Les Bell
Blog entry by Les Bell
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
Yet Another Amplification Attack
Network security professionals know that a number of UDP-based application-layer protocols can be used for amplification attacks. In these attacks, the threat actor sends UDP datagrams to a vulnerable service, but spoofs the source IP address to be the victim's IP address rather than her own. In response to a single UDP datagram request, the vulnerable service will reply with many datagrams in reply - hence the term, amplification attack.
A number of protocols provide quite high amplification factors: for example, the QOTD (Quote of the Day) service will respond with an average of over 140 datagrams for one query, while the CharGEN service has an amplification factor of over 358 to 1. The saving grace is that these protocols are rarely used, hence pose little threat. A bit more troublesome is the network time protocol (NTP), which has an amplification factor of almost 557.
Now, researchers from Bitsight and Curesec have reported a high-severity vulnerability - CVE-2023-29552 - in the Service Location Protocol (SLP, RFC 2608), which could provide attackers with amplification factors as high as 2,200. This seems to be a new record, and could lead to massive distributed denial of service (DDoS) attacks.
Despite its age, SLP is still in use; the researchers identified over 54,000 SLP instances in over 2,000 organizations globally. Products that incorporate SLP include VMware ESXi Hypervisor, Konica Minolta printers, Planex routers, IBM Integrated Management Module (IMM), SMC IPMI and many others. Many of these systems are accessible on the Internet, and are likely to be older, unmanaged or even abandoned systems, as in well-managed networks, firewalls would not pass SLP datagrams, which use port 427.
CISA, Abuse of the Service Location Protocol May Lead to DoS Attacks, alert, 25 April 2023. Available online at https://www.cisa.gov/news-events/alerts/2023/04/25/abuse-service-location-protocol-may-lead-dos-attacks.
Stone, Noah, New high-severity vulnerability (CVE-2023-29552) discovered in the Service Location Protocol (SLP), blog post, 25 April 2023. Available online at https://www.bitsight.com/blog/new-high-severity-vulnerability-cve-2023-29552-discovered-service-location-protocol-slp.
Critical Vulnerabilities In Print Management Software, Exploited in the Wild
Two vulnerabilities in enterprise print management software PaperCut MF and PaperCut NG are being exploited in the wild. The vulnerabilities, reported to PaperCut by Trend Micro, are:
- CVE-2023-27350 - CVSS v3.x: 9.8 (Critical) - Unauthenticated remote code execution in SYSTEM context
- CVE-2023-27351 - CVSS 3.x: 8.2 (High) - Authentication bypass
The vulnerabilities have been fixed in PaperCut MF and NG versions 20.1.7, 21.2.11 and 22.0.9 and higher, but many organizations are yet to deploy the patches. A Shodan search showed that close to 1,700 instances of the software were exposed to the Internet.
Security firm Huntress has observed post-exploitation deployment of backdoors on compromised instances, followed by installation of Truebot malware or cryptomining software. Apart from this, exploitation of CVE-2023-27350 would allow exfiltration of sensitive data such as user names, email addresses and more from unpatched servers.
Goodin, Dan, Exploit released for 9.8-severity PaperCut flaw already under attack, Ars Technica, 25 April 2023. Available online at https://arstechnica.com/information-technology/2023/04/exploit-released-for-9-8-severity-papercut-flaw-already-under-attack/.
Uncredited, URGENT | PaperCut MF/NG vulnerability bulletin (March 2023), knowledgebase article, 25 April 2023. Available online at https://www.papercut.com/kb/Main/PO-1216-and-PO-1219.
North Korean APT Targets MacOS with 'RustBucket' Malware
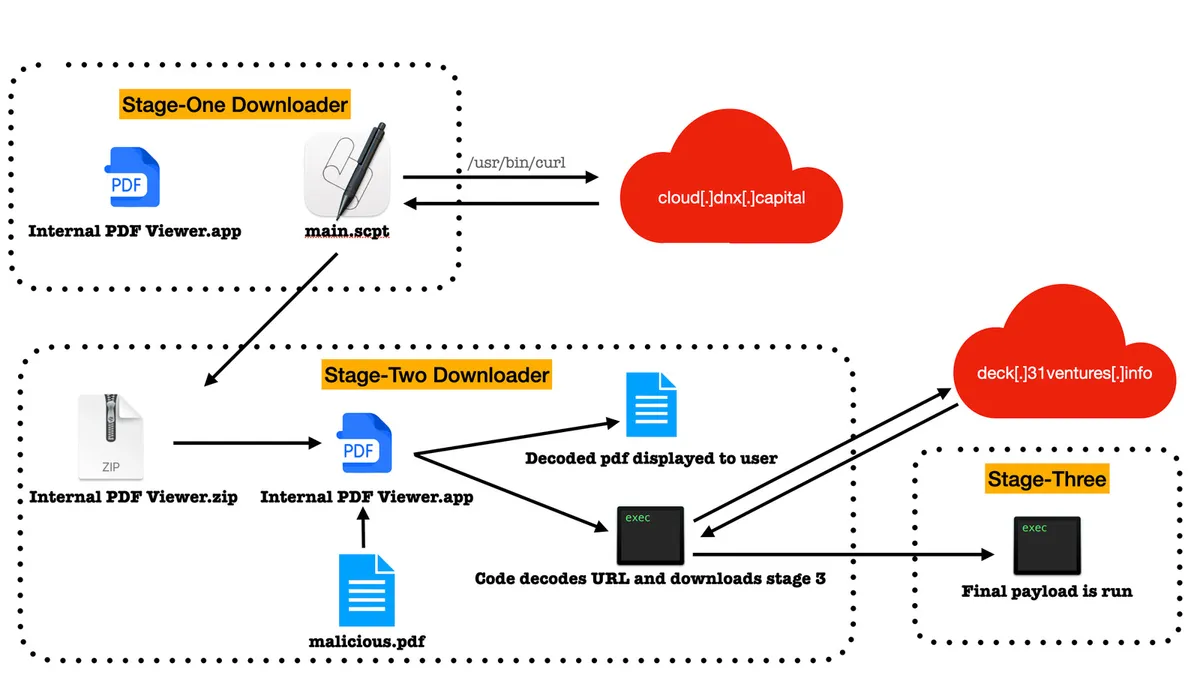
Researchers at Jamf Threat Labs have discovered a MacOS malware family which they have christened 'RustBucket'. The malware contacts C2 servers to download and execute various payloads and, based upon the similarity to a Windows attack documented by Kaspersky, is attributed to BlueNoroff, a subgroup of the North Korean Lazarus Group.
(Image credit: Jamf)
The first stage dropper of the malware chain is written in compiled AppleScript, and embedded into an unsigned application named Internal PDF Viewer.app; this is consistent with BlueNoroff's technique of luring victims with fake job application correspondence. Stage 2 is written in Objective-C and also masquerades as a PDF viewer, and is a trojan horse which activates when a specific PDF file is loaded, functioning as a loader. Stage 3, written in Rust (hence, 'RustBucket'), is a more sophisticated backdoor.
Saljooki, Ferdous and Jaron Bradley, BlueNoroff APT group targets macOS with ‘RustBucket’ Malware, blog post, 21 April 2023. Available online at https://www.jamf.com/blog/bluenoroff-apt-targets-macos-rustbucket-malware/.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.