Les Bell and Associates Pty Ltd
Site blog
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
FBI Takes Down Qakbot
The US DoJ and FBI have announced their successful disruption of the long-running Qakbot malware botnet in an international operation called "Operation Duck Hunt".
Qakbot appeared in 2008, initially as a banking trojan, but in the years since then has evolved, thorugh continual updates, into a general-purpose trojan dropper or second-stage loader used by multiple threat actor groups as a remote access trojan; its modular design provides remote code execution, the ability to install ransomware, keystroke logging and other functions. It can also be classified as a worm, since it can propagate itself to other systems on a network. Over the years, it has proved popular with ransomware gangs such as REvil, ProLock, ALPHV/BlackCat and Lockbit, who use it in their big game hunting.
Threat actors have usually obtained initial access by using malmail phishing campaigns; their emails carry malicious files - sometimes MS Office documents with malicious macros, but also archives such as ISO images - which the victim is lured into opening and running. This then injects the Qakbot code into a the memory of a legitimate process, in order to evade detection.
The FBI operation, which was conducted with international partners in France, Germany, the Netherlands, Romania, Latvia, and the United Kingdom, involved accessing the Qakbot C2 infrastructure; this allowed the identification of over 700,000 Qakbot-infected computers worldwide, including over 200,000 in the US. The Qakbot botnet traffic was then redirected to servers controlled by the FBI.
Now comes the "clever" part: in conjunction with technical partners, the FBI developed an uninstaller program for Qakbot, and their servers instruced the infected computers to download and run the uninstaller. The uninstaller consists of shellcode to unpack a custom DLL which sends a QPCMD_BOT_SHUTDOWN command via a named pipe which Qakbot uses for interprocess communications. This has the effect of shutting the Qakbot main thread and exiting the process in such a way that it will not restart after a reboot.
Many users will have been unaware that their systems had been infected, and the FBI's removal process is similarly invisible, so possible victims should check with services like https://haveibeenpwned.com/ to discover whether they were affected.
This operation has significantly disrupted the Qakbot botnet, but no arrests have been made, so its operators will doubtless be back with a new generation of their malware. In the meantime, the way the FBI invisibly distributed their uninstaller program is bound to renew debate about the ethical basis of the no-longer-quite-so-hypothetical 'good virus' approach to defeating malware. The argument used to be that users should be in control of every piece of code that runs on their system, but the complexity and opacity of todays operating systems and applications means that that particular horse bolted from the stable years ago.
Office of Public Affairs, US Department of Justice, Qakbot Malware Disrupted in International Cyber Takedown, press release, 29 August 2023. Available online at https://www.justice.gov/opa/pr/qakbot-malware-disrupted-international-cyber-takedown.
Federal Bureau of Investigation, FBI, Partners Dismantle Qakbot Infrastructure in Multinational Cyber Takedown, news release, 29 August 2023. Available online at https://www.fbi.gov/news/stories/fbi-partners-dismantle-qakbot-infrastructure-in-multinational-cyber-takedown.
Secureworks, Law Enforcement Takes Down Qakbot, blog post, 29 August 2023. Available online at https://www.secureworks.com/blog/law-enforcement-takes-down-qakbot.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
Authentication Vulnerability in Azure Active Directory
A key benefit of the federated identity management systems provided by cloud service providers like Google and Microsoft is the ability to authenticate to cloud applications without having to maintain credentials on all of them. To do this, the identity provider - in the case of Microsoft, this is Azure Active Directory - authenticates the user once, and then the user allows the relying party to obtain an authentication token from the identity provider.
This process involves the use of RESTful API's to pass the necessary messages among the parties. When a web service requests authorization for a user from the identity provider, it does so by calling an API, but the operation is not synchronous - rather, it registers an API URL which the identity provider will, in turn, call back, and this will run code which completes the authentication or login process in the web service. This API is called a reply URL or callback URL. A lot of cloud services work this way, as do widely-used web sites such as newspapers and magazines which integrate with cloud identity providers.
Now, researchers at Secureworks Counter Threat Unit have discovered a vulnerability which allows threat actors to redirect these reply URL's, and receive the authorization tokens which they can then exchange for access tokens and, eventually, achieve a privilege escalation attack.
The vulnerability was first observed early this year in an Azure AD API used by Microsoft's Power Platform - a low-code application development framework - and worked via an abandoned reply URL. Secureworks reported it to Microsoft, who confirmed the vulnerability, assigned it a critical severity rating, and promptly removed the abandoned reply URL API. But the researchers asked themselves the obvious question: are there other abandoned reply URL API's in Azure AD applications which could be similarly exploited.
After developing a scanner which would search for abandoned reply URL values and confirm if they were available for registration, they had their answer: yes, there were. The exploit itself is quite involved, so I won't get into the details here; the Secureworks blog post does a good job of that. But the researchers found an abandoned Dynamics Data Integration app reply URL, associated with the Azure Traffic Manager profile, which was pre-consented and therefore required no additional consent to stage the attack.
The researchers reported the vulnerability to the Microsoft Security Response Center, who immediately investigated and released an update the following day. However, this entire saga illustrates the dangers posed by outdated and abandoned API's. It's important for developers and operations personnel not just to focus on deployment of new API's, but also to include a procedure for retirement of the old ones.
