Les Bell and Associates Pty Ltd
Site blog
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
Signal Users' Number Compromised By Twilio Breach
The Twilio breach a couple of weeks ago revealed the phone numbers of 1,900 Signal users, according to an advisory published by Signal. The Signal encrypted messaging app uses Twilio for phone number verification, and this is how the numbers were leaked. However, message history, contact lists, profile information and other data were not compromised.
Signal is contacting the affected users and prompting them to re-register the Signal app - this is necessary because it was possible for the attackers to register these phone numbers to another device using an SMS verification code revealed by the breach.
Uncredited, Twilio Incident: What Signal Users Need to Know, Signal Support, August 2022. Available online at https://support.signal.org/hc/en-us/articles/4850133017242.
Zoom Update Vulnerability Exposes Mac Users
A nasty vulnerability in the automatic update feature of the Zoom videoconferencing app for Mac OS could grant attackers root access, security researcher Patrick Wardle revealed at DefCon on Saturday. Although initial installation of Zoom prompts for the user password, subsequent updates do not, because the updater runs as root. By feeding it a package with the right name, an attacker could either downgrade the zoom version or even install a trojan, earning the vuln a CVSS score of 8.8.
This is the most recent of a long series of vulnerabilities in Zoom; the company has released a patch which fixes this vulnerability but users really should not rely on the auto-update process to install it.
Purdy, Kevin, Update Zoom for Mac now to avoid root-access vulnerability, Ars Technica, 16 August 2022. Available online at https://arstechnica.com/information-technology/2022/08/zoom-patches-mac-auto-updater-vulnerability-that-granted-root-access/.
Zoom Security Bulletin ZSB-22018, Local Privilege Escalation in Zoom Client for Meetings for macOS, Zoom Inc., 13 August 2022. Available online at https://explore.zoom.us/en/trust/security/security-bulletin/.
Credential Theft Still Popular - Especially Callback Phishing
A new report from Ponemon Institute says that 54% of security incidents were caused by credential theft, followed by ransomware and DDoS attacks, backing similar results in the Verizon Data Breach Investigations Report. One leading cause: almost 60% of organizations do not revoke credentials once they are no longer needed, and these unused and unmonitored accounts are easy prey for attackers.
But as user awareness is improving resistance to simple phishing attacks, spear-phishers are increasing their use of hybrid techniques such as barrel-phishing and callback phishing. A report from Agari claims that while phishing attacks have increased by only 6% since Q1 2021, callback phishing has increased by 625%.
Toulas, Bill, Callback phishing attacks see massive 625% growth since Q1 2021, Bleeping Computer, 15 August 2022. Available online at https://www.bleepingcomputer.com/news/security/callback-phishing-attacks-see-massive-625-percent-growth-since-q1-2021/.
Uncredited, Credential Theft Is (Still) A Top Attack Method, The Hacker News, 15 August 2022. Available online at https://thehackernews.com/2022/08/credential-theft-is-still-top-attack.html.
Uncredited, The State of Cybersecurity and Third-Party Remote Access Risk, SecureLink (sponsor), August 2022. Available online at https://www.securelink.com/research-reports/the-state-of-cybersecurity-and-third-party-remote-access-risk/ (registration required).
Android Banking Trojan Expands Capabilities and Reach
The SOVA (Russian for owl) banking trojan, which first appeared in September 2021, has continued to develop. The trojan uses the Accessibility Services feature of Android to overlay its own form fields over banking and shopping apps, and in its latest incarnation, SOVA v4, is able to intercept two-factor authentication codes and steal cookies. The operators have also expanded its targets from Spain and the US, where it was first seen, to Australia, Brazil, China, India, the Philippines and the UK.
Lakshamanan, Ravie, SOVA Android Banking Trojan Returns With New Capabilities and Targets, The Hacker News, 15 August 2022. Available online at https://thehackernews.com/2022/08/sova-android-banking-trojan-returns-new.html.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]() Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License.
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
Microsoft Finally Reverses Advice on DogWalk
This story has been emerging for some time. Despite first claiming that the DogWalk vulnerability was not a security issue, Microsoft has now issued a patch for CVE-2022-34713 and is advising customers to install it as soon as possible. The patch was part of last week's Patch Tuesday (Wednesday in the Antipodes) update, so many users on an auto-update policy will already have installed it, but enterprise users may not yet have patched Windows Server systems.
The RCE vulnerability allows attackers to exploit the Microsoft Support Diagnostic Tool via either social engineering or phishing and has been known since January 2020, so this has been quite a long delay on Microsoft's part.
Trueman, Charlotte, Microsoft urges Windows users to run patch for DogWalk zero-day exploit, ComputerWorld, 11 August 2022. Available at https://www.computerworld.com/article/3669434/microsoft-urges-windows-users-to-run-patch-for-dogwalk-zero-day-exploit.html.
Massive Ransomware Outage Hit UK NHS
A service provider to the UK's National Health Service has been hit by a targeted ransomware attack, shutting down or slowing access to patient records, the 111 telephone advice service and the out-of-hours appointment booking system for general practices. Some urgent treatment centres and mental health providers have also been affected.
At the time of writing, the National Cyber Security Centre and the Information Commissioner's Office are both working to investigate the attack on service provider Advanced, but have not identified who is behind the attack. Idle speculation suggests that it could be any of several groups who have spun off from the Conti gang, but there are many others who have specialised in healthcare attacks, including BlackCat, Quantum, Hive and AvosLocker.
Full restoration of services could take some weeks, as data must be restored, systems reconfigured and updated, additional controls possibly installed, and the remediation plans approved by NHS Digital. The repercussions are likely to continue for even longer, as patient data may well have been exfiltrated.
36 different healthcare trusts use Advanced's services; while the NHS is able to achieve economies of scale through this kind of arrangement, this breach illustrates the danger of putting so many eggs in one basket.
Milmo, Dan and Denis Campbell, Fears for patient data after ransomware attack on NHS software supplier, The Guardian, 11 August 2022. Available online at https://www.theguardian.com/society/2022/aug/11/fears-patient-data-ransomware-attack-nhs-software-supplier.
9,000 Machines Online With No Passwords
VNC (virtual network computing) is a popular cross-platform software tool for providing graphical remote access for system installation, configuration and management - it is used to install SuSE Linux Enterprise Server on IBM zSeries mainframes, for example and is a popular alternative to SSH'ing to the command line for novice Linux system administrators.
Now security researchers at Cyble have discovered over 9,000 VNC endpoints which are not secured with a password, including SCADA and ICS systems such as water treatment plants, which could allow an attacker to remotely control pumps, causing all kinds of problems. While the systems are found all over the world, the majority are found in Sweden (perhaps unsurprising considering its size) with Sweden not far behind (surprising considering its size).
Toulas, Bill, Over 9,000 VNC servers exposed online without a password, Bleeping Computer, 14 August 2022. Available online at https://www.bleepingcomputer.com/news/security/over-9-000-vnc-servers-exposed-online-without-a-password/.
Want to Program? Go Python
The August edition of the TIOBE Index, which charts the popularity of different programming languages, shows that Python has now definitively passed long-time leaders C and Java. Although C and C++ did gain popularity, primarily for systems programming where performance is the key criterion in language selection, the all-round capability of Python will probably see it retain the top spot for some time to come.
Because Python features a REPL (Read, Evaluate, Print, Loop) interface which allows interactive execution, it is quite easy to learn its basic features. However, it can also compile its code for efficiency, and so the language is used in everything from small Raspberry Pi-based embedded systems through scripting applications for systems administration and reporting to scientific computing, data analysis and machine learning.
If asked to recommend which language security professionals should pick up for occasional use, the answer would have to be Python.
Other security-related language movements include the continued growth of safe systems-programming language Rust and the first appearance of Google's new C-derived language, Carbon.
Uncredited, TIOBE Index for August 2022: Python going through the roof, TIOBE (The Importance of Being Earnest), August 2022. Available online at https://www.tiobe.com/tiobe-index/.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]() Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License.
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
Companies Profit from Stolen Code
Macintosh malware researcher Patrick Wardle has found his code, released as open source, in a number of commercial products. As exhibit one, he cites a software tool he created back in 2016, called Oversight. The program monitors a Mac's microphone and webcam, to see whether any applications are accessing them without the knowledge of the owner (no surprise: a number were).
Several years later, Wardle was surprised to discover a number of commercial applications that were not only doing the same thing as Oversight, and in a similar way - they also contained the same bugs. When he approached the three companies involved, they all acknowledge that his code had been used without his consent, and they all eventually paid for rights.
Although it is likely that employees used the code without their employers' knowledge, it does bring to light a risk we sometimes overlook, and emphasizes the need to educate developers on free and open source software licensing.
Faife, Corin, This Mac hacker's code is so good, corporations keep stealing it, The Verge, 11 August 2022. Available online at https://www.theverge.com/2022/8/11/23301130/patrick-wardle-mac-code-corporations-stealing-black-hat.
Meta's In-App Browsers Inject Code to Track You Outside Facebook
Security researcher Felix Krause has investigated the behaviour of the Facebook and Instagram app browser component, and discovered that the app could track every interaction with external websites view from within it. The app injects JavaScript code into every website it renders - the code doesn't currently track everything, but it could monitor every button clicked, every link, all text selections and even form inputs, including passwords.
Now, I was pretty sure that I'd set an option in the Facebook app for Android to turn off the in-app browser, and use the Chrome browser instead - but looking for it now, any such setting seems to be quite deeply buried. So I, for one, welcome our new surveillance capitalism overlords.
Krause, Felix, iOS Privacy: Instagram and Facebook can track anything you do on any website in their in-app browser, Felix Krause blog, 10 August 2022. Available online at https://krausefx.com/blog/ios-privacy-instagram-and-facebook-can-track-anything-you-do-on-any-website-in-their-in-app-browser.
Signed Secure UEFI Boot Loaders Not Trustworthy
The whole point of the Secure Boot process is to preserve a chain of trust that starts with the system's TPM chip and ends with a guaranteed-unmodified operating system. However, it turns out that three hardware vendors were somehow shipping UEFI boot loaders, signed by Microsoft, which were willing to bypass the process and execute arbitrary, unsigned, code. This would be the perfect way to install a rootkit, for example.
Fortunately, Microsoft's Patchday, earlier this week, saw updates shipped which fix the problem.
Lakshamanan, Ravie, Researchers Uncover UEFI Secure Boot Bypass in 3 Microsoft Signed Boot Loaders, The Hacker News, 12 March 2022. Available online at https://thehackernews.com/2022/08/researchers-uncover-uefi-secure-boot.html.
GitHub Proposes Adoption of SigStore for NPM
As more and more software distributors adopted cryptographic signing of the packages they distribute, GitHub has asked developers to comment on a proposal to adopt Sigstore for the Node Package Manager (npm) which distributes pJavaScript packages for node.js and related systems. SigStore is an open-souce project which operates public-key infrastructure to both sign packages and to verify signatures, something that is seen as essential to the integrity of the software supply chain.
Lemos, Robert, Software Supply Chain Chalks Up a Security Win With New Crypto Effort, Dark Reading, 13 August 2022. Available online at https://www.darkreading.com/application-security/software-supply-chain-chalks-up-security-win-with-crypto-effort.
Chinese Threat Actor Targets Linux, Mac IM Application
Chinese group APT 27, variously known as Iron Tiger, Emissary Panda and LuckyMouse), is alleged to have deployed a JavaScript trojan in a popular instant messaging app called "MiMi". The backdoor first identifies the OS platform of the victim system, then downloads a back door called rshell. This then exfiltrates system information to its C2 server and awaits commands to search for and upload files to the server.
