Les Bell and Associates Pty Ltd
Blog entries about Les Bell and Associates Pty Ltd
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
Microsoft Adds Passkey Support to Windows 11
Microsoft has, for many years, been engaged in the Sisyphean task of securing an increasingly complex software stack. These two forces are in continual opposition; as the old saw has it, the enemy of security is complexity. But to give them their credit, the Redmondites keep plugging away at it, and things are, gradually, getting better.
The architecture that was reborn with Windows Vista has allowed the firm to take advantage of a range of hardware and software innovations, such as the use of the Trusted Platform Module (TPM) to provide a root of trust for a secure boot process, core isolation features like Hypervisor-protected Code Integrity and enabling the use of shadow stacks - part of Intel's Control-flow Enforcement Technology - for code running in kernel mode, thereby mitigating buffer overflows. While this has caused pain for device driver and application developers who use non-standard techniques - and their users - it has paid off.
The firm has now announced support for passkeys - an implementation of the FIDO2 passwordless authentication system - in Windows 11. Users will be able to create, use and protect passkeys using Windows Hello or Windows Hell for Business, or using their phone, authenticating using their face, fingerprint or device PIN. The Windows 11 implementation will work with multiple browsers including Edge (obviously), Google Chrome, Firefox and others. All we need now is for the mass of web sites to add support for passkeys.
Users with FIDO2 security keys or Windows Hello for Business will now be able to eliminate passwords altogether; in fact Azure Active Directory (now renamed Entra ID) administrators can configure policy so that users will no longer even see the option for password entry at logon. Another new feature is 'Config Refresh', which mitigates attempts to tamper with the registry by resetting it periodically (every 90 minutes by default, but every 30 minutes if desired). There are also new configuration options for the Windows Firewall.
This all represents another step towards a password-less world - something that will come as a relief to security professionals everywhere, as it will dramatically reduce phishing attacks.
In other Microsoft security news, the company's Security Resource Center blog has a nice profile of Australian-born security researcher Rocco Calvi, who has been continually at or near the top of the MSRC Most Valuable Researcher leaderboard in recent years.
MSRC, Journey Down Under: How Rocco Became Australia’s Premier Hacker, blog post, 25 September 2023. Available online at https://msrc.microsoft.com/blog/2023/09/journey-down-under-how-rocco-became-australias-premier-hacker/.
Weston, David, New security features in Windows 11 protect users and empower IT, blog post, 26 September 2023. Available online at https://www.microsoft.com/en-us/security/blog/2023/09/26/new-security-features-in-windows-11-protect-users-and-empower-it/.
RaaS Groups Share Infrastructure, Tools
The Ransomware-as-a-Service ecosystem is a highly dynamic one, with groups splintering, members forming new groups, re-using, adapting and evolving TTP's on a continual basis. It seems that the groups may also share infrastructure, or at least, pass it on to new users. A new report from Group-IB Threat Intelligence and its associates describes a new group, called ShadowSyndicate, that has taken this to new levels.
The key which allowed the Group-IB research team to identify the ShadowSyndicate infrastructure was the presence of the same SSH key fingerprint on many servers - 85 at the time of writing. The group has been working with various ransomware groups and their affiliates since July 2022, using a set of 'off-the-shelf' tools including Cobalt Strike (52 of those servers were used for Cobalt Strike C2), IcedID and Silver malware.
The researchers also linked ShadowSyndicate to a Quantum ransomware campaign in September 2022, Nokoyama ransomware campaigns in October and November 2022, and ALPHV activity in February 2023. It is possible ShadowSyndicate has also been associated with Royal, Cl0p, Cactus and Play ransomware campaigns, with connections between ShadowSyndicate's infrastructure and Cl0p/Truebot, which is one of the most successful ransomware operators.
The ShadowSyndicate infrastructure is widely dispersed - most of it is in Panama, Cyprus or the Russian Federation, but there are servers in locations such as the Seychelles, the Netherlands and Honduras.
The Group-IB blog post provides a full analysis as well as IOC's such as IP addresses, and domain names.
Switzer, Eline and Joshua Penny, Dusting for fingerprints: ShadowSyndicate, a new RaaS player?, blog post, 26 September 2023. Available online at https://www.group-ib.com/blog/shadowsyndicate-raas/.
Upcoming Courses
- SE221 CISSP Fast Track Review, Virtual/Online, 13 - 17 November 2023
- SE221 CISSP Fast Track Review, Sydney, 4 - 8 December 2023
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
New Backdoor Targets Middle East Journalists, Dissidents
A new backdoor, which targets journalists, dissidents and political activists in the Middle East with the objective of cyber-espionage, has been discovered by ESET researchers. The backdoor, dubbed Deadglyph, is attributed to the Stealth Falcon APT, also known as FruityArmor, which is associated with the United Arab Emirates, and was originally discovered by Citizen Lab, who saw it conducting spyware attacks. It was also seen in 2019, when ESET analyzed an unusual backdoor it was then using.
