Les Bell and Associates Pty Ltd
Site blog
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
GTA VI Videos Leaked, Source Code Stolen
The company behind the incredibly popular Grand Theft Auto series of video games, Rockstar Games, has announced that a threat actor was able to access and download confidential information from their systems, including early development footage of the next edition of the game. The video clips were leaked to a gamer forum by someone calling themselves "teapotuberhacker", suggesting an (unsubstantiated) link to last week's Uber breach, although the material has now been removed. The hacker is demanding a substantial ransom for return of source code and threatening to leak more if not paid.
The videos are claimed to be from a Slack channel used by Rockstar's developers, and the initial breach seems to have been achieved by yet another MFA push deluge - again, similar to the Uber breach. However, Uber is pointing the finger at a different threat actor - see the next story.
Rockstar Games, A Message from Rockstar Games, tweet, 19 September 2022. Available online at https://twitter.com/RockstarGames/status/1571849091860029455.
teapotuberhacker, Hi, Here are 90 fottage/clips from GTA 6, forum post, 18 September 2022. Available online at https://gtaforums.com/topic/985481-gta-6-americas-leak-90-mp4-footagevideos/#comments.
Uber Details Response to Breach
An update from Uber provides more detail on last week's breach, claiming that initial access was achieved when the threat actor used an external contractor's password - likely purchased on the dark web after it was exfiltrated by malware - and coupled this with a deluge of MFA approval requests, to which the contractor eventually succumbed.
Uber's investigations are still continuing, but the company claims that its production systems, which store customer information, were not accessed, and that the attacker did not make any unauthorized changes to their source code. Uber also says that no customer data stored with cloud providers had been accessed.
Uber attributes the attack to the Lapsu$ group, who have previously conducted similar attacks on Cisco, Microsoft and Okta, among others.
Uber Team, Security Update, news release, 19 September 2022. Available online at https://www.uber.com/newsroom/security-update/.
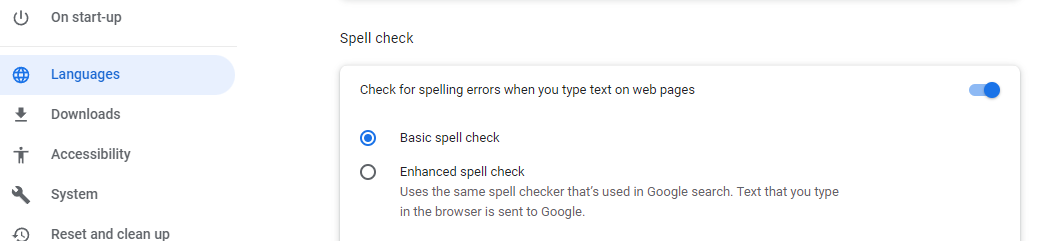
Browser Spell-Checkers Hijack Passwords
Google's Chrome and Microsoft's Edge browsers are both potentialy exposing user passwords by sending them to Google and Microsoft. The exposure occurs when "Enhanced spell check" is enabled, or when Edge's MS Editor is used, in which case any sensitive data entered into form fields will be sent to the vendors' servers, including passwords, if the user clicks on "show password".
This is an obscure, corner-case vulnerability, but users who wish to protect themselves should ensure that this feature is disabled:
otto-js Research Team, Chrome & Edge Enhanced Spellcheck Features Expose PII, Even Your Passwords, news article, 16 September 2022. Available online at https://www.otto-js.com/news/article/chrome-and-edge-enhanced-spellcheck-features-expose-pii-even-your-passwords.
GhostSec Hacks Hotel Swimming Pool
ICS hacking group GhostSec has struck again, according to specialist security firm Otorio, who reported last week on the group's compromises of Berghof PLC devices. This time, the pro-Palestinian hacktivists breached a ProMinent AegisII controller, which continuously measures and controls conductivity abd biocide levels in water - but they did not identify the victim.
Otorio searched for Aegis II controllers on Israeli public IP addresses and successfuly identified the right one, which is managing a hotel swimming pool. Yet again, the breach was due to a password not being changed from the default.
Krivobokov, David, GhostSec Strikes Again in Israel Alleging Water Safety Breach, blog post, 14 September 2022. Available online at https://www.otorio.com/blog/ghostsec-strikes-again-in-israel-seeking-to-impact-swimming-pools/.
Massive Breach of NY Emergency Medical Service
A threat actor, believed to be the Hive ransomware group, has exfiltrated sensitive data, including patient information, from New York medical tranport provider Empress Emergency Medical Services. In a notice to customers, the EMS provider confirms that some of its systems were encrypted and that an "unauthorized party ... copied a small subset of files", revealing that those files contained patient names, dates of service, insurance information and, in some cases, social security numbers.
However, it seems that the breach was much larger than this, totaling 280 GB of contract information, internal budgets and plans, employee and customer info (the latter including email and physical addresses, passport information and more) and the contents of various databases.
Truță, Filip, Hackers Steal 280 GB of Data from NY Emergency Medical Service - Phone Numbers, Passports, SSNs, and More, Bitdefender blog, 19 September 2022. Available online at https://www.bitdefender.com/blog/hotforsecurity/hackers-steal-280gb-of-data-from-ny-emergency-medical-service-phone-numbers-passports-ssns-and-more/.
VMware Releases 2022 Global Incident Response Threat Support
Virtualization (and more) vendor VMware has released its Global Incident Response Threat Report for 2022, delivering 8 "Key Findings":
- Lateral movement is the new battleground - 1 in 10 respondents said they account for at least half of all attacks
- Deepfake attacks shot up 14 percent - 66 percent of respondents witnessed them in the past 12 months
- Cyberattacks have increased since Russia invaded Ukraine - reported 65% of respondents
- Zero-day exploits were encountered by 62% of respondents - up 11% since last year
- Nearly one quarter of attacks now compromise API security - these have emerged as a promising endpoint for exploitation
- Nearly 60% of respondents experienced a ransomware attack in the past 12 months
- 87% of respondents say they are able to disrupt a cybercriminals activities sometimes or often
- Burnout and stress remain a critical issue - although down slightly since last year
Uncredited, Global Incident Response Threat Report, 2022, VMware Inc., September 2022. Available online at https://www.vmware.com/content/dam/learn/en/amer/fy23/pdf/1553238_Global_Incident_Response_Threat_Report_Weathering_The_Storm.pdf.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]() Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License.
