. Available online at https://twitter.com/Uber_Comms/status/1570584747071639552.
Trojaned Version of PuTTY Drops Backdoor
A novel WhatsApp spearphishing attack employed by a likely North Korean threat actor uses the possibility of a tech job with Amazon to entice possibly privileged users to run a trojaned version of the popular PuTTY SSH client. The campaign, reported by Mandiant, hides the infected utility within a .ISO image file in order to escape detection.
If the victim falls for the lure and runs the trojaned version of PuTTY - which is much larger than the genuine program - the program writes an embedded payload to disk and then lanches it. This code makes itself persistent by creating a scheduled task, then drops a copy of the AIRDRY (also known as BLINDINGCAN) backdoor. This can be configured to remain inactive for a time, but will then contact a C2 server to request commands, which will most generally be to download and execute a plugin.
Maclachlan, James, et. al., It's Time to PuTTY! DPRK Job Opportunity Phishing via WhatsApp, Mandiant blog, 14 September 2022. Available online at https://www.mandiant.com/resources/blog/dprk-whatsapp-phishing.
Akamai Blocks Record DDoS Attack
On September 12, Akamai detected and successfully mitigated the largest (so far!) attack against a European customer. A previous attack against the same customer, who is headquartered in Eastern Europe, peaked at 659.6 Mpps (million packets per second), but this one - probably initiated by the same threat actor - peaked at 704 Mpps.
This time around, the attacker targeted not just their primary data center, but six separate locations around the world, using 1,813 different IP addresses per minute. Such a widely distributed attack would make it hard for customer security staff to respond, as they were being bombarded from six different locations.
Sparling, Craig, Record-Breaking DDoS Attack in Europe, Akamai blog, 15 September 2022. Available online at https://www.akamai.com/blog/security/record-breaking-ddos-attack-in-europe.
ACSC Releases Updated Information Security Manual
The Australian Cyber Security Centre has issued a new release of the Information Security Manual, the definitive set of guidelines for Australian Government departments and other organizations which may have to comply with it.
The new edition of the ISM places increased emphasis on cyber supply chain risk management and supplier relationship management, with a lot of clarification and tightening of definitions, and a new control requiring the development and implementation of a supplier relationship management policy. A new control requires a minimum length of 30 characters for local administrator accounts and service accounts, and an existing control was clarified to require restarting workstations on a daily basis.
Email security requirements are also tightened, with clarification that subdomains are within scope (I suspect someone saw an opportunity for easy 'compliance' there) and a clarification that MTA-STS is used to prevent the unencrypted transfer of emails.
Perhaps the biggest recent innovation is the introduction of the ISM in machine-readable OSCAL (Open Security Controls Assessment Language) format for use in automated tools.
Uncredited, Information Security Manual, Australian Signals Directorate / Australian Cyber Security Centre, 15 September 2022. Available online at https://www.cyber.gov.au/acsc/view-all-content/ism.
Need for Scam Workers Drives Human Trafficking
The Australian Broadcasting Corporation has continued its investigation into the human trafficking which underlies online scamming sweatshops based in Cambodia. The scammers use the messaging capabilities of language-learning apps (among others) in order to contact and gain the trust of their potential victims through an initial phase of innocuous chat - a process referred to as "pig butchering" (a literal translation of the Chinese term for fattening an animal before slaughter). This is followed by claims of windfall returns through a cryptocurrency platform which the victim is encouraged to use.
Insiders, lured to what they initially believed would be legitimate employment, report being told to "find customers" by creating fictious accounts and adding friends on social media, then convincing their marks to deposit money into fake investments or online gambling accounts. Once the account balance reaches $10,000, the money will be transfered to the scammers. The bosses demand 14-hour days, seven days a week, with a target of $55,000 per month for each 'employee' and beatings for not achieving this.
The workers are held captive, and if they are released, may find themselves on the street with no identity documents and no way of getting back to their home country. Cambodia - which was traditionally a country from which people were trafficked in search of better employment - is only responding slowly to this new crime wave.
Handley, Erin, et. al., Inside the 'pig-butchering' scams seeing thousands trafficked into cyber slavery, ABC News, 16 September 2022. Available online at https://www.abc.net.au/news/2022-09-16/cambodia-human-trafficking-online-scam-pig-butchering/101407862.
Crypto Bros' Spat - About Who Is the Original Crypto Bro - Reaches Court
A defamation suit brought by Bitcoin personality Craig Wright (possible alter ego: Satoshi Nakamoto) against Twitter poster Hodlonaut (real identity: Magnus Granath) over Wright's claim to be the original inventor/developer of Bitcoin has finally reached court in Oslo.
