Les Bell
Blog entry by Les Bell
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
Reddit Breached; Basic MFA Not Much Help
The big news of the weekend was the breach of internal systems at Reddit by an as-yet-unidentified attacker. According to the site, the initial access mechanism was "a sophisticated and highly-targeted phishing attack". However, they then go on to say,
As in most phishing campaigns, the attacker sent out plausible-sounding prompts pointing employees to a website that cloned the behavior of our intranet gateway, in an attempt to steal credentials and second-factor tokens.
In other words, this was a proxy or man-in-the-middle attack which captured a user's password and 2FA token of some kind. They go on to say,
Soon after being phished, the affected employee self-reported, and the Security team responded quickly, removing the infiltrator’s access and commencing an internal investigation. Similar phishing attacks have been recently reported. We’re continuing to investigate and monitor the situation closely and working with our employees to fortify our security skills. As we all know, the human is often the weakest part of the security chain.
Aye, and there's the rub. In this case, the use of a second factor did not prevent the breach, and what detected it was the humble Mark I human eyeball. This illustrates the continued importance of security education, training and awareness; MFA products alone will not solve the problem. Security is a process, not a product.
Reddit's incident disclosure provides the usual advice: set up MFA (yes), change your password frequently (not such a good idea - it leads to weak passwords) and use a password manager (yes). However, I think security architects and developers need to pick up some of the load by a) providing more contextual information and clues in login dialogs, to alert users to spoofing, and b) moving to cryptographic techniques that can detect MitM attacks, like SSH and TLS can.
Fortunately for Reddit and Redditors, only limited data was exfiltrated, and there is nothing - so far - to suggest that users' personal data or credentials have been compromised.
After successfully obtaining a single employee’s credentials, the attacker gained access to some internal docs, code, as well as some internal dashboards and business systems. We show no indications of breach of our primary production systems (the parts of our stack that run Reddit and store the majority of our data).