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
Universal LockerGoga Decryptor Now Available
The LockerGoga ransomware has long wreaked havoc around the world, most notably in a famous targeted attack on Norsk Hydro in 2019. The ransomware operator, who was detained in October 2021 and is now awaiting trial, was part of a larger cybercrime group that infected over 1,800 people and enterprises in 71 countries, causing an estimated $US 104 million of damage.
Now, a joint effort between security firm Bitdefender, Europol, the NoMoreRansom Project, the Zurich Public Prosecutor's Office and the Zurich Cantonal Police has led to the release of a universal decryptor for LockerGoga.
LockerGoga renames encrypred files by adding a '.locked' extension to the filename. Victims who see this can download the new tool for free from Bitlocker and follow the steps in a tutorial to recover their files.
Uncredited, Bitdefender Releases Universal Lockergoga Decryptor in Cooperation with Law Enforcement, blog post, 16 September 2022. Available online at https://www.bitdefender.com/blog/labs/bitdefender-releases-universal-lockergoga-decryptor-in-cooperation-with-law-enforcement.
LastPass Development Environment Compromised
Password safe service provider LastPass disclosed last month that it had suffered a security breach, and has now revealed the extent of the damage. A forensic investigation performed in conjunction with incident response firm Mandiant has revealed that the threat actor was able to obtain access to the LastPass development environment for four days during August, after which their activities were curtailed.
The attacker was not able to gain access to customer data and especially their password vaults, which in any case are encrypted under a passphrase-derived key not stored in the LastPass systems; physical separation of the development environment kept that data safe. The next question is, was the source code integrity compromised? After extensive analysis, the LastPass investigators have concluded there was no injection of malicious code. And it's doubtful that having access to the source will reveal a significant vulnerability which the attackers can exploit (Kerchoff's Second Principle, and all that).
Access to the environment was obtained via compromise of a developer account, including an MFA bypass, although the exact mechanism by which this was achieved was not determined - possibly this was another case of MFA push bombardment.
Toubba, Karim, Notice of Recent Security Incident, blog article, 15 September 2022. Available online at https://blog.lastpass.com/2022/08/notice-of-recent-security-incident/.
Growing Botnet Tries to Break Bitcoin Elliptic Curve Crypto
Specialist container security firm Aqua has discovered - using its honeypots - a new botnet which seems to be run by a threat actor called TeamTNT, which had been lying low in recent months. The attackers are scanning for misconfigured Docker daemons, and deploying a container image which then downloads a shell script to update the image and then clone a mysterious GitHub project set up by TeamTNT.
The container becomes a node in a distributed cracking project directed against the SECP256K1 Elliptic Curve encryption used to sign Bitcoin transactions. This will require an enormous amount of compute power, but since the threat actor isn't paying for it, that's not their problem. And with some quite powerful cloud containers, it will be interesting to see if they can pull it off. The odds are against it, however.
Morag, Assaf, Threat Alert: New Malware in the Cloud by TeamTNT, blog article, 15 September 2022. Available online at https://blog.aquasec.com/new-malware-in-the-cloud-by-teamtnt.
Crypto Documentary Series
File under 'light entertainment': A new documentary series looks into the history of code-breaking of all kinds - from deciphering early language text to breaking the encryption of black phones used by criminals.
The first episode focuses on Elizabeth Smith Friedman, who worked for the US War Department and the US Navy (her husband, William Friedman, was also a legendary cryptanalyst who ran the Army's Signal Intelligence Service and was late the chief cryptologist for the fledgling NSA). During the Prohibition years, Elizabeth Friedman worked for the US Coastguard, decrypting the radio messagesof bootleggers and smugglers - and being the mother of young children, was a pioneer of working from home.
Cracking the Code airs in Australia on Sunday evenings at 9:20 pm on SBS Viceland, and is also available via SBS on Demand. It is probably available via streaming services elsewhere.
Johnson, Travis, Mysteries and secret messages are unlocked in 'Cracking The Code', SBS program guide, 15 September 2022. Available online at https://www.sbs.com.au/guide/article/2022/09/15/mysteries-and-secret-messages-are-unlocked-cracking-code.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]() Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License.
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
Starbucks Singapore Breached
The personal details of 200,000 customers of Starbucks in Singapore have been offered for sale in an online forum. For $SGD3,500, the buyer will get a highly-exploitable collection of names, user ID's, birthdates, email addresses, phone numbers and more.
The company claims that credit card details have not been breached but that customers should reset their passwords, and warns them to be alert for social engineering attacks.
Cluely, Graham, Starbucks Singapore warns customers after hacker steals data, offers it for sale on underground forum, Bitdefender HotForSecurity blog, 17 September 2022. Available online at https://www.bitdefender.com/blog/hotforsecurity/starbucks-singapore-warns-customers-after-hacker-steals-data-offers-it-for-sale-on-underground-forum/.
More Info on Uber Hack
More information continues to emerge on last week's major breach of rideshare company Uber. The initial breach was apparently accomplished by spamming an Uber employee with MFA push authentication requests for over an hour, then contacting him on WhatsApp, claiming to be from Uber IT and telling him the only way to stop the requests was to accept it - which he did. This technique is referred to as 'push fatigue'.
This got the attacker VPN credentials and access to Uber's intranet, but what happened next should send shivers down the spine of any infosec pro: the attacker found a network share containing PowerShell scripts which contained the hardcoded username and password of a system administrator. Having obtained the keys to the castle, the attacker was able to get more credentials and access many of Uber's systems, including Amazon Web Services and Google Workspace environments.
