Les Bell
Blog entry by Les Bell
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
Cancer Centre Hit By Ransomware Attack
NSW Health has revealed that the Crown Princess Mary Cancer Centre, which is part of Sydney's Westmead Hospital, has been hit by a ransomware attack. NSW Health was alerted to the attack late yesterday afternoon, and states that the attack does not seem to have impacted other NSW health systems or the cancer centre's databases.
Ransomware group Medusa is apparently behind the attack, having added the cancer centre to its victim list with a countdown timer on its site giving the victim a week to pay up before sensitive information will be leaked. Medusa has been highly active in recent months, targeting the Minneapolis Public Schools as well as targets in Australia.
FalconFeedsio, Medusa #ransomware group added The Crown Princess Mary Cancer Centre..., tweet, 4 May 2023. Available online at https://twitter.com/FalconFeedsio/status/1653990479367749634.
Tran, Danny, Crown Princess Mary Cancer Centre in Westmead Hospital in cyber attack, hackers threatening to release stolen data, ABC News, 4 May 2023. Available online at https://www.abc.net.au/news/2023-05-04/crown-princess-mary-cancer-centre-being-hacked/102305996.
Google Adds Passkey Support
Google has added support for passkeys on personal Google accounts, allowing users to finally dispense with passwords.
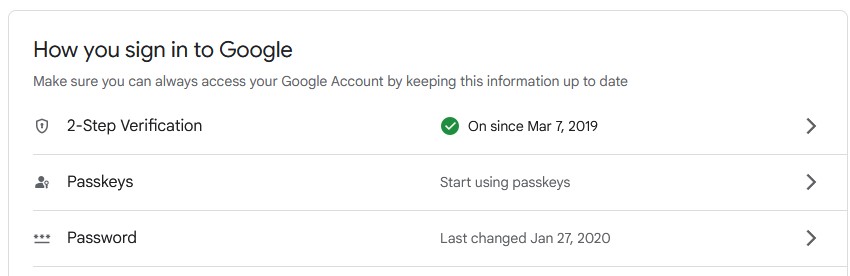
Experience shows that passwords are problematic: users create weak passwords, share them with others, and accidentally disclose them to bad actors via phishing attacks. Worse still, people have trouble remembering them, and will routinely use the same password across multiple sites, increasing their exposure to credential stuffing attacks.
By contrast, passkeys operate by using public key cryptography - when the user generates a passkey the private key is stored locally, on a computer or mobile device, while the public key is uploaded to the authenticating site - in this case, Google. For subsequent logins, the authenticator will generate a challenge which is sent to the user's device; this will ask the user to authenticate themselves, by biometric techniques such as facial recognition or fingerprint recognition, or some other technique, and then use the private key to sign a response sent back to the authenticator, which can then verify the signature and grant the user access.
Each passkey is unique to a single account, so there is no reuse across sites; they do not need to be memorized, and are generally simpler to use than passwords, once set up. Furthermore, they can also be used on shared or borrowed devices without being stored on them - for example, a user can select the option to "use a passkey from another device" to use their phone to obtain a one-time sign-in on, say, a campus lab computer or library computer. And of course, passkeys can be revoked if the user suspects they are compromised.
Birgisson, Arnar and Siana K Smetters, So long passwords, thanks for all the phish, blog post, 3 May 2023. Available online at https://security.googleblog.com/2023/05/so-long-passwords-thanks-for-all-phish.html.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.