Counter Threat Unit Research Team, Power Platform Privilege Escalation, threat analysis, 24 August 2023 (updated 28 August 2023). Available online at https://www.secureworks.com/research/power-platform-privilege-escalation.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
BitLocker Broken Using Cheap Logic Analyzer
One of the most common - and, generally, most effective - safeguards for mobile devices such as laptop computers is the use of encrypted filesystems such as BitLocker, Veracrypt and others. And, of course, to protect the encryption key used for an encrypted volume, the best option would be to store it, not on the disk itself, but in the Trusted Platform Module.
This is the way that BitLocker works; the BitLocker partition on a laptop is encrypted using a Full Volume Encryption Key, which is itself encrypted using the Volume Master Key and then stored on the disk, next to the encrypted data. The Volume Master Key is sealed in the TPM chip, and only unsealed when the system is booted.
Now, pen tester and security engineer Guilaume Quéré has demonstrated a fairly simple and inexpensive attack which extracts the Volume Master Key as it is transferred over the laptop SPI (Serial Peripheral interface) bus from the TPM to the CPU. Quéré accomplished this attack on a Lenovo L13 laptop, using a sub-$US100 logic analyzer, admittedly pushing it to its limits. The SPI bus has several lines, but the best the DSLogic analyzer can do is to sample three of them without exceeding its limits - but fortunately only the clock (CLK) and the two data lines (MOSI and MISO) are required. And rather than trying to connect to the tiny pins of the TPM chip, he was able to pick these signal lines of a larger nearby flash memory chip which is also on the SPI bus.
Once the logic analyzer was successfully capturing the signal, the next step was to decode the protocol used to transfer the VMK. In fact, there are three layers involved:
- SPI (the physical layer)
- TIS (TPM Interface Specification)
- TPM 2.0 (which carries the TPM commands and the VMK itself)
According to Quéré, it was the TIS layer that proved most challenging, perhaps because his captures did not include the SPI bus's CS (Chip Select) signal. In the end, Quéré resorted to manually decoding these frames. From there, he was able to identify the TPM_Unseal command in the TPM 2.0 frames, and then find the response, which comes around 10 ms later and carries the 256-bit Volume Master Key. From there, it was a simple matter of a few commands to mount the disk and bypass the BitLocker protection.
According to Quéré, the use of the TPM does not increase the security of the system as expected, especially since a more expensive, professional-grade logic analyzer - well within the budget of even moderately serious threat actors - would have saved a lot of time and simplified the attack. Currently, the best safeguard will be to set a passphrase or PIN on BitLocker; in the longer term, integration of the TPM onto the CPU die will mean that the communication between them is not externally exposed.
Quéré, Guillaume, Bypassing Bitlocker using a cheap logic analyzer on a Lenovo laptop, blog post, undated. Available online at https://www.errno.fr/BypassingBitlocker.html.
Rowntree, Dave, Bypassing Bitlocker With A Logic Analzyer, Hackaday, 25 August 2023. Available online at https://hackaday.com/2023/08/25/bypassing-bitlocker-with-a-logic-analzyer/.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
Credential Abuse Our Biggest Problem, Says Sophos
In their mid-2023 Active Adversary Report for Tech Leaders, Sophos provide some interesting food for thought. Based on data summarized from the firm's incident response investigations for the first half of this year, the goal is to provide better insight on changes in the threat landscape.
Perhaps the most significant finding is that the initial access techniques favoured by threat actors have changed. As before, attackers exploited external remote services (such as VPN's and gateways to Citrix servers, etc.) and public-facing applications, including email gateways (Exchange - we're looking at you). However, they are no longer primarily exploiting vulnerabilities to do this but rather compromising credentials - vulnerabilities lay at the root of only 23% of exploitations, while compromising account credentials accounted for 50%. Furthermore, having access to a legitimate account makes it easier for an intruder to evade detection. (Only yesterday we mentioned the Cyber Safety Review Board report on Lapsus$ and related attacks; Lapsus$ used quite simple social engineering techniques to obtain credentials, very successfully.)
The obvious implication for defenders is that there is enormous return on a minimal investment to be had in the deployment of multi-factor authentication. Sophos state that MFA was not configured in 39% of the cases examined for their report - and as confirmation of the effectiveness of strong, phishing-resistant MFA, they observe that one of the very latest social-engineering tactics is texting to encourage the recipient to disable their Yubikey.
The decline in the successful exploitation of vulnerabilities does not mean that rapid patching is less necessary, however - in fact, it might reflect the fact that we are getting better at it. Sophos point to the US Government's Binding Operational Directive 19-02, which states that:
- Critical vulnerabilities must be remediated within 15 calendar days of initial detection
- High vulnerabilities must be remediated within 30 calendar days of initial detection
This has prompted US Government agencies to improve their patch management, and this is reflected in CISA's 2022 Risk and Vulnerability Assessments, which found that only 1% of initial access attacks were due to exploits - but compromised credentials were responsible for 54%. Are we seeing the pattern here?
In Sophos' previous report, just two vulnerabilities accounted for 55% of exploits investigated: ProxyShell and Log4Shell, both of which already had patches released. In the FHY 2023 data, there were no Log4Shell exploits, but ProxyShell lives on, along with a few other vulnerabilities which had been patched in 2020 and even 2019. There is obviously still scope for a lot more improvement in patch management.
The Sophos report provides other insights which are, at first glance, more comforting - for example, dwell times (the delay between exploitation and detection) is falling. But looking more deeply into this, it's actually bad news: the dwell time for ransomware has fallen from 9 days to 5 days, as its operators exfiltrate data more quickly before encrypting files, making the infection obvious, while the dwell time for non-ransomware incidents has risen slightly, from 11 days to 13 days.