Older versions of the trojanized "MiMi" app also targeted Windows systems. The campaign appears to be targeting Chinese expatriates, perhaps to monitor their activities in other countries. The same threat actor has previously conducted cyberespionage campaigns internationally, attacking defence, healthcare, energy and technology enterprises. They were among several groups exploiting the Microsoft Exchange ProxyLogon vulnerability last year.
Gatlan, Sergiu, Chinese hackers backdoor chat app with new Linux, macOS malware, Bleeping Computer, 12 August 2022. Available online at https://www.bleepingcomputer.com/news/security/chinese-hackers-backdoor-chat-app-with-new-linux-macos-malware/.
NSFW Section (It's Saturday)
Excremental Retribution Exposed
A web service which sent a box of animal faeces, along with personalised message, to enemies of their customers (because surely nobody would do this to their friends?) has been exploited by a customer who discovered an SQL injection vulnerability and downloaded the service's entire database.
Unfortunately for ShitExpress (I couldn't avoid saying it in the end), this customer was pompompurin, the owner of the Breached.co forum - exactly the kind of person who would spot a vulnerability - who was planning to use the service to send some dung to a rival security researcher. Instead, he shared the contents of the database on the forum, revealing the motherlode of abusive messages.
The moral of the story: shit doesn't just happen.
Sharma, Ax, Anonymous poop gifting site hacked, customers exposed, Bleeping Computer, 12 August 2022. Available online at https://www.bleepingcomputer.com/news/security/anonymous-poop-gifting-site-hacked-customers-exposed/.
And that's it for this week!
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]() Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License.
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
Facebook Draws Ire of Privacy and Freedom of Choice Advocates
Facebook is being criticized for surrendering the private messages of a teenager and her mother who were planning to use (and did use) a pharmaceutical product to terminate a pregnancy. The teenager, her mother and a man who assisted with disposal of the fetus have been charged with a number of offences, following investigations by police in Madison County, Nebraska, who had obtained a warrant requiring disclosure of the contents of an electronic communication.
Police subsequently seized the girl's phone and computer and retrieved the body of the fetus, which had been stillborn. The circumstances of the case are not as clear-cut as pro-choice advocates might like - the abortion was performed at 28 weeks gestation, which could be a crime prior to the contentious recent changes brought about by the US Supreme Court - but it does illustrate the way in which more recent cases will be prosecuted, with the cooperation of tech service providers.
The problem here is not Facebook; no US-based company, or company that operates in the US, be it a social media company, an email service provider, a messaging company or a telco, has the power to resist a warrant or court order issued by a US court. Those who seek privacy protections are going to have to use international service providers and also make use of encryption.
Koebler, Jason and Anna Merlan, This Is the Data Facebook Gave Police to Prosecute a Teenager for Abortion, Vice Motherboard, 9 August 2022. Available online at https://www.vice.com/amp/en/article/n7zevd/this-is-the-data-facebook-gave-police-to-prosecute-a-teenager-for-abortion.
Snort Rule Snafu Snookers Office 365
A Snort rule update pushed to Cisco Meraki firewalls accidentally blocked access to Microsoft Office 365. The Snort rule, 1-60381, is commented, "Microsoft Windows IIS denial-of-service attempt" and blocked a number of IP addresses belonging to Microsoft. Disabling the rule restored access, and Cisco has now pushed out an update.
What can we say, but: measure twice and cut once.
GiacomoS, [RESOLVED] Microsoft vulnerability and IPS/SNORT, Meraki Community forum, 11 August 2022. Available online at https://community.meraki.com/t5/Meraki-Service-Notices/RESOLVED-Microsoft-vulnerability-and-IPS-SNORT/ba-p/156649.
Microsoft 365 Status, We're working with our firewall partners to investigate snort rule 1-60381, Twitter thread, 11 August 2022. Available online at https://twitter.com/MSFT365Status/status/1557435310874587136.
SIM Box Used to Blast Smishes
The Australian Federal Police arrested two men who had allegedly used a SIM box to send out hundreds of thousands of SMS phishing messages which linked to fake bank and telco sites in order to capture the victims credentials. The AFP allege the pair had been targeting customers of the Commonwealth Bank of Australia, National Australia Bank and Telstra since 2018.
A SIIM box can hold hundred of SIM cards and can send hundreds of thousands of SMS messages per day.
Noyes, Jenny, Phishing fraudsters used SIM box to fleece hundreds of victims, police allege, Sydney Morning Herald, 11 August 2022. Available online at https://www.smh.com.au/national/nsw/phishing-fraudsters-used-sim-box-to-fleece-hundreds-of-victims-police-allege-20220811-p5b8xv.html.
Ethical Question: Should We Build Quantum Computers?
Quantum physicist Emma McKay, a PhD student at McGill University, is concerned about how people practice science and develop technology. In an interview with the American Physical Society, she expresses the controversial view that perhaps we should not build quantum computers at all. McKay points out that one of the main applications of quantum computers is the optimization of financial market trades - essentially, making the rich richer. Then there are the possible military applications of quantum computers.
On the other hand, quantum annealing - the type of quantum computer currently sold by Canadian company D-Wave - might have wide application in optimization problems. But, says McKay, this might simply be used to optimize traffic flows for single-occupant vehicles, when a better approach from an environmental and economic point of view might be to promote public transport as well as bicycling infrastructure.
Do you remember the Ten Commandments of the Computer Professionals for Social Responsibility? The 9th Commandment says, "Thou shalt think about the social consequences of the program you are writing or the system you are designing". And then remember Shakespeare: it is "more honoured in the breach than in the observance". A timely reminder.
Chen, Sophia, Should We Build Quantum Computers at All?, American Physical Society News, 8 August 2022. Available online at https://www.aps.org/publications/apsnews/202209/build-quantum.cfm.
Ransomware Gang More Trouble Than Ever
The remnants of the Conti ransomware gang have continued to cause more trouble for enterprises all over the world. Several groups have spun off and are operating independently, using the BazarCall tactic pioneered by Conti to gain access to victims' networks.
BazarCall, also known as call-back phishing, starts with an email telling the recipient that a subscription is about to renew, but the payment can be cancelled by calling a particular number. The number is answered by a social engineer, who convinces the caller to start a remote access session, which will be used by a network intruder to scout the network defences and deploy tools which will not be detected.
At least three groups - called Silent Ransom Group, Quantum and Roy/Zeon - are using this technique, which allows them to defeat sophisticated automated defences.
So damaging have these attacks become that the US State Department is offering a $US10 million reward for information on five of the ransomware gang members. Posting a photo of the hacker known as 'Target', the State Department is asking for information about him and four other members known as 'Tramp', 'Dandis', 'Professor' and 'Reshaev' - the information to be provided via a Tor anonymizing network link.
The success of the BazarCall technique's social engineering carries a message: we cannot pin all our hopes on technical controls; when the human becomes the weakest link, we must ramp up our efforts in security education, training and awareness.
Abrams, Lawrence, US govt will pay you $10 million for info on Conti ransomware members, Bleeping Computer, 11 August 2022. Available online at https://www.bleepingcomputer.com/news/security/us-govt-will-pay-you-10-million-for-info-on-conti-ransomware-members/.
Ilascu, Ionut, Conti extortion gangs behind surge of BazarCall phishing attacks, Bleeping Computer, 10 August 2022. Available online at https://www.bleepingcomputer.com/news/security/conti-extortion-gangs-behind-surge-of-bazarcall-phishing-attacks/.
HTTP Request Smuggling Attacks
In a paper released via a Black Hat talk today, PostSwigger Director of Research James Kettle has expanded his previous work on attacks against web servers to show how the same techniques can be used to exploit vulnerabilities in the HTTP/2 request handling of browsers.
The techniques utilized are somewhat too involved to detail here, and rely on interactions between the HTTP/1.1 and /2 and TCP protocols, along with the behaviour of reverse proxies and web content accelerators. For those interested, there's lots of good reading in the references below, while for everyone else, expect updates to popular web server software and browsers as the Bad Guys enjoy reading the same references and develop related exploits.
Kettle, James, Browser-Powered Desync Attacks: A New Frontier in HTTP Request Smuggling, white paper, 10 August 2022. Available online at https://portswigger.net/research/browser-powered-desync-attacks.
Vijayan, Jai, New HTTP Request Smuggling Attacks Target Web Browser, Dark Reading, 11 August 2022. Available online at https://www.darkreading.com/application-security/researcher-at-black-hat-describes-new-htpp-request-smuggling-attack.
Open Source Threat Intelligence - Not As Open As You'd Think
An article by three security researchers from Samsung Research in IEEE Security & Privacy points out that we should be wary of licensing conditions on open-source threat intelligence feeds. In many cases, the information is provided for personal, informational and research purposes only, and in some cases, the site or feed has no licence information or terms of service at all - in which case, no-one can use, copy, modify or distribute the information. In other cases, the meaning of terms like commercial use is unclear, making use risky.
Shim, WooChul, Hyejin Shin and Yong Ho Hwang, On Data Licenses for Open Source Threat Intelligence, IEEE Security & Privacy, Vol 20 No. 4, July/August 2022, pp. 8 - 22. Digital Object Identifier 10.1109/MSEC.2021.3127218.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]() Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License.
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
Cisco Corporate Network Breached by Ransomware Gang
The group, called Yanluowang, managed to exfiltrate some files from one employee's Box folder, and then attempted to extort the networking company. However, it took some work for them to get this far - the attackers had to use a whole series of voice phishing attacks and forged multi-factor authentication push notifications to finally trick a victim into handing over the credentials for his Google account.
From there, though, the gang were able to get VPN access into the company and pivot to domain controllers and Citrix servers, where they exfiltrated more data and installed their tools in an attempt to persist. Despite being evicted, the attackers kept trying to return - Cisco claims, unsuccessfully. No ransomware was installed, but the threat actor's behaviour suggests that would have been one of their next steps if not discovered.
Biasini, Nick, Cisco Talos shares insights related to recent cyber attack on Cisco, Cisco Talos, 10 August 2022. Available online at https://blog.talosintelligence.com/2022/08/recent-cyber-attack.html.
Gatlan, Sergiu, Cisco Hacked by Yanluowang ransomware gang, 2.8 GB allegedly stolen, Bleeping Computer, 10 August 2022. Available online at https://www.bleepingcomputer.com/news/security/cisco-hacked-by-yanluowang-ransomware-gang-28gb-allegedly-stolen/.
5G IoT API's a Disaster Waiting to Happen
One of the benefits of 5G is to move IoT devices off domestic and SME wi-fi networks, where they have to punch holes through NATting routers, onto a high-bandwidth, but - more importantly - low latency cellular network which will allow direct management. In a presentation at Black Hat, Technical University of Berlin researcher Altaf Shaik says that the IoT API's of 10 mobile carriers he examined share common, but serious, vulnerabilities which could allow unauthorised access to data or even direct access to devices on the 5G network.
The 5G standards do not define IoT service platforms, and so a plethora of new protocols have sprung up, many designed by telcos with limited experience in this area. The results include weak authentication and a lack of access controls which can reveal customer data, access to data streams or even direct access to devices via simple replay attacks.
Newman, Lily May, One of 5G's Biggest Features Is a Security Minefield, Wired, 9 August 2022. Available online at https://www.wired.com/story/5g-api-flaws/.
