Les Bell and Associates Pty Ltd
Site blog
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
Cloud Cryptojacking Operation Uses Multiple AWS Services
A new cloud-native cryptojacking operation attributed to Indonesian hackers could cost victims massive amounts as it unexpectedly consumes cloud services before they realize what is occurring. The operation, dubbed AMBERSQUID by the Sysdig researchers who uncovered it, makes use of a number of less-commonly-used AWS services such as the Amplify build and deployment platform, the ECS and Fargate container orchestration service, Codebuild, CloudFormation and EC2 Auto Scaling.
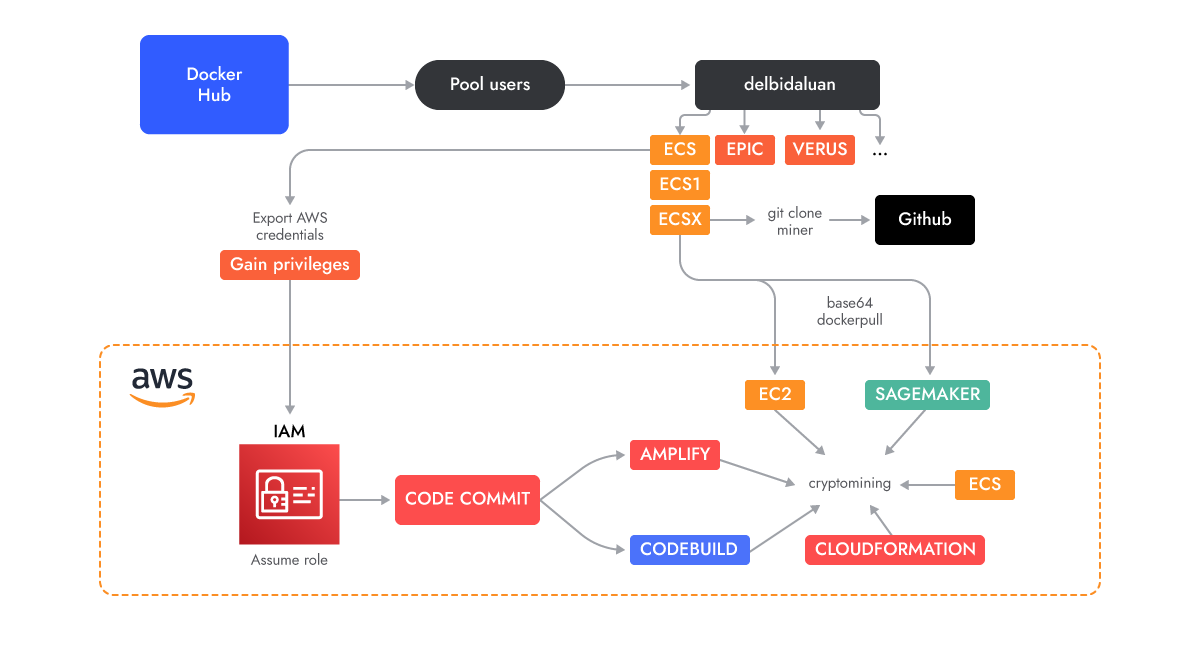
The AMBERSQUID deployment process (Image: Sysdig)
The researchers found AMBERSQUID in an innocuous container image while analysing over 1.7 million Linux images on Docker Hub; static scanning of the image showed no indicators or malicious binaries, and it was only when the image was run that its cryptojacking, using multiple services, was revealed. A number of Docker Hub user accounts are related to this operation - while some have been abandoned, others remain active. When launched, the Docker images download a cryptominer binary from a GitHub account and then run it.
The exploitation begins with execution of a script called amplify-role.sh, which creates the "AWSCodeCommit-Role" role, and then uses it throughout the process in order to add full access permissions for the various AWS services. The scripts that follow use the various services to first, create a private repository for the CodeCommit service in every region, which is then used as a source for the other services, then create five Amplify web apps, running the miner as it does does so, then uses ECS and Fargate to start each container, using 2 virtual CPU's and 4 GB of memory, A similar process is used to run the miner in Codebuild, CloudFormation., EC2 AutoScaling and the Sagemaker deployment tool for machine learning models,
The resulting resource utilization can be very expensive for the victim - assuming a relatively modest number of regions and instance scaling, it would be $US2,244 per day, but it could easily be much more.
While AMBERSQUID targets AWS, the same techniques could be used to exploit similar deployment services offered by other cloud service providers. Defenders tend to focus on the possibility of cryptominers being installed on conventional IaaS instances in EC2, Google Compute Engine, etc. but this case demonstrates that other services need to be secured and monitored as well, with quotas and alerts set even for services not currently in use.
Brucato, Alessandro, AWS’s Hidden Threat: AMBERSQUID Cloud-Native Cryptojacking Operation, blog post, 18 September 2023. Available online at https://sysdig.com/blog/ambersquid/.
Latest Aussie Ransomware Victim: Pizza Hut
Pizza Hut Australia is the latest company to fall victim to a ransomware attack, disclosing the detection of an incident in early September. Subsequent analysis revealed that an unauthorised third party had accessed the data of 193,000 customers, including names, delivery addresses and instructions, email addresses and contact numbers. No usable credit card data or other financial details were exposed.
The affected customers have been contacted by the company, which has also notified the Australian Cyber Security Centre and the Office of the Australian Information Commissioner.
Rawling, Caitlin, Pizza Hut says nearly two-hundred thousand customers affected by data breach, ABC News, 20 September 2023. Available online at https://www.abc.net.au/news/2023-09-20/pizza-hut-customers-affected-by-cyber-hack/102881804.
Upcoming Courses
- SE221 CISSP Fast Track Review, Virtual/Online, 13 - 17 November 2023
- SE221 CISSP Fast Track Review, Sydney, 4 - 8 December 2023
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
Chinese APT Deploys New Linux Backdoor
Trend Micro researchers have published a research paper on a new and evolving Linux backdoor which they discovered while monitoring the activities of a Chinese government-linked threat actor they track as 'Earth Lusca'. The group has primarily engaged in cyber-espionage against targets in government and education, some religious movements, and pro-democracy and human rights groups in Hong Kong - with a side interest in criminal activities against gambling and cryptocurrency sites, presumably in order to be self-funding.