There's more bad news for Windows network admins, although they probably know it already: after gaining initial access, threat actors are pivoting more quickly than ever to exploit Active Directory servers, which give them greatly enhanced capabilities within networks, including the ability to manipulate accounts and policies throughout the domain. They also continue to exploit RDP (Remote Desktop Protocol) to move laterally - in fact, it was used in 95% of attacks, up from 88% in 2022.
There's a lot more to digest in the Sophos report: it discusses exfiltration techniques, the various types of attacks (ransomware, network breaches, extortion and exfiltration, web shells, denial of service, etc.) and the times and weekdays thy are run, as well as attribution to various threat groups. Much to consider, from a strategic threat intelligence perspective.
Shier, John, Time keeps on slippin’ slippin’ slippin’: The 2023 Active Adversary Report for Tech Leaders, technical report, 23 August 2023. Available online at https://news.sophos.com/en-us/2023/08/23/active-adversary-for-tech-leaders/.
New Release of Security Onion
Many of us are running a security operations center on a tight budget, and a favourite tool is Security Onion, an open-source SOC platform which has had over 2 million downloads. Security Onion integrates well with the Elastic stack, and offers signature-based detection via Suricata, protocol metadata and file extraction using Zeek or Suricata, packet capture via Stenographer and file analysis via Strelka.
The preview version 2.4 Security Onion Console has a number of new features:
- add a value directly from a record in Hunt, Dashboards, or Alerts as an observable to an existing or new case
- a new DNS lookup capability
- pivots for relational operators on numbers
- Cases support dynamic observable extraction
- import of PCAP and EVTX files
Among the many new admin features in the SOC Administration interface:
- user management
- a new Grid Members Interface to manage adding and removing nodes
- Configuration interface for most aspects of deployment
- Grid interface has been improved to show more status information about your nodes
- a simplified installer
- new members of the grid are now configured in the Grid Members interface
- SOC authentication has been upgraded to include additional authentication protections, such as rate-limiting login requests and support has been added for passwordless login via Webauthn
In addition, the ISO image has been updated from the aging CentOS 7 to Oracle Linux 9. Security Onion is available at https://github.com/Security-Onion-Solutions/securityonion, and the 2.4.10 release can be found at https://github.com/Security-Onion-Solutions/securityonion/blob/2.4/main/DOWNLOAD_AND_VERIFY_ISO.md.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
Lapsus$ Hacker Finds Out
As we reported back in September last year, a Oxfordshire teenager was arrested on suspicion of being a key player in attacks on Rockstar Games and Uber. The teenager, now 18, has been identified as Arion Kurtaj, a key member of the Lapsus$ ransomware gang who, along with other teenagers in the UK and Brazil, conducted social engineering and more technical lateral movement exploits in extortion attacks on Rockstar, Uber, Microsoft, BT, Nvidia and Cisco, among others. Along with another 17-year-old (who is still 17, and therefore cannot be named), Kurtaj was charged with counts of blackmail, fraud and offences under the UK's Computer Misuse Act.
Back in July, psychiatrists assessed Kurtaj as autistic and deemed him not fit to stand trial; however, a trial of the other teenager was commenced, during which the jury was asked to determine whether or not he had done the acts alleged, but not whether he did them with criminal intent. They found that he had. The other teenager was found guilty.
Both defendants were unable to resist the temptation to engage in cybercrime. Despite being arrested in January 2022, upon their release they breached Nvidia's systems, using a hired accomplice to call the company's help desk to obtain credentials. They also used MFA push fatigue attacks in order to get employees to verify their logins. They were re-arrested in late March 2022, but upon his release, Kurtaj broke his bail conditions by going online again - in fact, a few weeks after the City of London Police arrested and then released him, he accessed that police force's cloud storage.
So effective were the teenagers that the US DHS ordered its Cyber Safety Review Board to examine and report upon their attacks; their report was released earlier this month, with a number of key recommendations, including a move away from voice and SMS-based MFA in favour of phishing-resistant FIDO-compliant MFA methods.
The teenagers' alleged Brazilian accomplice was arrested in October and will doubtless stand trial in that jurisdiction. Despite the fact that Kurtaj was not fit to stand trial, and did not give evidence, he is remanded in custody and both he and the unnamed teenager will be sentenced by Her Honour Judge Lees at Southwark Crown Court at a later date.
City of London Police, On the evening of Thursday 22 September ..., tweet, 23 September 2022. Available online at https://twitter.com/CityPolice/status/1573281533665972225.
Tidy, Joe, Lapsus$: Court finds teenagers carried out hacking spree, BBC News, 23 August 2023. Available online at https://www.bbc.com/news/technology-66549159.Uncredited, Cisco Talos shares insights related to recent cyber attack on Cisco, blog post, 11 September 2022. Available online at https://blog.talosintelligence.com/2022/08/recent-cyber-attack.html.
Cyber Safety Review Board, Review of the Attacks Associated with Lapsus$ and Related Threat Groups, technical report, 24 July 2023. Available online at https://www.cisa.gov/resources-tools/resources/review-attacks-associated-lapsus-and-related-threat-groups-report.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
Infostealer Masquerades as MacOS App
The XLoader malware-as-a-service infostealer has existed in various forms since around 2015, targeting primarily Windows systems. Although a MacOS variant appeared in 2021, it was written as a Java program - and since most Macs no longer supported the Java Runtime Environment (JRE) as standard, its impact was highly limited.