Threat Actors Shift Left
The automation and orchestration of the development and deployment process - generally labeled CI/CD (Continuous Integration / Continuous Deployment) has introduced vulnerabilities which attackers are now exploiting, according to two speakers at Black Hat. In their talk, RCE-as-a-Service: Lessons Learned from 5 Years of Real-World CI/CD Pipeline Compromise, Iain Smart and Viktor Garzdag provide examples of common vulnerabilities in these pipelines:
- Hardcoded credentials in version control systems and source control management
- Over-permissive roles
- Lack of audit, monitoring and alerting
Traditional, on-prem, software development practices were largely secure by virtue of being well inside the enterprise network. Now that source is in shared, cloud-hosted, repositories, along with all the test scripts, manifests and deployment tools that push them into production, they need a lot more attention from security professionals. Even for on-prem deployment, the COVID-19-inspired shift to hybrid work means that developers are often working with cloud-hosted tools. In short, DevOps must become DevSecOps or even SecDevOps.
Seals, Tara, Software Development Pipelines Offer Cybercriminals 'Free-Range' Access to Cloud, On-Prem, Sark Reading, 10 August 2022. Available online at https://www.darkreading.com/application-security/software-development-pipelines-cybercriminals-free-range-access-cloud-on-prem.
Amazon Expands Biometric Payments
Retail giant Amazon is expanding the use of its Amazone One palm print scanning checkout system to 65 Whole Foods stores across California. The system is contactless, reducing the risks of infection; the user can simply hold their hand, palm down, above the scanner. The scheme has, perhaps inevitably, drawn the ire of privacy advocates. - which Amazon has countered by simply offering customers a $10 credit to register for the system.
Axon, Samuel, Amazon begins large-scale rollout of palm print-based payments, Ars Technica, 11 August 2022. Available online at https://arstechnica.com/gadgets/2022/08/amazon-begins-large-scale-rollout-of-palm-print-based-payments/.
Multiple VMware Vulnerabilities
In an advisory, VMware warns of multiple vulnerabilities which will allow privilege escalation, information disclosure and authentication bypass.
Uncredited, Advisory VMSA-2022-0022, 9 August 2022. Available online at https://www.vmware.com/security/advisories/VMSA-2022-0022.html.
CISA Vulnerability Summary
The US Cybersecurity & Infrastructure Security Agency has released its weekly vulnerability summary for the first week of August. Well worth a look, albeit depressing - it really has something for everyone.
CISA, Vulnerability Summary for the Week of August 1, 2022. Available online at https://www.cisa.gov/uscert/ncas/bulletins/sb22-220.
COVID Contact App Finally Scrapped
After over two years, $A21 million and yet only two cases identified, the Australian government has finally canned its much-reviled COVIDSafe contact-tracing app. Many experts - your humble scribe included - warned that the app was an incredibly bad idea, largely due to the vagaries of Bluetooth antenna patterns, the likelihood of false positives from people passing on the other side of walls and windows, power consumption, the inverse square law and many other problems, but a previous government minister with little understanding of, and far too much faith in, technology pressed ahead regardless. As the old saying has it, if you think technology will solve your problem, then you don't understand technology and you don't understand your problem.
No-one will mourn its passing; First Dog on the Moon perhaps said it best:
Black, Jessica, The COVIDSafe app is dead - but was it ever really alive?, ABC News, 10 August 2022. Available online at https://www.abc.net.au/news/2022-08-10/covidsafe-app-scrapped-what-went-wrong/101317746.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
News Stories
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
Intel APIC Vulnerability Breaks Crypto
A couple of security students from Rome and Graz, Austria, have discovered a vulnerability in Intel's SGX security archicture which will leak information via uninitialized memory reads - a variation on the classic Time of Check/Time of Use class of vulnerabilities.
The SGX architecture is intended to protect sensitive data such as encryption keys in memory by the creation of secure memory blocks called enclaves. The proof-of-concept exploit uses a vulnerability in the Advanced Programmable Interrupt Controller to access stale data in registers and thereby break SGX, obtaining a 128-bit AES key in 1.35 seconds with 94% success rate. It can alse extract a 1024-bit RSA key (but who uses those?) in an average of 81 seconds with a 74% success rate.
The lesson here? The complexity of modern CPU's is making it impossible to make guarantees about security. For some years, the use of formal methods in hardware design had made the possible, but for the last 5 years or so, we have seen the growth of CPU vulnerabilities like Spectre, Meltdown and others which created sidechannel attacks, and now ÆPIC. As we have long known, the enemy of security is complexity.
Goodin, Dan, SGX, Intel's supposedly impregnable data fortress, has been breached yet again, Ars Technica, 10 August 2022. Available online at https://arstechnica.com/information-technology/2022/08/architectural-bug-in-some-intel-cpus-is-more-bad-news-for-sgx-users/.
WIndows 11 Crypto Bug Corrupts Data
A newly-discovered bug in Windows 11 affects systems using AES-XTS and AES-GCM encryption modes on Intel Ice Lake, Tiger Lake, Rocket Lake and Alder Lake processors. Let's break this down.
AES-XTS is XEX-based tweaked codebook mode with ciphertext stealing (I won't delve further into this, but it's something I cover in a forthcoming course on crypto for developers), and is primarily used for encrypted filesystems such as Bitlocker, Veracrypt, etc. AES-CGM is much more common - it's the Galois Counter Mode used by the majority of TLS connections on the web.
The processor architectures listed cover some of Intel's 10th-generation laptop processors, as well as all their 11th- and 12th-geeration Core CPU's. AMD's as yet un-released Zen 4 processors will also support the VAES (Vector AES) instructions which underlie the problem.
Microsoft introduced a patch for the problem in the June 2022 security update package for Windows 11 and Windows Server 2022. If you have deployed this patch, you will not be hit with the data corruption problem - but systems running before this may have as-yet-undetected corrupted data - most likely in encrypted filesystems. Clearly, the fix should be applied ASAP. The first version of the patch caused performance degradation, probably because it disabled hardware crypto acceleration. The July 2022 version should remedy this, however.
Unattributed, KB5017259 - Windows devices that have the newest supported processors might be susceptible to data damage, Microsoft Windows support, August 2022. Available online at https://support.microsoft.com/en-us/topic/kb5017259-windows-devices-that-have-the-newest-supported-processors-might-be-susceptible-to-data-damage-d5e7c0cb-6e0a-4865-81ed-c82e91657a24.
Cisco Small Business Routers - Update Urgently
Cisco has disclosed multiple vulnerabilities in their Small Business RV160, RV260, RV340 and RV345 series routers, which can allow a remote code execution (RCE) by an unauthenticated remote threat attacker, or simply trigger a denial of service. There are no workarounds - the only fix is a software update.
You know what to do.
Uncredited, Cisco Small Business RV Series Routers Vulnerabilities, Cisco Security Advisory, 3 August 2022. Available online at https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-sb-mult-vuln-CbVp4SUR.
A New Form of Steganography
The classic approach to steganography was the use of milk, urine and other substances as an invisible ink which would reveal a message when heated over a candle. Now, scientists at the University of Texas at Austin have put a twist on this by storing a 256-bit encryption key into a polymer material made up of sequence-defined polymers - basically long chains of polymers, each of which corresponds to one of 16 different symbols, which they then incorporated into a special ink.
Ouelette, Jennifer, Scientists hid encryption key for Wizard of Oz text in plastic molecules, Ars Technica, 9 August 2022. Available online at https://arstechnica.com/science/2022/08/scientists-encoded-the-wizard-of-oz-in-the-chemical-structure-of-ink/.
Customer Engagement Firm Twilio Breached
Twilio, which provides mass marketing, email and customer communications services, had several employees fall victim to a smishing attack, which gained an as-yet-unidentified threat actor access to some of the company's internal systems. The SMS messages looked credible, taking employees to what looked like Twilio's SSO sign-in page hosted at fake domains.
This illustrates a weakness in using federated identity management systems hosted by external providers - they take the employee out of the company domain to one they don't really take notice of, in order to sign in. The best additional layer of defence is multi-factor authentication - and a text-message-based mTAN is emphatically not the right approach here!
Uncredited, Incident Report: Employee and Customer Account Compromise - August 4, 2022, Twilio Security Blog, 7 August 2022. Available online at https://www.twilio.com/blog/august-2022-social-engineering-attack.
Nice Doggy - Now Roll Over
A few weeks ago, a video of a robot dog firing a machine gun went viral:
If this has been giving you sleepless nights, take comfort from the fact that the robot killer canine is just as vulnerable as your garage door opener - a kill signal sent over a 433 MHz channel will instantly disable the dog. You can use any of many devices, such as a Flipper Zero, to send the signal; if you aren't familiar with these, ask your friendly local car thief.
Gault, Matthew, Hacker Finds Kill Switch for Submachine Gun-Wielding Robot Dog, Vice, 8 August 2022. Available online at https://www.vice.com/en/article/akeexk/hacker-finds-kill-switch-for-submachine-gun-wielding-robot-dog.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
News Stories
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
Targeted Ransomware Attacks on South Korea
South Korean manufacturing, pharmaceutical and healthcare companies are being targeted by Linux and Windows ransomware which will lock up files including VMware ESXi virtual machines. The GiswinLocker ransomware is produced by an otherwise-unidentified threat actor with a good knowledge of South Korean business - the attacks occurred on Korean public holidays and in the early hours of the morning. "Gwisin" means "ghost" in Korean.
The ransom note text files left behind include a lot of very specific information, including the victim company name and the types of data stolen, indicating a highly targeted attack.
Toulas, Bill, New GwisinLocker ransomware encrypts Windows and Linux ESXi servers, Bleeping Computer, 6 August 2022. Available online at https://www.bleepingcomputer.com/news/security/new-gwisinlocker-ransomware-encrypts-windows-and-linux-esxi-servers/.
Cheat Sheet Maps MITRE ATT&CK to Google Cloud Platform
MSSP Expel is offering a mind map cheat sheet which maps the MITRE ATT&CK framework to the services and API calls a threat actor would use at each stage of an attack in Google Cloud Platform. The 18-page map is useful to SOC analysts for incident response triage and investigations as well as to security architects designing instrumentation for SOAR.
It wouldn't be too difficult to re-map this approach to other cloud platforms like AWS and Azure. It's not a playbook, but a very useful adjunct.
Pellett, Kyle, A defender's MITRE ATT&CK cheat sheet for Google Cloud Platform (GCP), Expel Inc, 5 August 2022. Available online at https://expel.com/blog/mitre-attack-cheat-sheet-for-gcp/ (registration required for download).
Fixing Open Source Vulnerabilities At Scale
The fact that thousands of open source projects firstly, are open source and secondly, are hosted on public repositories like GitHub make it possible to use search tools like GitHib's code query language, CodeQL, to find common vulnerabilities across many projects and automate their reporting and fixing. Jonathan Leitschuh, inaugural Dan Kamitsky Fellow at HUMAN Security, has used his fellowship year to work on refining tools and methods for this process, and will be delivering a presentation on it at Black Hat in Las Vegas this week.
Given that open source components permeate not just the open source culture but also vast swathes of the proprietary code ecosystem, vulnerabilities in them can be devastating, as we have seen with the notorious Log4J vulnerability. This research could well have a massive payoff.