In June, the researchers discovered an encrypted file on Earth Lusca's delivery server, and after finding the related loader on VirusTotal, they were able to decrypt it to reveal a previously-unknown Linux-targeted backdoor. Analysis of the main execution routine and its strings reveal it to be derived from Trochilus, an open-source Windows backdoor, with a number of functions obviously rewritten to work on Linux. They named this variant 'SprySOCKS' -a reference to the way it combines the rapid operation of Trochilus with a new implementation of the SOCKS multi-protocol proxy protocol.
To date, two versions of SprySOCKS have been found, with two different version numbers. Its interactive shell seems to derive from the Linux version of the Derusbi malware, while its command and control protocol is similar to that of the ReadLeaves remote access trojan for Windows targets which is reportedly also derived from Trochilus. SprySOCKS also has a similar structure, consisting of two components - a loader in an ELF executable named 'mkmon' and an encrypted main payload in a file called libmonitor.so.2.
Like the SprySOCKS backdoor itself, the loader was not developed from scrach, but is based on a publicly-available ELF process injector called 'mandibule' (the French word for mandible or lower jaw). The SprySOCKS programmers adapted it by removing the process injection code, replacing it with the code to download and decrypt their backdoor.
SprySOCKS itself makes used of a high-performance network library, developed in China and called HP-Socket, to implement its encrypted binary C2 protocol. The protocol has commands for collecting system information, listing network connections, creating a SOCKS proxy, transferring files, some basic file operations and, mostly importantly, starting an interactive shell.
Earth Lusca is using SprySOCKS to aggresively target the Internet-facing servers of its victims - primarily government foreign affairs offices, tech companies and telcos in SE Asia, Central Asia and the Balkans. It uses a number of recent vulnerabilities to infect Fortinet and other perimeter devices - presumably to reconnoiter and then establish a SOCKS proxy which can be used to then forward traffic from internal victims using ReadLeaves and similar tools such as web shells and Cobalt Strike for lateral movement.
The Trend Micro report has a full analysis, recommendations for mitigation (primarily proactive patch management) and IOC's.
Chen, Josoph C and Jaromir Horejsi, Earth Lusca Employs New Linux Backdoor, Uses Cobalt Strike for Lateral Movement, research paper, 18 September 2023. Available online at https://www.trendmicro.com/en_us/research/23/i/earth-lusca-employs-new-linux-backdoor.html.
Upcoming Courses
- SE221 CISSP Fast Track Review, Virtual/Online, 13 - 17 November 2023
- SE221 CISSP Fast Track Review, Sydney, 4 - 8 December 2023
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
HWL Ebsworth Breach Affects 65 Australian Government Agencies
Back in May, we reported on the ALPHV/BlackCat breach of law firm HWL Ebsworth, which saw approximately 4 TB (estimates vary) of data exfiltrated - a mix of financial data, employee records and client documentation. In June, the ransomware gang posted 1.45 TB of data to the dark web in an attempt to force the lawyers into paying their extortion demand - a move which saw the firm double down and issue legal threats, including a non-publication order in the NSW Supreme Court to prevent dissemination of any of the data.
At the AFR Cyber Summit yesterday, Australian cybersecurity coordinator Air Marshal Darren Goldie revealed that 65 government agencies were affected:
"As of 18 September 2023, a total of 65 Australian government entities have been impacted, as direct clients of the firm through its legal and consulting services. A large number of private sector clients were also affected."
"I stress that these agencies were clients of HWL Ebsworth and did not suffer a cyber incident themselves."
One of the affected agencies was the National Disability Insurance Agency, and Goldie confirmed that some of its clients' PII, likely including health information, was stolen in the attack, since HWL Ebsworth had represented the agency in appeals cases. However, the affected individuals were contacted directly by the firm before this aspect of the breach was revealed this week.
Taylor, Josh, HWL Ebsworth hack: 65 Australian government agencies affected by cyber-attack, The Guardian, 18 September 2023. Available online at https://www.theguardian.com/australia-news/2023/sep/18/hwl-ebsworth-hack-65-australian-government-agencies-affected-by-cyber-attack.
ASIC Tightens Cybersecurity Governance Demands on Directors
Also speaking at the AFR Summit were the chairman of the Australian Securities and Investment Commission, Joe Longo, and the chairman of the Commonwealth Government's cybersecurity strategy review, Andy Penn.
Penn laid out four key priorities for directors, stating that he hoped government would make these explicit in guidance. Boards should:
- know what data they hold - in other words, have a registry of information assets
- have an inventory of their IT systems
- have a plan to upgrade these systems
- have a response plan to remediate systems and manage fallout in the event of a breach
These are very basic requirements which most large companies can easily meet - the first two from their GRC platforms and risk management processes, the third from proactive patch management and asset lifecycle management, and the last from their incident response and management policies - and the key requirement is to provide this information to boards and provide assurance of their management.
Longo warned that ASIC would take legal action against directors of hacked companies if they were held to to have taken insufficient steps to protect information and critical infrastructure. However, a survey conducted by law firm Herbert Smith Freehills, of 122 senior Australian lawyers, found that two-thirds of respondents said their boards had not given management formal guidance on how to handle cyber extortion demands. And according to ASIC's unreleased research, half of their respondents said they had not identified business critical systems.
Attendees also focused on the tension between demands by regulators to share incident and breach information promptly - both with the regulator and others in the same industry - and the need to withhold information which could be used against them in regulatory action or class actions.
There is also an obvious need for directors to better understand cybersecurity - fortunately, we are already doing our part here, with short courses on cybersecurity governance and information risk management for boards and senior managers.
Bonyhady, Nick, The tougher regime for cyber threats that directors must heed, Australian Financial Review, 18 September 2023. Available online at https://www.afr.com/technology/four-steps-businesses-must-take-to-avoid-cyber-lawsuits-penn-20230918-p5e5j2.