But now a new variant has emerged, say SentinelOne researchers, this time written in the C and Objective C programming languages, compiled down to a native binary, and masquerading as an office productivity application called 'OfficeNote'. This app bundled inside a standard Apple disk image file under the name OfficeNote.dmg, signed on 17 July 2023 with the developer signature MAIT JAKHU (54YDV8NU9C).
Apple has subsequently revoked this developer key, but tests by the SentinelOne researchers indicate that the Apple malware blocker, XProtect, does not have a signature to protect against this malware, as of 21 August, and uploads to VirusTotal indicates that it spread quite widely during July. Its developers are offering this Mac version of XLoader for rent at rates of $US199/month or $US399/3 months - high in comparison with the Windows variants.
If invoked by a victim, the promised 'OfficeNote' fails to run, but in the background the malware drops and runs its payload, creating a hidden directory containing the malware as well as a LaunchAgent so that it will persist. Once running, it attempts to steal secrets from the user's clipboard as well as the Chrome and Firefox browsers, but does not target Safari. It also contacts its C2 server, hiding the server's IP address among hundreds of dummy network requests. It also uses a variety of other detection evasion techniques, such as sleeping for some time before executing malicious behaviour, and using stripped binaries to make static analysis harder.
The SentinelOne blog post contains a detailed analysis and IOC's.
Devadoss, Dinesh and Phil Stokes, XLoader’s Latest Trick | New macOS Variant Disguised as Signed OfficeNote App, blog post, 21 August 2023. Available online at https://www.sentinelone.com/blog/xloaders-latest-trick-new-macos-variant-disguised-as-signed-officenote-app/.
RCE Vulnerability Affects Ivanti Sentry
Researchers at Norwegian security firm mnemonic have discovered a zero-day vulnerability in Ivanti Sentry (formerly MobileIron Sentry), a secure gateway for mobile devices accessing corporate networks. The vulnerability, CVE-2023-38035, allows an unauthenticated threat actor to both read and write files to the Sentry server, and execute OS commands with root privileges via sudo.
The vulnerability is in some API endpoints in the Sentry server's System Manager Portal (commonly known as MICS [MobileIron Configuration Service]), which normally runs on port 8443. If this is not exposed to the Internet, a threat actor will have to have internal access. However, this can be acquired by compromising the Ivanti Endpoint Manager Mobile (EPMM), as this communicates with the Sentry server using port 8443 - and the EPMM server may be exploited via CVE-2023-35078 and CVE-2023-35081 - an authentication bypass and directory traversal vulnerabilities which have previously been exploited in the wild.
Ivanti has issued RPM packages which update currently supported versions of Ivanti Sentry.
Not entirely coincidentally, the US Cybersecurity & Infrastructure Security Agency has added this vulnerability as one of two new entries in its Known Exploited Vulnerabilities Catalog - the other is CVE-2023-27532, a missing authentication for critical function vulnerability in Veeam Backup & Replication Cloud Connect.
mnemonic, Threat Advisory: Remote Code Execution (RCE) vulnerability in Ivanti Sentry (CVE-2023-38035), blog post, 21 August 2023. Available online at https://www.mnemonic.io/resources/blog/threat-advisory-remote-code-execution-vulnerability-in-ivanti-sentry/.
Ivanti, CVE-2023-38035 - Vulnerability affecting Ivanti Sentry, blog post, 21 August 2023. Available online at https://www.ivanti.com/blog/cve-2023-38035-vulnerability-affecting-ivanti-sentry.
Ivanti, CVE-2023-38035 – API Authentication Bypass on Sentry Administrator Interface, forum post, 21 August 2023. Available online at https://forums.ivanti.com/s/article/CVE-2023-38035-API-Authentication-Bypass-on-Sentry-Administrator-Interface?language=en_US.
CISA, CISA Adds Two Known Exploited Vulnerabilities to Catalog, cybersecurity advisory, 22 August 2023. Available online at https://www.cisa.gov/news-events/alerts/2023/08/22/cisa-adds-two-known-exploited-vulnerabilities-catalog.
Telemarketer Breached; Charity Donor Details Published on Dark Web
An April attack on a Brisbane telemarketing firm, Pareto Phone, has culminated with the dark web publication of the personal information of thousands of donors to charities which used the firm. The breach has been notified to the National Cyber Security Coordinator, but it is not clear whether the Office of the Australian Information Commissioner has been notified - and if so, within the required notification period of 30 days.
The firm has been used by a number of charities, including the Cancer Council and Canteen, which supports young people with cancer, and who reported that 2,600 current and former donors hade been contacted. It said information including full names, date of birth, addresses, email addresses and phone numbers had been released, but not financial information.
The Fred Hollows Foundation said that 1,700 of its donors had been affected, and further indicated that data had been held by the telemarketer long beyond its usefulness: "We worked with Pareto Phone only during 2013 and 2014. We were not aware our data was still held by them". This suggests a significant breach of the Australian Privacy Principles, which are an annex to the Privacy Act.
Burt, Jemima, Thousands of donors to Australian charities, including Cancer Council and Canteen, have data leaked to dark web, The Guardian, 23 August 2023. Available online at https://www.abc.net.au/news/2023-08-23/qld-charity-donors-dark-web-cyber-criminals-pareto-phone/102757194.