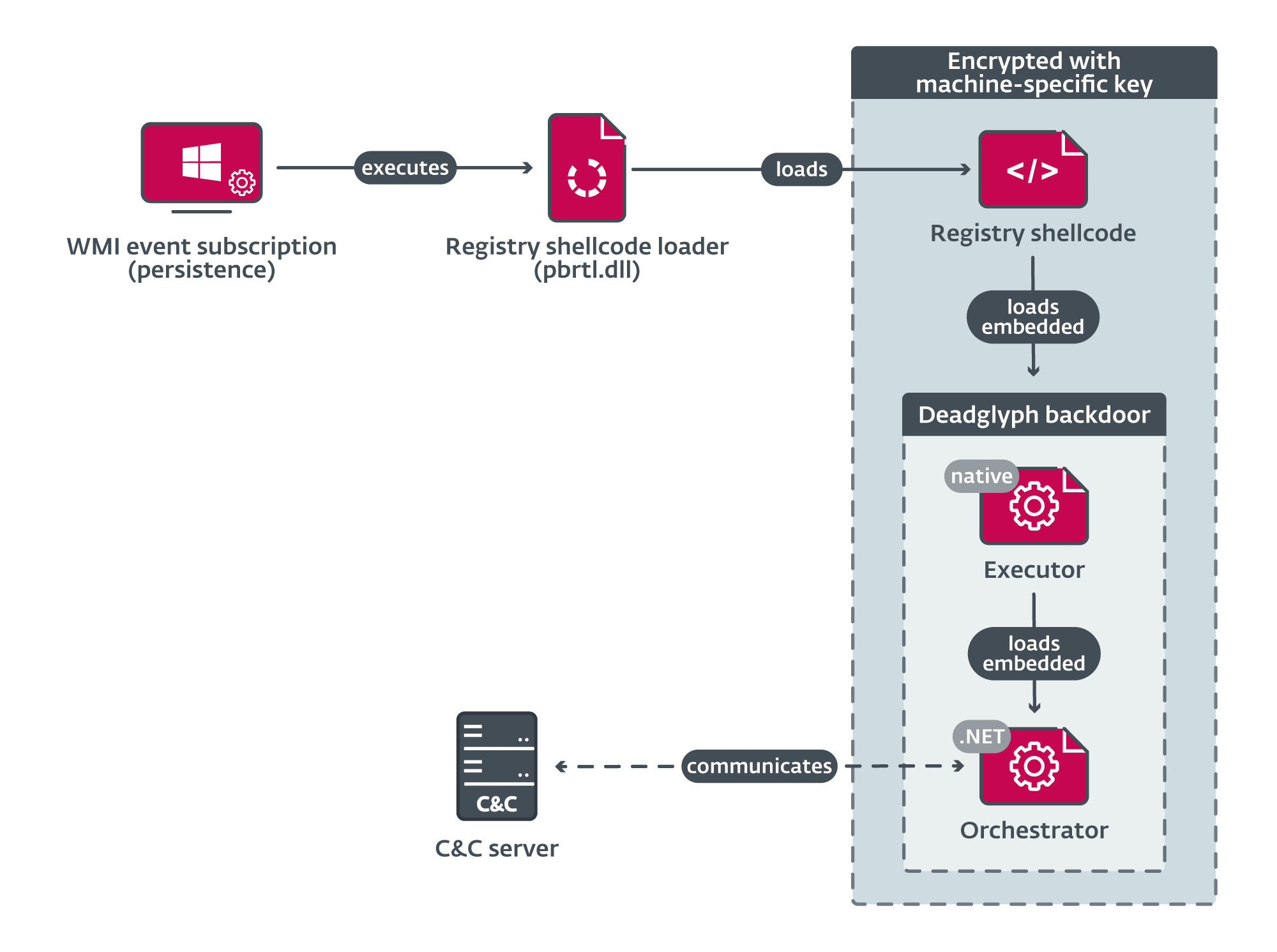
The Deadglyph loading chain components (Image: ESET)
The initial loader of the Deadglyph backdoor is the only component that resides as a disk file in the victim machine. It is a small DLL, with only one exported function which operates as a registry shellcode loader. It first RC4-decrypts the path to the encrypted shellcode in the registry, then derives a unique RC4 key from the system UUID, using it to decrypt the shellcode it retrieves from the registry and then executes it. Deriving the key from the system UUID prevents successful decryption and execution on a different computer.
Interestingly, the VERSIONINFO resource of this and other components mimics the name 'Microsoft Corporation', using both Greek and Cyrillic Unicode characters - a form of homoglyph attack. It is this feature, along with the presence of hexadecimal ID's like 0xDEADB001 and 0xDEADB101 in its configuration. that gave the backdoor its name.
The registry shellcode contains an minimally-encrypted payload and the corresponding decryption code. Once decrypted, the body consists of a PE (Portable Executable) loader and a PE file; the latter is the native part of the backdoor, termed the Executor. This loads and decrypts its AES-encrypted configuration (keys and other settings, which are subsequently stored in the registry), then initializes the .NET runtime and loads the embedded .NET part of the backdoor, termed the Orchestrator, which is in the .rsrc section of the Executor. Once the Orchestrator is running, the Executor provides a library of native code functions which it will use.
The Orchestrator is the main component of Deadglyph; it first loads its configuration, then establishes a connection to a command and control server, using a number of threads to perform various tasks, including checking the environment for likely security-related processes - if any of these is detected, the backdoor will either pause C2 communications while the suspicious process is present, or terminate and uninstall itself. The other threads are used for periodic communication with the C2 server and to execute the received commands.
Two modules are used for C2 communications - a Network module and a Timer module. Again, the architecture is cautious to evade analysis: if it cannot establish a connection to the C2 server for a preset interval, then the backdoor terminates and uninstalls itself. The Network module communicates with the C2 server using a custom binary protocol with encrypted content is used underneath TLS/SSL, and has the ability to discover proxy configuration in the event it is on a network protected by a proxy web server.
The commands from the C2 server take the form of three types of tasks: Orchestrator tasks, which are used for configuring the backdoor; Executor tasks, which execute additional modules; and Upload tasks, which send the output of commands and errors to the C2 server. Interestingly, the backdoor does not implement the code for most of its commands - the traditional design. Rather, each command is delivered in the form of an additional module in PE format or as shellcode. This means that Deadglyph is almost infinitely extensible, and also that its capabilities cannot be fully analyzed unless and until all command/modules are captured.
However, the ESET researchers were able to capture three modules: a process creator, which provides remote command execution; an information collector, which profiles the system via Windows Management Instrumentation API queries; and a file reader, which can read a file and return it to the Orchestrator for subsequent uploading - this module was observed retrieving a victim's MS Outlook data file.
The exact exploitation mechanism by which Deadglyph infects a target system is not known; however, while investigating it, the ESET researchers discovered a .CPL (Control Panel extension) file which had been uploaded to VirusTotal from Qatar, and which appeared to be related to Deadglyph.