Leyden, John, Uber hack linked to hardcoded secrets spotted in powershell script, The Daily Swig, 16 September 2022. Available online at https://portswigger.net/daily-swig/uber-hack-linked-to-hardcoded-secrets-spotted-in-powershell-script.
Vijayan, Jai, Attacker Apparently Didn't Have to Breach a Single System to Pwn Uber, Dark Reading, 17 September 2022. Available online at https://www.darkreading.com/attacks-breaches/attacker-apparently-didnt-breach-single-system-pwn-uber.
Multiple Vulns in Web Application Firewall
We rely on external controls such as firewalls to reduce our risk, but that doesn't happen in a straightforward fashion, as security software (and appliances) brings its own vulnerabilities. The latest example is the WAPPLES web application firewall from Korean vendor Penta Security Systems. In a blog post, security researcher Konstantin Burov lists multiple very basic errors in this product, which is sold either as a VM image for cloud deployment or as an appliance.
The vulnerabilities are absolute classics, ranging from the same keys being used across multiple machines, for both the self-signed SSL certificates in the web UI and SSH server, through a system account with a predefined password and varoius privilege escalation vulns to remote command execution via a default CouchDB configuration. Almost all of these are very basic configuration errors - in many cases, it is possible for an admin to fix these settings and reconfigure the system - although an update to the current version of the product will also provide fixes.
Burov, Konstantin, WAPPLES Web Application Firewall Multiple Vulnerabilities, blog post, 12 September 2022. Available online at https://medium.com/@_sadshade/wapples-web-application-firewall-multiple-vulnerabilities-35bdee52c8fb.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]() Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License.
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
Uber Hacked, Bug Bounty Submissions Disclosed
Rideshare company Uber seems to be in an invidious position after an unidentified hacker gained access to its internal systems, including its AWS console, VMware ESXi VM's, Google Workspace dashboard, its AD domain and - probably most damaging - the submissions to its bug bounty program, which it runs through HackerOne.
The attacker was definitely not stealthy, posting comments on bug bounty submissions and broadcasting a message announcing the hack via an employee's Slack account. It seems like the hacker gained access via a social engineering attack which obtained an employee's credentials and pivoted from there, gaining access to many of Uber's internal systems - then posting screenshots to confirm this.
Having download all the bug bounty submissions before this, it seems likely that the hacker will either makes use of them in future, or - more likely - auction them off to the highest bidder. The security team at Uber are likely to have their hands full for the foreseeable future. Meanwhile, there is no word on whether customer credentials or financial data were exposed.
Abrams, Lawrence, Uber hacked, internal systems breached and vulnerability reports stolen, Bleeping Computer, 16 September 2022. Available online at https://www.bleepingcomputer.com/news/security/uber-hacked-internal-systems-breached-and-vulnerability-reports-stolen/.
vx-underground, Update: A Threat Actor claims ..., Tweet, 16 September 2022. Available online at https://twitter.com/vxunderground/status/1570597582417821703.
Uber Comms, We are currently responding . . ., Tweet, 16 September 2022. Available online at https://twitter.com/Uber_Comms/status/1570584747071639552.
Trojaned Version of PuTTY Drops Backdoor
A novel WhatsApp spearphishing attack employed by a likely North Korean threat actor uses the possibility of a tech job with Amazon to entice possibly privileged users to run a trojaned version of the popular PuTTY SSH client. The campaign, reported by Mandiant, hides the infected utility within a .ISO image file in order to escape detection.
If the victim falls for the lure and runs the trojaned version of PuTTY - which is much larger than the genuine program - the program writes an embedded payload to disk and then lanches it. This code makes itself persistent by creating a scheduled task, then drops a copy of the AIRDRY (also known as BLINDINGCAN) backdoor. This can be configured to remain inactive for a time, but will then contact a C2 server to request commands, which will most generally be to download and execute a plugin.
Maclachlan, James, et. al., It's Time to PuTTY! DPRK Job Opportunity Phishing via WhatsApp, Mandiant blog, 14 September 2022. Available online at https://www.mandiant.com/resources/blog/dprk-whatsapp-phishing.
Akamai Blocks Record DDoS Attack
On September 12, Akamai detected and successfully mitigated the largest (so far!) attack against a European customer. A previous attack against the same customer, who is headquartered in Eastern Europe, peaked at 659.6 Mpps (million packets per second), but this one - probably initiated by the same threat actor - peaked at 704 Mpps.
This time around, the attacker targeted not just their primary data center, but six separate locations around the world, using 1,813 different IP addresses per minute. Such a widely distributed attack would make it hard for customer security staff to respond, as they were being bombarded from six different locations.
Sparling, Craig, Record-Breaking DDoS Attack in Europe, Akamai blog, 15 September 2022. Available online at https://www.akamai.com/blog/security/record-breaking-ddos-attack-in-europe.
ACSC Releases Updated Information Security Manual
The Australian Cyber Security Centre has issued a new release of the Information Security Manual, the definitive set of guidelines for Australian Government departments and other organizations which may have to comply with it.
The new edition of the ISM places increased emphasis on cyber supply chain risk management and supplier relationship management, with a lot of clarification and tightening of definitions, and a new control requiring the development and implementation of a supplier relationship management policy. A new control requires a minimum length of 30 characters for local administrator accounts and service accounts, and an existing control was clarified to require restarting workstations on a daily basis.
Email security requirements are also tightened, with clarification that subdomains are within scope (I suspect someone saw an opportunity for easy 'compliance' there) and a clarification that MTA-STS is used to prevent the unencrypted transfer of emails.
Perhaps the biggest recent innovation is the introduction of the ISM in machine-readable OSCAL (Open Security Controls Assessment Language) format for use in automated tools.
Uncredited, Information Security Manual, Australian Signals Directorate / Australian Cyber Security Centre, 15 September 2022. Available online at https://www.cyber.gov.au/acsc/view-all-content/ism.