CISA, NSA, NIST Push Post-Quantum Cryptography
Once again, we are beating the drum about cryptographic agility and the need to prepare for the possibility that well-resourced - probably (but not necessarily) affiliated with nation states - threat actors develop the capability of breaking our public-key algorithms using quantum computers.
To this end, CISA, the NSA and NIST have jointly released an factsheet to alert organizations - particularly in critical infrastructure - of the possibilities and to start planning for the migration to post-quantum cryptography (PQC) standards. NIST will release a set of PQC standards in 2024, although we already know what many of the algorithms are likely to be.
The factsheet recommends preparing a post-quantum roadmap, starting with preparing a cryptographic inventory in order to identify technology which may be vulnerable to a quantum computing attack, then engaging with suppliers to ascertain their roadmaps. We need to start now, to ensure that the cybersecurity supply chain encompasses PQC.
CISA, Quantum-Readiness: Migration to Post-Quantum Cryptography, factsheet, 21 August 2023. Available online at https://www.cisa.gov/resources-tools/resources/quantum-readiness-migration-post-quantum-cryptography.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
HiatusRAT Targets Defense Contractors
Since March of this year, researchers at Lumen Black Lotus Labs have been tracking a complex campaign targeting edge routers for traffic collection, which they have dubbed "HiatusRAT". In June, HiatusRAT shifted its attention from Latin America and Europe, to focus on US a military procurement system as well as Taiwanese-based organizations, suggesting that the threat actor is serving Chinese strategic interests.
Since June, multiple new versions of the HiatusRAT malware have emerged, targeting a range of platform architectures, although curiously - and somewhat audaciously - these continue to use the same C2 servers. However, the new variants have been hosted on new VPS servers, with over 90% of connections to their addresses being made from a range of Taiwanese organizations, including semiconductor and chemical manufacturers and at least one municipal government.
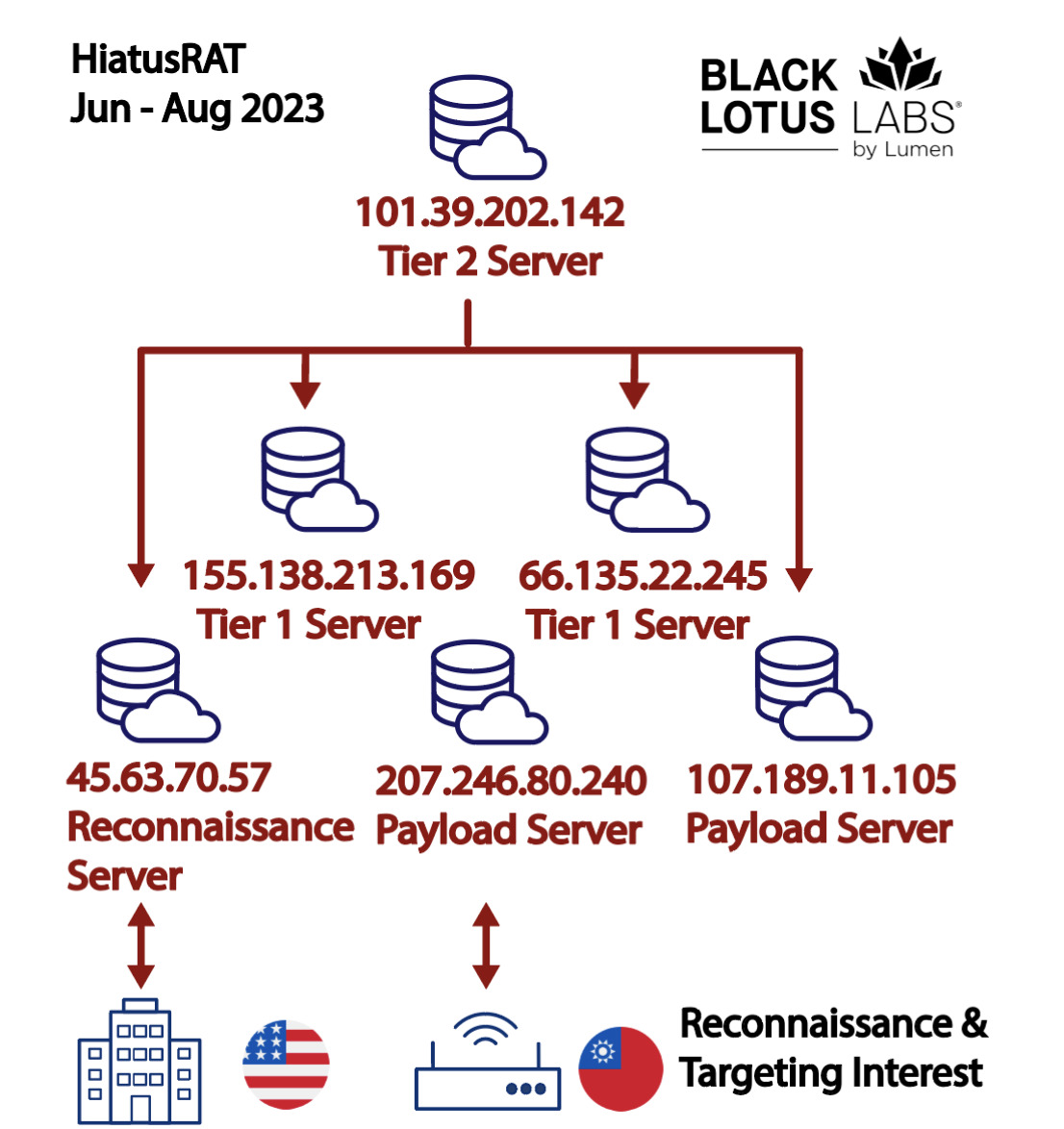
The logical connections in the new HiatusRAT network (image credit: Lumen Black Lotus Labs)
Following traffic from the distribution VPS's to upstream infrastructure, the Black Lotus Labs researchers were able to identify several new nodes in both China and the US, two of which connectd to a US Department of Defense server used for submission and retrieval of proposals for defence contracts, the traffic suggesting the threat actor was searching for publicly available information relating to defence contracts, possibly to identify defence contractors for subsequent targeting.