The ESET report provides IOC's, along with a mapping to MITRE ATT&CK techniques.
ESET Research, Stealth Falcon preying over Middle Eastern skies with Deadglyph, blog post, 22 September 2023. Available online at https://www.welivesecurity.com/en/eset-research/stealth-falcon-preying-middle-eastern-skies-deadglyph/.
Upcoming Courses
- SE221 CISSP Fast Track Review, Virtual/Online, 13 - 17 November 2023
- SE221 CISSP Fast Track Review, Sydney, 4 - 8 December 2023
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
$A10 million Turns Up Unexpectedly - What Would You Do?
When $A10.47 million was suddently deposited into her account by a cryptocurrency exchange, the answer was obvious to a hard-working immigrant - invest in real estate, vehicles, art and furniture. After years of hard work, life was good - until the mistake was realized, her bank set out to recover the funds, ands she was arrested attempting to flee the country.
The case, which has implications for the operation of systems to process failed transactions, started when the partner of a Malaysian immigrant to Australia, Thevamanogari Manivel, tried to open an account with crypto exchange Crypto.com, making an initial transfer of funds from Manivel's bank account. The exchange rejected the payment, however, because the name on the bank account did not match the name on the crypto account. So far, so good.
But a Bulgaria-based worker who processed the refund did so by directly entering the data into an Excel spreadsheet - and entered the account number into the refund amount column. Instead of refunding $A100, the bank transferred over $A10 million into Manivel's account. When her partner discovered this the following day, he told her to transfer the funds into a joint account at a different bank, telling her he had won a competition run by Crypto.com.
It was over a year later that Crypto.com detected the error and tried to recover the funds from the bank, but when the bank contacted her, Manivel assumed this was likely a scam - and on calling the bank, was told that it probably was. To safeguard the remaining money, she and her partner transferred the remaining $A4 million to Malaysia. She was arrested while attempting to board a flight to Malaysia in March 2022, after which she spent 209 days in custody.
Prior to the windfall, Manivel had been a struggling immigrant, taking low-paid jobs while studying aged care and pathology at night school and saving enough money to bring her children to Australia. On pleading guilty to a charge of recklessly dealing with the proceeds of crime, she was sentenced to an 18 month community corrections order with six months' intensive compliance and unpaid community work in addition to time already spent in custody. The sentencing judge remarked that the money had been recovered and no sinister intent was proven - up to the point where her bank had informed her of the error.
Manivel seems to have returned to the straight and narrow, now studying for a B.Sc., but now her visa could be rescinded. Her partner, Jatinder Singh, was charged with theft and will face a plea hearing on 23 October.
All this started with a simple data entry error in a spreadsheet; such manual processes are sometimes used to deal with unusual transaction problems, but this illustrates the need for appropriate safeguards such as separate review to meet segregation of duties requirements, and the implementation of input validation - something easily implemented, even in spreadsheets. Crypto.com says that it has updated its refund and withdrawal systems after this incident.
Taylor, Josh, A crypto firm sent a disability worker $10m by mistake. Months later she was arrested at an Australian airport, The Guardian, 24 September 2023. Available online at https://www.theguardian.com/australia-news/2023/sep/24/a-crypto-firm-sent-a-disability-worker-10m-by-mistake-months-later-she-was-arrested-at-an-australian-airport.
Upcoming Courses
- SE221 CISSP Fast Track Review, Virtual/Online, 13 - 17 November 2023
- SE221 CISSP Fast Track Review, Sydney, 4 - 8 December 2023
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
The Worst Privacy-Invading Devices? Cars
The integration of embedded processors into cars began with simple devices for engine control, some diagnostics and the very basic 'trip computer' to help drivers estimate trip times. But as silicon has become both more powerful and less expensive than mechanical devices for displaying information on the dashboard, cars have become more electronic than mechanical. Add ubiquitous connectivity, smartphone integration and GPS for navigation, and your car is probably the smartest device you own. All this culminates in battery electric vehicles, of course, in which the car's intelligence is completely integrated with the drive train and other basic functionality.
So as you drive around, the car's systems know not just how fast you are going, but where you are, where you are going, whether you will run out of fuel before you get there, the driving conditions, the streaming service music you are playing and a lot more.
Now researchers with the Mozilla Foundation have researched the data-gathering capabilities of 25 different car brands, along with what the manufacturers do with that data and the terms of their privacy policies (I say 'manufacturers' but if the recent moves of BMW and others are any guide, we may soon have to think of them as 'service providers'. Think transportation-as-a-service). The results are startling:
"All 25 car brands we researched earned our *Privacy Not Included warning label -- making cars the official worst category of products for privacy that we have ever reviewed."
Every car brand collects more personal data than necessary, using that information for purposes other operating the vehicle and maintaining a customer relationship (a performance much worse than even mental health smartphone apps, only 63% of which earned the "*Privacy Not Included" label). Furthermore, most of them go beyond using the data internally for marketing and related purposes, and share (84%) or even sell (76%) personal information. 56% say they can share your information with governments or law enforcement in response to a request - not a court order or warrant, but a request.
Only two of the brands say that drivers have the right to have their personal data deleted - presumably to comply with the EU General Data Protection Regulation.
Another concern is a lack of assurance that the companies comply with good cybersecurity practices - for example, the researchers could not find out whether any of the cars encrypt the personal information they store. Email requests for clarification were mostly ignored, but a review of public breach disclosures over the last three years showed that 17 of the 25 car brands have a bad track record for leaks, hacks and breaches.
The companies' privacy policies make for concerning reading. Among the data categories collected by Nissan, according to their policy, is your "sexual activity". Kia can also collect information about your "sex life", apparently. In fact, six of the companies state that they can collect your genetic information or characteristics. The companies may also claim that their policies also apply to passengers and it is the responsbility of the driver to inform them of this, ignoring the fact that just reading the policy to your passengers could take hours!