Need for Scam Workers Drives Human Trafficking
The Australian Broadcasting Corporation has continued its investigation into the human trafficking which underlies online scamming sweatshops based in Cambodia. The scammers use the messaging capabilities of language-learning apps (among others) in order to contact and gain the trust of their potential victims through an initial phase of innocuous chat - a process referred to as "pig butchering" (a literal translation of the Chinese term for fattening an animal before slaughter). This is followed by claims of windfall returns through a cryptocurrency platform which the victim is encouraged to use.
Insiders, lured to what they initially believed would be legitimate employment, report being told to "find customers" by creating fictious accounts and adding friends on social media, then convincing their marks to deposit money into fake investments or online gambling accounts. Once the account balance reaches $10,000, the money will be transfered to the scammers. The bosses demand 14-hour days, seven days a week, with a target of $55,000 per month for each 'employee' and beatings for not achieving this.
The workers are held captive, and if they are released, may find themselves on the street with no identity documents and no way of getting back to their home country. Cambodia - which was traditionally a country from which people were trafficked in search of better employment - is only responding slowly to this new crime wave.
Handley, Erin, et. al., Inside the 'pig-butchering' scams seeing thousands trafficked into cyber slavery, ABC News, 16 September 2022. Available online at https://www.abc.net.au/news/2022-09-16/cambodia-human-trafficking-online-scam-pig-butchering/101407862.
Crypto Bros' Spat - About Who Is the Original Crypto Bro - Reaches Court
A defamation suit brought by Bitcoin personality Craig Wright (possible alter ego: Satoshi Nakamoto) against Twitter poster Hodlonaut (real identity: Magnus Granath) over Wright's claim to be the original inventor/developer of Bitcoin has finally reached court in Oslo.
Wright has several times attempted to prove that he is Satoshi, but on each occasion, the 'proof' has not stood up to scrutiny. This time, he has abandoned attempts to produce a strong, cryptographic proof, claiming that he intentionally destroyed a hard drive which contained his private keys and in any case, "identity is not related to keys". He is now relying on his relationships with many people in the cryptocurrency community, along with his patents, career history and academic achievements to confirm that he is, indeed, the owner of Satoshi's stash of 1.1 million Bitcoin.
His testimony makes entertaining reading, especially his attempts to gloss over a 2019 article in Bitcoin Magazine which debunked Wright's claims. Many readers will particularly enjoy his claim that "practically no on in information technology knows who [philosopher Jean-Paul] Sarte is".
Ligon, Cheyenne, Craig Wright Tells Court He 'Stomped on the Hard Drive' Containing Satoshi Wallet Keys, CoinDesk, 15 September 2022. Available online at https://www.coindesk.com/policy/2022/09/15/craig-wright-tells-court-he-stomped-on-the-hard-drive-containing-satoshi-wallet-keys/.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]() Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License.
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
New Linux Variant of Windows Backdoor
ESET researchers have identified a new Linux variant of the SideWalk backdoor which has been used in an attack against a Hong Kong university in February 2021. Based on code similarities and the IP address of a C2 server, they attribute the malware and the attack to Sparkling Goblin, a China-based APT which has previously taken an interest in Hong Kong academic institutions during previous student pro-democracy protests.
ESET had originally blogged about this malware in its Windows form back in August 2021, and documented the Linux malware in July of that year, but had not realised that it was just a variant of the same code - an indication of how long it can take to reverse-engineer and analyze malware. Their report makes fascinating reading.
Hrčka , Vladislav, Thibaut Passilly and Mathieu Tartare, You never walk alone: The SideWalk backdoor gets a Linux variant, ESET WeLiveSecurity blog, 14 September 2022. Available online at https://www.welivesecurity.com/2022/09/14/you-never-walk-alone-sidewalk-backdoor-linux-variant/.
Ransomware Exploits VoIP Systems
Too tight a focus on data security can seduce us into losing sight of all the other stuff that's on our networks. Voice-over-IP phone systems, in particular, are often supplied as a black box turnkey 'solution' that we don't get to see into very deeply. This is concerning particularly because they live on the network perimeter and are exposed to outside threats.
Back in June, CrowdStrike identified an exploit against Mitel VoIP appliances; the attackers were able to perform a command injection, exploiting some vulnerable PHP code and achieving unauthenticated remote command execution. This was used to establish a reverse shell and then a webshell based on a Linux pipe. This was followed by extensive antiforensic activity.
Subsequent research by Arctic Wolf suggests that the actor behind this is the Lorenz ransomware group, which they have tracked using this technique, then waiting for a month post-exploitation before using the Mitel appliance's command line interface to pivot to other systems, commencing credential dumping followed by network and domain enumeration. Having obtained credentials for two accounts - one with domain admin privileges - they then moved through the environment using EDP. This was followed by data exfiltration via FileZilla and then using BitLocker drive encryption to take data hostage.
The moral of the story: if you haven't got the ability to monitor activity on VoIP PBX's, then they may well be the weakest link in your defences.
Bennett, Patrick, The Call Is Coming from Inside the House: CrowdStrike Identifies Novel Exploit in VOIP Appliance, CrowdStrike blog, 23 June 2022. Available online at https://www.crowdstrike.com/blog/novel-exploit-detected-in-mitel-voip-appliance/.
Neis, Markus, et. al., Chiseling In: Lorenz Ransomware Group Cracks MiVoice And Calls Back for Free, Arctic Wolf blog, 12 September 2022. Available online at https://arcticwolf.com/resources/blog/lorenz-ransomware-chiseling-in/.
Teams App Stores Tokens as Plaintext
Researchers at Vectra have identified a privilege escalation vulnerability in Microsoft Teams which will allow an attacker who has obtained filesystem access on a victim machine to steal the credentials of any logged-in Teams user - worst of all, bypassing multi factor authentication.
