Les Bell
Blog entry by Les Bell
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
Careful What You Ask For
Honestly, you just can't trust anyone these days. In a lovely example of this old adage, thousands of naive would-be-cybercriminals have been caught out, registering for DDoS-as-a-Service or 'booter' sites which turned out to be fakes set up by the UK's National Crime Agency.
Last week, the NCA unmasked one of the sites, replacing it with a splash page warning users that their data has been collected and law enforcement will be in touch shortly:
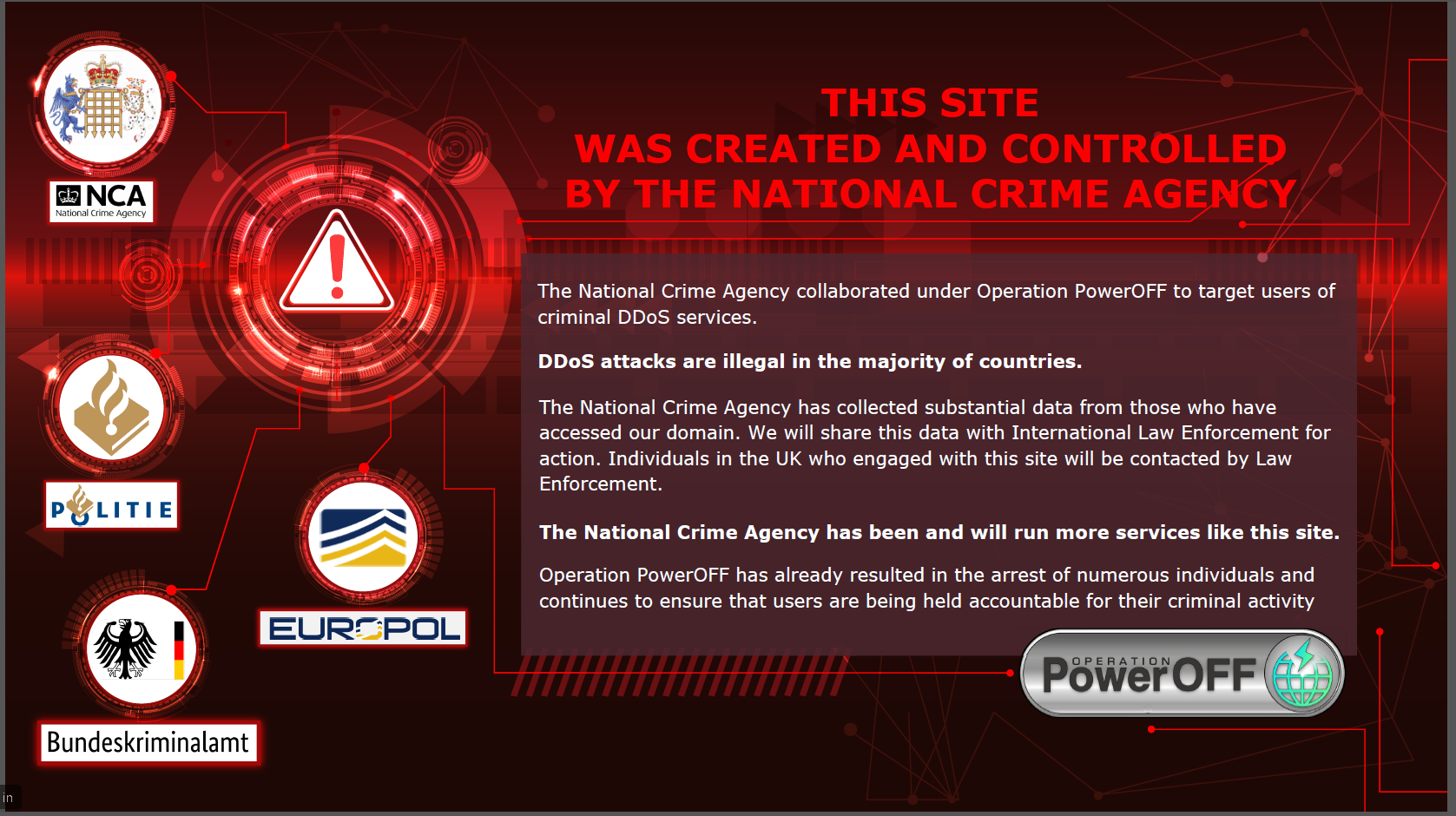
The National Crime Agency Operation PowerOff splash page (Image: National Crime Agency)
Distributed denial of service attacks are illegal in most countries - in the UK, they are covered under the Computer Misuse Act, 1990 - and while those who accessed these sites from the UK will be contacted either by the NCA or local police, details of overseas registrants will be passed to international partners including Dutch and German police.
