Les Bell
Blog entry by Les Bell
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
HardBit 2.0 Ransomware Wants to Know About Your Cyber Insurance
Since first appearing in October of last year, the HardBit ransomware has evolved rapidy, with the latest variant, HardBit 2.0, exhibiting some interesting characteristics, according to security firm Varonis.
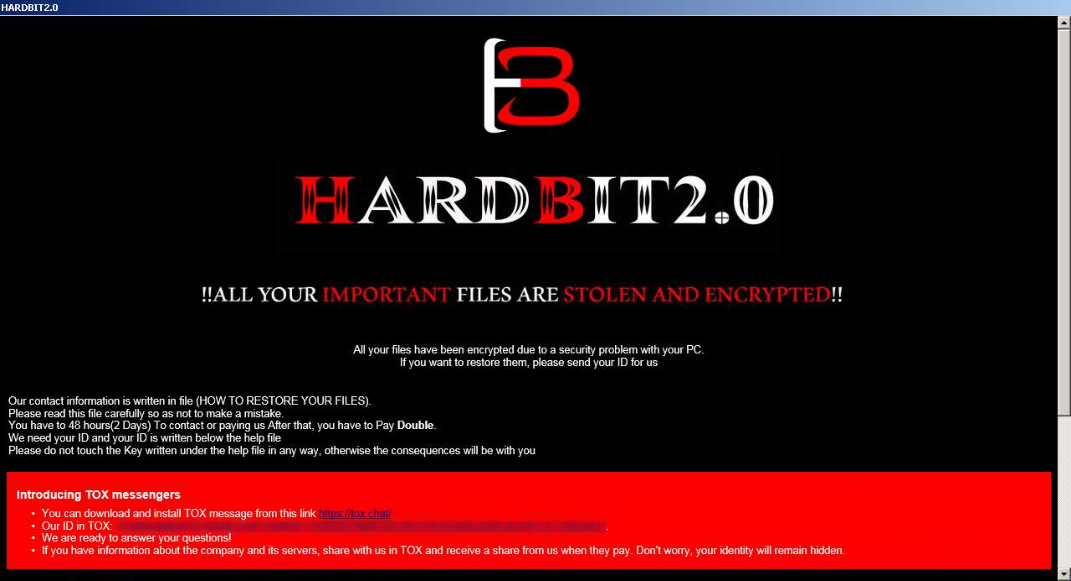
The HardBit ransom note (Varonis)
In many respects, HardBit 2.0 is conventional; after initial infection - the exact mechanism is unknown; possibly an initial access broker is involved - it does the usual things: first, it gathers system information via the Windows Management Instrumentation API, then it disables the Volume Shadow Copy Service (VSS) and deletes any shadow copies. Next, it disables a list of Windows Defender Antivirus features so it can get to work uninterrupted. It also disables up to 86 different services, including backup and recovery tools and security programs, and also persists by copying itself into the Startup folder.
It then sets about the in-situ encryption of target files, finally changing the desktop to a ransom note image and displaying the main ransom note from a .hta file.
What makes HardBit 2.0 particularly interesting is that while it threatens to release sensitive data, its operators do not seem to have a leak site. Another wrinkle is the lack of a fixed ransom amount: instead asking for details of the victim's cyber insurance coverage. In an attempt to paint insurance companies as the bad guys, the ransom note states:
"Insurance companies require you to keep your insurance information secret, this is to never pay the maximum amount specified in the contract or to pay nothing at all, disrupting negotiations.
"The insurance company will try to derail negotiations in any way they can so that they can later argue that you will be denied coverage because your insurance does not cover the ransom amount."
In practice, insurers are generally felt to have a distorting effect in the ransomware market because of their willingness to pay ransom demands, rather than covering any loss and/or costs of recovery. It's possible the HardBit 2.0 operators want to know when they are onto a sure thing.
The Varonis blog post provides a comprehensive analysis, including indicators of compromise.
Hill, Jason, HardBit 2.0 Ransomware, blog post, 20 February 2023. Available online at https://www.varonis.com/blog/hardbit-2.0-ransomware.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.