Les Bell
Blog entry by Les Bell
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
Four Corners Cybercrime Doco Drops
As we predicted, the Australian Broadcasting Commission has made available the latest episode of its flagship current affairs program, Four Corners, on YouTube so that it is available to international viewers. The documentary deals with the nexus between cybercrime and cyberwarfare, and covers attacks in Australia - most notably on Medibank - and in Ukraine.
Four Corners, Cyber Gangs Cracked Open, documentary film, 17 April 2023. Available online at https://www.youtube.com/watch?embed=no&v=4m6Ydx0TGMY.
Alleged Criminals Challenge Evidence From 'Secure' Messaging Service
In a case that could have implications for the use of evidence obtained via implants on smartphones, around 50 alleged criminals are challenging the admissibility of evidence obtained in the Australian Federal Police's Operation Ironside.
Ironside was the Australian end of a joint operation with the FBI (who called it Trojan Shield) and Europol's Task Force Greenlight. The FBI had obtained the 'cooperation' of a developer who had been working on an encrypted messaging device called ANOM for use by criminal networks; in exchange for a reduced sentence he agreed to finish the development and make it available to his criminal customers. However, the customers did not know that the service's proxy servers were copying all messages, along with the related private keys, to FBI-controlled servers, and the FBI was sharing some of these with the AFP.
In this week's Sydney committal hearing, barristers for the defendants will challenge the validity of evidence obtained via these messages. The AFP claimed that they had been granted a "court order to legally monitor the ANOM devices of the individuals in Australia or with a clear nexus to Australia". However, magistrate Robert Williams will now have to decide whether that evidence was legally intercepted. Much hinges on the question of where duplication of of messages took place and whether the devices were connected to a telecommunications network at that time, based on technical testimony by an expert witness who has examined some of the ANOM source code.
In a similar challenge heard before the Supreme Court of South Australia, Justice Adam Kimber held that the Operation Ironside intercepts were legally conducted.
Parkes-Hupton, Heath, Why accused criminals are challenging evidence in Sydney from one of the world's biggest police stings, ABC News, 18 April 2023. Available online at https://www.abc.net.au/news/2023-04-18/accused-criminals-challenge-an0m-app-evidence-in-supreme-court/102107344.
Former FIN7 and Conti Members Join Forces
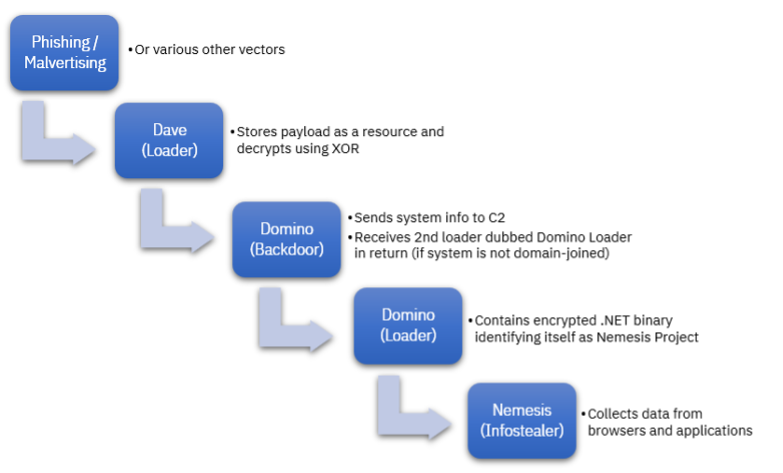
A report from IBM Security X-Force reveals that developers from the FIN7 gang have developed a new backdoor family called (by X-Force) Domino. The Domino code overlaps with the older Lizar malware which cames from the same source. But what makes recent campaigns particularly interesting is that Domino is being deployed using the Dave Loader, suggesting that the campaigns are being run by former members of the Conti ransomware syndicate. Conti fragmented into several factions, including Quantum, Royal, BlackBasta and Zeon.
These factions have used Dave Loader to deliver Cobalt Strike payloads, as well as IcedID and Emotet, which are both used as initial access vectors for subsequent ransomware operations. However, the payload of some recent Dave Loader samples was Domino Backdoor, a DLL which performs basic system enumeration (system name, user names, running processes), sending this back to the group's C2 server. The server will respond with a command which triggers download of a second loader which shares code with Domino (hence, Domino Loader) which in turn decrypts an internal payload which turns out to be a .NET infostealer called Nemesis Project.
(Image credit: IBM Security X-Force)
However, if the victim machine is a domain member, Domino Backdoor contacts a different C2 server, possibly to download a more capable backdoor such as Cobalt Strike which can then be used to pivot against other systems.
The combination of tools in this campaign indicates the fluid nature of cybercrime operations, with groups fracturing and members collaborating to form new syndicates.
Hammond, Charlotte and Ole Villadsen, Ex-Conti and FIN7 Actors Collaborate with New Domino Backdoor, blog post, 14 April 2023. Available online at https://securityintelligence.com/posts/ex-conti-fin7-actors-collaborate-new-domino-backdoor/.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.