This operation follows December's takedown of 48 of the world's most popular booter sites by the FBI in collaboration with European agencies. The NCA also arrested an 18-year-old man in Devon; he was suspected to be an administrator of one of the sites.
NCA, NCA infiltrates cyber crime market with disguised DDoS sites, news release, 24 March 2023. Available online at https://www.nationalcrimeagency.gov.uk/news/nca-infiltrates-cyber-crime-market-with-disguised-ddos-sites.
Australian Federal Police Bust Cybercrime Gang
The Australian Federal Police (AFP) has busted a sophisticated cybercrime syndicate which had allegedly performed multiple identity theft and business email compromise (BEC) attacks between January 2020 and March 2023.
The AFP investigation began in October 2021, after an Indonesian businessman lost over $A100,000 in a BEC attack. The trail they uncovered led them to two Brisbane women, a Melbourne man and an Adelaide man who had allegedly operated as a cybercrime and money-laundering syndicate with links to South Africa. The AFP alleges the syndicate orchestrated more than 15 sophisticated breaches, setting up over 80 bank accounts with stolen identities to help transfer $A1.7 million in stolen cash from Australian and overseas victims.
Apart from the BEC attacks, the syndicate allegedly also ran scams targeting Facebook Marketplace users and fraudulent superannuation investments, running about 180 bank accounts through which their victims individually lost anywhere between $A2,500 and $A500,000.
On Thursday of last week, investigators executed fives search warrants across Queensland, Victoria and South Australia, arresting 35-year and 27-year old women in the Durack and Sherwood suburbs of Brisbane, a man, 26, in Wyndham Vale, Melbourne and a man, 30, in the Adelaide suburb of Croydon Park. They also seized fake passports, international driver licences and luxury handbags - plus, of course, a number of digital devices which will be subject to forensic examination.
The accused face multiple charges, including possession of false documents, dishonestly obtaining or dealing in personal financial information, dealing in proceeds of crime worth $A100,000 or more - charges which carry a maximum penalty of 20 years imprisonment.
AFP Media, Cybercrime syndicate dismantled after allegedly laundering $1.7 million, media release, 24 March 2023. Available online at https://www.afp.gov.au/news-media/media-releases/cybercrime-syndicate-dismantled-after-allegedly-laundering-17-million.
USB Keys Explode on Insertion
We are all well aware of the potential for malware to infect a system via USB keys, which is why it is so important to have a 'found devices' policy for all employees as well as a documented procedure for dealing with them inside IT/IS departments. This usually involves investigating their contents in a constrained and untrusted environment, such as an isolated throw-away machine or a revertible VM. However, from Ecuador comes news of a new challenge for junior analysts dealing with these devices.
In mid-March journalist Lenín Artieda, at Ecuadorian television station Ecuavisa, received a USB key through the mail - which, upon being inserted into a computer, exploded. Artieda was apparently unhurt and rapidly decamped for a safer location.
However, he was not alone - another journalist, Mauricio Ayora at TC Television, also received a USB key. Fortunately his employer had a strict policy about connecting devices to computers, and set it aside until after news of the first attack broke. And at Telemazonas, journalist Milton Perez also received a USB key, this time accompanied by a note clearly intended to lure the intended victim:
"This information will unmask (Ecuadorian political movement) Correísmo . If you think it's useful, we can come to an agreement and I'll send you the second part. I will communicate with you." (translation)
This time, sheer luck saved Perez - he did not insert the drive properly and it failed to detonate. However, police later confirmed that it contained explosive material, and they performed a controlled detonation of the device sent to TC Television.
So, add to your forensic toolkit: one long-handled extension for plugging suspect USB devices into computers, and a Kevlar containment sleeve to wrap around it. Stab vest and Kevlar protection for other body parts is optional.
Cluley, Graham, Danger USB! Journalists sent exploding flash drives, Bitdefender blog, 24 March 2023. Available online at https://www.bitdefender.com/blog/hotforsecurity/danger-usb-journalists-sent-exploding-flash-drives/.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.