Black Lotus Labs, No rest for the wicked: HiatusRAT takes little time off in a return to action, blog post, 17 August 2023. Available online at https://blog.lumen.com/hiatusrat-takes-little-time-off-in-a-return-to-action/.
CISA Releases Vulnerability Summary for Week of August 14, Adds One Known Exploited Vulnerability
The US Cybersecurity & Infrastructure Security Agency has released its weekly vulnerability summary for the week of 14 August. A quick scan of just the most serious vulnerabilities - those with a CVSS 3.x score of 9.0 or above - reveals a variety of remote code execution, SQL injection, privilege escalation, missing function level access control and other vulnerabilities across a range of products including WordPress plugins, Veritas NetBackup Snapshot Manager, GitPython and various Huawei products.
CISA has also added one vulnerability to its Known Exploited Vulnerabilities Catalog - CVE-2023-26359, an Adobe ColdFusion deserialization of untrusted data vulnerability that can allow remote code execution.
CISA, Vulnerability Summary for the Week of August 14, 2023, security bulletin, 21 August 2023. Available online at https://www.cisa.gov/news-events/bulletins/sb23-233.
CISA, CISA Adds One Known Exploited Vulnerability to Catalog, cybersecurity advisory, 21 August 2023. Available online at https://www.cisa.gov/news-events/alerts/2023/08/21/cisa-adds-one-known-exploited-vulnerability-catalog.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
Juniper Releases Advisory for Multiple Vulnerabilities in Junos OS
Networking device manufacturer Juniper has released an advisory dealing with multiple vulnerabilities in Junos OS on SRX Series and EX Series. The vulnerabilities are:
- CVE-2023-36844: A PHP external variable modification vulnerability allows an unauthenticated network attacker to control some important environment variables (CVSS 3.x score: 5.3)
- CVE-2023-36845: A PHP external variable modification vulnerability allows an unauthenticated network attacker to control some important environment variables (CVSS 3.x score: 5.3)
- CVE-2023-36846: A function level access control vulnerability allows an unauthenticated network attacker to compromise filesystem integrity and upload arbitrary files (CVSS 3.x score: 5.3)
- CVE-2023-36847: A function level access control vulnerability allows an unauthenticated network attacker to compromise filesystem integrity and upload arbitrary files (CVSS 3.x score: 5.3)
Individually, these vulnerabilities aren't too bad, but when chained, they escalate to allow unauthenticated remote code execution.
The vulnerabilities affect all versions of Junos OS on SRX Series prior to 20.4R3-S8 and Junos OS on EX Series prior to version 20.4R3-S8. Admins of affected systems should either patch immediately or disable J-Web.
Juniper Networks Inc., 2023-08 Out-of-Cycle Security Bulletin: Junos OS: SRX Series and EX Series: Multiple vulnerabilities in J-Web can be combined to allow a preAuth Remote Code Execution, support article, 17 August 2023. Available online at https://supportportal.juniper.net/s/article/2023-08-Out-of-Cycle-Security-Bulletin-Junos-OS-SRX-Series-and-EX-Series-Multiple-vulnerabilities-in-J-Web-can-be-combined-to-allow-a-preAuth-Remote-Code-Execution?language=en_US.
ESET Spots Zimbra Phishing Campaign
Security researchers at ESET have reported a mass phishing campaign intended to capture user account credentials for the Zimbra freemium collaboration platform. The campaign seems to be targeting SME and government users in Poland, followed by Ecuador and Italy; the threat actor behind the campaign remains unidentified.
Campaign targets receive emails which purport to be from a mail server administrator, advising of an upcoming change to the client login page. Attached is an HTML 'preview' of the new login page - customized with the name and logo of the target organization and pre-filled with the intended victim's email address - which the recipient is lured to open. Should they naively enter their passphrase, it will be submitted, by the HTML form, to a server controlled by the attackers.
The campaign is far from sophisticated, but it is far from the first to target budget-constrained organizations using Zimbra Collaboration, suggesting that such campaigns are generally successful.
Šperka, Viktor, Mass-spreading campaign targeting Zimbra users, blog post, 17 August 2023. Available online at https://www.welivesecurity.com/en/eset-research/mass-spreading-campaign-targeting-zimbra-users/.
WinRAR Vulnerability Leads to RCE
Zero Day Initiative researcher 'goodbyeselene' has disclosed a rather nasty vulnerability, CVE-2023-40477, in the popular WinRAR file archiving utility. The vulnerability, which has a CVSS 3.x score of 7.8, is in the code for processing recovery volumes, where a buffer overflow can allow an attacker to execute code in the context of the WinRAR process.