While most of the companies claim to comply with the Alliance for Automative Innovation's Consumer Protection Principles, but it seems that none of them actually comply in practice. And you really have little choice, since all the brands are similar and those that do allow you to opt out will dramatically reduce the smart functionality of the vehicle.
In short, you may wish to reconsider buying that new high-end EV.
Caltrider, Jen, Misha Rykov and Zoë MacDonald, It’s Official: Cars Are the Worst Product Category We Have Ever Reviewed for Privacy, Mozilla *Privacy Not Included review, 6 September 2023. Available online at https://foundation.mozilla.org/en/privacynotincluded/articles/its-official-cars-are-the-worst-product-category-we-have-ever-reviewed-for-privacy/.
Upcoming Courses
- SE221 CISSP Fast Track Review, Virtual/Online, 13 - 17 November 2023
- SE221 CISSP Fast Track Review, Sydney, 4 - 8 December 2023
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
Cloud Cryptojacking Operation Uses Multiple AWS Services
A new cloud-native cryptojacking operation attributed to Indonesian hackers could cost victims massive amounts as it unexpectedly consumes cloud services before they realize what is occurring. The operation, dubbed AMBERSQUID by the Sysdig researchers who uncovered it, makes use of a number of less-commonly-used AWS services such as the Amplify build and deployment platform, the ECS and Fargate container orchestration service, Codebuild, CloudFormation and EC2 Auto Scaling.
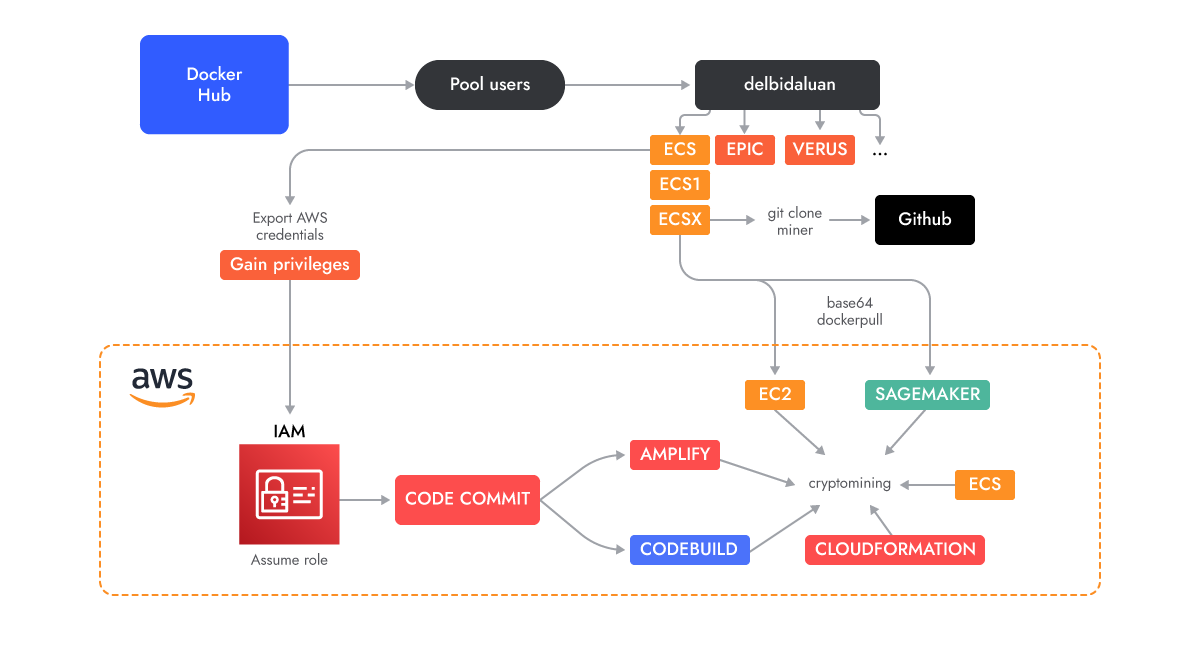
The AMBERSQUID deployment process (Image: Sysdig)
The researchers found AMBERSQUID in an innocuous container image while analysing over 1.7 million Linux images on Docker Hub; static scanning of the image showed no indicators or malicious binaries, and it was only when the image was run that its cryptojacking, using multiple services, was revealed. A number of Docker Hub user accounts are related to this operation - while some have been abandoned, others remain active. When launched, the Docker images download a cryptominer binary from a GitHub account and then run it.
The exploitation begins with execution of a script called amplify-role.sh, which creates the "AWSCodeCommit-Role" role, and then uses it throughout the process in order to add full access permissions for the various AWS services. The scripts that follow use the various services to first, create a private repository for the CodeCommit service in every region, which is then used as a source for the other services, then create five Amplify web apps, running the miner as it does does so, then uses ECS and Fargate to start each container, using 2 virtual CPU's and 4 GB of memory, A similar process is used to run the miner in Codebuild, CloudFormation., EC2 AutoScaling and the Sagemaker deployment tool for machine learning models,
The resulting resource utilization can be very expensive for the victim - assuming a relatively modest number of regions and instance scaling, it would be $US2,244 per day, but it could easily be much more.
While AMBERSQUID targets AWS, the same techniques could be used to exploit similar deployment services offered by other cloud service providers. Defenders tend to focus on the possibility of cryptominers being installed on conventional IaaS instances in EC2, Google Compute Engine, etc. but this case demonstrates that other services need to be secured and monitored as well, with quotas and alerts set even for services not currently in use.
Brucato, Alessandro, AWS’s Hidden Threat: AMBERSQUID Cloud-Native Cryptojacking Operation, blog post, 18 September 2023. Available online at https://sysdig.com/blog/ambersquid/.
