Les Bell
Blog entry by Les Bell
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
Open Garage Doors, Everywhere, in One Easy Step!
In an outstanding demonstration of the dangers of the Internet of Things, security researcher Sam Sabetan has disclosed a collection of critical vulnerabilities in Nexx smart devices - garage door openers, alarms and plugs - which allow remote attackers to open and close garage doors, control alarms and switch devices on and off for any and all Nexx customers.
The devices boast five different vulnerabilities:
- Use of Hard-coded Credentials; CWE-798 (CVE-2023–1748, CVSS3.0: 9.3)
- Authorization Bypass Through User-Controlled Key; CWE-639 (CVE-2023–1749, CVSS3.0: 6.5)
- Authorization Bypass Through User-Controlled Key; CWE-639 (CVE-2023–1750, CVSS3.0: 7.1)
- Improper Input Validation; CWE-20 (CVE-2023–1751, CVSS3.0: 7.5)
- Improper Authentication Validation; CWE-287 (CVE-2023–1752, CVSS3.0: 8.1)
In short, the critical issue is this: the Nexx devices use a single universal password to communicate with their controlling servers in the cloud, using the MQTT (Message Queueing Telemetry Transport) IoT messaging protocol. For applications like this, a unique password should be assigned for each device in order to achieve secure, confidential, authenticated communications.
To make matters worse, the Nexx messages are broadcast universally - i.e. to all devices - and the garageDoorOpener messages expose user emails, device ID's and contractions of user names. This allows enumeration of customer and device information, as well as simple replay attacks. And it goes on from there: the Nexx app is also vulnerable to Insecure Direct Object Reference attacks, the smart alarm controller - which can turn other manufacturers' alarm systems on and off remotely - does not properly validate bearer tokens and also exposes the MAC address of those alarms.
In short, this is an epic IoT security fail. Nexx has not responded to contacts from Sabetan, the US Cybersecurity & Infrastructure Security Agency, or media outlets, and one can almost understand why: the exposure of affected customers (at least 20,000 of them) is massive, and remediation will also be a costly undertaking, if it can be done at all (if the firmware which contains the hard-coded passwords is not stored in flashable media). The only safe course for Nexx customers is to unplug these devices and contact Nexx to get them fixed or replaced.
Sabetan, Sam, The Uninvited Guest: IDORs, Garage Doors, and Stolen Secrets, blog post, 5 April 2023. Available online at https://medium.com/@samsabetan/the-uninvited-guest-idors-garage-doors-and-stolen-secrets-e4b49e02dadc.
Self-Extracting Archives Considered Harmful
Our readers are doubtless familiar with the use of WinZIP, WinRAR and similar utilities to compress files and package them for faster download and distribution. So common have these techniques become that the Windows desktop shell has code built in to transparently open ZIP files as though they are just another folder. However, most archiving utilities offer another feature that Windows doesn't: the ability to encrypt an archive under a password in order to provide some degree of security for email attachments.
In order to make it possible for a recipient to extract the contents of an password-protected archive file without having to buy additional software, many utilities can create self-extracting archive (SFX) files which package the desired files along with a stub of code for decryption and file extraction. The risk here is that it entices the recipient to run code which has just been received from a source which may be untrusted or even unknown - but naive end-users rarely stop to consider this.
Threat actors are increasingly making use of this to install malware such as backdoors into victims' machines. Crowdstrike's Falcon OverWatch team provides a nice example they recently discovered: an apparently empty SFX archive which could could implant a persistent backdoor.
