Les Bell
Blog entry by Les Bell
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
Resilience, Redundancy and Separation in Incident Response
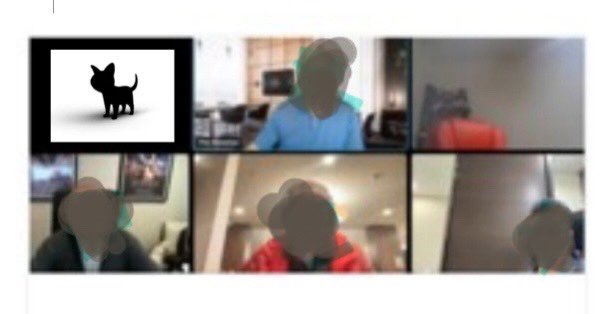
The March breach of systems at storage vendor Western Digital has provided an interesting lesson for those who work in - or more importantly, plan for - incident response operations. Ransomware gang BlackCat/ALPHV has allegedly broken into an early morning videoconference held by the company's incdent response team and posted a screen grab on the gang's web site, dubbing the attendees, "the finest threat hunters Western Digital has to offer". Ouch!
(Image credit: Dominic Alvieri)
There's an important lesson here. Putting all your eggs in one basket with a monoculture (typically Microsoft, these days) can allow all those eggs to be compromised simultaneously. Separation of systems may be more complex and expensive to administer, but it can limit the impact of an attack, as Norsk Hydro showed when it dealt with a targeted ransomware attack on its on-prem systems by using its Microsoft 365 and Azure resources to keep communication channels open and some systems running. And once the bad guys are in your systems, using those same systems to coordinate defence will let the bad guys stay one step ahead.
Incidentally, BlackCat/ALPHV also last week claimed responsibility for a ransomware attack on Canadian software company Constellation Software, exfiltrating over 1 TB of both business and personal data which is now being ransomed on the group's web site.
Alvieri, Dominic, This is a black eye for Western Digital., tweet, 28 April 2023. Available online at https://twitter.com/AlvieriD/status/1652173436888784896.
Gatlan, Sergiu, ALPHV gang claims ransomware attack on Constellation Software, Bleeping Computer, 5 May 2023. Available online at https://www.bleepingcomputer.com/news/security/alphv-gang-claims-ransomware-attack-on-constellation-software/.
Former Uber CISO Sullivan Sentenced; Escapes Jail Time
A key concern for chief information security officers is the extent to which they may be found legally liable in the event of a breach. A case in point is that of former Uber CSO Joe Sullivan, who was found guilty obstructing justice by concealing a data breach from the Federal Trade Commission, which had been investigating the company's privacy protections, and also of actively hiding a felony (Menn, 2022). The charges arose from protracted negotiations Sullivan had undertaken with the hackers in an attempt to identify them and to minimise the extortion payment- allegedly with the knowledge and agreement of other company officers.
On 4 May, Judge William Orrick of the US District Court for the Northern District of California sentenced Sullivan to three years' probation and ordered him to do 200 hours of community service, along with a $US50,000 fine. Despite having received 186 letters from Sullivan's peers, friends and family, many of them arguing for leniency, the judge was scathing in his summary and stated that other security professionals would not be so fortunate if brought before him in future:
"If I have a similar case tomorrow, even if the defendant had the character of Pope Francis, they would be going to prison. . . . When you go out and talk to your friends, to your CISOs, you tell them that you got a break not because of what you did, not even because of who you are, but because this was just such an unusual one-off."
Menn, Joseph, Former Uber security chief convicted of covering up 2016 data breach, The Washington Post, 5 October 2022. Available online at https://www.washingtonpost.com/technology/2022/10/05/uber-obstruction-sullivan-hacking/.
US Department of Justice, Former Chief Security Officer Of Uber Sentenced To Three Years’ Probation For Covering Up Data Breach Involving Millions Of Uber User Records, press release, 5 May 2023. Available online at https://www.justice.gov/usao-ndca/pr/former-chief-security-officer-uber-sentenced-three-years-probation-covering-data.
Vijayan, Jai, Judge Spares Former Uber CISO Jail Time Over 2016 Data Breach Charges, Dark Reading, 6 May 2023. Available online at https://www.darkreading.com/attacks-breaches/judge-spares-former-uber-ciso-jail-time-over-2016-data-breach-charges.
Meta (Facebook) Takes Down Malware Using ChatGPT As Lure
You might have noticed a rash of Facebook ads promoting desktop apps and browser plugins which act as a 'free' front-end for OpenAI's massively over-hyped (not their fault) conversational large language model. If these seemed too good to be true - or merely pointless - you were right, and Meta has now confirmed that it has taken down a massive campaign that was promoting these malware-infested tools via over one thousand different URL's.
It seems that the primary goal of the malware families - Ducktail, NodeStealer and others - is to compromise businesses with access to ad accounts across the Internet. In fact, ten different malware families have used ChatGPT and similar themes to compromise account.
The Ducktail malware has been evolving for several years since it first emerged, distributing malware via file-hosting services like Dropbox and Mega to infect browsers such as Google Chrome, Microsoft Edge, Brave, and Firefox in order to access victims' information on desktop systems. Meta issued a cease and desist letter to its Vietnam-based operators, referred the case to law enforcement and will take additional actions as appropriate.
The Meta analysts' report also provides a detailed breakdown of the NodeStealer malware.
In other Facebook-related news, the company has also disrupted nine different adversarial networks. Six of these were engaged in disinformation campaigns (what Meta calls 'Coordinated Inauthentic Behavior'), originating in the US, Venezuela, Iran, China, Georgia, Burkina Faso and Togo, and primarily targeting people outside of their countries.
However, the firm also disrupted three cyber-espionage operations in South Asia: an advanced persistent threat (APT) group we attributed to state-linked actors in Pakistan, a threat actor in India known in the security industry as Patchwork APT, and the threat group known as Bahamut APT in South Asia. Each of these groups relied heavily on social engineering to trick people into clicking on malicious links, downloading malware or sharing personal information.
Nguyen, Duc H. and Ryan Victory, The malware threat landscape: NodeStealer, DuckTail, and more, blog post, 3 May 2023. Available online at https://engineering.fb.com/2023/05/03/security/malware-nodestealer-ducktail/.
Rosen, Guy, Meta’s Q1 2023 Security Reports: Protecting People and Businesses, news release, 3 May 2023. Available online at https://about.fb.com/news/2023/05/metas-q1-2023-security-reports/.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.