Latest Aussie Ransomware Victim: Pizza Hut
Pizza Hut Australia is the latest company to fall victim to a ransomware attack, disclosing the detection of an incident in early September. Subsequent analysis revealed that an unauthorised third party had accessed the data of 193,000 customers, including names, delivery addresses and instructions, email addresses and contact numbers. No usable credit card data or other financial details were exposed.
The affected customers have been contacted by the company, which has also notified the Australian Cyber Security Centre and the Office of the Australian Information Commissioner.
Rawling, Caitlin, Pizza Hut says nearly two-hundred thousand customers affected by data breach, ABC News, 20 September 2023. Available online at https://www.abc.net.au/news/2023-09-20/pizza-hut-customers-affected-by-cyber-hack/102881804.
Upcoming Courses
- SE221 CISSP Fast Track Review, Virtual/Online, 13 - 17 November 2023
- SE221 CISSP Fast Track Review, Sydney, 4 - 8 December 2023
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
Chinese APT Deploys New Linux Backdoor
Trend Micro researchers have published a research paper on a new and evolving Linux backdoor which they discovered while monitoring the activities of a Chinese government-linked threat actor they track as 'Earth Lusca'. The group has primarily engaged in cyber-espionage against targets in government and education, some religious movements, and pro-democracy and human rights groups in Hong Kong - with a side interest in criminal activities against gambling and cryptocurrency sites, presumably in order to be self-funding.
In June, the researchers discovered an encrypted file on Earth Lusca's delivery server, and after finding the related loader on VirusTotal, they were able to decrypt it to reveal a previously-unknown Linux-targeted backdoor. Analysis of the main execution routine and its strings reveal it to be derived from Trochilus, an open-source Windows backdoor, with a number of functions obviously rewritten to work on Linux. They named this variant 'SprySOCKS' -a reference to the way it combines the rapid operation of Trochilus with a new implementation of the SOCKS multi-protocol proxy protocol.
To date, two versions of SprySOCKS have been found, with two different version numbers. Its interactive shell seems to derive from the Linux version of the Derusbi malware, while its command and control protocol is similar to that of the ReadLeaves remote access trojan for Windows targets which is reportedly also derived from Trochilus. SprySOCKS also has a similar structure, consisting of two components - a loader in an ELF executable named 'mkmon' and an encrypted main payload in a file called libmonitor.so.2.
Like the SprySOCKS backdoor itself, the loader was not developed from scrach, but is based on a publicly-available ELF process injector called 'mandibule' (the French word for mandible or lower jaw). The SprySOCKS programmers adapted it by removing the process injection code, replacing it with the code to download and decrypt their backdoor.
SprySOCKS itself makes used of a high-performance network library, developed in China and called HP-Socket, to implement its encrypted binary C2 protocol. The protocol has commands for collecting system information, listing network connections, creating a SOCKS proxy, transferring files, some basic file operations and, mostly importantly, starting an interactive shell.
Earth Lusca is using SprySOCKS to aggresively target the Internet-facing servers of its victims - primarily government foreign affairs offices, tech companies and telcos in SE Asia, Central Asia and the Balkans. It uses a number of recent vulnerabilities to infect Fortinet and other perimeter devices - presumably to reconnoiter and then establish a SOCKS proxy which can be used to then forward traffic from internal victims using ReadLeaves and similar tools such as web shells and Cobalt Strike for lateral movement.
The Trend Micro report has a full analysis, recommendations for mitigation (primarily proactive patch management) and IOC's.
Chen, Josoph C and Jaromir Horejsi, Earth Lusca Employs New Linux Backdoor, Uses Cobalt Strike for Lateral Movement, research paper, 18 September 2023. Available online at https://www.trendmicro.com/en_us/research/23/i/earth-lusca-employs-new-linux-backdoor.html.
Upcoming Courses
- SE221 CISSP Fast Track Review, Virtual/Online, 13 - 17 November 2023
- SE221 CISSP Fast Track Review, Sydney, 4 - 8 December 2023
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
HWL Ebsworth Breach Affects 65 Australian Government Agencies
Back in May, we reported on the ALPHV/BlackCat breach of law firm HWL Ebsworth, which saw approximately 4 TB (estimates vary) of data exfiltrated - a mix of financial data, employee records and client documentation. In June, the ransomware gang posted 1.45 TB of data to the dark web in an attempt to force the lawyers into paying their extortion demand - a move which saw the firm double down and issue legal threats, including a non-publication order in the NSW Supreme Court to prevent dissemination of any of the data.
At the AFR Cyber Summit yesterday, Australian cybersecurity coordinator Air Marshal Darren Goldie revealed that 65 government agencies were affected:
"As of 18 September 2023, a total of 65 Australian government entities have been impacted, as direct clients of the firm through its legal and consulting services. A large number of private sector clients were also affected."
"I stress that these agencies were clients of HWL Ebsworth and did not suffer a cyber incident themselves."
One of the affected agencies was the National Disability Insurance Agency, and Goldie confirmed that some of its clients' PII, likely including health information, was stolen in the attack, since HWL Ebsworth had represented the agency in appeals cases. However, the affected individuals were contacted directly by the firm before this aspect of the breach was revealed this week.
Taylor, Josh, HWL Ebsworth hack: 65 Australian government agencies affected by cyber-attack, The Guardian, 18 September 2023. Available online at https://www.theguardian.com/australia-news/2023/sep/18/hwl-ebsworth-hack-65-australian-government-agencies-affected-by-cyber-attack.
ASIC Tightens Cybersecurity Governance Demands on Directors
Also speaking at the AFR Summit were the chairman of the Australian Securities and Investment Commission, Joe Longo, and the chairman of the Commonwealth Government's cybersecurity strategy review, Andy Penn.
Penn laid out four key priorities for directors, stating that he hoped government would make these explicit in guidance. Boards should:
- know what data they hold - in other words, have a registry of information assets
- have an inventory of their IT systems
- have a plan to upgrade these systems
- have a response plan to remediate systems and manage fallout in the event of a breach
These are very basic requirements which most large companies can easily meet - the first two from their GRC platforms and risk management processes, the third from proactive patch management and asset lifecycle management, and the last from their incident response and management policies - and the key requirement is to provide this information to boards and provide assurance of their management.