The basic problem is that the Teams client is written as an Electron app, - in other words, a web application that runs through a customised browser, and therefore makes use of traditional browser authentication mechanisms like cookies and session strings. However, Electron does not provide encrypted storage or access to system protected directories, and because the product presents a relatively high level of abstraction to the programmer, these vulnerabilities are far from evident (and hard to fix).
Peoples, Connor, Undermining Microsoft Teams Security by Mining Tokens, Vectra blog, 13 September 2022. Available online at https://www.vectra.ai/blogpost/undermining-microsoft-teams-security-by-mining-tokens.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]() Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License.
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
Mudge Spills Beans on Twitter
Former Twitter CISO Peiter "Mudge" Zatko has appeared before a Congressional committee to testify on failures of governance at the company, which he divided into two categories: the company does not know enough about its own data, and employees have too much access to data. “They don’t know what data they have, where it lives and where it came from and so, unsurprisingly, they can’t protect it,” Zatko said. “It doesn’t matter who has keys if there are no locks.”
The lack of granular access control mechanisms is particularly concerning in light of Mudge's allegations that the company is unable to identify and expel foreign agents in its employ. He claimed that the company knowingly allowed a foreign agent placed by the Indian government to influence negotiations over social media restrictions in the country. Furthermore, a week before Mudge was fired by the company, the FBI had informed Twitter's security team that at least one agent from China's Ministry of State Security was working there.
The problems, claims Mudge, stem from a corporate culture that avoids negativity and selects favourable information to present to the board. "I saw that Twitter was a company that was managed by risk and crises, instead of one that manages risk and crises", he claimed. When he told one executive that he was confident there was a foreign agent within the company, their response was, "Well, since we already have one, what does it matter if we have more?", he claims.
Mudge's testimony comes at an awkward time for Twitter, as it also supports Elon Musk's case for backing out of his planned acquisition on the grounds that the company had failed to disclose that a large proportion of user accounts were, in fact, bots. Twitter, of course, paints his account of events as "a false narrative ... riddled with inconsistencies and inaccuracies".
A related article suggests that various companies are frantically searching for dirt in order to discredit Mudge, but that they will find it difficult.
Paul, Kari, Twitter whistleblower tells Senate of 'egregious' security failings by company, The Guardian, 14 September 2022. Available online at https://www.theguardian.com/technology/2022/sep/13/twitter-whistleblower-testimony-congress-peiter-zatko.
Bond, Shannon and Raquel Maria Dillon, Twitter may have hired a Chinese spy and four other takeaways from the Senate hearing, NPR, 13 September 2022. Available online at https://www.npr.org/2022/09/13/1122671582/twitter-whistleblower-mudge-senate-hearing.
Kaplan, Fred, The People Looking for Dirt to Discredit Twitter Whistleblower "Mudge" Are Not Going to Find It, Slate, 13 September 2022. Available online at https://slate.com/news-and-politics/2022/09/twitter-whistleblower-mudge-hearing-dirt-nope.html.
New Google Tool Minimizes Use-after-free Vulnerabilities
A use-after-free bug arises when a programmer allocates memory from the heap, then frees it but accidentally continues to use it. If an attacker finds the bug and can figure out how to exploit it, it becomes a vulnerability - and these are surprisingly common, because figuring out the ideal code location for a free() function call is surprisingly tricky.
Work done at Google found that half of the known exploitable bugs in the Chrome browser are use-after-frees, and this has spurred their developers on to create a tool which can prevent their exploitation. This defines a new 'smart' pointer type, raw_ptr<T>, which uses a reference counting similar to the garbage collector found in some modern OO languages. When the application code calls free() or delete, but the reference count is not zero - indicating that a variable somewhere still points to the allocated block, the memory is quarantined, rather than being immediately released for reuse. Only after the reference count reaches zero will the memory be reused.
Taylor, Adrian, Bartek Nowlerski and Kentaro Hara, Use-after-freedom: MiraclePtr, Google Security Blog, 13 September 2022. Available online at https://security.googleblog.com/2022/09/use-after-freedom-miracleptr.html.
WordPress Plugin 0Day Actively Exploited
Wordfence - a security firm which specializes in WordPress security - has published details of a new zero-day exploit with a CVSS score of 9.8, which is being actively used in the wild for unauthenticated privilege escalation. The underlying vulnerability is in the WPGateway plugin, which is tied to the WPGateway cloud service, an administration dashboard which simplifies the setup and management of WordPress sites.
A simple IOC is the addition of an administrator account called rangex. This is also signaled by an entry in the access_log:
//wp-content/plugins/wpgateway/wpgateway-webservice-new.php?wp_new_credentials=1
Administrators who are using the WPGateway plugin should remove it immediately, until a patched version becomes available.
Gall, Ram, PSA: Zero-Day Vulnerability in WPGateway Actively Exploited in the Wild, Wordfence blog, 13 September 2022. Available online at https://www.wordfence.com/blog/2022/09/psa-zero-day-vulnerability-in-wpgateway-actively-exploited-in-the-wild/.
You Knew This Would Happen, Right?
After every major news event, there's inevitably a round of attacks seeking to exploit it in some way. For example, within hours of the 2004 Indian Ocean tsunami, hackers had set up fake Red Cross donation sites and were phishing like crazy.
Inevitably, the death of Queen Elizabeth II has triggered similar activity, and Proofpoint's Threat Insights team have found one such campaign. The victims are lured by emails purporting to be from Microsoft, inviting them to an "artificial technology hub" in her honour. The emails contain links to a credential-harvesting page which uses the EvilProxy phishing kit to run a MitM attack which can bypass multi factor authentication.
I dare say this won't be the last such campaign.
Threat Insight, Proofpoint identified a credential #phish campaign using lures related to Her Majesty Queen Elizabeth II. Messages purported to be from Microsoft and invited recipients to an “artificial technology hub” in her honor, Twitter thread, 15 September 2022. Available online at https://twitter.com/threatinsight/status/1570092339984584705.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]() Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License.
