Les Bell
Blog entry by Les Bell
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
KeePass Vulnerability Allows Plaintext Export of Entire Password Database
Many security professionals use the KeePass open-source password manager - it is free, lightweight and versatile, while not exposing a large attack surface. However, a newly-revealed vulnerability (CVE-2023-24055) suggests that some caution might be necessary, at least until a fix or workaround appears.
KeePass is configured by the KeePass.config.xml file in the program directory. If an attacker can edit this file, they can add a trigger which will export the password database when it is initially opened, without the user being asked to confirm this - it will happen invisibly in the background. The view of the KeePass developers is that if an attacker has that level of access to the machine, it is game over already - but our view is that this represents a significant privilege escalation which will gain the attacker access to many other systems.
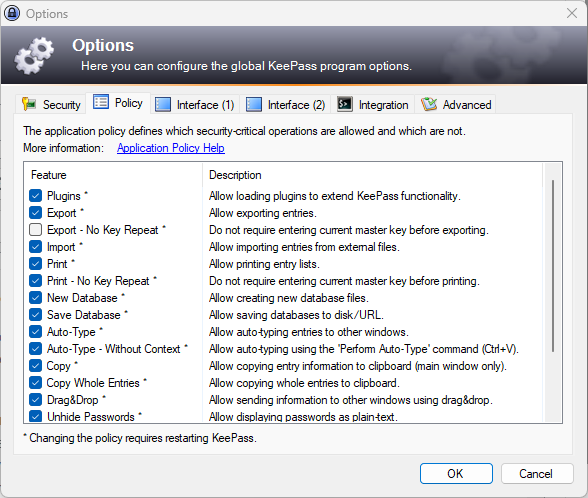
One suggestion is to use "Tools" -> "Options" -> "Policy" and then deselect "Export - No Key Repeat", but the same argument makes this suggestion moot: an attacker who has that level of access to the machine can disable that setting and execute the attack. Perhaps the best approach for the time being, especially for those who must allow others access to a shared system, is to run the Portable version of KeePass off a USB key. A write-protected KeePass.config.enforced.xml file is another option. But in all these cases, a sophisticated attack can bypass these measures.
With PoC code now available, expect a KeePass database export feature to be added to many infostealers.
Chris, If an attacker modifies the xml config file . . ., discussion thread, 28 December 2022. Available online at https://sourceforge.net/p/keepass/discussion/329220/thread/a146e5cf6b/.
QNAP Pushes Update to Fix SQL Injection Remote Code Execution Vulnerability
NAS vendor QNAP has warned customers to update their devices' firmware in order to fix a critical remote code execution vulnerability (CVE-2022-27596). The vulnerability, which has a CVSS 3.1 score of 9.8, seems to relate to improper sanitization of special elements in SQL (CWE-89).
Users are urged to update to QTS 5.0.1.2234 build 20221201 or later (5.0.1.2248 seems to be current) or QuTS hero h5.0.1.2248 build 20221215 or later. Most users who have automatic firmware update checks enabled and log in to their devices regularly will already have updated, so this is mainly a reminder for those who let the months go by, lulled into a tranquil state by the reliability of NAS devices in typical SME settings.
Uncredited, Vulnerability in QTS and QuTS hero, security advisory, 30 January 2023. Available online at https://www.qnap.com/en/security-advisory/qsa-23-01.
Microsoft Reminds Sleepy Exchange Admins: Patch!
In a similar vein, Microsoft's Exchange Team has blogged, reminding admins that it is critical to keep Exchange servers updated; this shouldn't really be necessary, as Exchange has proved to be fertile ground for attackers in recent years - remember ProxyShell, ProxyNotShell, ProxyOracle and all the rest? - and Exchange admins really ought to be in a permanently paranoid and jittery state.
As Redmond's reminder points out, this means installing the latest available Cumulative Update (CU) and Security Update (SU) on all Exchange servers as well as on Exchange Management Tools workstations. The problem is that email access is so critical in an always-connected, 24 x 7 x 52 world that admins find it hard to schedule even brief downtime.
Additional Exchange controls are a good idea, including enabling Windows Extended Protection, which mitigates MitM attacks, as well as enabling certificate signing of PowerShell serialization payloads. Attackers love to use PowerShell in Exchange attacks, especially for exploiting Active Directory. The blog post provides lots of other useful tips.
The Exchange Team, Protect Your Exchange Servers, blog post, 26 January 2023. Available online at https://techcommunity.microsoft.com/t5/exchange-team-blog/protect-your-exchange-servers/ba-p/3726001.
MD5 Lives On To Bite Samba Users
An interesting article by Paul Ducklin for Sophos' Naked Security blog makes a plea for cryptographic agility - the somewhat obvious idea that we must be willing to abandon old cryptoprimitives as the prove weak. This is an especially important notion given the possibility that someone, somewhere - who will never let on that they have it, for obvious reasons - builds a quantum computer that is able to break the most popular public-key cryptoprimitives.
That day does not seem to be upon us quite yet, but older algorithms are vulnerable to attacks using classical computer hardware, especially GPU's, and a leading example is the birthday paradox attack on the older hash algorithms, such as MD5. The complexity of a birthday paradox attack is \(2^{n/2}\) operations, where \(n\) is the length of the digest, in bits.
Now, MD5 produces a 128-bit digest, which means that a birthday paradox attack can be achieved in only \(2^{64}\) - or approximately \(1.85 \times 10^{19}\) - attempts. This might seem like a large number, but it's not - and it can be cut down massively using a technique called a chosen-prefix collision, which works by making slight changes to initially-identical strings to quickly find two different strings which still produce the same digest value. This process takes only seconds.
Some authentication code in Samba is a holdover from the days of Windows 2000, when Microsoft introduced the use of RC4 encryption with an MD5 HMAC (hash-based message authentication code). The vulnerability arises from the use of a single round of MD5 to compute a digest over the data to be authenticated before calculating the HMAC over that; an attacker who knows the plaintext data can create another set of plaintext which will generate the same digest value, and insert that into the data stream without being detected. Somebody probably inserted this extra digest calculation in an attempt to improve authentication security, not realising that it actually weakened the protocol.
Since most systems have this old HMAC-MD5 authentication disabled, it was never detected as a serious problem, but attackers could negotiate the authentication protocol down and make use of this - hence CVE-2022-38023, which was fixed by Microsoft in November last year, and which could allow an attacker to insert malicious packets into the SMB protocol and achieve a privilege escalation attack. The whole sad tale is a lesson that keeping old versions of protocols around for backward compatibility can lead to disaster (which is why it is so important to configure web servers to not allow the older versions of the TLS and SSL protocols).
Ducklin, Paul, Serious Security: The Samba logon bug caused by outdated crypto, blog post, 30 January 2023. Available online at https://nakedsecurity.sophos.com/2023/01/30/serious-security-the-samba-logon-bug-caused-by-outdated-crypto/.
Stevens, Marc, Arjen Lenstra and Benne de Weger, Vulnerability of software
integrity and code signing applications to chosen-prefix collisions for
MD5, web page, 30 November 2007. Available online at https://www.win.tue.nl/hashclash/SoftIntCodeSign/.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.