Longo warned that ASIC would take legal action against directors of hacked companies if they were held to to have taken insufficient steps to protect information and critical infrastructure. However, a survey conducted by law firm Herbert Smith Freehills, of 122 senior Australian lawyers, found that two-thirds of respondents said their boards had not given management formal guidance on how to handle cyber extortion demands. And according to ASIC's unreleased research, half of their respondents said they had not identified business critical systems.
Attendees also focused on the tension between demands by regulators to share incident and breach information promptly - both with the regulator and others in the same industry - and the need to withhold information which could be used against them in regulatory action or class actions.
There is also an obvious need for directors to better understand cybersecurity - fortunately, we are already doing our part here, with short courses on cybersecurity governance and information risk management for boards and senior managers.
Bonyhady, Nick, The tougher regime for cyber threats that directors must heed, Australian Financial Review, 18 September 2023. Available online at https://www.afr.com/technology/four-steps-businesses-must-take-to-avoid-cyber-lawsuits-penn-20230918-p5e5j2.
Microsoft's AI Research Team Exposes 38 TB of Private Data
In an embarrassing blunder, Microsoft's AI research team accidentally exposed 38 terabytes of private data, including disk backups of two employees' workstations - revealing secrets, private keys, passwords and over 30,000 internal Teams messages. The blunder occurred while publishing a bucket of open-source training data on GitHub, using an Azure feature called SAS tokens, which allows shareing from Azure Storage accounts. While the access level can be limited to specific files only, in this case the link was configured to share the entire storage account, including that 38TB of private files.
The leak was discovered by researchers at Wiz Research, who work on accidental exposure of cloud-hosted data, scanning the Internet for misconfigured storage containers. Their report provides a full analysis, including the risks of using SAS tokens, and a number of suggested mitigations.
Ben-Sasson, Hillai and Ronny Greenberg, 38TB of data accidentally exposed by Microsoft AI researchers, blog post, 18 September 2023. Available online at https://www.wiz.io/blog/38-terabytes-of-private-data-accidentally-exposed-by-microsoft-ai-researchers.
Upcoming Courses
- SE221 CISSP Fast Track Review, Virtual/Online, 13 - 17 November 2023
- SE221 CISSP Fast Track Review, Sydney, 4 - 8 December 2023
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
ISS Leaking - But Not in the Way You Think
Via New Scientist comes the strange story of a leak on the International Space Station (ISS). In this case, there's no hiss of escaping air - it's data that is leaking.
Pseudonymous security researcher Gi7w0rm, in hot pursuit of a space-related vulnerability in a "sensitive" government system, accidentally discovered an open telemetry feed which provides a continuous stream of all kinds of interesting, and some not-so-interesting, information about the status of various systems on the ISS: battery charger assemblies, antenna alignments, and, most curiously, the status of the unit that processes urine into potable water:

The feed is viewable at https://iss-mimic.github.io/Mimic/. So now you can see whenever an astronaut takes a leak.
NASA has not commented at this time, but a Boeing engineer has stated that the feed is an obsolete component of a now-defunct web site called ISSLive. While the project was abandoned, this stream lives on, providing a small subset of the thousands of telemetry channels used by the ISS.
The lesson for us: this is a classic example of Improper Web API Asset Management: a failure to retire an old version of an API that is no longer in use. Fortunately, in this case, no particularly sensitive information is exposed.
Sparkes, Matthew, Data leak means anyone can see when astronauts urinate on the ISS, New Scientist, 15 September 2023. Available online at https://www.newscientist.com/article/2392360-data-leak-means-anyone-can-see-when-astronauts-urinate-on-the-iss/.
CoinEx Crypto Theft Down to Lazarus Group, Say Analysts
Being the subject of extremely tight financial sanctions, North Korea has long resorted to cybercrime as a source of hard currencies, and the growth of cryptocurrencies has only accelerated this process. In a period of just over three months, the most prolific North Korean APT, Lazarus Group, has been identified as behind theft of almost $US240 million of cryptocurrency from Atomic Wallet ($US100 million) CoinsPaid ($US37.3 million), Alphapo ($US60 million), and Stake.com ($US41 million).
Despite the widespread assumption that cryptocurrency transactions are anonymous, blockchain analysis performed by several analysis firms can trace the flow of funds through wallets and mixers, making it possible to link different breaches to the same actors and attribute them with some confidence. Now, reports from two companies attribute the latest breach, at CoinEx on 12 September, to Lazarus Group with a high degree of confidence. At this stage, CoinEx has not identified all the affected wallets, but the total value of the theft is estimated to be around $US54 million.
In these thefts, Lazarus Group has employed a strategy of switching funds between blockchains as well as converting stolen funds into Ethereum before transferring them onwards. However, this is not enough to stop analysts from tracing the funds.
Certik, Lazarus Group's Web3 Rampage, blog post, 13 September 2023. Available online at https://www.certik.com/resources/blog/216tegKHtRmx5pOI3UgYCX-lazarus-groups-web3-rampage.
Elliptic Research, How the Lazarus Group is stepping up crypto hacks and changing its tactics, blog post, 15 September 2023. Available online at https://www.elliptic.co/blog/how-the-lazarus-group-is-stepping-up-crypto-hacks-and-changing-its-tactics.
Dymocks Customer Data Stolen From External Supplier
Last week, we revealed the theft of the personal information of Dymocks' customers by a ransomware operator, and a threat to publish this data on the dark web.
The company has now confirmed that customer records have been placed on the dark web, but states that the breach was achieved by the compromise of a business partner's systems:
"Although our investigations are ongoing, we do believe that one of our third-party partner’s systems were subject to unauthorised access. Whilst we continue to keep all avenues open, we are working with the identified partner to focus on understanding if and how their systems were accessed despite their security measures."