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
Cisco Attributes Breach to Lapsus$, Yanluowang Ransomware Groups
Back in May, Cisco's systems were breached by a highly sophisticated phishing attack. Cisco Talos and Cisco's internal response team have now concluded an investigation, and their report is highly instructive.
The initial access to a Cisco VPN was achieved by compromising an employee's personal Google account - the employee had enabled password sync in their Chrome browser and stored their Cisco credentials there. From there, the next step was to get past the Multi Factor Authentication for the Cisco VPN, and this was achieved with a variety of techniques, including voice phishing ("vishing") as well as pushing a high volume of push requests to the user's device until they either slip up or or give in, in frustration, to make it stop. The employee concerned reported receiving multiple calls, in variously-accented English, purporting to come from tech support.
After gaining access, the attackers enrolled a number of new devices for MFA and successfully authenticated to the Cisco VPN. From there a privilege escalation let them log in to multiple systems, rapidly deploying tools such as Cobalt Strike, PowerSploit, Mimikatz and impact, and creating backdoor accounts. This was followed by enumeration, mostly performed manually at the command line (indicated by numerous typing errors), and then pivoting to other systems, including Citrix servers and domain controllers, from which they extracted credentials.
The Cisco Talus report contains a lot of detail on TTP's, as well as useful recommendations; key among these is the need to educate users on what to do in response to multiple MFA push requests and who to contact. It's not as simple as setting up an authenticator app on their phones and telling them to get on with it.
Uncredited, Cisco Talos shares insights related to recent cyber attack on Cisco, blog post, 11 September 2022. Available online at https://blog.talosintelligence.com/2022/08/recent-cyber-attack.html.
Skills Gap Contributing to Breaches
A new report from Fortinet turns up a slightly scary finding - 80% of respondents to a global survey suffered at least one breach that they could attribute to a lack of cybersecurity skills and/or awareness. 64% of organizations lost revenue or paid fines due to breaches in the past year, and 38% reported breaches that cost them more than $US1 million.
The key problem is the struggle to find and retain certified cybersecurity talent (reported by 60% of respondents), then retain them (52%). At least the message is reaching boards, with 76% of organizations reporting that their board of directors recommends increases in IT and cybersecurity headcounts.
Uncredited, 2022 Cybersecurity Skills Gap, Global Research Report, September 2022. Available online at https://www.fortinet.com/content/dam/fortinet/assets/reports/report-2022-skills-gap-survey.pdf.
Programmable Logic Controllers on Public IP Addresses? Pwned!
An interesting example of an easy attack on industrial control systems has been analyzed by ICS security specialist firm Otorio. The attack, conducted and proclaimed by hacktivist group GhostSec, successfully breached 55 Berghof PLC's (Programmable Logic Controllers) being used by companies in Israel. The group was able to log in to the PLC's, which were on public IP addresses and secured with default or trivial passwords, then stop the PLC process and dump data from it.
Fortunately, the group stopped at this point, choosing to embarrass their victims rather than interfere with industrial processes - gaining access to a single PLC gives no insight into the entire process or the other devices being used.
Lakshamanan, Ravie, Hacktivist Group GhostSec Compromises 55 Berghof PLCs Across Israel, The Hacker News, 12 September 2022. Available online at https://thehackernews.com/2022/09/palestinian-hacktivist-group-ghostsec.html.
Let's Encrypt Reintroduces CRL's
Free certificate authority Let's Encrypt has announced plans to build infrastructure to distribute certificate revocation lists (CRL's). CRL's were never widely deployed, except for the most expensive types of certificates and private PKI's in high-risk environments, and most commercial CA's purveying web site SSL (really TLS) certificates have preferred to use the Online Certificate Status Protocol (OCSP) for their more expensive certificates. Those paying for the cheaper certificates would simply have to wait out the remaining lifetime of a compromised website private key.
However, the browser vendors - primarily Mozilla Firefox and Google Chrome - are now implementing proprietary, browser-specific CRL's which are highly compressed and much more efficient, and then distributed using the update mechanisms already built into their browsers - Firefox, for example, can push updates every six hours.
Let's Encrypt has now joined this effort, developing new specialized infrastructure, splitting what would be a single 8-GB CRL (for their 200 million active certificates) into 128 shards which will download separately, with the content of each shard being carefully tuned so as to minimize the need for frequent updates.
Gable, Aaron, A New Life for Certificate Revocation Lists, blog article, 7 September 2022. Available online at https://letsencrypt.org/2022/09/07/new-life-for-crls.html.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]() Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License.
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
Does Cybersecurity Awareness Change Behaviour?
Badly-designed awareness campaigns are of dubious value in changing security culture, with a majority of US Government employees surveyed by NIST reporting 'security fatigue' (Stanton et. al., 2016). Now the EU's cybersecurity agency, ENISA, is partnering with Anima People, UCL and Gothenburg University to run a research study about the effectiveness of their European Cybersecurity Month, which takes place each October to promote cybersecurity among EU citizens and organizations. If you are interested in participating, see https://ec.europa.eu/eusurvey/runner/Cybersecurity_Awareness_ECSM-PreC.
Stanton, B., M. F. Theofanos, S. S. Prettyman, and S. Furman, Security Fatigue, IT Professional 18, no. 5 (September 2016): 26–32. doi:10.1109/MITP.2016.84.
China Gets Some of What It Gives
China is accusing the NSA's Office of Tailored Access Operations of running a major campaign of attacks against its Northwestern Polytechnical University in Xi'an during June of this year. The National Computer Virus Emergency Response Centre (NCVERC) released its findings last week, accusing the NSA of delivering thousands of attacks, using at least 40 different cyber weapons, against the university, which conducts military and aeronautical engineering research.
"The U.S. NSA's TAO has carried out tens of thousands of malicious cyber attacks on China's domestic network targets, controlled tens of thousands of network devices (network servers, Internet terminals, network switches, telephone exchanges, routers, firewalls, etc.), and stole more than 140GB of high-value data," the NCVERC said.