Wright has several times attempted to prove that he is Satoshi, but on each occasion, the 'proof' has not stood up to scrutiny. This time, he has abandoned attempts to produce a strong, cryptographic proof, claiming that he intentionally destroyed a hard drive which contained his private keys and in any case, "identity is not related to keys". He is now relying on his relationships with many people in the cryptocurrency community, along with his patents, career history and academic achievements to confirm that he is, indeed, the owner of Satoshi's stash of 1.1 million Bitcoin.
His testimony makes entertaining reading, especially his attempts to gloss over a 2019 article in Bitcoin Magazine which debunked Wright's claims. Many readers will particularly enjoy his claim that "practically no on in information technology knows who [philosopher Jean-Paul] Sarte is".
Ligon, Cheyenne, Craig Wright Tells Court He 'Stomped on the Hard Drive' Containing Satoshi Wallet Keys, CoinDesk, 15 September 2022. Available online at https://www.coindesk.com/policy/2022/09/15/craig-wright-tells-court-he-stomped-on-the-hard-drive-containing-satoshi-wallet-keys/.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]() Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License.
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
New Linux Variant of Windows Backdoor
ESET researchers have identified a new Linux variant of the SideWalk backdoor which has been used in an attack against a Hong Kong university in February 2021. Based on code similarities and the IP address of a C2 server, they attribute the malware and the attack to Sparkling Goblin, a China-based APT which has previously taken an interest in Hong Kong academic institutions during previous student pro-democracy protests.
ESET had originally blogged about this malware in its Windows form back in August 2021, and documented the Linux malware in July of that year, but had not realised that it was just a variant of the same code - an indication of how long it can take to reverse-engineer and analyze malware. Their report makes fascinating reading.
Hrčka , Vladislav, Thibaut Passilly and Mathieu Tartare, You never walk alone: The SideWalk backdoor gets a Linux variant, ESET WeLiveSecurity blog, 14 September 2022. Available online at https://www.welivesecurity.com/2022/09/14/you-never-walk-alone-sidewalk-backdoor-linux-variant/.
Ransomware Exploits VoIP Systems
Too tight a focus on data security can seduce us into losing sight of all the other stuff that's on our networks. Voice-over-IP phone systems, in particular, are often supplied as a black box turnkey 'solution' that we don't get to see into very deeply. This is concerning particularly because they live on the network perimeter and are exposed to outside threats.
Back in June, CrowdStrike identified an exploit against Mitel VoIP appliances; the attackers were able to perform a command injection, exploiting some vulnerable PHP code and achieving unauthenticated remote command execution. This was used to establish a reverse shell and then a webshell based on a Linux pipe. This was followed by extensive antiforensic activity.
Subsequent research by Arctic Wolf suggests that the actor behind this is the Lorenz ransomware group, which they have tracked using this technique, then waiting for a month post-exploitation before using the Mitel appliance's command line interface to pivot to other systems, commencing credential dumping followed by network and domain enumeration. Having obtained credentials for two accounts - one with domain admin privileges - they then moved through the environment using EDP. This was followed by data exfiltration via FileZilla and then using BitLocker drive encryption to take data hostage.
The moral of the story: if you haven't got the ability to monitor activity on VoIP PBX's, then they may well be the weakest link in your defences.
Bennett, Patrick, The Call Is Coming from Inside the House: CrowdStrike Identifies Novel Exploit in VOIP Appliance, CrowdStrike blog, 23 June 2022. Available online at https://www.crowdstrike.com/blog/novel-exploit-detected-in-mitel-voip-appliance/.
Neis, Markus, et. al., Chiseling In: Lorenz Ransomware Group Cracks MiVoice And Calls Back for Free, Arctic Wolf blog, 12 September 2022. Available online at https://arcticwolf.com/resources/blog/lorenz-ransomware-chiseling-in/.
Teams App Stores Tokens as Plaintext
Researchers at Vectra have identified a privilege escalation vulnerability in Microsoft Teams which will allow an attacker who has obtained filesystem access on a victim machine to steal the credentials of any logged-in Teams user - worst of all, bypassing multi factor authentication.
The basic problem is that the Teams client is written as an Electron app, - in other words, a web application that runs through a customised browser, and therefore makes use of traditional browser authentication mechanisms like cookies and session strings. However, Electron does not provide encrypted storage or access to system protected directories, and because the product presents a relatively high level of abstraction to the programmer, these vulnerabilities are far from evident (and hard to fix).
Peoples, Connor, Undermining Microsoft Teams Security by Mining Tokens, Vectra blog, 13 September 2022. Available online at https://www.vectra.ai/blogpost/undermining-microsoft-teams-security-by-mining-tokens.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]() Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License.