Microsoft's AI Research Team Exposes 38 TB of Private Data
In an embarrassing blunder, Microsoft's AI research team accidentally exposed 38 terabytes of private data, including disk backups of two employees' workstations - revealing secrets, private keys, passwords and over 30,000 internal Teams messages. The blunder occurred while publishing a bucket of open-source training data on GitHub, using an Azure feature called SAS tokens, which allows shareing from Azure Storage accounts. While the access level can be limited to specific files only, in this case the link was configured to share the entire storage account, including that 38TB of private files.
The leak was discovered by researchers at Wiz Research, who work on accidental exposure of cloud-hosted data, scanning the Internet for misconfigured storage containers. Their report provides a full analysis, including the risks of using SAS tokens, and a number of suggested mitigations.
Ben-Sasson, Hillai and Ronny Greenberg, 38TB of data accidentally exposed by Microsoft AI researchers, blog post, 18 September 2023. Available online at https://www.wiz.io/blog/38-terabytes-of-private-data-accidentally-exposed-by-microsoft-ai-researchers.
Upcoming Courses
- SE221 CISSP Fast Track Review, Virtual/Online, 13 - 17 November 2023
- SE221 CISSP Fast Track Review, Sydney, 4 - 8 December 2023
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
ISS Leaking - But Not in the Way You Think
Via New Scientist comes the strange story of a leak on the International Space Station (ISS). In this case, there's no hiss of escaping air - it's data that is leaking.
Pseudonymous security researcher Gi7w0rm, in hot pursuit of a space-related vulnerability in a "sensitive" government system, accidentally discovered an open telemetry feed which provides a continuous stream of all kinds of interesting, and some not-so-interesting, information about the status of various systems on the ISS: battery charger assemblies, antenna alignments, and, most curiously, the status of the unit that processes urine into potable water:

The feed is viewable at https://iss-mimic.github.io/Mimic/. So now you can see whenever an astronaut takes a leak.
NASA has not commented at this time, but a Boeing engineer has stated that the feed is an obsolete component of a now-defunct web site called ISSLive. While the project was abandoned, this stream lives on, providing a small subset of the thousands of telemetry channels used by the ISS.
The lesson for us: this is a classic example of Improper Web API Asset Management: a failure to retire an old version of an API that is no longer in use. Fortunately, in this case, no particularly sensitive information is exposed.
Sparkes, Matthew, Data leak means anyone can see when astronauts urinate on the ISS, New Scientist, 15 September 2023. Available online at https://www.newscientist.com/article/2392360-data-leak-means-anyone-can-see-when-astronauts-urinate-on-the-iss/.
CoinEx Crypto Theft Down to Lazarus Group, Say Analysts
Being the subject of extremely tight financial sanctions, North Korea has long resorted to cybercrime as a source of hard currencies, and the growth of cryptocurrencies has only accelerated this process. In a period of just over three months, the most prolific North Korean APT, Lazarus Group, has been identified as behind theft of almost $US240 million of cryptocurrency from Atomic Wallet ($US100 million) CoinsPaid ($US37.3 million), Alphapo ($US60 million), and Stake.com ($US41 million).
Despite the widespread assumption that cryptocurrency transactions are anonymous, blockchain analysis performed by several analysis firms can trace the flow of funds through wallets and mixers, making it possible to link different breaches to the same actors and attribute them with some confidence. Now, reports from two companies attribute the latest breach, at CoinEx on 12 September, to Lazarus Group with a high degree of confidence. At this stage, CoinEx has not identified all the affected wallets, but the total value of the theft is estimated to be around $US54 million.
In these thefts, Lazarus Group has employed a strategy of switching funds between blockchains as well as converting stolen funds into Ethereum before transferring them onwards. However, this is not enough to stop analysts from tracing the funds.
Certik, Lazarus Group's Web3 Rampage, blog post, 13 September 2023. Available online at https://www.certik.com/resources/blog/216tegKHtRmx5pOI3UgYCX-lazarus-groups-web3-rampage.
Elliptic Research, How the Lazarus Group is stepping up crypto hacks and changing its tactics, blog post, 15 September 2023. Available online at https://www.elliptic.co/blog/how-the-lazarus-group-is-stepping-up-crypto-hacks-and-changing-its-tactics.
Dymocks Customer Data Stolen From External Supplier
Last week, we revealed the theft of the personal information of Dymocks' customers by a ransomware operator, and a threat to publish this data on the dark web.
The company has now confirmed that customer records have been placed on the dark web, but states that the breach was achieved by the compromise of a business partner's systems:
"Although our investigations are ongoing, we do believe that one of our third-party partner’s systems were subject to unauthorised access. Whilst we continue to keep all avenues open, we are working with the identified partner to focus on understanding if and how their systems were accessed despite their security measures."
Approximately 1.24 million customer contact records have been released. Dymocks also states that there is no evidence of any unauthorized access to its own systems. This is just the latest in a long series of breaches in which smaller suppliers expose the data of their larger clients and partners.
Dymocks, Frequently Asked Questions (FAQs) – Dymocks Data Incident, customer notice, 15 September 2023. Available online at https://www.dymocks.com.au/customer-notices.
Upcoming Courses
- SE221 CISSP Fast Track Review, Virtual/Online, 13 - 17 November 2023
- SE221 CISSP Fast Track Review, Sydney, 4 - 8 December 2023
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
Vuln Discovered in Windows 11 Desktop Themes Code
One of the vulnerabilities fixed a few days ago in this month's Microsoft Patchday was CVE-2023-38146, a remote code execution vuln in the code which handles theme files for the Windows desktop background. Microsoft learned of the vuln via a bug bounty submission from security researcher Gabe Kirkpatrick, and judged CVE-2023-38146 important, with a CVSS 3.x score of 8.8 (high). Kirkpatrick dubbed the vulnerability 'Themebleed'.
[VisualStyles]
Path=%SystemRoot%\resources\Themes\Aero\Aero.msstyles
Windows desktop theme files (.theme files) are actually .ini text files, with a number of stanzas. Among these is a [VisualStyles] stanza, as shown above, which can load .msstyles files - but these are not text files; rather, they are DLL files which contain resources such as icons for the theme, and generally do not, and should not, contain code.