Lakshamanan, Ravie, China Accuses NSA's TAO Unit of Hacking its Military Research University, The Hacker News, 12 September 2022. Available online at https://thehackernews.com/2022/09/china-accuses-nsas-tao-unit-of-hacking.html.
Apple Fixes Eighth 0Day for 2022
A serious vulnerability, CVE-2022-32917, which could allow malicious applications to execute code with root privileges, is reported as being actively exploited in the wild. Apple has released patches for iPhones, iPads and Macintoshes for what is the eighth zero-day vulnerability in their devices this year. Users are urged to update their devices promptly.
Gatlan, Sergiu, Apple fixes eighth zero-day used to hack iPhones and Macs this year, Bleeping Computer, 12 September 2022. Available online at https://www.bleepingcomputer.com/news/security/apple-fixes-eighth-zero-day-used-to-hack-iphones-and-macs-this-year/.
More Info on Iranian Group APT42
Last week we posted about a Microsoft report on an Iranian group called DEV-0270 or Nemesis Kitten. Mandiant has now joined the chorus of firms reporting on this group, which is associated with the Islamic Revolutionary Guard Corps (IRGC) and has been running highly-targeted spear-phishing and social engineering campaigns against a wide range of sectors - education, government, healthcare, legal, media and pharmaceuticals - in at least 14 countries, including Australia, Europe and the US.
The group's operations encompass three major areas: credential harvesting to gather multi-factor authentication credentials and compromise networks and devices; surveillance operations using Android mobile malware to track locations and monitor the communications of individuals of interest to the Iranian government; and deployment of custom malware, including backdoors, for their more advanced campaigns. By correlating Telegram traffic, open-source intelligence and OPSEC lapses by the group, Mandiant assesses that they are also associated with two front companies, Najee Technology and Afkar Systems.
Mandiant Intelligence, APT42: Crooked Charms, Cons and Compromises, blog article and report, 7 September 2022. Available online at https://www.mandiant.com/resources/blog/apt42-charms-cons-compromises.
Developers Speed Up Their Ransomware
Ransomware developers have realized that encrypting all the data in every file is a slow process, and the longer it takes, the greater the chances of detection and the more data a victim may be able to save. Intensive file I/O operations may also be detected and flagged by anti-malware which is monitoring the system.
In response, a number of ransomware families have adopted a techniques such as intermittent or partial encryption of files, according to a report from Sentinel Labs. In many cases, simply encrypting the first 64 or 128 bytes of a file - often, the header - is enough to render a file un-openable by applications. However, some ransomware samples will encrypt every third or fourth block or 10% of the complete file, or various combinations.
As a result, these ransomware encryptors are significantly faster than earlier examples, and better able to evade detection. In many cases, they still manage to exfiltrate data for use in subsequent extortion.
Milenkoski, Aleksandar, Crimeware Trends | Ransomware Developers Turn to Intermittent Encryption to Evade Detection, Sentinel Labs, 8 September 2022. Available online at https://www.sentinelone.com/labs/crimeware-trends-ransomware-developers-turn-to-intermittent-encryption-to-evade-detection/.
US Claws Back Cryptocurrency Stolen by North Korea
People often assume that cryptocurrency transactions are untraceable, making them a favourite payment method of ransomware and extortion operators, as well as a favourite target of hackers such as North Korea's Lazarus Group. However, that turns out not to be the case, even when the cryptocurrency is passed through exchanges and tumblers, as Erin Plante, senior director of investigations at specialist blockchain analysis firm Chainalysis has related in a report.
Five months ago, Lazarus Group struck at Ronin Network, a decentralized finance (DeFi) side channel for the play-to-earn game Axie Infinity, scoring $US600 million, the bulk of which they laundered through Ethereum-Bitcoin swaps and mixing in batches through the Tornado Cash tumbler. However, using their specialized tools, Chainalysis was able to track some of the funds right through this process and, in cooperation with law enforcement and cryptocurrency industry organizations, $US30 million worth of cryptocurrency has been seized.
This is the first time that cryptocurrency stolen by a North Korean hacking group has been retrieved, and it is unlikely to be the last.
Plante, Erin, $30 Million Seized: How the Cryptocurrency Community Is Making It Difficult for North Korean Hackers to Profit, Chainalysis report, 8 September 2022. Available online at https://blog.chainalysis.com/reports/axie-infinity-ronin-bridge-dprk-hack-seizure/.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]() Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License.
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
US Sanctions Iran Over Albanian Attack
The US Treasury Department has announced sanctions against the Iranian Ministry of Intelligence and Security (MOIS) and its Minister for engaging in cyber-enabled activities against Albania and other US allies. The sanctions mean that US citizens, as well as visitors to the US, are prohibited from conducting business or carrying out any transactions involving funds, goods or services with the sanctioned entitities.
“Iran’s cyber attack against Albania disregards norms of responsible peacetime State behavior in cyberspace, which includes a norm on refraining from damaging critical infrastructure that provides services to the public,” said Under Secretary of the Treasury for Terrorism and Financial Intelligence Brian E. Nelson. “We will not tolerate Iran’s increasingly aggressive cyber activities targeting the United States or our allies and partners.”
In the most recent campaigns, the threat groups MuddyWater and APT39, both controlled by MOIS, have attacked several NATO members, as well as Iranian dissidents and journalists.
US Department of the Treasury, Treasury Sanctions Iranian Ministry of Intelligence and Minister for Malign Cyber Activities, press release, 9 September 2022. Available online at https://home.treasury.gov/news/press-releases/jy0941.
Monti Steals from Conti
A new threat group called 'Monti' is running a ransomware campaign relying almost entirely on reusing the software tools and TTP's of the now-dispersed Conti gang. The only difference is that Monti makes use of the Acrion 1 Remote Monitoring and Maintenance (RMM) Agent.