Approximately 1.24 million customer contact records have been released. Dymocks also states that there is no evidence of any unauthorized access to its own systems. This is just the latest in a long series of breaches in which smaller suppliers expose the data of their larger clients and partners.
Dymocks, Frequently Asked Questions (FAQs) – Dymocks Data Incident, customer notice, 15 September 2023. Available online at https://www.dymocks.com.au/customer-notices.
Upcoming Courses
- SE221 CISSP Fast Track Review, Virtual/Online, 13 - 17 November 2023
- SE221 CISSP Fast Track Review, Sydney, 4 - 8 December 2023
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
Vuln Discovered in Windows 11 Desktop Themes Code
One of the vulnerabilities fixed a few days ago in this month's Microsoft Patchday was CVE-2023-38146, a remote code execution vuln in the code which handles theme files for the Windows desktop background. Microsoft learned of the vuln via a bug bounty submission from security researcher Gabe Kirkpatrick, and judged CVE-2023-38146 important, with a CVSS 3.x score of 8.8 (high). Kirkpatrick dubbed the vulnerability 'Themebleed'.
[VisualStyles]
Path=%SystemRoot%\resources\Themes\Aero\Aero.msstyles
Windows desktop theme files (.theme files) are actually .ini text files, with a number of stanzas. Among these is a [VisualStyles] stanza, as shown above, which can load .msstyles files - but these are not text files; rather, they are DLL files which contain resources such as icons for the theme, and generally do not, and should not, contain code.
The .msstyles files get loaded by a function called LoadThemeLibrary() which, among things, checks the version number of the theme - normally stored in a resource called PACKTHEM_VERSION. However, if this is 999, it then calls a ReviseVersionIfNecessary() function, which attempts to load and call a VerifyThemeVersion() function from a related DLL file which is supplied as part of theme. (Can you see where this is going? 😁)
Now, any programmer with at least some concern for security will want to ensure this DLL is not malicious, and so the ReviseVersionIfNecessary() function checks that the file has a valid signature. But the function has a flaw: it opens the file to check its signature and then closes it before loading it as a DLL in order to call VerifyThemeVersion().
Now, boys and girls - can you spell Time of Check / Time of Use vulnerability? I knew you could! 🙂
Kirkpatrick obviously could, too - and set about developing a proof of concept exploit, which delivers the attack over the LAN via the SMB protocol. The PoC also adds an extra step - in order to avoid a pop-up UAC warning caused by the Mark of the Web on the .themes file, it is packed into a .themepack file.
As mentioned, Microsoft released their fix for this particular exploit in this week's Windows update - however, the fix works by simply removing the check for a 999 value in the theme version resource, and the TOC/TOU vulnerability in VerifyThemeVersion() still remains, so related exploits could emerge.
Kirkpatrick, Gabe, CVE-2023-38146: Arbitrary Code Execution via Windows Themes, blog post, 13 September 2023. Available online at https://exploits.forsale/themebleed/.
Microsoft Uncovers Vulnerabilities in Linux Terminal Handling Code
One of the common assumptions in the open source community is that the older software packages which are core to that ecosystem must have had all the bugs and vulnerabilities distilled out of them by constant review and usage over the years. We treat many of the older products of the BSD and GNU projects that way, for example - after all, they date back to a simpler time, and the biggest enemy of security is complexity, so these 'simple' programs can't be a problem, right?
Wrong, as it turns out. It's an invalid assumption for a number of reasons - not least that many of these programs are not at all simple, as demonstrated by the case of the ncurses package, the 'new' version of the even older curses library for dumb terminal cursor management on UNIX/Linux systems. Many programs use ncurses - almost any text-mode full-screen program such as your favourite editor, be it vi, nano or emacs, various system admin tools and even the top utility for monitoring processes.
With the growth of minicomputers from the 1960's onwards, a variety of manufacturers - Televideo is one example that comes easily to mind - flooded the market with increasingly sophisticated serial-interface terminals, each manufacturer using its own 'command language' of escape sequences and control characters for functionality like cursor positioning, erasing sections of lines, entire lines or blocks of the screen area and other functionaity for use by programs. Things got even more complicated with different models having different screen sizes, windowing or screen-switching capabilities, extended character sets and primitive, box-drawing graphics capabilities.
In order to map the functionalities required by programs, such as screen-clearing and cursor positioning, to the different possibilities and escape sequences, the curses library was developed. This could be customised through termcap databases, which define the capabilities of different terminals and the escape sequences and control characters that drive them. Eventually, curses was replaced by the Free Software Foundation's ncurses package, which is even more capable.
Both curses and ncurses are configured by environment variables, especially TERMINFO, which points to any non-default directory where a termcap database can be found. If TERMINFO is undefined, then ncurses will look in the user's home directory for a .terminfo directory - but the home directory itself is defined by an environment variable: HOME. This opens up the possibility of introducing malicious termcap files and using environment variable poisoning to get them loaded.
What's worse is that terminfo is far from simple; its capabilities include a primitive stack-oriented programming language, rather like that found in Hewlett-Packard scientific programmable calculators, not to mention FORTH and the Postscript page description language. This little language might not be Turing-complete, but to a hacker (whether good or bad) the availability of a scripting or programming language opens up all kinds of delicious possibilities. What's more, the word stack is positively ripe with possibilities, conjuring up visions of buffer overflows and stack smashing attacks.
And sure enough, when some security researchers at Microsoft turned their attention to ncurses, using code review and fuzzing, that's exactly what they found: a number of exploitable memory mis-management vulnerabilities. The details are moderately technical and too detailed to go into here; suffice to say that they are enough to demolish the idea that 'mature' code is low-risk. Consider the fact that the top command on macOS is a setUID executable (unlike on Linux) and you can see that a buffer overflow in ncurses could be a useful path to a privilege escalation exploit.