The .msstyles files get loaded by a function called LoadThemeLibrary() which, among things, checks the version number of the theme - normally stored in a resource called PACKTHEM_VERSION. However, if this is 999, it then calls a ReviseVersionIfNecessary() function, which attempts to load and call a VerifyThemeVersion() function from a related DLL file which is supplied as part of theme. (Can you see where this is going? 😁)
Now, any programmer with at least some concern for security will want to ensure this DLL is not malicious, and so the ReviseVersionIfNecessary() function checks that the file has a valid signature. But the function has a flaw: it opens the file to check its signature and then closes it before loading it as a DLL in order to call VerifyThemeVersion().
Now, boys and girls - can you spell Time of Check / Time of Use vulnerability? I knew you could! 🙂
Kirkpatrick obviously could, too - and set about developing a proof of concept exploit, which delivers the attack over the LAN via the SMB protocol. The PoC also adds an extra step - in order to avoid a pop-up UAC warning caused by the Mark of the Web on the .themes file, it is packed into a .themepack file.
As mentioned, Microsoft released their fix for this particular exploit in this week's Windows update - however, the fix works by simply removing the check for a 999 value in the theme version resource, and the TOC/TOU vulnerability in VerifyThemeVersion() still remains, so related exploits could emerge.
Kirkpatrick, Gabe, CVE-2023-38146: Arbitrary Code Execution via Windows Themes, blog post, 13 September 2023. Available online at https://exploits.forsale/themebleed/.
Microsoft Uncovers Vulnerabilities in Linux Terminal Handling Code
One of the common assumptions in the open source community is that the older software packages which are core to that ecosystem must have had all the bugs and vulnerabilities distilled out of them by constant review and usage over the years. We treat many of the older products of the BSD and GNU projects that way, for example - after all, they date back to a simpler time, and the biggest enemy of security is complexity, so these 'simple' programs can't be a problem, right?
Wrong, as it turns out. It's an invalid assumption for a number of reasons - not least that many of these programs are not at all simple, as demonstrated by the case of the ncurses package, the 'new' version of the even older curses library for dumb terminal cursor management on UNIX/Linux systems. Many programs use ncurses - almost any text-mode full-screen program such as your favourite editor, be it vi, nano or emacs, various system admin tools and even the top utility for monitoring processes.
With the growth of minicomputers from the 1960's onwards, a variety of manufacturers - Televideo is one example that comes easily to mind - flooded the market with increasingly sophisticated serial-interface terminals, each manufacturer using its own 'command language' of escape sequences and control characters for functionality like cursor positioning, erasing sections of lines, entire lines or blocks of the screen area and other functionaity for use by programs. Things got even more complicated with different models having different screen sizes, windowing or screen-switching capabilities, extended character sets and primitive, box-drawing graphics capabilities.
In order to map the functionalities required by programs, such as screen-clearing and cursor positioning, to the different possibilities and escape sequences, the curses library was developed. This could be customised through termcap databases, which define the capabilities of different terminals and the escape sequences and control characters that drive them. Eventually, curses was replaced by the Free Software Foundation's ncurses package, which is even more capable.
Both curses and ncurses are configured by environment variables, especially TERMINFO, which points to any non-default directory where a termcap database can be found. If TERMINFO is undefined, then ncurses will look in the user's home directory for a .terminfo directory - but the home directory itself is defined by an environment variable: HOME. This opens up the possibility of introducing malicious termcap files and using environment variable poisoning to get them loaded.
What's worse is that terminfo is far from simple; its capabilities include a primitive stack-oriented programming language, rather like that found in Hewlett-Packard scientific programmable calculators, not to mention FORTH and the Postscript page description language. This little language might not be Turing-complete, but to a hacker (whether good or bad) the availability of a scripting or programming language opens up all kinds of delicious possibilities. What's more, the word stack is positively ripe with possibilities, conjuring up visions of buffer overflows and stack smashing attacks.
And sure enough, when some security researchers at Microsoft turned their attention to ncurses, using code review and fuzzing, that's exactly what they found: a number of exploitable memory mis-management vulnerabilities. The details are moderately technical and too detailed to go into here; suffice to say that they are enough to demolish the idea that 'mature' code is low-risk. Consider the fact that the top command on macOS is a setUID executable (unlike on Linux) and you can see that a buffer overflow in ncurses could be a useful path to a privilege escalation exploit.
The Microsoft researchers obviously disclosed what they had found, and the current maintainer of ncurses, Thomas E. Dickey, worked up fixes back in April, making this particular set of vulns of historical interest only. But perhaps this will alert black hats to revisit some old code, working up some new exploits. And in the meantime, the Microsoft blog piece is a fascinating read.
Microsoft Threat Intelligence, Uncursing the ncurses: Memory corruption vulnerabilities found in library, blog post, 14 September 2023. Available online at https://www.microsoft.com/en-us/security/blog/2023/09/14/uncursing-the-ncurses-memory-corruption-vulnerabilities-found-in-library/.
Upcoming Courses
- SE221 CISSP Fast Track Review, Virtual/Online, 13 - 17 November 2023
- SE221 CISSP Fast Track Review, Sydney, 4 - 8 December 2023
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
Kubernetes Admins Urged to Patch Against Remote Command Execution Vuln
Administrators of Kubernetes clusters with Windows endpoints are being urged to update, following the discovery by Akamai security researcher Tomer Peled of a high-severity vulnerability which allows remote command execution. Analysing the vulnerability revealed the underlying root causes: an insecure function call and the lack of user input sanitization. And working forward again from there revealed two more vulnerabilities with the same root causes.
The vulnerabilities are:
All three have a CVSS score of 8.8, and fixes for them were released on 23 August, but they do not yet appear in the National Vulnerability Database.