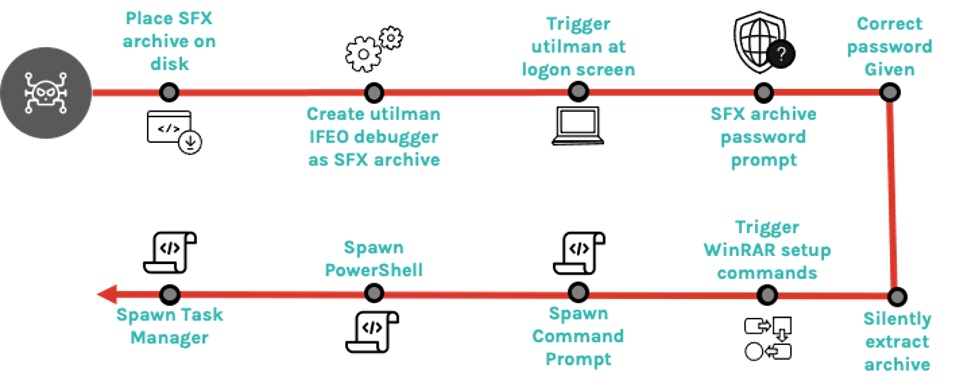
(Image credit: Crowdstrike)
In this case, the malware used a registry key to configure utilman.exe to run an ImageFileExecutionOptions debugger at logon time, with the debugger then running a password-protected SFX archive. But the really curious fact is that the archive contains only a text file of 0 bytes length, rather than any actual malware. In fact, the backdoor was established by using the ability of WinRAR SFX archives to run extended SFX commands upon successful unarchiving; in this case, the SFX would automatically spawn a command prompt, PowerShell and a copy of Task Manager with no visible dialogs - just what a threat actor needs in order to regain access to a compromised system.
Because many anti-malware tools will scan only the files within a self-extracting archive, and this archive contained only an innocent-looking empty text file, it could easily escape detection.
Minton, Jill, How Falcon OverWatch Investigates Malicious Self-Extracting Archives, Decoy Files and Their Hidden Payloads, blog post, 31 March 2023. Available online at https://www.crowdstrike.com/blog/self-extracting-archives-decoy-files-and-their-hidden-payloads/.
ChatGPT Happily Works on the Dark Side
Many IT and security professionals have experimented with ChatGPT, getting it to write code. Inevitably, our thoughts drift to how threat actors might make use of such tools. While ChatGPT's creators, OpenAI, have put in place some protections and obvious requests to write malware will be blocked, we are learning that chaining multiple requests and using oblique phrasing can often circumvent OpenAI's defensive efforts.
Now Forcepoint solutions architect Aaron Mulgrew has shown how, with just a few hours experimenting and very limited tech skills, ChatGPT can be enticed into writing some functional malware - in this case, an undetectable information exfiltration tool that uses steganographic techniques.
The basic technique that Mulgrew used was to generate small snippets of code and then manually assemble the completed code. By asking ChatGPT for code to a) find large PNG files, b) steganographically encode the found files and c) exfiltrate them to Google Drive, he was able to create a working proof-of-concept. Unfortunately, when processed by VirusTotal, this first version was flagged as malicious by five different vendors out of 69 possible detections - not a bad start, though.
Armed with some clues about why some vendors might be detecting this code, Mulgrew then set about getting ChatGPT to refactor the code, first by incorporating some steganography code directly, rather than calling an external library. Next, to evade sandbox detection, he had ChatGPT delay execution of the code by two minutes. Finally, after a simple request to obfuscate the code was rebuffed, he simply had ChatGPT change all the variable names to random English first names and surnames. This time, VirusTotal did not detect the code as malicious.
The final step was to achieve initial access or delivery, e.g. by getting a naive user to execute it. Mulgrew was able to coax ChatGPT into providing instructions to package the executable as a Windows screensaver (.SCR) file. However, this led to three detections by VirusTotal - but at least the point was made: ChatGPT can be 'social engineered' into writing malware, and we should expect threat actors to take advantage of this in coming months.
Interestingly, Mulgrew ended his experiment by getting ChatGPT's advice on how to mitigate this kind of attack, and it was pretty much what you might expect: generally obvious but certainly not foolproof.
Mulgrew, Aaron, I built a Zero Day with undetectable exfiltration using only ChatGPT prompts, blog post, 4 April 2023. Available online at https://www.forcepoint.com/blog/x-labs/zero-day-exfiltration-using-chatgpt-prompts.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.