The result is that, by crafting a malicious archive file, or perhaps by luring a victim to a malicious web page, an attacker can achieve a remote code execution attack. The vulnerability was fixed in WinRAR 6.23, which was released on 2 August 2023.
Zero Day Initiative, RARLAB WinRAR Recovery Volume Improper Validation of Array Index Remote Code Execution Vulnerability, security advisory, 17 August 2023. Available online at https://www.zerodayinitiative.com/advisories/ZDI-23-1152/.
BEC Attack Costs Home Buyers Their Life Savings
Finally, a salutary tale for those engaged in large personal purchases - which usually means cars and real estate. Business email compromise actors continue to attack these large transfers, and the results can be devastating.
A New South Wales couple were in the final stages of buying their first home, and had received an invoice from the conveyancer for the payment of their deposit. So they transferred the requested amount - and then heard nothing. When they investigated, they found that the account they had transferred their deposit to had been drained, and they had lost $A274,311.57. Their bank was able to recover only $A270.72.
“We were just emailing back and forth, and then we get an email saying, ‘This is the account you need to pay the money into’,” said the victim. “I had quite a reasonable relationship with the conveyancers. So I just didn’t think anything of it … It was getting close to completion.
“I just paid it. There was no warning to ring them before I pay.”
Unfortunately, the onus is on the customer to confirm the details of the destination bank account, and this should always be done out-of-band, by telephone or by using a funds transfer system that links the account to some other verification data.
Kelly, Cait, Gone in two transfers: the email scam that cost Australian homebuyers their life savings, The Guardian, 20 August 2023. Available online at https://www.theguardian.com/australia-news/2023/aug/20/australian-email-payment-redirection-scam.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
PowerShell Gallery Users Vulnerable to Typosquatting Attacks
The Windows PowerShell scripting language is incredibly powerful, able to hook into lots of low-level functionality in the underlying operating system, and hence is extremely popular with system administrators, as well as developers of admin tools. Of course, the same attributes make PowerShell attractive to threat actors, too, and they use PowerShell scripts in a range of attacks.
Now researchers at Aqua have drawn attention to a major vulnerability in the PowerShell software supply chain - specifically, in PowerShell Gallery, which is the major repository of PowerShell packages. PowerShell Gallery hosts thousands of packages and boasts billions of downloads - it is the first place administrators and PowerShell developers will turn to when looking for packages useful in their work. However, a lax approach to validating the names of submitted packages makes it possible for attackers to dupe victims into installing malicious packages.
Other repositories and package managers, such as npm, impose rules which prevent the creation of packages with a similar name to existing, legitimate, packages. For example, there is an existing npm package called reactnative, and as a consequence, no-one can create packages with names like react_native, react-native, react.native and so on. If they try, the server responds with a 403 Forbidden status.
There is no such checking in PowerShell Gallery. In addition, the use of periods in package names, such as the "Az." prefix for names of packages relating to Azure, is only a convention, and not a scoping rule that restricts the creation of packages within a domain. The Aqua researchers give the example of Aztable, a popular module which provides functions for manipulation of Azure Storage Tables - there is nothing to stop someone creating a module called Az.Table.
The problem is exacerbated by the fact that module creators can fake almost every detail in the landing page for their module, making it appear to be the legitimate package which they are spoofing. Determining the real author of a PowerShell module can be near-impossible.
These are not the only problems with PowerShell Gallery; the Aqua researchers also found a way to enumerate unlisted modules, including those which were hidden because they exposed secrets such as API keys. But they went on to create a proof-of-concept for a typosquatting attack, creating a fake module which would reveal when it was downloaded and deployed - and within just hours, they started receiving responses from hosts across multiple cloud services.
The researchers disclosed their findings to the Microsoft Security Resource Center in late September of 2022; however, as of 16 August 2023, the vulnerabilities seem to remain.
Weinberger, Mor, Yakir Kadkoda and Ilay Goldman, PowerHell: Active Flaws in PowerShell Gallery Expose Users to Attacks, blog post, 16 August 2023. Available online at https://blog.aquasec.com/powerhell-active-flaws-in-powershell-gallery-expose-users-to-attacks.
Citrix ShareFile Vulnerability Exploitation in the Wild
The Cybersecurity & Infrastructure Security Agency has added one vulnerability to its Known Exploited Vulnerabilities Catalog this week - CVE-2023-24489, a vulnerability in Citrix ShareFile, also known as Citrix Content Collaboration. This is a nasty one, with a CVSS 3.x base score of 9.8 (although Citrix rate it at only 9.1).
This vulnerability goes back to early June, when it was disclosed to Citrix by AssetNote researcher Dylan Pindur, who was able to use it "to achieve unauthenticated arbitrary file upload and full remote code execution by exploiting a seemingly innocuous cryptographic bug". The bug in question allows what is essentially a variant of a padding oracle attack, and Pindur's blog provides a nice potted explanation and demonstration of its operation.
ShareFile users should update to ShareFile storage zones controller 5.11.24 or later. This is especially important now that the vulnerability is being actively exploited.
Citrix, ShareFile StorageZones Controller Security Update for CVE-2023-24489, security bulletin, 13 June 2023. Available online at https://support.citrix.com/article/CTX559517/sharefile-storagezones-controller-security-update-for-cve202324489.