So far.
u/KeyserSosa, We had a security incident. Here's what we know., Reddit post, 10 February 2023. Available online at https://www.reddit.com/r/reddit/comments/10y427y/we_had_a_security_incident_heres_what_we_know/.
Romance Scammers Analyzed
This is not really enterprise infosec - but it's a conversational morsel that can be used to open that conversation with employees. Remember, employees may not be strongly vested in protecting corporate data - but they have a strong interest in privacy which can cause their ears to prick up. And having talked about ways to spot a romance scammer, you could move the conversation on - to the clues that signal a phishing attack.
The US Federal Trade Commission has released a fascinating article in their Data Spotlight series, this time dealing with romance scammers, and in particular, their favourite lies. The statistics are quite staggering: in 2022, nearly 70,000 people reported a romance scam, and reported losses totaled $US1.3 billion - and that's just in the US alone. The median reported loss was $US4,400, but some will obviously be much higher, and it's worth reflecting that an employee under the pressure of financial loss may turn to fraud or larceny - yet another reason to cover this in security awareness sessions.
The scammers have developed a short list of buttons they can push to get their payout, and the article lists the most popular:
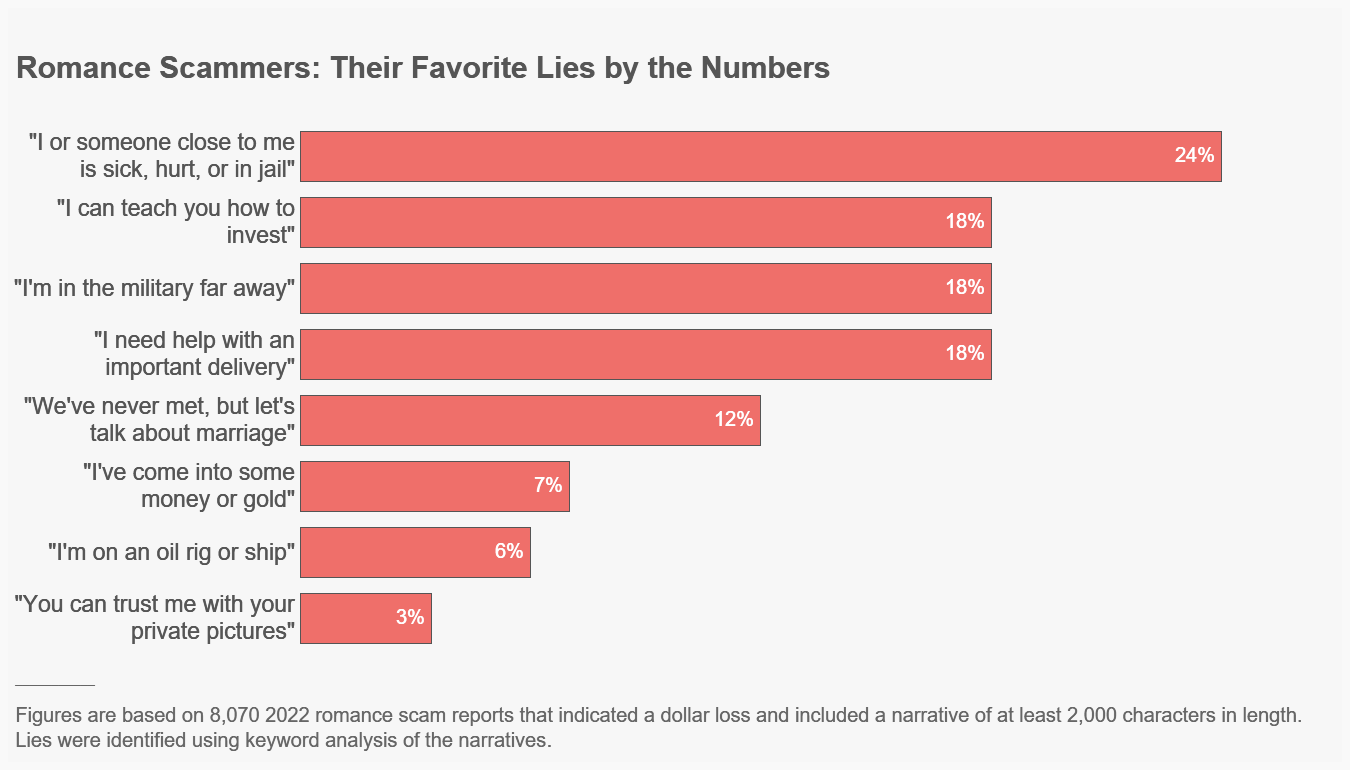
Of course, the scammers also need a way - preferably a non-reversible way - to transfer their ill-gotten gains. Gift cards are a perennial favourite, but for larger amounts, cryptocurrencies are now the method of choice, followed by bank wire transfers:
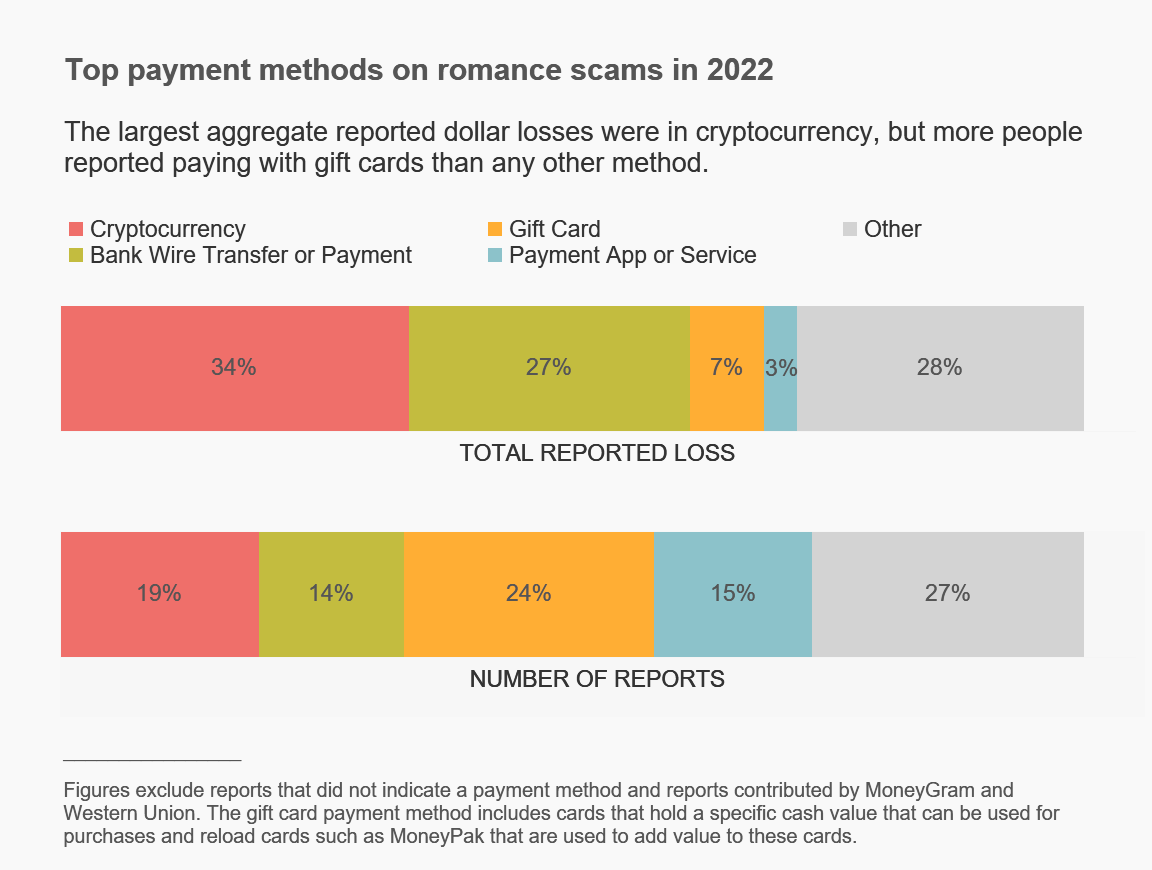
The FTC article contains a lot of other clues; this could easily be worked up into an internal newsletter piece or even a 'lunch-and-learn' session.
Fletcher, Emma, Romance scammers' favorite lies exposed, blog post, 9 February 2023. Available online at https://www.ftc.gov/news-events/data-visualizations/data-spotlight/2023/02/romance-scammers-favorite-lies-exposed.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.