The Microsoft researchers obviously disclosed what they had found, and the current maintainer of ncurses, Thomas E. Dickey, worked up fixes back in April, making this particular set of vulns of historical interest only. But perhaps this will alert black hats to revisit some old code, working up some new exploits. And in the meantime, the Microsoft blog piece is a fascinating read.
Microsoft Threat Intelligence, Uncursing the ncurses: Memory corruption vulnerabilities found in library, blog post, 14 September 2023. Available online at https://www.microsoft.com/en-us/security/blog/2023/09/14/uncursing-the-ncurses-memory-corruption-vulnerabilities-found-in-library/.
Upcoming Courses
- SE221 CISSP Fast Track Review, Virtual/Online, 13 - 17 November 2023
- SE221 CISSP Fast Track Review, Sydney, 4 - 8 December 2023
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
Kubernetes Admins Urged to Patch Against Remote Command Execution Vuln
Administrators of Kubernetes clusters with Windows endpoints are being urged to update, following the discovery by Akamai security researcher Tomer Peled of a high-severity vulnerability which allows remote command execution. Analysing the vulnerability revealed the underlying root causes: an insecure function call and the lack of user input sanitization. And working forward again from there revealed two more vulnerabilities with the same root causes.
The vulnerabilities are:
All three have a CVSS score of 8.8, and fixes for them were released on 23 August, but they do not yet appear in the National Vulnerability Database.
CVE-2023-3676 allows remote command execution, and the way it does this is instructive. Kubernetes allows directories to be shared between a created pod and the underlying host, and this is done by adding volume parameters in the pod's YAML configuration file. This file is parsed by the kubelet service, and it validates the YAML subPath parameter by calling a function called isLinkPath(), which is where the vulnerability can be exploited:
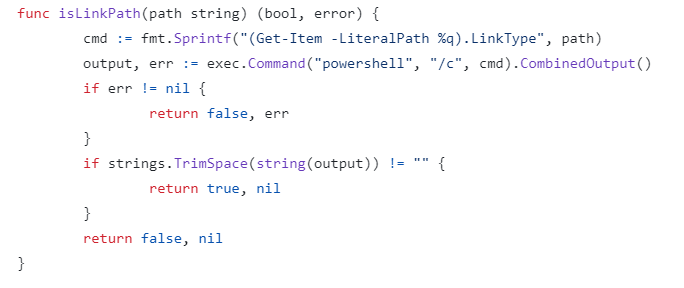
In order to validate the existence of a mount point path, this function directly inserts the path parameter, which is picked up from the YAML file, into a Windows PowerShell command, and then calls exec.Command() to execute it. The presence of exec.Command() is a massive red flag: any code that calls the isLinkPath() function would need to ruthlessly sanitize the path string passed to it. In particular, much like POSIX shells (e.g. bash), PowerShell allows parameter expansion using $( ) syntax. Any command - e.g. Start-process cmd - can be inserted into the $( ), and by placing this into the subPath parameter of the YAML file, it will get passed into the isLinkPath() function, which will assign the cmd variable the value
(Get-Item -LiteralPath $(Start-process cmd).LinkType)
then get PowerShell to execute it - which will first run StartProcess cmd, starting a command prompt, and then try to run Get-Item -LiteralPath on the result. This will probably fail, but for the attacker that's not a problem - they've got the shell they wanted.
Peled's write-up provides a proof-of-concept example, as well as suggested mitigations, the primary one being to apply a patch that fixes the vulnerability, by passing the path parameter to PowerShell as an environment variable, thereby avoiding the parameter expansion. Crude, but effective.
Peled, Tomer, Can't Be Contained: Finding a Command Injection Vulnerability in Kubernetes, blog post, 13 September 2023. Available online at https://www.akamai.com/blog/security-research/kubernetes-critical-vulnerability-command-injection.
CISA Adds Five Vulns to Known Exploited Vulnerabilites Catalog
CISA has added five vulnerabilities to its Known Exploited Vulnerabilities Catalog over the last couple of days.
- CVE-2023-36761 - a Microsoft Word Information Disclosure Vulnerability
- CVE-2023-36802 - a Microsoft Streaming Service Proxy Elevation of Privilege Vulnerability
- CVE-2023-35674 - Android Framework Privilege Escalation Vulnerability
- CVE-2023-20269 - Cisco Adaptive Security Appliance and Firepower Threat Defense Unauthorized Access Vulnerability
- CVE-2023-4863 - Google Chrome Heap-Based Buffer Overflow Vulnerability
In other news, yesterday was the monthly Windows Patchday; September's security updates consists of 59 vulnerabilities.
CISA, CISA Adds Two Known Vulnerabilities to Catalog, alert, 12 September 2023. Available online at https://www.cisa.gov/news-events/alerts/2023/09/12/cisa-adds-two-known-vulnerabilities-catalog.
CISA, CISA Adds Three Known Vulnerabilities to Catalog, alert, 13 September 2023. Available online at https://www.cisa.gov/news-events/alerts/2023/09/13/cisa-adds-three-known-vulnerabilities-catalog.
Microsoft Security Resource Center, September 2023 Security Updates, release note, 12 September 2023. Available online at https://msrc.microsoft.com/update-guide/releaseNote/2023-Sep.
US Agencies Warn of Deepfake Threats
As machine learning and AI continues to rapidly evolve, the US National Security Agency, FBI and CISA have released an information sheet on the problem of deepfaking - the use of synthetic media by threat actors. These AI-generated images, audio and video are used for a variety of tactics, ranging from information operations to spread false information to phishing and whaling attacks.
The 18-page report delves into the challenges posed by deepfakes, the impact deepfaking can have on organizations, and recommendations for mitigating attacks which use them.
CISA, NSA, FBI, and CISA Release Cybersecurity Information Sheet on Deepfake Threats, cybersecurity advisory, 12 September 2023. Available online at https://www.cisa.gov/news-events/alerts/2023/09/12/nsa-fbi-and-cisa-release-cybersecurity-information-sheet-deepfake-threats.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.