Les Bell
Blog entry by Les Bell
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
Record DDoS Attack Reaches 900 Gbps
DDoS (Distributed Denial of Service) attacks continue to grow in intensity as botnet operators add more compromised systems to their networks. Now Akamai reports a record-breaking DDoS attack - the largest ever launched against one of their customers in the Asia-Pacific (APAC) region, with the attack traffic peaking at 900.1 gigbits per scond and 158.2 million packets per second. The attack was not just intense, but was also short-lived, sustaining the peak for less than a minute and with the overall attack lasting just a few minutes.
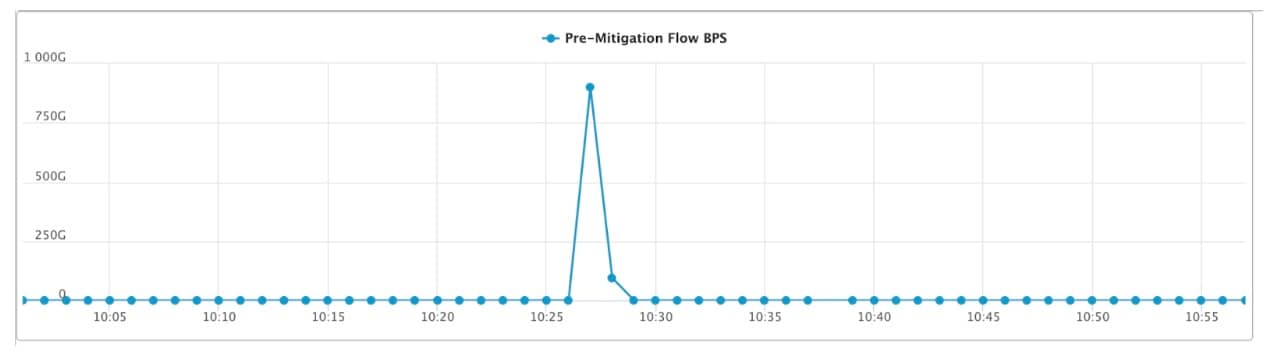
(Credit: Akamai)
The attack was distributed across all 26 of Akamai's scrubbing centers, although Hong Kong, Tokyo, São Paulo, Singapore, and Osaka saw the most traffic. 48% of the traffic was in-region. Akamai reports that, thanks to its proactive DDoS capabilities, there was no collateral damage.
Sparling, Craig, Akamai Mitigates Record DDoS Attack in Asia-Pacific (900 GBps), blog post, 8 March 2023. Available online at https://www.akamai.com/blog/security/record-breaking-ddos-in-apac.
APT Targets SonicWall Appliances
Firewalls are particularly attractive targets for threat actors; after all, compromising a firewall opens up the possibility of many new attacks on the network the firewall is defending, and there's also an opportunity to capture all kinds of useful traffic flowing through the firewall to and from a network the attacker cannot yet reach. Firewalls therefore have to be treated as bastion hosts and staunchly defended against attack - they are absolutely not a set-and-forget "solution" (I hate that word!).
An example of this is a campaign recently identified by Mandiant, working in partnership with SonicWall's Product Security and Incident Response Team (PSIRT). Analysis of a compromised machine revealed a number of malware files which give the attacker highly privileged access to the appliance, as well as allowing long-term persistence. The files mostly consist of bash scripts, along with one ELF executable which is a variant of the TinyShell backdoor.
| Path | Hash | Function |
|---|---|---|
| /bin/firewalld | e4117b17e3d14fe64f45750be71dbaa6 | Main malware process |
| /bin/httpsd | 2d57bcb8351cf2b57c4fd2d1bb8f862e | TinyShell backdoor |
| /etc/rc.d/rc.local | 559b9ae2a578e1258e80c45a5794c071 | Boot persistence for firewalld |
| /bin/iptabled | 8dbf1effa7bc94fc0b9b4ce83dfce2e6 | Redundant main malware process |
| /bin/geoBotnetd | 619769d3d40a3c28ec83832ca521f521 | Firmware backdoor script |
| /bin/ifconfig6 | fa1bf2e427b2defffd573854c35d4919 | Graceful shutdown script |
The main malware script, /bin/firewalld, starts by executing the TinyShell backdoor with command-line arguments that get it to create a reverse or 'shovel-back' shell which connects outwards to the attacker's C2 server at a specific date/time. From there, it scans every file on the system, likely to perform credential theft, executing SQL commands on the sqlite3 database /tmp/temp.db (which contains session information including hashed credentials) and also executing other components. The /bin/firewalld script is started by /etc/rc.d/rc.local in the event of a reboot.
/bin/iptabled is essentially the same script, presumably in order to provide a degree of resilience. The two scripts each check to see if the other is running, and starts it if it is not. You will notice the innocuous filenames here - these are exactly the kind of filenames you would expect to see on a firewall machine - although not in these locations.
However, a firmware update could overwrite these files. In order to avoid that, the /bin/geoBotnetd script checks every ten seconds for a new firmware upgrade to appear at /cf/FIRMWARE/NEW/INITRD.GZ, and if it does, effectively re-packages it to contain the malware scripts, ready for installation. Finally, the main malware script also modifies the main SonicWall binary firebased to call the /bin/ifconfig6 script on shutdown - this simply brings the eth0 network interface down, sleeps for 90 seconds and then shuts the system down as it normally would. Presumably this is a quick fix for some problem the attackers encountered.
The techniques used in this campaign are similar to those used in previous attacks by Chinese threat actors on Pulse Secure VPN devices as well as attacks on Fortinet devices. For this reason, Mandiant suspects a Chinese threat actor, which it currently tracks as UNC4540, is behind this campaign.
Lee, Daniel, Stephen Eckels and Ben Read, Suspected Chinese Campaign to Persist on SonicWall Devices, Highlights Importance of Monitoring Edge Devices, blog post, 8 March 2023. Available online at https://www.mandiant.com/resources/blog/suspected-chinese-persist-sonicwall.
Tips on Avoiding LDAP Injection Attacks
LDAP - the Lightweight Directory Access Protocol - is often used as part of authentication by web applications, especially for single sign-on across disparate applications. This makes LDAP injection - a close relative of the better known SQL injection - an attractive technique for attackers; they can use it to enumerate user accounts or credentials, log in without a valid password or even perform privilege escalation attacks.
A nicely-written short blog post from Trend Micro gives a brief rundown with examples of LDAP injection techniques, as well as advice on mitigation.
Trend Micro DevOps Resource Center, How to Avoid LDAP Injection Attacks, blog post, 9 March 2023. Available online at https://www.trendmicro.com/en_us/devops/23/c/avoid-ldap-injection-attacks.html.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.