Chickowski, Ericka, We Have the Tech to Scale Up Open Source Vulnerability Fixes - Now It's Time to Leverage It, Dark Reading, 9 August 2022. Available online at https://www.darkreading.com/dr-tech/we-have-the-tech-to-scale-up-open-source-vulnerability-fixes-now-it-s-time-to-leverage-it.
Insurer Found Not Liable for Ransomware Remediation
The Federal Court of Australia has delivered a judgement in favour of the insurer in Inchcape Australia Limited v Chubb Insurance Australia Limited [2022] FCA 883. Inchcape had suffered a ransomware attack which had encrypted its primary server, deleted the primary and offsite (!?!) backups, spread to client machines and exfiltrated data, and had claimed for the costs of incident response and forensic investigations, the costs of replacing hardware, data recovery and the additional manpower requirements.
Their policy with Chubb had three separate agreements covering 1, computer systems fraud in general, 2, direct financial loss from computer virus and similar programs, and 3, direct financial loss resulting from the fraudulent modification of electronic data, electronic media or electronic instruction.
The case primarily hinged on whether the expression "direct financial loss resulting directly from" in the latter two agreements would include the incident response costs, hardware replacement, etc. or be limited to just the cost of actually reproducing the lost data, etc.
I have simplified this substantially - Justice Jagot's judgement lays out the questions in much greater detail. The reasoning is very restricted to the specific policy and circumstances, but is a useful reminder to have your corporate counsel review the fine print of your insurance policies. In particular, be aware that cyber insurance policies are designed to provide specific incident response expertise and covers those costs - what Inchcape had was a more general - but tightly worded - policy to cover the costs of data recovery only.
Inchcape Australia Limited v Chubb Insurance Australia Limited [2022] FCA 883, Federal Court of Australia, 1 August 2022. Available online at https://www.austlii.edu.au/cgi-bin/viewdoc/au/cases/cth/FCA/2022/883.html.
Danish 7-Eleven Stores Closed Due to POS Attack
7-Eleven stores throughout Denmark were closed on Monday, due to an early-morning cyber attack on their checkout and point-of-sale systems.
There's a business continuity planning challenge here: keeping an old-fashioned cash register on hand is not going to be any use; since COVID-19 struck, almost everyone uses cashless, contactless, payment these days - in fact, credit cards are less used than smartphone payment systems.
Abrams, Lawrence, 7-Eleven stores in Denmark closed due to a cyberattack, Bleeping Computer, 8 August 2022. Available online at https://www.bleepingcomputer.com/news/security/7-eleven-stores-in-denmark-closed-due-to-a-cyberattack/.
Incident Response Delay Comes Back to Bite Experian
Credit reference company Experian suffered a major breach in July, due to really bad design of its account recovery processes. It appears that customers could regain access to locked accounts by simply recreating them on a different email address, using their name, address, phone number, social security number and answering a few questions based on publicly-available information.
Experian's real problem was that a couple of customers contacted security blogger Brian Krebs, who set out to replicate their experience and investigate further, publishing his findings. At this point, a major vulnerability was now public knowledge, but rather than moving rapidly to fix it, Experian downplayed the problem and claimed that additional controls would prevent account hijacking. Unfortunately, this was incorrect, and a number of people had their accounts hijacked.
Experian is now facing a class action for their failure to fix this issue, with the filing quoting liberally from the KrebsonSecurity article. It is doubtful if much will result from this, but it does illustrate the need to move quickly to really address vulnerability disclosure, rather than relying on crisis communications to manage public sentiment.
Krebs, Brian, Class Action Targets Experian Over Account Security, KrebsOnSecurity, 5 August 2022. Available online at https://krebsonsecurity.com/2022/08/class-action-targets-experian-over-account-security/.
Amazon Acquired iRobot - Here's Why
Last week, retail giant Amazon acquired iRobot Corp., maker of the best home appliance ever, the Roomba (as well as various other mopping, gutter-cleaning and other gizmos). Although Amazon does use Roomba-like gadgets in its warehouses (as does IBM, for temperature monitoring in the aisles of its data centers), and iRobot is a profitable business with lots of growth potential, these are perhaps not the real motivation for the acquisition.
It's about mapping the inside of your home. Amazon has big designs on being a smart-home company; its Echo smart speakers outsell their rivals, in part due to low pricing which Amazon will recoup through the devices' ability to directly order products from the company with minimal user effort. These smart speakers support a smart home ecosystem that can interact with lighting, security cameras, thermostats and much more. The company also sells tablets and streaming services, and has acquired grocery retailer Whole Foods, doorbell manufacturer Ring and wi-fi device manufacturer Eero.
But until now, Amazon hasn't known exactly where these gadgets were. Now, mapping data from the Roomba meandering from room to room will tell the company the size of your home, the layout of the rooms, the furniture layout, and much more. It's going to be interesting to see how privacy advocates and legislators respond to this.
Webb, Alex, Amazon's Roomba Deal Is Really About Mapping Your Home, Bloomberg, 6 August 2022. Available online at https://www.bloomberg.com/news/articles/2022-08-05/amazon-s-irobot-deal-is-about-roomba-s-data-collection.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
News Stories
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
Local Privilege Escalation Vuln in Kaspersky VPN Client
A vulnerability in Kaspersky's VPN Secure Connection for Microsoft Windows will allow an already-authenticated user to gain SYSTEM privilege on the victim's computer. While no exploits for CVE-2022-2735 have been seen in the wild, customers should update to version 21.6 or later.
Seals, Tara, High-Severity Bug in Kaspersky VPN Client Opens Door to PC Takeover, Dark Reading, 5 August 2022. Available online at https://www.darkreading.com/endpoint/high-severity-bug-kaspersky-vpn-client-pc-takeover.
Phishers Exploit Unvalidated Redirects on Amex and Snapchat Sites
The problem of unvalidated redirects and forwards in web server code has been known about since - well, since soon after CGI code first ran on web servers. Yet it continues to catch out many developers and their sites' users, most recently a campaign which was active for over two and a half months, and targeted American Express - who fixed the problem - and Snapchat, which remains vulnerable. Similar attacks have previously targeted Fedex and Microsoft.
Kay, Roger, Phishers Bounce Lures Off Unprotected Snapchat, Amex Sites, INKY Email Security Blog, 3 August 2022. Available online at https://www.inky.com/en/blog/phishers-bounce-lures-off-unprotected-snapchat-amex-sites.
5.4 Million Twitter Accounts Compromised
Not the highest-impact social media breach by a long shot, but Twitter has confirmed that a threat actor used a zero-day exploit to gather the profiles of 5.4 million Twitter users, including verified phone numbers and email addresses, screen names, login name, location and other information. The hacker subsequently sold this data dump to two different interested parties.
While much of this information was public anyway, it may have exposed personal information of users who had pseudonymous accounts for privacy reasons. It also seems likely that the information could be used by the purchasers to run highly-targeted spear-phishing attacks. Twitter recommends that users who may be affected - or suspect they may be affected - should enable multi-factor authentication on their accounts.
Abrams, Lawrence, Twitter confirms zero-day used to expose data of 5.4 million accounts, Bleeping Computer, 5 August 2022. Available online at https://www.bleepingcomputer.com/news/security/twitter-confirms-zero-day-used-to-expose-data-of-54-million-accounts/.
Cloud Billing Risk: Recursive Serverless Functions
I'm almost certain you never foresaw this particular risk: the possibility that a recursive function, running on a serverless cloud platform, could rapidly consume massive amounts of resources before any budget alert could fire to warn you of what's happening. Cloud developers are reporting horror stories on all the major cloud platforms - AWS, Azure and Google Cloud Platform - with one developer burning through $US72,000 in a few hours while exploring and testing.
OK, this isn't strictly security, but it's a big risk and probably worth passing on to your development teams. It's one thing to screw up and max out CPU and memory on your own development workstation - it's quite another to do it on a pay-as-you-go platform that can automagically scale up to consume an entire cloud.
Losio, Renato, Are Recursive Serverless Functions the Biggest Billing Risk on the Cloud?, InfoQ, 6 August 2022. Available online at https://www.infoq.com/news/2022/08/recursive-serverless-functions/.
Traffic Light Protocol Updated to Version 2.0
The Traffic Light Protocol, which governs the dissemination of threat intelligence, has seen its first significant update. The colour WHITE has been replaced by CLEAR (to avoid racial and ethnic overtones as well as the connotation of white being an additive mix of all the other colours) and a new marker, TLP:AMBER+STRICT, has been added. So there are now five levels:
- TLP:RED - for the eyes and ears of individual attendees only; you can act on information but not forward it; used when information cannot be effectively acted upon without significant risk for the privacy, reputation or operations of the organizations involved.
- TLP:AMBER+STRICT - may be shared within recipient's organization only but cannot be shared with customers, business partners or suppliers
- TLP:AMBER - may be shared within the recipient's organization and also with customers or clients
- TLP:GREEN - may be circulated freely within your community (which if not otherwise defined is the cybersecurity/defence community), but not publicly nor outside the community
- TLP:CLEAR - may be freely shared with the world
FIRST, TRAFFIC LIGHT PROTOCOL (TLP): FIRST Standards Definitions and Usage Guidance - Version 2.0, August 2022. Available online at https://www.first.org/tlp/.
Boards Now On Board with Security?
Not quite, not yet. According to a global survey report released by executive recruitment firm Heidrick and Struggles, only 12% of CISO's actually sit on the board of their company, but the situation is improving, in part due to market regulators like the SEC, ASIC and stock markets themselves. Gartner now predicts that 40% of boards will have a dedicated cybersecurity committee overseen by a qualified board member by 2025.
However, growing awareness of cybersecurity incidents and breaches by the board requires a change in approach, as they become inured to 'the sky is falling' pitches for budget increases. By now, many firms have lived through ransomware and other attacks and recovered to resume business as usual. A more measured approach is required to dealing with cybersecurity risks.
Aiello, Matt, et. al., 2021 Global Chief Information Security Officer (CISO) Survey, Heidrick & Struggles, 2022. Available online at https://www.heidrick.com/en/insights/technology-officers/2021-global-chief-information-security-officer-ciso-survey.
Glover, Claudia, Cybersecurity on the board: How the CISO role is evolving for a new era, Tech Monitor, 5 August 2022. Available online at https://techmonitor.ai/technology/cybersecurity/ciso-on-the-board.
IoT Device SSH Servers Used to Form Botnet
A derivative of the Mirai botnet named RapperBot has been rapidly evolving since first discovered back in June, The malware scans IoT devices and attempts to brute-force its way into the embedded SSH server, and has now amassed over 3,500 IP addresses it uses for this purpose. Once it has broken into a device it exfiltrates valid credentials back to its C2 network, and since mid-July, it has switched from propagating further to maintaining remote access into the compromised devices, adding its own public key to the authorized_keys file on the victim. In a nasty twist, it also deletes the existing public keys, which will prevent administrators logging in to fix the issue.
Lakshamanan, Ravie, New IoT RapperBot Malware Targeting Linux Servers via SSH Brute-Forcing Attack, The Hacker News, 6 August 2022. Available online at https://thehackernews.com/2022/08/new-iot-rapperbot-malware-targeting.html.
Weapons Systems Increasingly Complex, Increasingly Vulnerable
As high-tech weapons systems become more complex, relying on networked digital components, they are increasingly difficult to secure. An opinion piece in The Hill calls attention to the need to address the national security risk posed by vulnerabilities in weapons systems ranging from the B2 Spirit bomber, through tactical radio systems down to the engine and transmission controllers of ground combat vehicles.
