Les Bell
Blog entry by Les Bell
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
NSO's Pegasus - Still a Thing
Just over a week ago, we brought you news of Citizen Lab's discovery of new amrtphone implants produced by Israeli spyware firm QuaDream. This kind of implant is commonly used by governments to spy on journalists and civil rights activists - a market that was pioneered by another Israeli company, NSO Group. We hadn't heard from NSO Group in some time, suspecting that intense publicity had caused them to put the brakes on their activities.
Not so, it seems, according to a new report from Citizen Lab, who have discovered three new zero-click exploit chains against Apple iOS 15 and 16 which seem to have been developed by NSO Group during 2022. The Toronto researchers' investigation started with the discovery of infections on the phones of human rights defenders from Centro PRODH, which represents victims of military abuses in Mexico.
This led to the uncovering of PWNYOURHOME, which was deployed against iOS 15 and 6 starting in October 2022, and appears to be a novel two-step zero-click exploit - the first step targets HomeKit and the second target iMessage. Working backwards, FINDMYPWN was deployed against iOS 15 from June 2022, and is also a two-step exploit - stage one targets the iPhone's "Find My" feature, while stage two targets iMessage. Using information shared by Citizen Lab, Apple released fixes for HomeKit in iOS 16.3.1.
Having identified FINDMYPWN and PWNYOURHOME, the Citizen Lab researchers discovered traces of NSO Group's first 2022 zero-click, LATENTIMAGE, which may also have exploited the iPhone "Find My" feature.
The Citizen Lab report provides a full run-down on the technical aspects of these exploits, as well as the socio-political targeting, and suggested mitigation using Apple's Lockdown Mode.
Marczak, Bill, John Scott-Railton, Bahr Abdul Razzak and Ron Deibert, Triple Threat: NSO Group’s Pegasus Spyware Returns in 2022 with a Trio of iOS 15 and iOS 16 Zero-Click Exploit Chains, technical report, 18 April 2023. Available online at https://citizenlab.ca/2023/04/nso-groups-pegasus-spyware-returns-in-2022/.
GhostToken Vulnerability Hides Malicious Google Cloud Applications
A recently-patched vulnerability in Google Cloud Platform potentially exposed millions of Google accounts to access via an invisible, undeletable OAuth2 access token. The vulnerability, called GhostToken by the Astrix Security researchers who discovered it, was notified to Google on 19 June 2022. So deep in Google's processes was the vulnerability located that it took the cloud provider over nine moths to deploy a fix, in early April, allowing disclosure of the vulnerability by Astrix.
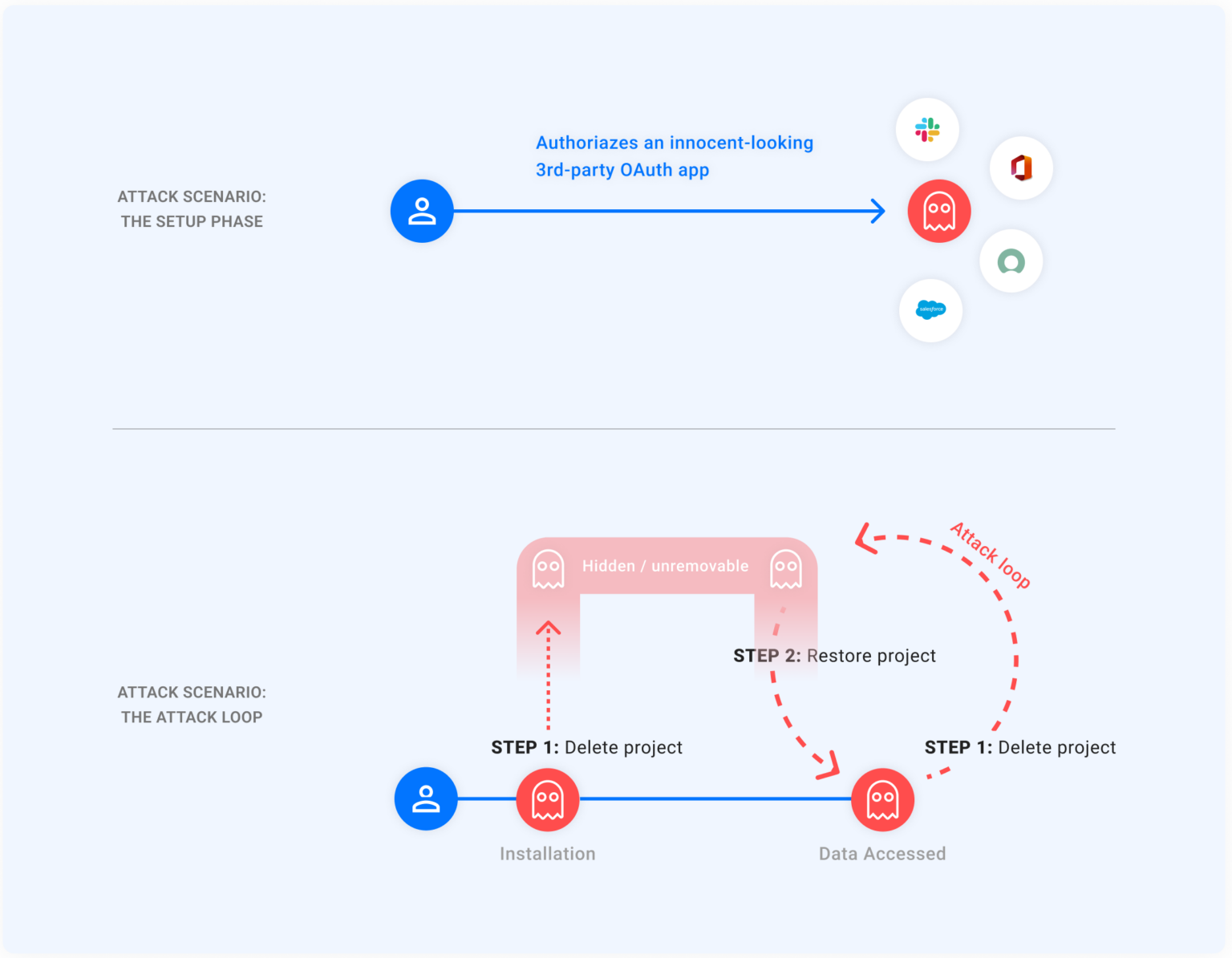
(Image credit: Astrix)
A hypothetical attack would work by getting the victim to naively grant access, via the OAuth 2.0 protocol, to their Google account by an apparently trustworthy app. The attacker then replaces the app code with a malicious version and - here's the GhostToken trick - deletes the Google Cloud Platform project associated with the OAuth2 authorization. This causes the project to go into a "pending deletion" state, which removes the app from the user's app permissions page at https://myaccount.google.com/permissions and preventing the victim from removing access.
However, the project will not be really deleted for another 30 days, allowing the attacker to restore it, use the access token to copy the victim's data, and then delete the project once more. Just what data the attacker can access depends upon the permissions granted by the victim, but could include access to Gmail, Google Drive, Docs and other application data.
The Google fix simply updates the app permissions page to include apps that are in a pending deletion state, so that the user can revoke access.
Uncredited, GhostToken – Exploiting GCP application infrastructure to create invisible, unremovable trojan app on Google accounts, blog post, 20 April 2023. Available online at https://astrix.security/ghosttoken-exploiting-gcp-application-infrastructure-to-create-invisible-unremovable-trojan-app-on-google-accounts/.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.