Pindur, Dylan, Encrypted Doesn't Mean Authenticated: ShareFile RCE (CVE-2023-24489), blog post, 4 July 2023. Available online at https://blog.assetnote.io/2023/07/04/citrix-sharefile-rce/.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
Citrix NetScaler ADC Exploitation - Almost 2,000 Machines Back-Doored
Back in mid-July, we brought you news of a Citrix security bulletin advising of patches for three significant vulnerabilities in the company's Netscaler application delivery controller. One of these, CVE-2023-3519, is a particularly nasty unauthenticated remote code execution vulnerability, with a CVSS score of 9.8 - clearly, something that should be addressed urgently.
Apparently, a large number of administrators didn't get the message, since security researchers at consulting firm Fox-IT (part of the NCC Group), working in conjunction with the Dutch Institute of Vulnerability Disclosure (DIVD), have discovered that found over 1800 Netscaler ADC's which have been backdoored. In some cases - 1,248 cases, to be precise - the CVE-2023-3519 patch had been installed, but only after an adversary had exploited the system and installed a web shell.
A campaign to exploit CVE-2023-3519 was already underway at the time that Citrix developed and released the patch, although the exact nature of the exploitation was not made public. However, a number of security firms started digging, and Mandiant released an informative blog post just a couple of days later, detailing their discovery of a small PHP web shell located in /var/vpn/themes, and just 113 bytes in size, which appeared to be a component of the initial exploitation. They also identified a number of malicious ELF binaries and a total of six different web shells on exploited Netscaler appliances.
Mandiant has also now published a scanning tool which uses a list of IOC's to identify Netscalers which have been compromised using CVE-2023-3519.
Meanwhile, Fox-IT and the DIVD had been doing similar work, and they now have released their findings. To quote their report:
Most apparent from our scanning results is the percentage of patched NetScalers that still contain a backdoor. At the time of writing, approximately 69% of the NetScalers that contain a backdoor are not vulnerable anymore to CVE-2023-3519. This indicates that while most administrators were aware of the vulnerability and have since patched their NetScalers to a non-vulnerable version, they have not been (properly) checked for signs of successful exploitation.
This illustrates a major problem with defensive patch management: by the time a patch is released, active exploitation may already be under way, especially if a patch is developed in response to reports of a 0-day attack, and it is entirely possible that admins may, in fact, be applying the patch to systems that have already been compromised. Even a short delay in patching increases the likelihood of this occurring, since once a patch is released, threat actors immediately set to work reverse-engineering it in order to develop their own exploits.
The lesson: patching is all very well, but it is also important to use other techniques, including monitoring and scanning for indicators of compromise, to ensure that systems have not been compromised.
Citrix, Citrix ADC and Citrix Gateway Security Bulletin for CVE-2023-3519, CVE-2023-3466, CVE-2023-3467, security bulletin, 18 July 2023. Available online at https://support.citrix.com/article/CTX561482/citrix-adc-and-citrix-gateway-security-bulletin-for-cve20233519-cve20233466-cve20233467.
Nugent, James et. al., Exploitation of Citrix Zero-Day by Possible Espionage Actors (CVE-2023-3519), blog post, 21 July 2023. Available online at https://www.mandiant.com/resources/blog/citrix-zero-day-espionage.
Mandiant, Indicators of Compromise Scanner for Citrix ADC Zero-Day (CVE-2023-3519), blog post, 14 August 2023. Available online at https://www.mandiant.com/resources/blog/citrix-adc-vulnerability-ioc-scanner.
Fox-IT, Approximately 2000 Citrix NetScalers backdoored in mass-exploitation campaign, blog post, 15 August 2023. Available online at https://blog.fox-it.com/2023/08/15/approximately-2000-citrix-netscalers-backdoored-in-mass-exploitation-campaign/.
NIST Drops CSF 2.0 Exploration Tool
Only yesterday, we discussed the release of the draft 2.0 version of the NIST Cybersecurity Framework (CSF) and mentioned the impending release of a reference tool which would allow browsing, searching and export of the CSF core data in both human- and machine-readable formats. A later version of the tool will provide the informative references which link to Standards and other resources.
And, right on cue, here it is:
NIST, NIST Cybersecurity Framework (CSF) 2.0 Reference Tool, August 2023. Available online at https://csrc.nist.gov/Projects/cybersecurity-framework/Filters#/csf/filters.
Google Develops Post-Quantum Security Keys
We are strong proponents of the use of FIDO U2F security keys as the strongest variant of multi-factor authentication, and personally use them whenever possible. The only looming cloud on the horizon is the ever-more-likely possible development of an attack, using a quantum computer, on the public-key cryptographic algorithms the security keys use. Someone may already have achieved this - if they have, they certainly would not disclose it!
So we continually track developments in post-quantum cryptography (PQC) and the cryptographic agility which prepares us to switch to post-quantum algorithms when the time comes. Now Google has announced an important next step with their development and release of a quantum resilient FIDO2 security key implementation as part of OpenSK, their open source security key firmware.
This implementation is optimized for the tightly constrained hardware of a typical security key. Written in Rust, it requires only 20 KB of memory and performs acceptably, although hardware acceleration could speed it further. It uses a hybrid approach, combining the elliptic curve DSA (ECDSA) signature algorithm with the recently standardized Dilithium quantum resistant signature algorithm.
Burzstein, Elie and Fabian Kaczmarczyck, Toward Quantum Resilient Security Keys, blog post, 15 August 2023. Available online at https://security.googleblog.com/2023/08/toward-quantum-resilient-security-keys.html.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.