Gates, Alexander, US strategic advantage depends upon addressing cybersecurity vulnerabilities of weapon systems, The Hill, 6 August 2022. Available online at https://thehill.com/opinion/cybersecurity/3591153-us-strategic-advantage-depends-upon-addressing-cybersecurity-vulnerabilities-of-weapon-systems/.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
The whole concept of identity is a complex one, and this was brought home to me by events of the last week.
I work from home, as does my better half. We have dedicated offices, quite a sophisticated network setup (as you'd expect) and some years ago we switched from using an on-premises Lotus Notes and Domino setup to Google Workspace domains to provide email, calendar and other services for our businesses. This reduced my admin workload markedly, which was a great relief, and Workspace has turned out to be a great resource for many collaborative tasks - you'll notice that some of the course slides on this site are maintained in Google Slides, for example, and we make heavy use of Google Meet, Chat, Groups and Spaces, etc.
We also have a smart home, with voice-actuated lighting, Chromecast with Google TV, Chromecast Audio devices for music in various places, voice-controlled air conditioning and rooftop solar PV which is monitored using a Google Sheets-based dashboard. I also have uploaded music in what used to be Google Play Music and is now YouTube Music, as well as purchased movies in Google Play or YouTube or Google TV or whatever it's called this week.
A couple of weeks ago, our doorbell died. It's a classic battery-operated electro-mechanical chime, suffering the ravages of time and corrosion, so I searched online for a replacement. Nobody makes them any more - the closest replacements are completely electronic, with synthesized tones that really don't appeal. But we already have a home full of smart devices, so the obvious answer is to add a smart doorbell, and an even more obvious next move is to extend our Google ecosystem with a Google Nest doorbell.
Now, I'd already had some hints that this might not be straightforward; our Google Nest smoke detectors don't work in the Google Home app, instead requiring the Nest app. And I found I couldn't set up the Nest app using my Google Workspace account - it gave spurious error messages and in the end I had to resort to a free Gmail account, which is now doing little other than attracting spam.
But I attributed that to the Nest app pre-dating the Google acquisition. By now, surely, Nest had been integrated into the Googleverse, their developers brought up to speed on the Google Way of doing things? And indeed, a Nest Hub I'd bought had configured itself with no problems. So the doorbell should work with it, right?
Boy, was I wrong!
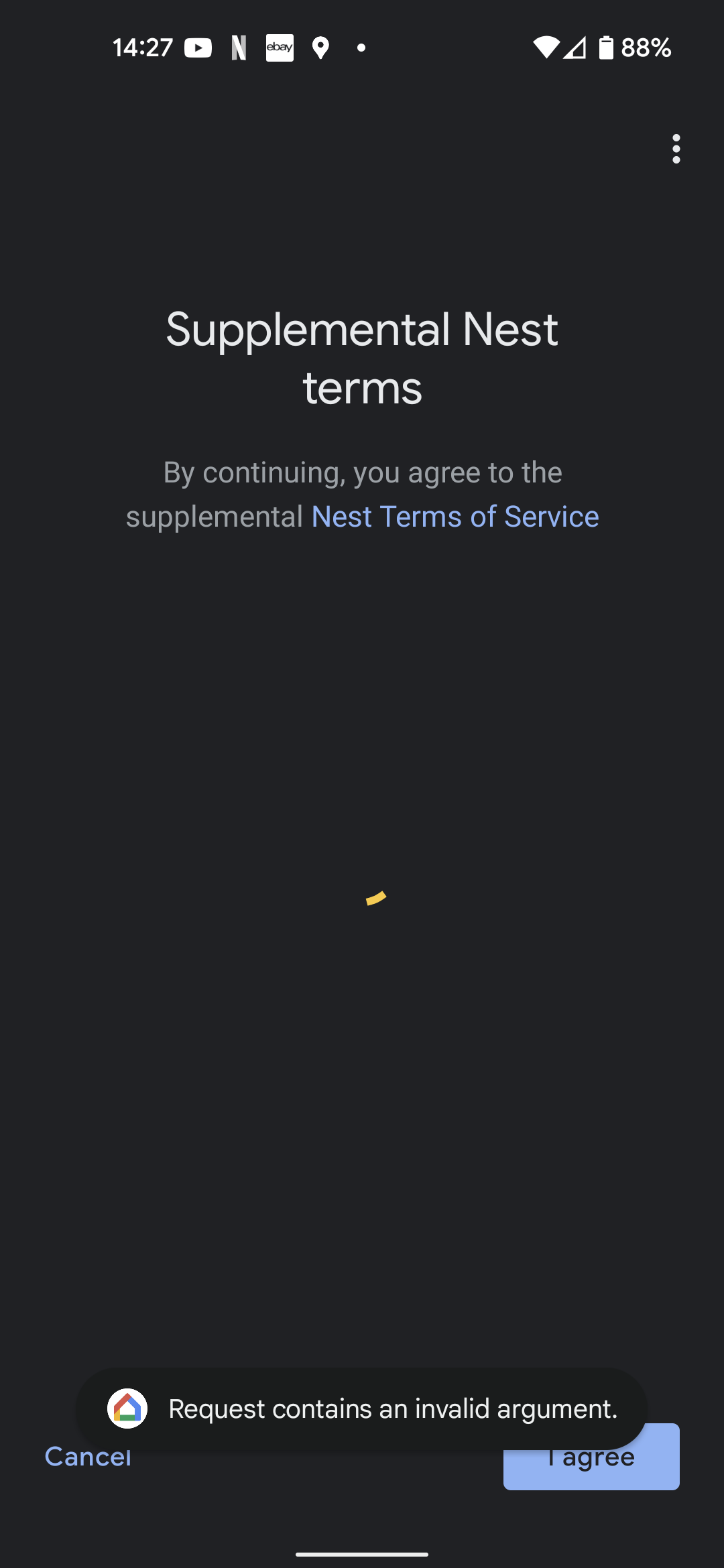 I ordered a doorbell from the Google Store, and it duly arrived. I immediately ripped the package open and set about following the setup instructions, which involve scanning a QR code printed on the doorbell and its packaging. However, when I got to a step which involved "Supplemental Nest terms", tapping on "I agree" I got an error message: "Request contains an invalid argument" and the setup process hung. No matter what I tried, I could not get past that point.
I ordered a doorbell from the Google Store, and it duly arrived. I immediately ripped the package open and set about following the setup instructions, which involve scanning a QR code printed on the doorbell and its packaging. However, when I got to a step which involved "Supplemental Nest terms", tapping on "I agree" I got an error message: "Request contains an invalid argument" and the setup process hung. No matter what I tried, I could not get past that point.
So I did all the usual things, and ended up requesting an online chat session with Nest support (in my experience, it's easier to debug phone-based setups without using the phone, and the chat session also preserves a record - something I felt might be useful).
To cut a long story short, Google's response is essentially that a Google Workspace account is not a Google account. In essence, "thanks for being a paying customer - screw you".
The support tech asked me to use a different email account. I said I wouldn't.
I asked, "Are you saying that a Google device will not work with a Google account?", and got the reply, "It will work with a Google account but it should not be any business account".
No matter what I said, the answer was, "Create another account". That won't work - and there's a very simple reason - every other device in our household is configured to use my Google Workspace account.
In the interests of fairness and accuracy, I later did do what they had recommended - I set up the doorbell using a free Gmail account, and guess what? It worked, but was useless, since whenever the button was pressed, nothing happened on any of the Google Home or Nest Hub devices in our home.
So I went back to the Google Store, and filled in their Returns form - and the very first pull-down option for the return reason in the form was "Does not work with my account". It certainly looks like this is a common complaint.
Why Is This So?
Look, I'm a security architect. I get it. In a Google Workspace account, the data is managed by the organization that runs the domain - in my case, that's my company. Google obviously feels that doorbell events, video recordings etc. are personal data that shouldn't be available to an employer.
But guess what? I am the employer. There's a conflict between Google Workspace and the Google Home app, and its related devices when, as in my case, your Workspace is your Home.
Besides, there are lots of small businesses that are located in converted warehouses, terrace houses (very popular in inner Sydney suburbs and North Sydney) or even suburban brick veneer house-like premises that actually have a front door and need a doorbell. Retails jewelers are an obvious example, but I can think of market research consultancies, accountants, advertising agencies, dentists and optometrists, medical specialists and many others that work this way. In this case, the owner of the doorbell is in no sense a person - it's the business.
We've seen this problem of corporate vs personal data being accessed by corporate or personal systems before. When the Google Home devices and the related Google Assistant feature for phones were first introduced, they were able to access email and calendar information for free Gmail accounts only. I suspect Google were concerned that allowing "home" devices to access information in Workspace accounts would cause them problems in passing SSAE 18 SOC 2 and 3 audits and the like (it's interesting that these devices use voice matching to identify who is speaking and respond appropriate - but this is not really authentication).
But then, a beta program was opened up, and eventually the feature was made fully available. Each morning the little speaker on my desktop greets me at 8:30 am and then tells me my appointments for the day, and will answer questions like "when is my next meeting?". The feature needs to be enabled in the Google Workspace admin console, but that's completely appropriate.
This is a risk management decision that needs to be made by the customer and not by Google. If someone is able to get into my office and somehow access sensitive data by talking to a smart speaker, I've got much bigger problems, primarily with physical security, than I do with voice authentication. I'd probably want to upgrade my physical security controls - perhaps by installing Google Nest cameras and a Google Nest doorbell . . . Oh, wait . . .
Google needs to similarly configure a flag which allows a Nest doorbell owner to accept that their doorbell data will be stored in a Workspace account and - shock! horror! - accessible by their employer, which is themselves. (In fact, I'm not entirely sure that Workspace admins can access that kind of profile data - I can't see anything like it in my own Workspace admin console.) Or it needs to allow a Google Workspace account to define locations which can be managed by Google Workspace.
At heart, the problem is one of our multi-faceted identities. Some of us do have a personal identity and a work identity, and possibly others. Google expects these to be different accounts. However, for some people these are just different facets of a single identity, or maybe it's all one.
For Google, this is a big problem that needs to be addressed.
I've struck lots of problems because of having a Workspace account. The first was trying to get a Xiami Mi Box running Android TV to work; because we had implemented mobile device management, and Workspace assumed that this Android device must be mobile, yet could not run the necessary agent, I never did manage to get it to work.
Then the ability to set reminders was removed, "in order to improve the product". My reminder to plug in a backup drive simply stopped working. I can't tell my smart device to remind me to move my laundry to the tumble dryer in an hour, because I'm a Google Workspace user.
If you are a paying Google customer, everybody else's products work better for you than Google's.
Then there were the Nest Alert smoke detectors - but then, I don't think even ordinary Gmail account users can see them in the Home app yet. If I try to invite my better half, who shares this home, to join the Google Home, I get yet another spurious, "Unable to send invitation - try again later", message. Google One cloud storage, which I got free when I bought a Pixel phone, is not available to me. Family sharing won't work.
The list goes on, and on. This is a problem that crops up again and again in Google's support communities, where volunteers simply tell those who complain what they already know - "this feature is not supported for Workspace accounts. Have a nice day". Don't tell us - tell Google. Before long, threads are simply locked or deleted, to avoid the extent of the customer unrest becoming obvious.
Nobody in senior management at Google seems to have any coherent strategy for building a Google ecosystem, or leveraging their product lines. Products are launched, achieve popularity and are then withdrawn, to join many others in the legendary Google Graveyard. But if you are a paying Google customer, it's even worse: everybody else's products work better for you than Google's. Ring doorbells, Sonos speakers - you name it.