CVE-2023-3676 allows remote command execution, and the way it does this is instructive. Kubernetes allows directories to be shared between a created pod and the underlying host, and this is done by adding volume parameters in the pod's YAML configuration file. This file is parsed by the kubelet service, and it validates the YAML subPath parameter by calling a function called isLinkPath(), which is where the vulnerability can be exploited:
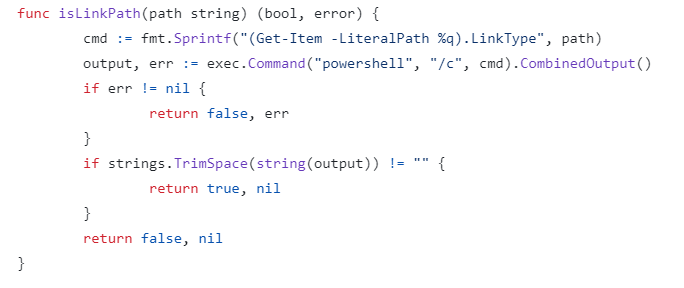
In order to validate the existence of a mount point path, this function directly inserts the path parameter, which is picked up from the YAML file, into a Windows PowerShell command, and then calls exec.Command() to execute it. The presence of exec.Command() is a massive red flag: any code that calls the isLinkPath() function would need to ruthlessly sanitize the path string passed to it. In particular, much like POSIX shells (e.g. bash), PowerShell allows parameter expansion using $( ) syntax. Any command - e.g. Start-process cmd - can be inserted into the $( ), and by placing this into the subPath parameter of the YAML file, it will get passed into the isLinkPath() function, which will assign the cmd variable the value
(Get-Item -LiteralPath $(Start-process cmd).LinkType)
then get PowerShell to execute it - which will first run StartProcess cmd, starting a command prompt, and then try to run Get-Item -LiteralPath on the result. This will probably fail, but for the attacker that's not a problem - they've got the shell they wanted.
Peled's write-up provides a proof-of-concept example, as well as suggested mitigations, the primary one being to apply a patch that fixes the vulnerability, by passing the path parameter to PowerShell as an environment variable, thereby avoiding the parameter expansion. Crude, but effective.
Peled, Tomer, Can't Be Contained: Finding a Command Injection Vulnerability in Kubernetes, blog post, 13 September 2023. Available online at https://www.akamai.com/blog/security-research/kubernetes-critical-vulnerability-command-injection.
CISA Adds Five Vulns to Known Exploited Vulnerabilites Catalog
CISA has added five vulnerabilities to its Known Exploited Vulnerabilities Catalog over the last couple of days.
- CVE-2023-36761 - a Microsoft Word Information Disclosure Vulnerability
- CVE-2023-36802 - a Microsoft Streaming Service Proxy Elevation of Privilege Vulnerability
- CVE-2023-35674 - Android Framework Privilege Escalation Vulnerability
- CVE-2023-20269 - Cisco Adaptive Security Appliance and Firepower Threat Defense Unauthorized Access Vulnerability
- CVE-2023-4863 - Google Chrome Heap-Based Buffer Overflow Vulnerability
In other news, yesterday was the monthly Windows Patchday; September's security updates consists of 59 vulnerabilities.
CISA, CISA Adds Two Known Vulnerabilities to Catalog, alert, 12 September 2023. Available online at https://www.cisa.gov/news-events/alerts/2023/09/12/cisa-adds-two-known-vulnerabilities-catalog.
CISA, CISA Adds Three Known Vulnerabilities to Catalog, alert, 13 September 2023. Available online at https://www.cisa.gov/news-events/alerts/2023/09/13/cisa-adds-three-known-vulnerabilities-catalog.
Microsoft Security Resource Center, September 2023 Security Updates, release note, 12 September 2023. Available online at https://msrc.microsoft.com/update-guide/releaseNote/2023-Sep.
US Agencies Warn of Deepfake Threats
As machine learning and AI continues to rapidly evolve, the US National Security Agency, FBI and CISA have released an information sheet on the problem of deepfaking - the use of synthetic media by threat actors. These AI-generated images, audio and video are used for a variety of tactics, ranging from information operations to spread false information to phishing and whaling attacks.
The 18-page report delves into the challenges posed by deepfakes, the impact deepfaking can have on organizations, and recommendations for mitigating attacks which use them.
CISA, NSA, FBI, and CISA Release Cybersecurity Information Sheet on Deepfake Threats, cybersecurity advisory, 12 September 2023. Available online at https://www.cisa.gov/news-events/alerts/2023/09/12/nsa-fbi-and-cisa-release-cybersecurity-information-sheet-deepfake-threats.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
Initial Access Broker Ramps Up MS Teams Attacks
A threat actor tracked by Microsoft as Storm-0324 (also TA543/Sagrid) has begun distributing payloads using an open-source tool called TeamsPhisher to send phishing lures through Microsoft Teams chats. Storm-0324 typically acts as an initial access broker - once it has compromised a victim, it then sells off access to other threat actors, by implanting their choice of loader, backdoor, stealer or ransomware (such as JSSLoader for ransomware-as-a-service operator FIN7).
Storm-0324 operates a sophisticated traffic distribution chain to bypass identification and filtering capabilities as they deliver phishing emails and malmails. Their emails often make references to invoices and payments, and they mimic cloud services like DocuSign, Quickbooks Online and others.
The Storm-0324 malware distribution chain typically redirects users to a Sharepoint-hosted compressed file - an MS Office document, a Windows Script File (.wsf) or VBScript - which then launches some malicious JavaScript to download the final malicious DLL payload. Since 2016, Storm-0324 has used a variety of first-stage payloads:
- Nymaim, a first-stage downloader and locker
- Gozi version 3, an infostealer
- Trickbot, a modular malware platform
- Gootkit, a banking trojan
- Dridex, a banking trojan
- Sage ransomware
- GandCrab ransomware
- IcedID, a modular information-stealing malware
- JSSLoader - a modular loader and infostealer
However, in July 2023, Storm-0324 began using phishing lures sent over Microsoft Teams with links leading to a malicious Sharepoint-hosted file, using TeamsPhisher, a Python program that enables Teams tenant users to attach files to messages sent to external tenants. These lures are identified by the Teams platform as "EXTERNAL" users (if the organization has enabled external access in the first place).
Microsoft has rolled out a number of enhancements to the Accept/Block dialog in one-on-one chats within Teams, to better emphasize the external nature of a user and their email address. There are also new restrictions on the creation of domains within tenants and improved notifications to admins when new domains are created.
Microsoft makes a number of recommendations for Teams customers, including better user education, deployment of phishing-resistant authentication mechanisms such as security keys or software TOTP authenticator apps and allowing chat and meetings with only specific trusted organizations.