As more of Conti's ransomware-as-a-service toolkits and source code leak, it seems likely that more similar ransomware groups will proliferate, says Blackberry Research and Intelligence, which has analysed the latest campaign.
Staff, Monti, the New Conti: Ransomware Gang Uses Recycled Code, Dark Reading, 10 September 2022. Available online at https://www.darkreading.com/vulnerabilities-threats/monti-conti-ransomware-recycled-code.
Fuzzing: More Than Tripping Over Buffer Overflows
A blog article from Google points out the success of their OSS-Fuzz project in discovering a wide range of vulnerabilities. Although fuzzing was first invented as a technique for bombarding application inputs as a way of discovering buffer overflow vulnerabilities, modern fuzzers have much broader capabilities, using instrumentation and machine learning to guide their actions.
In their latest success, OSS-Fuzz, which monitors 700 different critical open source projects, found a RCE vulnerability in the TinyGLTF project.
Metzman, Jonathan, Dongge Liu and Oliver Chang, Fuzzing beyong memory corruption: Finding broader classes of vulnerabilities automatically, Google Security Blog, 8 September 2022. Available online at https://security.googleblog.com/2022/09/fuzzing-beyond-memory-corruption.html.
WordPress SSRF Vulnerability Survives Five Years
A dispute has arisen between security researchers at Sonar and the WordPress development team over a server-side request forgery vulnerability that was first discovered back in 2017 yet remains unpatched. The vulnerability is in the WordPress pingback functionality, which allows authors to be notified when another web site links to their blog. This functionality is exposed via an XMLRPC (XML remote procedure call) API.
The Sonar researchers claim that this could be used in a DDoS attack, and have demonstrated a proof-of-concept, which they disclosed to WordPress on 21 January. However, the WordPress development team consider it a low-impact issue and therefore a low priority. After all, the pingback functionality can always be disabled.
Scannell, Simon and Thomas Cauchefon, WordPress Core - Unauthenticated Blind SSRF, blog article, 6 September 2022. Available online at https://blog.sonarsource.com/wordpress-core-unauthenticated-blind-ssrf/.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]() Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License.
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
MS Teams Vulnerable to . . . GIF's?
Security researcher Bobby Rauch has discovered a number of vulnerabilities in Microsoft Teams, particularly the way it handles base64-encoded GIF files - not scanning these allows malicious commands to be delivered within otherwise normal-looking graphics files. By using this along with several other vulnerabilities, an attacker can bypass security controls to perform remote command execution, data exfiltration and phishing attacks.
The main component of this attack, called GIFShell, allows a threat actor to create a reverse shell which delivers malicious commands and then exfiltrates the resultant data in GIF's returned via Microsoft's own infrastructure. The result is a unique C2 infrastructure which will avoid detection by EDR and other network monitoring tools.
Recommended mitigations including turning off the default external access settings in the Teams Admin Center, and monitoring access to Microsoft Teams' log files.
Rauch, Bobby, "GIFShell" - Covert Attack Chain and C2 Utilizing Microsoft Teams GIFs, Medium, 24 August 2022. Available online at https://medium.com/@bobbyrsec/gifshell-covert-attack-chain-and-c2-utilizing-microsoft-teams-gifs-1618c4e64ed7.
Bumblebee Malware Loader Uses Virtual Hard Disk, PowerShell Script
A new variant of the Bumblee malware loader is continuing the trend of obscuring malware payloads by wrapping them in contain files such as .ISO CD/DVD images. The new version has switched from using ISO's to a VHD (virtual hard disk) file which contains a .LNK shortcut. This in turn runs an obfuscated Windows PowerShell script which, after hiding its window from the user, loads a second stage.
The second stage makes use of the open source PowerSploit post-exploitation framework to perform DLL injection, loading the Bumblebee malware into the memory of the PowerShell process. This technique works entirely in the memory of the target PC and does not touch the disk, reducing the chance of detection by anti-malware software.
Toulas, Bill, Bumblebee malware adds post-exploitation tool for stealthy infections, Bleeping Computer, 8 September 2022. Available online at https://www.bleepingcomputer.com/news/security/bumblebee-malware-adds-post-exploitation-tool-for-stealthy-infections/.
Lazarus Group Targets Energy Sector
North Korean threat actor Lazarus Group has been running a campaign against energy providers around the world, including the US, Canada and Japan, according to Cisco Talos. The campaign is intended to turn an initial foothold gained via vulnerabilities in VMWare Horizon into long-term access with the likely goal of cybersepionage.
Once the attack compromises VMWare, this is followed by deployment of Lazarus Group's previously identified custom malware implants, an RCE bot called VSingle which fetches commands over HTTP and a backdoor called YamaBot which is written in Go. However, the campaign is also using a new remote access trojan Talos calls MagicRAT.
Malhotra, Asheer, Lazarus and the tale of three RATs, Talos Intelligence, 8 September 2022. Available online at https://blog.talosintelligence.com/2022/09/lazarus-three-rats.html.
pfSense Firewall RCE Vulnerability
pfSense is a popular firewall distribution popular with consultants and resellers support SME's. A recent remote command execution vulnerability (CVE-2022-31814) could spell disaster for some of their customers if left unpatched.
Fortunately the vulnerability is in a plug-in component which is not enabled by default. pfBlockerNG is used to allow or deny entire IP address ranges, such as blocking access from entire countries, but the vulnerability will allow an unauthenticated user to execute commands on the firewall with root privilege.
pfBlockerNG 2.1.4_26 and earlier are affected and admins should upgrade to a later version or use pfBlockerNG-devel, which is unaffected. The vulnerability is due to inadequate sanitization of the PHP $_SERVER['HTTP_HOST'] variable, which passes tainted data into the PHP exec() function.
Leyden, John, Vendor disputes seriousness of firewall plugin RCE flaw, The Daily Swig, 8 September 2022. Available online at https://portswigger.net/daily-swig/vendor-disputes-seriousness-of-firewall-plugin-rce-flaw.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]() Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License.