I can't imagine any other company managing to do so much to alienate their best customers.
Epilogue
You couldn't make this stuff up. Here's a newly-posted Google Workspace "Ask Me Anything" video on the subject of cloud identity. Less than four minutes in, the presenter is selling the virtues of a single cloud identity by pointing out that having to have multiple identities, with different credentials is time consuming, not secure, and an unpleasant user experience, requiring different passwords.
https://www.youtube.com/watch?v=c6ddHRc_f0M
So why is Google's answer to the problem of its own products not working with Google Workspace, "create another identity"?
There's an old saying: don't pee on my leg and tell me it's raining.
Welcome to this issue of Security News, for the week commencing 1st August 2022.
News Stories
Russia-Ukraine Cyberwarfare Escalates
As the conventional conflict in Ukraine grinds on, Russia is finding itself on the receiving end of attacks in cyberspace - not just from Ukrainians but from hackers all over the world. Cyber activist group Anonymous, in particular, has launched multiple campaigns which have compromised many websites and databases, changing some file names to "Glory to Ukraine" and deleting most others using a wiper script, and disrupting the web sites of Gazprom and state news (i.e. propaganda) channel Russia Today (RT). They even managed to shut down the control center of the Russian Space Agency, Roscosmos.
Fowler, Jeremiah, Hacker Group Anonymous and Others Targeting Russian Data, Website Planet blog, July 2022. Available online at https://www.websiteplanet.com/blog/cyberwarfare-ukraine-anonymous/.
Bad News for Students Everywhere
The CEO of textbook publisher, Pearson PLC, has said that he hopes blockchain technology will help the company take a cut of secondhand sales of its books.
"In the analogue world, a Pearson textbook was resold up to seven times, and we would only participate in the first sale", he told reporters.
Struggling students everywhere groaned into their ramen bowls.
CISSP course attendees can read more in the wiki's Cryptocurrencies and Blockchain Technology page.
Seal, Thomas, Pearson Says Blockchain Could Make It Money Every Time E-Books Change Hands, Bloomberg Technology, 1 August 2022. Available online at https://www.bloomberg.com/news/articles/2022-08-01/pearson-hopes-blockchain-will-make-it-money-every-time-its-e-books-change-hands.
Craig Wright - Satoshi or Not?
Australian Craig Wright has often
claimed to be the mythical Satoshi Nakomoto, who developed Bitcoin back in 2009.
In August 2022, Wright technically won a libel case against a blogger who had claimed that he was a fraud. However, the judge in the UK High Court case ruled that Wright had given "deliberately false evidence" in the case, and awarded only GBP1 in damages (Milmo, 2022). The claim that Wright was, in fact, Satoshi Nakamoto was not tested in court.
CISSP course attendees can read more in the wiki's Cryptocurrencies and Blockchain Technology page.
Milmo, Dan, Craig Wright wins 'only nominal damages of GBP1 in bitcoin libel case, The Guardian, 2 August 2022. Available online at https://www.theguardian.com/technology/2022/aug/01/craig-wright-wins-only-nominal-damages-of-1-in-bitcoin-libel-case.
Hackers Steal Passwords for 140,000 Payment Terminals
Wiseasy is a popular Android-based payment terminal used in hospitality and retail outlets in the Asia-Pacific region. The company's Wisecloud service provides remote management, configuration and update of its terminals. However, pen-testing and dark web monitoring company Buguard found Wiseasy employee passwords on a dark web marketplace used by cybercriminals.
The passwords, which were stolen by credential-stealing malware, were the only protection for two cloud dashboards - the Cloudeasy system did not use multi-factor authentication or other protections, although MFA has now been added.
CISSP course attendees can read more about Multi-Factor Authentication and password stealers in the course wiki.
Whittaker, Zack, Hackers stole passwords for accessing 140,000 payment terminals, Tech Crunch, 2 August 2022. Available online at https://techcrunch.com/2022/08/01/wiseasy-android-payment-passwords/.
Post-Quantum Cryptography News
The mere threat of quantum computers which could break all widely-deployed public-key cryptoprimitives such as RSA and Diffie-Hellman has been enough to spur frantic development of post-quantum, or quantum-resistant algorithms. At first, development seemed lethargic, but it accelerated in recent years with NIST running an open competition to standardize on the winners.
At the end of the third round, last month, NIST announced one winning algorithm for key encapsulation and four winning signature algorithms. Now, IBM has announced the available of most of these - the CRYSTALS-Kyber key encapsulation algorithm, and the CRYSTALS-Dilithium, FALCON and SPHINCS+ algorithms for signatures.
NIST also announced that four other key encapsulation algorithms, while not adopted as standards, would advance to a fourth round. However, one of these - SIKE (Supersingular Isogeny Key Encapsulation) - is quite probably dead in the water following the unexpected release of a paper detailing an attack which can recover a key in approximately one hour on a single-core PC.
Meanwhile, the ACM (Association for Computing Machinery) Technology Policy Council has released a short technical bulletin highlighting some risks and opportunities which have been obscured by our focus on the code-breaking implications of possible quantum computers. They point out that little progress has been made on quantum cryptanalysis, while powerful quantum simulators could be in use within two years.
CISSP course attendees can read the full background on the algorithms and the NIST competition in the Post-Quantum Cryptography wiki page, and some basic information on quantum computers on the Quantum Cryptography page.
Dames, Ann, How IBM z16 positions you to begin using quantum-safe cryptography, IBM cloud blog, 26 July 2022. Available online at https://www.ibm.com/cloud/blog/announcements/available-on-ibm-z16-future-proof-digital-signatures-with-a-quantum-safe-algorithm-selected-by-nist.
Garfinkel, Simson L. and Chris J. Hoofnagle, Quantum Computing and Simulation, ACM Technology Policy Council TechBrief, July 2022. Available online at https://dl.acm.org/doi/pdf/10.1145/3551664.
Goodin, Dan, Post-quantum encryption contender is taken out by single-core PC and 1 hour, Ars Technica, 2 August 2022. Available online at https://arstechnica.com/information-technology/2022/08/sike-once-a-post-quantum-encryption-contender-is-koed-in-nist-smackdown/.
Attackers Scanning for New Vulnerabilities
A new report from Palo Alto Networks' Unit 42 provides some insights which can assist defenders in planning their incident response plans and playbooks.
First, attackers tend to have particular favourites which they will scan for and repeatedly exploit, with just six CVE categories (ProxyShell, Log4j, ProxyLogon, SonicWall and Fortinet vulns and a vulnerability in Zoho ManageEngine ADSelfService Plus) accounting for more than 87% of vulnerabilities being exploited. These are all well known and have patches or compensating controls; the fact that they keep working clearly shows the importance of proactive patching. A second lesson is the importance of analyzing backwards along the kill chain, to find the vulnerability that led to the later stages of an attack, fix it, and block a campaign.
However, in other cases, some attackers are seen to be scanning for a vulnerability within 15 minutes of a CVE being released. This reinforces the old dilemma - patch as soon as you can, or regression-test the patch before deploying? Your vulnerability management and patch management processes clearly need to deal with this, possibly by patching highly-exposed systems immediately, but performing regression testing before patching well-defended critical systems such as back-end databases.
As found by others, the top access vectors was phishing, followed by software exploits, then brute-force credential attacks targeting RDP.
CISSP course attendees can read more background information in the Patch Management, Vulnerability Management and Incident Response wiki pages.
Edge Editors, Attackers Have 'Favorite' Vulnerabilities to Exploit, Dark Reading, 30 July 2022. Available online at https://www.darkreading.com/edge-threat-monitor/attackers-have-favorite-vulnerabilities-to-exploit.
Unit 42, Incident Response Report 2022, Palo Alto Networks, July 2022. Available online at https://www.paloaltonetworks.com/unit42/2022-incident-response-report.
Stealthy Trojan Bypasses AntiVirus
A new variant of a 2018 bot called Amadey is being distributed via SmokeLoader malware, disguised as software cracks and fake keys which naive people use to try to activate pirated software. Once Amadey has been downloaded, it resides in the Windows TEMP folder and also registers itself as a scheduled task so that it can persist.
From there, it contacts a C2 server and downloads a plug-in to collect environment information such as the current user and computer names, OS and a list of installed applications. It also takes periodic screenshots, which it sends back to the C2 server. It also catalogues the installed anti-malware software, and can bypass antivirus products from 14 different vendors, including Avast, Avira, BitDefender, Kaspersky, Sophos and Microsoft.
After inspecting the gathered information, the attackers can then take any of several follow-up actions, including installing specialized plug-ins, such as an Outlook email stealer, a generic info-stealer called RedLine, or a tool for gathering information about any VPN clients installed on the system.
Interestingly, researchers who examined an earlier version of Amadey noted that it would not install these additional payloads if it judged that the victim was in Russia.
For more information about bots and trojans, CISSP course attendees can see the Trojan wiki page.
Vijayan, Jai, Supercharged Version of Amadey Infostealer & Malware Dropper Bypasses AVs, Dark Reading, 26 July 2022. Available online at https://www.darkreading.com/attacks-breaches/supercharged-version-amadey-infostealer-malware-dropper-bypass-av.
URL Parsing Vulnerability Affects Golang Applications
Application developers increasingly rely on standard function and class libraries in modern languages such as Rust and Go, rather than writing all that low-level code themselves. This is not a bad thing - apart from the productivity gains, writing high-quality, high-performance, versatile low-level code is not easy, and shared code with lots of users and lots of eyes on it is likely to be safer than rolling your own.
Unless it's not, as developers using the Go programming language are finding out. A new vulnerability called ParseThru allows a threat actor to bypass URL argument validation, exposing the API's of applications written in the language to exploitation. The vulnerability is caused by changes to the way the net/url language library handles semicolons (;) in URL arguments - prior to version 1.17 they were treated as separators, but in 1.17 and later, non-URL-encoded semicolons are rejected and a warning logged.
When a Golang API using net/url version 1.17 or later communicates with a back-end service running an earlier version, an attacker is able to send a specially-crafted request containing a semicolon in the URL argument. The API code will ignore this, silently discarding the error message, but the back-end service will process it.
URL parsing vulnerabilities are not unique to Go, of course - this year alone they have been seen in libraries for C, JavaScript, PHP, Python and Ruby.
The take-away is that configuration management databases need to have a high degree of granularity. Would you know if an application you depended upon used two different versions of Go's net/url and was therefore vulnerable?
For CISSP course attendees, there's a little bit more information about the Go programming language in the course wiki, as well as info on configuration management databases.
Lakshmanan, Ravie, New 'ParseThru' Parameter Smuggling Vulnerability Affects Golang-based Applications, The Hacker News, 2 August 2022. Available online at https://thehackernews.com/2022/08/new-parsethru-parameter-smuggling.html.
Atlasssian Resolves RCE Vulnerability in Jira Server
Continuing its (Australian) winter of woe, has acted to fix a remote code execution vulnerability in its widely-used Jira Server and Data Center products. While the exploit, which worked via template injection in the Email Templates feature, required admin permissions, the company still gave it at CVSS score of 7.8.
Chirgwin, Richard, Atlassian patches email template vulnerability in Jira, IT News, 3 August 2022. Available online at https://www.itnews.com.au/news/atlassian-patches-email-template-vulnerability-in-jira-583531.