Microsoft Threat Intelligence, Malware distributor Storm-0324 facilitates ransomware access, blog post, 12 September 2023. Available online at https://www.microsoft.com/en-us/security/blog/2023/09/12/malware-distributor-storm-0324-facilitates-ransomware-access/.
CISA Releases Open Source Software Security Roadmap
The US Cybersecurity & Infrastructure Security Agency has released its Open Source Software Security Roadmap which lays out the agency's path to helping ensure a secure FLOSS ecosystem. The impact of highly-publicized vulnerabilities in open source software, and the related exploits such as Log4Shell, demonstrates that this effort could return significant benefits.
The roadmap lays out four key goals, each with subsidiary objectives:
- Establish CISA's Role in Supporting the Security of OSS
- Partner with OSS Communities
- Encourage Collective Action From Centralized OSS Entities
- Expand Engagement and Collaboration With International Partners
- Establish and Organize CISA’s OSS Work
- Drive Visibility into OSS Usage and Risks
- Understand OSS Software Prevalence
- Develop a Framework for OSS Risk Prioritization
- Conduct Risk-Informed Prioritization of OSS Projects in Federal Government and Critical Infrastructure
- Understand Threats to Critical OSS Dependencies
- Reduce Risks to the (US) Federal Government
- Evaluate Solutions to Aid in Secure Usage of OSS
- Develop Open Source Program Office Guidance For Federal Agencies
- Drive Prioritization of Federal Actions in OSS Security
- Harden the OSS Ecosystem
- Continue to Advance SBOM (Software Bill of Materials) Within OSS Supply Chains
- Foster Security Education for Open Source Developers
- Publish Guidance on OSS Security Usage Best Practices
- Foster OSS Vulnerability Disclosure and Response
The roadmap aims to address two primary classes of open-source vulnerabilities and exploits: the cascading effects of vulnerabilities in widely-used libraries and subsystems which ship as part of larger applications, and supply-chain attacks on open-source repositories, which then lead to compromise of downstream software.
The Agency is inviting feedback on its open-source efforts, at OpenSource@cisa.dhs.gov.
CISA, CISA Open Source Software Security Roadmap, resource, 12 September 2023. Available online at https://www.cisa.gov/resources-tools/resources/cisa-open-source-software-security-roadmap.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
CISA Warns of Apple Device Vulnerabilities
The Cybersecurity & Infrastructure Security Agency has added two new vulnerabilities to the Known Exploited Vulnerabilities Catalog, warning that "these types of vulnerabilities are frequent attack vectors for malicious cyber actors and pose significant risks to the federal enterprise." The two vulnerabilities, which are present in iOS, iPadOS and macOS are:
- CVE-2023-41064 - a buffer overflow vulnerability in imageIO which allows remote code execution when processing a maliciously-crafted image
- CVE-2023-41061 - an input sanitization vulnerability affecting Wallet which allows remote code execution when processing a maliciously-crafted attachment
The two vulnerabilities can be chained to create a zero-click exploit chain - i.e. with no user interaction required - used to deliver NSO Group's Pegasus spyware. The exploit chain was discovered by The Citizen Lab of the Munk School at University of Toronto while examining the device of an individual employed by a Washington DC-based NGO with international offices.
Citizen Lab stated:
We encourage everyone who may face increased risk because of who they are or what they do to enable Lockdown Mode. We believe, and Apple’s Security Engineering and Architecture team has confirmed to us, that Lockdown Mode blocks this particular attack.
Apple has fixed the vulnerabilities in iOS 16.6.1, iPadOS 16.6.1 and macOS Ventura 13.5.2; users are encouraged to upgrade as soon as possible.
CitizenLab, BLASTPASS: NSO Group iPhone Zero-Click, Zero-Day Exploit Captured in the Wild, news release, 7 September 2023. Available online at https://citizenlab.ca/2023/09/blastpass-nso-group-iphone-zero-click-zero-day-exploit-captured-in-the-wild/.
CISA, CISA Adds Two Known Vulnerabilities to Catalog, cybersecurity advisory, 11 September 2023. Available online at https://www.cisa.gov/news-events/alerts/2023/09/11/cisa-adds-two-known-vulnerabilities-catalog.
MrTonyScam Stealer Spreads Via Facebook Messenger
A campaign to steal the Facebook and other accounts of businesses is spreading via Facebook Messenger. The campaign, dubbed "MrTonyStealer", originates in Vietnam, according to Guardio Labs researcher Oleg Saytsev, and while it relies on social engineering the victim into downloading a file attachment, unzipping and then running it, it is achieving a concerning success rate, with roughly one in each 350 recipients becoming infected.
The goal is to hijack Facebook business accounts that have a good reputation, seller rating and many followers, with the intention of selling them on Telegram and other dark markets. The purchaser can then use such an account for advertising or scams. And business account owners are particularly vulnerable: while private users can happily ignore messages from unkown senders, a business cannot ignore what could be a legitimate enquiry, especially if the lure message threatens a copyright strike or other penalty. And, of course, once the stealer infects the victim, it can also gather credentials for other accounts - banks, cloud-hosted accounting, email, e-commerce platforms, etc. - from the browser's cookies and stored passwords.
The attack delivers an archive file - .rar or .zip - which the recipient is lured to download and open to reveal a batch file. This is a first-stage dropper which, if run, downloads a stage 2 dropper from GitHub. This, in turn, starts the Chrome browser, pointing it to the Alibaba web site as a distraction, while in the background it downloads additional components and starts the main stealer, called project.py, in a standalone Python environment and makes it persistent via a startup batch file.
Once running, the stealer extracts all cookies and login credentials from the victim's browsers, sending them to a Telegram channel via the Telegram/Discord bot API, and then deletes all the cookies, locking the victim out of their accounts and giving the scammers time to hijack the session and change the password. The code uses a variety of obfuscation and detection evasion techniques, but the presence of Vietnamese-language comments in the code, and the inclusion of the "Coc Coc" Chromium-based browser, popular in Vietnam, betray its origin.
The GuardIO blog post provides a comprehensive analysis and IOC's, but the basic message, and mitigation technique, is obvious: don't just double-click on Facebook Messenger attachments, and treat archive files as highly suspicious.
