Les Bell
Blog entry by Les Bell
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
seL4 Team Garners Major ACM Award
The Association for Computing Machinery (ACM) has awarded its 2022 Software System Award to the team behind seL4, a mathematically-proven secure implementation of the L4 microkernel. Back in 2009, a group from UNSW/NICTA (later, Data61 and CSIRO) used automated theorem proving to prove that seL4 is secure (Klein et. al., 2009); in order to allow automated reasoning, seL4 implements a capabilities-based access control model. In a DARPA study, hackers were able to break into the Linux-based OS of an autonomous helicopter, but after it was re-engineered to use seL4, the hackers were unable to break in, even after being given root access to a Linux VM hosted on the seL4 microkernel.
After a slow start, seL4 has seen increasing adoption by industry, particularly in US defense and aerospace, but increasingly in industrial control systems and embedded systems. A key industry project using seL4 is the development of a secure car operating system. seL4 is also used in the secure enclave of iOS devices.
Gernot Heiser, University of New South Wales; Gerwin Klein, Proofcraft; Harvey Tuch, Google; Kevin Elphinstone, University of New South Wales; June Andronick, Proofcraft; David Cock, ETH Zurich; Philip Derrin, Qualcomm; Dhammika Elkaduwe, University of Peradeniya; Kai Engelhardt; Toby Murray, University of Melbourne; Rafal Kolanski, Proofcraft; Michael Norrish, Australian National University; Thomas Sewell, University of Cambridge; and Simon Winwood, Galois, receive the Award for their work, which has fundamentally changed the research community's perception of what formal methods can accomplish, showing that not only is it possible to complete a formal proof of correctness and security for an industrial-strength operating system, but that this can be accomplished without compromising performance or generality.
seL4 has now been open-sourced under the auspices of the seL4 Foundation. More information can be found at http://sel4.systems/.
Klein, G., K. Elphinstone, G. Heiser, J. Andronick, D. Cock, P. Derrin, D. Elkaduwe, et al., SeL4: Formal Verification of an OS Kernel. In Proceedings of the ACM SIGOPS 22nd Symposium on Operating Systems Principles, 207–220, 2009.
Uncredited, About ACM Software System Award, ACM, May 2023. Available online at https://awards.acm.org/software-system.
Australian Law Firm Hacked by ALPHV/BlackCat
Commercial law firm HWL Ebsworth has apparently fallen victim to an attack conducted by an affiliate of one of the most prolific ransomware and data leak actors, ALPHV/BlackCat, which has posted the exfiltrated data on its dark web site. ALPHV/BlackCat operates as Ransomware-as-a-Service, and its affiliates typically target high-value targets; earlier this year it was responsible for attacks on real estate company, LJ Hooker, a medical practice in Lackawanna County, Pennsylvania and Amazon's Ring doorbell division.
The threat actor claims to have 4TB of data from HWL Ebsworth, including employee CV's, ID's, financial reports and accounting data, as well as a complete network map. Perhaps more concerningly, the data also includes client documentation and credit card information.
The law firm's privacy policy claims it takes "stringent measures to protect that information from misuse, interference and loss and from unauthorised access, modification or disclosure". To do this, it employs " broad range of security safeguards", stating that "all electronic databases incorporate strict password access and virus and firewall protection procedures" and "Physical and logical security measures are employed to deal with external threats and the possibility of internal ones". Regular readers will recognise that there is a lot more to information security and privacy than that.
Taylor, Josh, Australian law firm HWL Ebsworth hit by Russian-linked ransomware attack, The Guardian, 2 May 2023. Available online at https://www.theguardian.com/technology/2023/may/02/australian-law-firm-hwl-ebsworth-hit-by-russian-linked-ransomware-attack.
Chinese APT's Employee New DLL Sideloading Techniques
Researchers from both Trend Micro and Sophos have independently detected the use of sophisticated new DLL sideloading techniques by Chinese APT groups. In DLL sideloading, a malicious loader, typically carrying an encrypted payload, injects its code into an innocent, non-malicious application once it is running.
The Trend Micro team has discovered a campaign by Earth Longzhi (a subgroup of APT41), targetting organizations in Taiwan, Thailand, the Philippines and Fiji. The campaign abuses a Windows Defender executable to perform DLL sideloading while also exploiting a vulnerable driver, zamguard.sys to disable security products on the target hosts in a 'bring-your-own-vulnerable-driver' (BYOVD) attack. Their report also describes an innovative technique for disabling security products which they have named 'stack rumbling' via Image File Execution Options (IFEO).
The campaign also evades security products' API monitoring by instead using remote procedure calls to install drivers as kernel-level services.
The Sophos researchers document a campaign, likely conducted by an APT variously known as "Operation Dragon Breath", "APT-Q-27" or "Golden Eye Dog", which is believed to specialize in attacks on online gambling participants. This campaign adds complexity and layers to the classic DLL sideloading attack. This variant adds a second stage to the attack: a first-stage 'clean' application 'side-loads' and executes a second 'clean' application, which in turn, sideloads the malicious loader DLL. Finally, the loader DLL executes the final malicious payload.
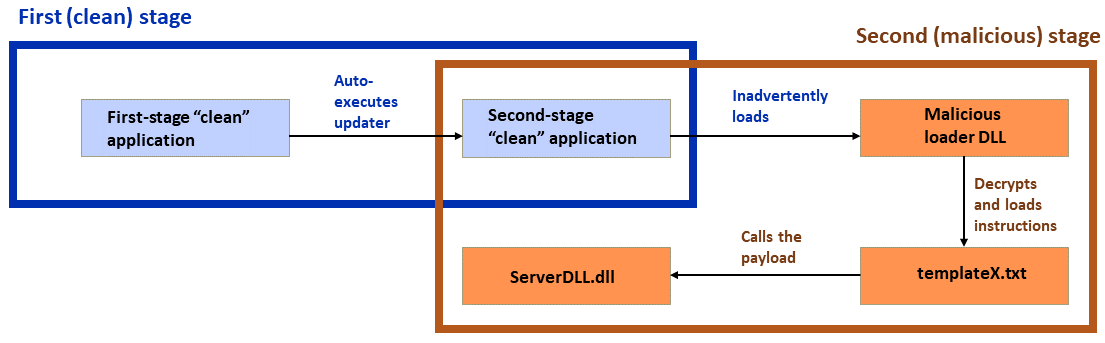
The two-step sideloading attack; 'clean' applications shown in blue with malicious payloads and steps shown in orange. (Image credit: Sophos)
Initial infection is accomplished via a malicious installer for what claims to be a Chinese-language version of the Telegram messaging application or via a trojanized installer for LetsVPN. Another variant claims to be a WhatsApp installer.
The two reports provide lots of technical detail for those of us who enjoy that kind of thing, as well as IOC's and other actionable information.
Lee, Ted and Hara Hiroaki, Attack on Security Titans: Earth Longzhi Returns With New Tricks, Trend Micro research report, 2 May 2023. Available online at https://www.trendmicro.com/en_us/research/23/e/attack-on-security-titans-earth-longzhi-returns-with-new-tricks.html.
Szappanos, Gabor, A doubled “Dragon Breath” adds new air to DLL sideloading attacks, Sophos blog post, 3 May 2023. Available online at https://news.sophos.com/en-us/2023/05/03/doubled-dll-sideloading-dragon-breath/.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.