Les Bell
Blog entry by Les Bell
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
Google Shows Benefits of Memory Safe Languages
Operating systems and high-performance applications (especially for low-powered devices) have traditionally been written in the C and C++ programming languages, which suffer from problems with safe memory management. C, in particular, relies on the programmer correctly matching malloc() (and similar) function calls, which allocate memory blocks, with the corresponding free() calls - something that is particularly tricky in interrupt-driven and multi-threaded code. Forgetting to call free() results in memory leaks and swap file growth, while calling free() more than once on the same pointer will corrupt the heap (or the equivalent structure in the underlying OS). Worse still are use-after-free vulnerabilities - and we haven't yet mentioned buffer overflows, which are probably the most exploited class of vulnerabilities over many decades.
Yet memory-safe languages - Pascal, Ada, Java and others - have been available for decades and only resisted on grounds of efficiency. The most recent and most efficient examples, like Kotlin and Rust, have arrived at a time when processors are so powerful that efficiency is no longer a problem, and so support for Rust is being introduced into the Linux kernel and has already been introduced into the Android mobile OS.
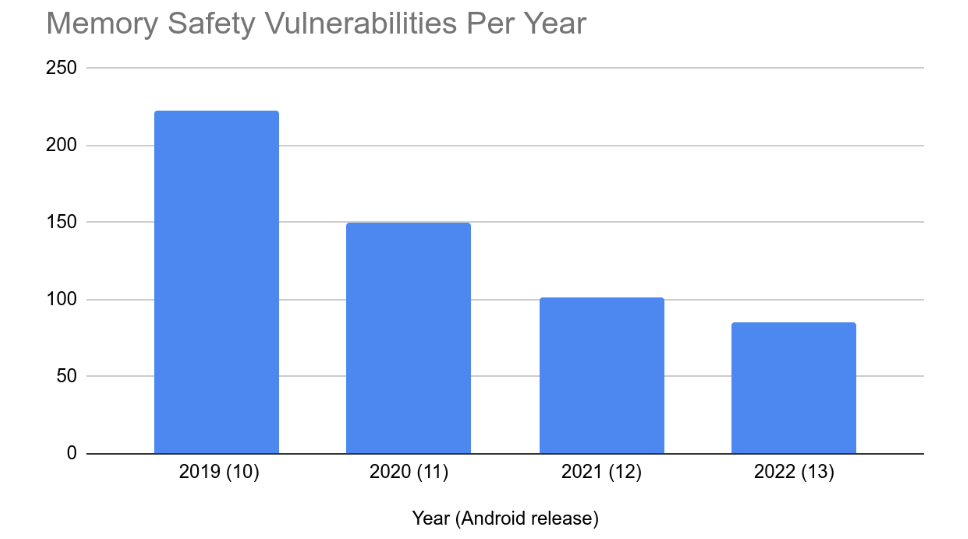 In a blog post, Google provides statistics that show how the introduction of memory-safe languages into Android has dramatically reduced that class of vulnerability. From 2019 to 2022 the annual number of reported memory safety vulnerabilities has gone from 223 down to just 85. It's no coincidence that 2022's Android 13 is the first release where most new code is in a memory safe language, and that 2022 is the first year where the majority of vulnerabilities do not relate to memory safety.
In a blog post, Google provides statistics that show how the introduction of memory-safe languages into Android has dramatically reduced that class of vulnerability. From 2019 to 2022 the annual number of reported memory safety vulnerabilities has gone from 223 down to just 85. It's no coincidence that 2022's Android 13 is the first release where most new code is in a memory safe language, and that 2022 is the first year where the majority of vulnerabilities do not relate to memory safety.
This is good for security; to date, there have been no memory safety vulnerabilities discovered in Android's Rust code.
Of course, this change is not the only contributor to reducing vulnerabilities in Android; the existing C/C++ is being hardened using a variety of tools, although the fact that most of Andoid's API's are implemented in Java also helps. The Google blog post provides some useful ammunition for developers who want to persuade their shops to migrate to memory-safe languages.
Vander Stoep, Jeffrey, Memory Safe Languages in Android 13, Google Security Blog, 1 December 2022. Available online at https://security.googleblog.com/2022/12/memory-safe-languages-in-android-13.html.
CISA Warns of Cuba Ransomware
The FBI and the US Cybersecurity & Infrastructure Security Agency have issued a joint cybersecurity advisory concerning the increased activities of Cuba ransomware operators. Cuba, which is not associated with the Republic of Cuba, was first observed in 2021, and by mid-2022 its operators had compromised over 100 entities worldwide, demanding over $US145 million in ransom payments, of which $US60 million was paid.
Their primary targets are the financial services, government, healthcare, manufacturing and IT sectors, mostly in the US, and their tactics, techniques and procedures have continued to evolve, exploiting new vulnerabilities for initial compromise and then using a variety of tools for privilege escalation. There also seems to be a link between the Cuba threat actors, the Industrial Spy ransomware and the operators of the RomCom remote access trojan, with the Cuba group selling data exfilatrated by their ransomware via Industrial Spy's online market and also deploying the RomCom RAT.
The CISA advisory provides a complete rundown, including IOC's and MITRE ATT&CK techniques.
Uncredited, #StopRansomware: Cuba Ransomware, cybersecurity advisory alert AAA22-335A, 1 December 2022. Available online at https://www.cisa.gov/uscert/ncas/alerts/aa22-335a.
Android Trojan Steals Facebook Logins
While Android security continues to improve (see above), the mobile OS still has its unfair share of trojaned apps which are being disseminated through the Google Play Store as well as stores which permit side-loaded apps. Zimperium zLabs has documented a long-running Android threat campaign, dubbed the Schoolyard Bully Trojan, which has spread to over 300,000 victims, stealing their Facebook credentials.
Disguised as legitimate educational applications providing books on a range of topics, primarily for Vietnamese readers, these apps are trojaned with a Facebook-specific infostealer, grabbing the victims' email, phone number, password, name and Facebook ID. In many cases, naive users re-use the same password for both Facebook and also for financial accounts, making this campaign even more profitable. Despite the Vietnamese language focus, Zimperium found over 300,000 victims across 71 countries.
The campaign's techniques are also interestinmg - the credential theft is achieved via JavaScript injection; the legitimate Facebook login URL has additional, injected, code which extracts the user's credentials and then sends it to the threat actor's Firebase C2 site. The malware also uses native libraries as an evasion technique, getting past the majority of antivirus products, including those which use machine learning, and it encodes the exfiltrated data to hide it from detection mechanisms.
Gupta, Nipun, Schoolyard Bully Trojan Facebook Credential Stealer, blog post, 1 December 2022. Available online at https://www.zimperium.com/blog/schoolyard-bully-trojan-facebook-credential-stealer/.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.