Zaytsev, Oleg, “MrTonyScam” - Botnet of Facebook Users Launch High-Intent Messenger Phishing Attack on Business Accounts, blog post, 11 September 2023. Available online at https://labs.guard.io/mrtonyscam-botnet-of-facebook-users-launch-high-intent-messenger-phishing-attack-on-business-3182cfb12f4d.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
Dymocks Latest Ransomware Victim
Australian bookstore chain Dymocks is the latest victim of ransomware attack. In an email titled "Important Update About Your Dymocks Information", sent to customers on Friday afternoon (8 September), the firm disclosed that on 6 September it had become aware of discussions regarding its customer records being made available on the dark web.
At the time the email was sent, the company was unaware of the precise nature of the attack or which customers were affected, but the information they hold includes:
- date of birth
- postal address
- email address
- mobile number
- gender
- membership details such as gold expiry date, account status, member created date and card ranking
Dymocks does not store credit card or other financial data, but what they do hold could form the basis of some scams and identity fraud. Dymocks' email procides the usual guidance such as changing passwords, monitoring bank statements, and being alert to scams.
However, Have I Been Pwned states that the breach actually occurred in June, and the data set comprises 1.2 million records with 836,120 unique email addresses.
Dymocks Pty Ltd, Important Update About Your Dymocks Information, email, 8 September 2023.
Scammers Can Abuse Email Forwarding
In a paper presented at the 8th European Symposium on Privacy and Security in July - winning the best paper award - researchers from UC San Diego, Stanford and University of Twente revealed that flaws in how major email services process the forwarding of email can make it easier for email scam and phishing operators to impersonate legitimate email addresses at high-profile domains.
The basic problem is that spam filtering techniques mostly work on the assumption that each Internet domain operates its own email infrastructure so that, for example, a reverse DNS lookup for a connecting IP address (using the PTR resource record) will return a hostname that matches a host in the same domain. More advanced protections such as SPF (Sender Policy Framework) and DKIM (DomainKeys Identified Mail) implicitly incorporate this assumption.
However, most enterprises today have outsourced their email infrastructure to a few, very large, service providers - most notably Microsoft (outlook.com) and Google (gmail.com) - and while these companies validate that their users only send email on behalf of the domains they operate, this validation can be bypassed by email forwarding
Forwarding is both ubiquitous and necessary in the email ecosystem, due to the wide use of email filtering services, mailing lists and autoforwarding employed by individual users and small and medium enterprises, who often use a web hosting account to forward inbound email to their Outlook or Gmail account.
The researchers identified four different approaches in the way mail services rewrite the sender and recipient fields in the SMTP envelope and email headers while forwarding and email to its recipient. Using the domain of the US Department of State (state.gov) as an example, they showed how an attacker can create a spoofed email with a fake identity which appears to come from the Department, and then forward it through their personal Outlook account. To the recipient, this will appear legitimate, since it comes from an Outlook email server - and the Department of State uses Outlook as its email provider.
This works because, almost uniquely, Outlook uses a custom forwarding implementation which the researchers term "MAIL FROM Equals FROM" (MFEF). This not only rewrites the RCPT TO header to be the final recipient (to whom the email is being forwarded) but also sets the MAIL FROM header to be the same as the FROM header. While this will break SPF, the fact is that this and similar problems have hindered the adoption of SPF and DMARC, forcing email providers to use customised defenses.
Variants of this flaw affect five other email providers including iCloud, while smaller issues impact users of Gmail and Zohomail, a popular Indian email provider. The researchers disclosed the vulnerabilities to the various providers, some of whom fixed the issues or at least are working on them.
Liu, Enze, et. al, Forward Pass: On the Security Implications of Email Forwarding Mechanism and Policy, Proc. 8th IEEE Symposium on Privacy and Security, 3 - 7 July 2023, Delft. Available online at https://arxiv.org/abs/2302.07287.
Patringenaru, Ioana, Scammers Can Abuse Security Flaws in Email Forwarding to Impersonate High-profile Domains, UC San Diego Today, 5 September 2023. Available online at https://today.ucsd.edu/story/forwarding_based_spoofing.
China Ramps Up Cyber-Espionage, Disinformation Campaigns
A new report from Microsoft Threat Intelligence warns that China has ramped up both its cyber-espionage efforts against the US defence and critical infrastructure sectors, and its online influence operations to destabilise the US political environment.
The operations by China-affiliate threat actors have focused on three areas in particular:
- The South China Sea and Taiwan, reflecting conflicts over territorial claims, rising tensions across the Taiwan Strait, and increased US military presence in the region
- The US defence industrial base, particularly enterprises with any connection to the satellite and telecommunications facilities associated with the US Marine Corps base in Guam
- US critical infrastructure across multiple sectors including transportation, utilities, medical (e.g. hospitals) and telecommunications, particularly with the potential to disrupt US-Asia communications
China has also become significantly more effective in engaging social media users with influence operations, switching from a strategy of deluging social networks via bots to engaging directly with authentic users, targeting specific candidates in content about US elections and posing as US voters. Microsoft estimates that this initiative has successfully engaged target audiences in at least 40 languages and grown its audience to over 103 million.
The operators behind some of these social media accounts have begun using generative AI to create visual content which is more eye-catching than the memes used in previous campaigns. Authentic users often repost these, despite their obvious clues of AI generation, such as more than five fingers on the torch-holding hand of the Statue of Liberty. Other accounts pose as independent social media influencers, despite being employed by Chinese state media in what the Chinese Communist Party terms "multilingual internet celebrity studios".
In online news media, Chinese state media has been artfully positioning itself as the authoritative voice in international discourse on China, using a variety of means to exert influence in media outlets worldwide, such as localized news websites which push Chinese Communist Party propaganda to the Chinese diaspora in over 35 countries.
The report also covers increasingly sophisticated operations by North Korea, as the regime has set high-priority requirements for its cyber-espionage operations, particularly for maritime technologies, as well as increasing cryptocurrency theft and supply chain attacks.