Australian Businesses Rate Cybersecurity As Highest Risk
While 20% of international respondents to PWC's annual Global Risk Survey rated 'cyber' as the top risk, behind market risks (22%) and business operating model risk (21%), Australian businesses see things differently, with 32% seeing 'cyber' as the top risk. Business operating model risk and geopolitical risks came well behind, at 22% and 19% respectively - in fact, the impact of COVID-19, economic volatility and climate change trailed even further behind.
This, in part, reflects increasing government attention, with the appointment of a Federal Minister for Home Affairs and Minister for Cyber Security (Claire O'Neil) - the first time cybersecurity has been a dedicated cabinet portfolio. However, it may also reflect an increasing realization that historical under-investment in cybersecurity has left companies exposed.
Perhaps we are finally getting the message through?
Crethar, Rick, et. al., PWC 2022 Global Risk Survey - Australian Highlights, Price Waterhouse Coopers, July 2022. Available online at https://www.pwc.com.au/publications/global-risk-survey/2022-GRS-Australian-highlights.pdf.
Samaratunga, Sam, et. al., PWC 2022 Global Risk Survey, Price Waterhouse Coopers, July 2022. Available online at https://www.pwc.com/us/en/services/consulting/cybersecurity-risk-regulatory/library/global-risk-survey.html.
New Exploitation Framework Found in the Wild
Many of us are familiar with the Cobalt Strike toolkit, which is widely used by both sides of the business. Now researchers have found a similar framework, named Manjusaka, which seems to have been developed and deployed by Chinese threat actors to attack both Windows and Linux systems. It joins an earlier toolkit called Brute Ratel.
Manjusaka consists of a versatile remote access trojan (RAT) which can execute arbitrary commands via a shell, steal credentials from the OS itself, web browsers, and wifi interfaces, as well as capturing screenshots. A matching file management module can explore directories and files, read, write and delete files, and move them.
A unique characteristic of Manjusaka is the fact that it is written in the Go programming language, while its implants are written in the cross-platform language, Rust, making possible attacks on different processors, such as those found in embedded systems and industrial control systems.
Abrams, Lawrence, Ransomware, hacking groups move from Cobalt Strike to Brute Ratel, Bleeping Computer, 6 July 2022. Available online at https://www.bleepingcomputer.com/news/security/ransomware-hacking-groups-move-from-cobalt-strike-to-brute-ratel/.
Toulas, Bill, Chinese hackers use new Cobalt Strike -like attack framework, Bleeping Computer, 2 August 2022. Available online at https://www.bleepingcomputer.com/news/security/chinese-hackers-use-new-cobalt-strike-like-attack-framework/.
China - Taiwan Tensions Could Impact Chip Shortages
The semiconductor supply chain woes that have bedevilled many industries could be made much worse if China was to invade Taiwan. The world's biggest semiconductor manufacturer, TSMC, is headquartered in Hsinchu, Taiwan, and would be rendered inoperable in any conflict.
"Nobody can control TSMC by force. If you take a military force or invasion, you will render TSMC factory not operable", the Chairman of the company said in an interview with CNN this week. "Because this is such a sophisticated manufacturing facility, it depends on real-time connection with the outside world, with Europe, with Japan, with U.S., from materials to chemicals to spare parts to engineering software and diagnosis."
This gives the western world yet another incentive to maintain stability in the region - but in this respect, China would gain nothing, either.
Zakaria, Fareed, On GPS: Can China afford to attack Taiwan?, CNN, undated. Available online at https://edition.cnn.com/videos/tv/2022/07/31/exp-gps-0731-mark-liu-taiwan-semiconductors.cnn.
India Backs Down on Data Privacy
While the Indian government has passed far-reaching legislation dealing with cybersecurity and privacy, it has put on hold the introduction of its long-awaited Personal Data Protection Bill.
The bill, which was introduced in 2019, had attracted criticism from all sides: tech giants Meta, Google and Amazon expressed concerns as expected, but privacy groups had complained that the bill exempted government departments, prioritized the interests of large corporations and did not adequately respect the fundamental right to privacy.
A parliamentary panel received dozens of recommendations and proposed amendments which identified issues that were relevant but beyond the scope of a modern digital privacy law, according to Junior IT Minister Rajeev Chandrasekhar. The government will now work on a new comprehensive legal framework and present a new bill.
Given that India is the world's second-largest Internet market and many companies have dealings there, the passage of a sweeping privacy bill there could pose challenges, especially if it is tighter that the EU's GDPR, which many find challenging enough.
CISSP course attendees can find more background in the course wiki's Privacy page.
Singh, Manish, India withdraws personal data protection bill that alarmed tech giants, TechCrunch, 3 August 2022. Available online at https://techcrunch.com/2022/08/03/india-government-to-withdraw-personal-data-protection-bill/.
VMWare Vulnerabilities - Patch Promptly!
VMware has released security updates to address multiple vulnerabilities
in multiple products
VMware Workspace ONE Access, Identity Manager and vRealize Automation contain an authentication bypass vulnerability (CVE-2022-31656) affecting local domain users. VMware has evaluated the severity of this issue to be in the Critical severity range with a maximum CVSSv3 base score of 9.8.
VMware Workspace ONE Access, Identity Manager and vRealize Automation contain a remote code execution vulnerability (CVE-2022-31658). VMware has evaluated the severity of this issue to be in the Important severity range with a maximum CVSSv3 base score of 8.0.
VMware Workspace ONE Access and Identity Manager contain a remote code execution vulnerability (CVE-2022-31659), which VMware has evaluated to be in the Important severity range with a maximum CVSSv3 base score of 8.0.
And many, many more . . . See https://www.vmware.com/security/advisories/VMSA-2022-0021.html for full details.
Universities Expose Students To Email Threats
A study of DMARC reports done by Proofpoint has revealed that universities are not doing a good job of securing their student email systems, exposing students to spam, phishing, malmail-based ransomware and other email-based threats.
While 65% of the top US and UK universities - 13 out of 20 - did have a base level of DMARC protection, 5 of the top 10 US universities did not publish any level of DMARC record, Proofpoint found.
Montalbano, Elizabeth, Universities Put Email Users at Cyber Risk, ThreatPost, 2 August 2022. Available online at https://threatpost.com/universities-email-cyber-risk/180342/.
Checkpoint Releases its 2022 Mid-Year Cyber Attack Trends Report
Security vendor Checkpoint has released its mid-year report on cyber attack trends and, as you'd expect, it makes depressing reading. Major trends include continuing growth in cyber attacks - up 42% globally - cyberwarfare (with associated hacktivism) becoming an essential part of conventional warfare, ransomware remaining the number one threat, supply chain attacks moving into the cloud, and everyday life now being noticeably impacted by cybercrime.
The chapter on prevention of attacks is interesting; for some years the focus in our industry seems to have swung away from prevention towards detection and response, leading to a perpetual game of whack-a-mole as entry-level SOC analysts frantically respond to what they see in Splunk - the theory being that the Bad Guys will get in anyway, so detection and response are where the rubber meets the road. The problem is that it can get hard to spot the Bad Guys, hidden as they are among the Very Naughty Boys - you'd better have some experienced threat hunters on hand to sort the wheat from the chaff
Perhaps it is time to apply a bit more effort to prevention, through the application of some basic security architecture and hygiene principles - this will improve the signal-to-noise ratio and also reduce the manpower requirements. Of course, Checkpoint would love to sell you a complete 'solution' to do a lot of this, but the basic principles are universally applicable.
Horowitz, Maya, et. al., Cyber Attack Trends 2022 Mid-Year Report, Checkpoint Research, August 2022. Available online at https://pages.checkpoint.com/cyber-attack-2022-trends.html.
Cryptocurrency Irony Abounds
Cryptocurrencies aren't usually a concern for infosec professionals, but you probably get dragged into conversations about cryptocurrencies and blockchain technology (which is why the CISSP course wiki has a page devoted to the topic). After I've regaled people with a few horror stories of rug pulls and other scams, my interlocutors generally lose interest, and I check off my good deed for the day.
But the horror stories continue. The collapse of cryptocurrency lender Celsius has provided yet another cautionary tale, this time laced with irony. The crypto giant was "marketing itself much like a bank but without the same regulations" (my emphasis), the lack of regulation presumably being why investors could expect huge returns. When the inevitable happened and the company collapsed, those same investors are now petitioning the bankruptcy court in hopes that regulations might allow them to recover at least some of their money.
How can I put this? If you take huge risks on unregulated . . . for lack of a better word, scams . . . then you cannot rely on regulation to kiss it better.
It would be funny, except that people have lost their life savings, causing real hardship.
In related news, the market is being flooded with second-hand Rolex and Patek Phillipe watches, as desperate crypto bros are forced to liquidate some of their toys.
Bogle, Ariel, Australian investors left with nothing as cryptocurrency giant Celsius goes bankrupt, ABC News, 4 August 2022. Available online at https://www.abc.net.au/news/science/2022-08-04/cryptocurrency-celsius-network-bankruptcy-australian-investors/101293028.
Hoffman, Andy, The Crypto Collaps Has Flooded the Market With Rolex and Patek, Bloomberg Pursuits, 29 July 2022. Available online at https://www.bloomberg.com/news/articles/2022-07-29/the-crypto-collapse-has-flooded-the-market-with-rolex-and-patek.
Everyone's a Winner in the Upcoming (ISC)² Board of Directors Election
In November, (ISC)² will run the election for its Board of Directors. There are five open positions, and by coincidence, the Board's Nomination Committee has recommended, and the entire Board has endorsed, five candidates. Unless a few candidates manage to raise the required 500 signatures to successfully petition to be included in the ballot, it's hardly an election at all.
Lest readers think this is no big deal, here are a few facts and figures: according to (ISC)²'s IRS form 990, its gross receipts for the last reported financial year were $US85,362,992 - not exactly chicken feed - and its assets were $US115,725,304. CISSP's might want to ask themselves whether this non-profit is delivering value for the Annual Maintenance Fees; those who think not might consider petitioning to stand for election - instructions were in the Board Candidates announcement email they received yesterday. The deadline is 2 September - better start organising those signatures now!
(Form 990 figures sourced from https://www.guidestar.org).
Remote Worker Reprimanded for Using Mouse Jiggler
A cautionary tale: telecommuter Gabrielle Judge was reprimanded by her employer for using a 'mouse jiggler' program, which keeps a computer awake and gives the appearance the worker is online and available. The program was not the only issue - apparently she had missed some meetings and explained offline periods as due to thunderstorms.
Security lessons: Obviously, there's the issue of a user installing unauthorised software (but if this is really a concern, use application whitelisting and don't give the user local admin privileges). But then there's the issue of security staff being dragged into policing employee productivity and timekeeping. It's not a security issue, but one of management supervision, and security can have a fraught relationship with staff anyway, with constant "Don't do this, don't do that" messaging. This just further erodes the trust we need. What do you think?
Harding, Rebekah, 'My manager caught me': Remote worker says they got reprimanded for using 'mouse jiggler' app, sparking debate, Daily Dot, 1 August 2022. Available online at https://www.dailydot.com/irl/remote-work-mouse-jiggler/.
Zero-Day Defence Hints
An article by Akamai's Principal Security Researcher provides a list of useful techniques for hardening defences against zero-day exploits, returning us to the them of stiffening defences, rather than operating reactively. The techniques should be well known to all of us, but it's good to be reminded now and again:
- Monitor and update from vulnerability scanner repositories
- Make the most of your web application firewall
- Monitor client reputation
- Control traffic rates
- Watch out for bots
- Don't overlook outbound activity
- Sequester identified attack sessions
- Contain the blast radius (network enclaves, microsegmentation)
CISSP course attendees can find more resources throughout the course wiki, but especially on the Cyber Resilience page
Barnett, Ryan, Zero-Day Defense: Tips for Defusing the Threat, Dark Reading, 4 August 2022. Available online at https://www.darkreading.com/attacks-breaches/zero-day-defense-tips-for-defusing-the-threat.
GitHub Projects Cloned, Not Hacked, to Distribute Malware
Cloning of GitHub projects is not uncommon as people fork open-source projects to create customised derivatives. But attackers have cottoned on to this technique as a way of distributing back-doored versions and malware. Software developer Stephen Lacy dropped a bombshell when he revealed that he had discovered over 35,000 different cloned github repositories, including clones of crypto, golang, python, js, bash and docker. The malware is added to rpm package install scripts, docker images and install documentation.
The malicious projects were easily identified by a single IoC, the URL of what it presumably a C2 server - which suggests a single group is behind this attack.
Update: a day later, Paul Ducklin at Sophos followed up with some more information. A Twitter account going under the name of "pl0x_plox_chiken_p0x" claims to have created the cloned projects as part of some bugbounty research. To which we can only say: pull the other leg, squire - it has got bells on.
The lesson: it's safer to install software as signed packages from official distribution repositories, and when looking for software, don't search GitHib but instead follow links from official software project pages.
Ducklin, Paul, GitHub blighted by "researcher" who created thousands of malicious projects, Sophos Naked Security, 4 August 2022. Available online at https://nakedsecurity.sophos.com/2022/08/04/github-blighted-by-researcher-who-created-thousands-of-malicious-projects/.
Sharma, Ax, 35,000 repos not hacked - but clones flood GitHub to serve malware, Bleeping Computer, 3 August 2022. Available online at https://www.bleepingcomputer.com/news/security/35-000-code-repos-not-hacked-but-clones-flood-github-to-serve-malware/.
Malware Masquerades as Legit Software
Yet another reason to block users installing unauthorised software: threat actors are tricking users into downloading and installing malware by making it look like popular programs. The most popular mimicked applications include Skype, Adobe Reader, VLC Player, 7-Zip, TeamViewer, CCleaner, Microsoft Edge, Steam, Zoom and WhatsApp.
Independent users - working from home or in SME's, etc. - often simply Google for software they need to join webinars and meetings, unzip files, or perform other tasks. So they Google for them - and very often, unauthorised distribution sites appear at the top of the results page - and, of course, the attackers can simply pay Google to ensure they are at the top of the page. They also register plausible-looking domain names, add the icon of the genuine product to their infected installer program and generally look authentic and plausible. In other cases, the genuine software product is simply packaged with other malware infectors, or the malware is installed from within a modified installation script.
Lakshamanan, Ravie, VirusTotal Reveals Most Impersonated Software in Malware Attacks, The Hacker News, 3 August 2022. Available online at https://thehackernews.com/2022/08/virustotal-reveals-most-impersonated.html.
Draytek Vigor Routers RCE Vulnerability
Alhtough Draytek routers are not normally found in enterprise networks, the prevalence of telecommuting and hybrid work means that we need to keep a watching brief on devices like these that are widely deployed in homes and small businesses. Another vulnerability (CVE-2022-032548) has popped up, and given that this is an RCE vuln with a CVSS score of 10 and these routers are a favourite target of Chinese state-sponsored attackers, this one is worthy of prompt action.
Laulheret, Philippe, Unauthenticated Remote Code Execution in a Wide Range of DrayTek Vigor Routers, Trellix, 3 August 2022. Available online at https://www.trellix.com/en-us/about/newsroom/stories/threat-labs/rce-in-dratyek-routers.html.
Security Training - Common Mistakes
The gap between the informed and always-on approach of security professionals and the sleepy approach of the average user means that we are not always the most sympathetic and well-equipped people to design and especially deliver security education, training and awareness to The Great Unwashed - err, I mean, the non-technical personnel in our enterprises. Nonetheless, there are some activities we typically have to be involved in, and one of these is phishing simulations.
Given that phishing is the number one attack vector - just ask any pen-tester how effective it is for them - it's worth doing this right, and a short article from CybReady gives three common phishing simulation mistakes that can sabotage our training efforts:
- Testing instead of educating - trying to catch and punish repeat offenders is counterproductive
- Using the same simulation for all employees - this will only catch the stragglers of the herd
- Relying on data from a single campaign
CISSP course attendees will find more tips in our Security Education, Training and Awareness wiki page.
CyebReady staff, Three Common Mistakes That May Sabotage Your Security Training, The Hacker News, 4 August 2022. Available online at https://thehackernews.com/2022/08/three-common-mistakes-that-may-sabotage.html.
Lockheed Martin Manufacturing Systems Targeted by Russian Hacktivists
The Russia-Ukraine conflict continues to spill over into cyberspace. According to Killmilk, the leader of pro-Russian hacker group Killnet, his group has switched from its earlier DDoS attacks on such targets as Lithuanian government and business, the website of the US Congress and - for some weird reason - the website of a Connecticut airport, to a more sophisticated attack on the manufacturing systems of defence contractor Lockheed Martin.
Killmilk has claimed he would also leak personal information of the company's employees so that they could be "persecuted and destroyed around the world", and has set out to recruit other groups to the cause: "I call on all hacker groups to create an escalation in Lockheed Martin's production cycles around the world, as well as to spread personal information about the terrorists of this company", he posted on Telegram.
In related news, the Russian military has claimed to have hacked into the US-supplied HIMARS Multiple Launch Rockets System which Ukraine has been putting to devastatingly good use against Russian command centres, ammo dumps and supplies.
Kadam, Tammay, Double Whammy: Russian Hackers Launch Cyber Attacks On Lockheed Martin; Armed Forces Hack Into HIMARS - Reports, The Eurasian Times, 2 August 2022. Available online at https://eurasiantimes.com/russian-hackers-launch-cyber-attacks-on-lockheed-martin/.
Top Malware Strains of 2021
The US Cybersecurity & Infrastructure Security Agency and Australian Cyber Security Centre have issued a joint advisory (Alert AA22-216A) listing a hit parade of 2021's malware. Probably most concerning is that two aging bits of code - the Qakbot and Ursnif banking trojans - have continued to evolve, adding new functionality such as reconnaisance, lateral movement, data gathering and infiltration, payload dropping and the formation of botnets.
As discussed here previously, phishing and malmail remain the most popular vectors for delivery, followed by RDP brute-forcing, and the best defensive controls remain the obvious ones: proactive patching, security education, training and awareness, offline, offsite backups and multi-factor authentication.
The advisory includes brief descriptions of the top malware strains - Agent Tesla, AZORult, Formbook, Ursnif, LokiBot, MOUSEISLAND, NanoCore, Qakbot, Remcos, TrickBot and GootLoader - as well as Snort signatures for them.
CISA and ACSC, 2021 Top Malware Strains, Alert AA22-216A, 4 August 2022. Available online at https://www.cisa.gov/uscert/ncas/alerts/aa22-216a.
Identity and Access Management is the New Perimeter
The process of deperimeterization and movement to cloud has shifted our focus away from firewalls and network security. In an upcoming talk at Black Hat in Las Vegas, Igal Gofman, will make the case that threat actors have also shifted focus - to cloud-hosted IAM systems. He's got a good point - many enterprises, of all sizes, have cut costs by migrating to SaaS systems like Google Workspace and Microsoft 365, as well as building systems using PaaS and IaaS. This has now led to increasingly complex cloud architectures in which services authenticate to each other via API keys.
The problem is, says Gofman, that the Bad Guys are figuring out ways to compromise these identities, and his talk will cover these techniques, the competing cloud providers' security architectures, as well as open-source tools for gaining visibility into infrastructure.
Seals, Tara, Cyberattackers Increasingly Target Cloud IAM as a Weak Link, Dark Reading, 5 August 2022. Available online at https://www.darkreading.com/cloud/cyberattackers-increasingly-target-cloud-iam-as-a-weak-link.
Getting Started With Post-Quantum Crypto
Cloudflare has quickly jumped on the post-quantum bandwagon, and has encouraged others to do so as well by adding support for the CRYSTALS-Kyber key encapsulation algorithm on a number of test domains, and also adding support for CRYSTALS-Kyber in forks of the BoringSSL and Go open-source projects. This will allow security architects to investigate the performance and RAM requirement impact of using this algorithm.
Westerbaan, Bas, Christopher Patton and Peter Wu, Experiment with post-quantum cryptography today, Cloudflare blog, 4 August 2022. Available online at https://blog.cloudflare.com/experiment-with-pq/.
Logical Qubits Used for First Calculation
Researchers have, for several years, been trying to improve the stability of the qubits that form the basis of quantum computers. Last year, both Google and Honeywell announced significant advances by linking qubits into more stable groups called logical qubits, which use quantum error-correction. Without this, current quantum computers have error rates as high as one in one-thousand, which is clearly insufficient for even simple computing tasks.
Now, startup Quaninuum, formed through a merger between Cambridge Quantum and Honeywell Quantum Solutions, has been able to demonstrate - wait for it - calculations performed using a pair of logical qubits. This might not sound like much, but this is one of those 'walk before you can run' steps that will eventually make quantum computers practical.
Google Quantum AI, Exponential suppression of bit or phase errors with cyclic error correction, Nature, vol. 595, no. 7867, pp. 383–387, Jul.y 2021. doi: 10.1038/s41586-021-03588-y.
[Ryan-Anderson, C. et al., Realization of real-time fault-tolerant quantum error correction, arXiv, Jul. 15, 2021. Available online at http://arxiv.org/abs/2107.07505.
Shankland, Stephen, This '90's-Era Quantum Computing Idea Could Lead to a Massive Breakthrough, CNet, 5 August 2022. Available online at https://www.cnet.com/tech/computing/new-technique-brings-quantum-computers-closer-to-their-promise/.
Final Funny
Tying Spammers in Knots
Courtesy of contributor Peter Hillier: Security researcher Troy Hunt, of https://haveibeenpwned.com/ fame has wreaked vengeance on spammers by replying to them and inviting them to register on a site via an online form which ties them up in password generation hell. 😂
This reminds me of a similar technique I used to use on unsolicited salespersons calling our company. I had created a script for our Asterisk VoIP PBX which would read the weather forecast from the Bureau of Meterology web site every few hours, strip out the HTML, and drop the resulting text in a file. I had a matching extension number which, when dialled, would read the contents of the file via a text-to-speech library.
So when someone rang and tried to sell me cheaper electricity, or long-distance services, or whatever, I would quickly reply, "Sorry - you're talking to the wrong person. I'm not in charge of that, but I'll transfer you to the right person, if you'll just hold for a few seconds". Then I'd transfer them to that extension, leaving them befuddled by what sounded like Stephen Hawking regaling them with the Sydney weather forecast.
They never rang back.
Fraunfelder, Mark, This guy made a diabolical form to send spammers to password purgatory, BoingBoing, 4 August 2022. Available online at https://boingboing.net/2022/08/04/this-guy-made-a-diabolical-form-to-send-spammers-to-password-purgatory.html.
That ends this weekly security news summary. I'll resume on Monday with a new daily format which should be smaller, easier to read and keep track of. Watch for it in your RSS feed or at https://www.lesbell.com.au/blog/index.php.