Microsoft Threat Intelligence, Digital threats from East Asia increase in breadth and effectiveness, report, 7 September 2023. Available online at https://www.microsoft.com/en-us/security/business/security-insider/reports/nation-state-reports/digital-threats-from-east-asia-increase-in-breadth-and-effectiveness/ (full report PDF at https://query.prod.cms.rt.microsoft.com/cms/api/am/binary/RW1aFyW).
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
Mirai Derivative Exploits Android TV's
Russian anti-malware company Dr. Web reports the identification of a new family of trojans that compromises Android TV devices, either during firmware updates or when applications for watching pirated video content are installed. This new backdoor sports advanced DDoS attack capabilities by using code from the Mirai botnet trojan.
Dubbed Android.Pandora.2, the trojan seems to be a modification of the Android.Pandora.10 backdoor (also known as Android.Backdoor.334). It targets low-end Android TV set-top boxes such as the Tanix TX6 TV Box, MX10 Pro 6K and H96 MAX X3. An analysed sample arrived as a malicious formware update - released in December 2015 (!) - for the MTX HTV BOX HTV3 device and has likely been deployed to a number of websites. Other samples target Spanish-speaking users via apps for streaming pirated movies and TV shows, via domains with names like 'youcine', 'magistv', 'latinatv' and 'unitv' this variant has a different installation process and is identified as Android.Pandora.4.
The main malware is a file called /system/bin/pandoraspearrk, which joins the infected system to a DDoS botnet; it is monitored by a process called /system/bin/supervisord which will restart it if it is killed. It also installs its own copies of the busybox shell and curl. Once installed and running, the trojan will accept commands to start and stop various DDoS attacks, open a reverse shell, mount partitions in RW mode, etc.
This malware illustrates the dangers posed by IoT device users who know just enough to side-load their devices with code from dubious sources but not enough to secure them; they may well get cheap functionality and access to pirated content, but their devices can become useful platforms for attackers interested in bigger fish.
Dr. Web, Pandora's box is now open: the well-known Mirai trojan arrives in a new disguise to Android-based TV sets and TV boxes, news release, 6 September 2023. Available online at https://news.drweb.com/show/?lng=en&i=14743.
Apache Project Vulnerabilities
Two Apache projects are causing problems in the enterprise world.
The first is Apache RocketMQ, a distributed messaging and streaming middleware system, which has triggered action from CISA by adding CVE-2023-33246 to its list of known exploited vulnerabilities. Several components of RocketMQ, including NameServer, Broker and Controller are often exposed via an extranet but lack permission verification; an attacker can exploit this by using the 'update configuration' function to execute commands with privileges of the RocketMQ system account. Alternatively, they can also achieve remote command execution by forging RocketMQ protocol messages.
Affected users should upgrade to RocketMQ version 5.1.1 or above, or RocketMQ version 4.9.6 or above.
Meanwhile, researchers at Horizon3.ai warn of vulnerabiliities in Apache Superset, a popular Python open source data exploration and visualization tool based on the Flask web framework. A previous vulnerability, CVE-2023-27524 (also discovered by Horizon3.ai) could allow an attacker to obtain the Flask SECRET_KEY value and thereby obtain admin privileges, but this was mostly fixed in Superset 2.1.0. The two new high-severity vulnerabilities, CVE-2023-39265 and CVE-2023-37941, allow further exploitation - in some cases after using CVE-2023-27524 or other means of obtaining admin privileges, but in others from non-admin accounts.
CVE-2023-39265 allows a bypass of URI checking in the Superset UI, which would normally block connection to its own metadata database (which is SQLite, by default). The checks will fail if the supplied URI includes both the dialect and driver name, e.g.
sqlite+pysqlite:////app/superset_home/superset.db
After connecting to the metadata store, an attacker can then access it via SQLLab, allow database exploration, querying and updates. The same vulnerability also applies to database connection information imported from files, allowing control of arbitrary SQLite metadata databases. In fact, if Superset is configured to use MySQL for the metadata database, it is also possible to obtain credentials for the database and also connect to it through the Superset UI.
CVE-2023-37941 extends this attack chain further, allowing remote code execution by an attacker with access to the metadata database. Vulnerable versions of Superset use Python's pickle package to store some configuration data, and the attacker can insert an arbitrary pickle payload into the database and then trigger its deserialization and execution.
These vulnerabilities are fixed in Superset version 2.1.1, and users should upgrade immediately.
CISA, CISA Adds One Known Vulnerability to Catalog, cybersecurity advisory, 6 September 2023. Available online at https://www.cisa.gov/news-events/alerts/2023/09/06/cisa-adds-one-known-vulnerability-catalog.
Sunkavally, Naveen, Apache Superset Part II: RCE, Credential Harvesting and More, blog post, 6 September 2023. Available online at https://www.horizon3.ai/apache-superset-part-ii-rce-credential-harvesting-and-more/.
Multiple Nation State Actors Exploit Zoho ManageEnging ServiceDesk Plus
Back in June, we reported on an campaign conducted by China-affiliated threat actor VANGUARD PANDA (also known as Volt Typhoon), exploiting Zoho ManageEngine ADSelfService Plus in order to obtain initial access, after which they deployed webshells and made use of living-off-the-land techniques to avoid leaving behind detectable artifacts which could be used as IOC's.
Now the US Cybersecurity & Infrastructure Security Agency, FBI and Cyber National Mission Force have published a joint cybersecurity advisory providing information on an incident which appears to be related. The agencies confirmed that a nation-state advanced persistent threat exploited CVE-2022-47966 (an RCE vuln related to yet another Apache project, xmlsec) to gain unauthorized access to a public-facing application (Zoho ManageEngine ServiceDesk Plus), establish persistence, and move laterally through the network of an aviation sector entity. Additional APT actors were also observed exploiting CVE-2022-42475 to establish presence on the organization’s firewall device.
The joint advisory provides a full, detailed analysis of initial access vectors and post-exploitation activities, including the tools the threat actor used, along with a mapping to MITRE ATT&CK techniques, detection methods and suggested mitigations.
CISA, Multiple Nation-State Threat Actors Exploit CVE-2022-47966 and CVE-2022-42475, cybersecurity advisory, 7 September 2023. Available online at https://www.cisa.gov/news-events/cybersecurity-advisories/aa23-250a.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.