Les Bell
Blog entry by Les Bell
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
Lazarus Group Targets IIS Via DLL Sideloading Attack
Researchers at South Korean security firm AhnLab has reported on a campaign being run by North Korean state-sponsored APT the Lazarus Group. The specific attack targets servers running a vulnerable version of Microsoft's Internet Information Server, achieving initial access via a DLL sideloading technique.
In this attack, the threat actor uses the IIS web server process, w3wp.exe, to place a malicious DLL named msvcr100.dll into the same directory as a normal application executable, Wordconv.exe. When they run Wordconv.exe, this loads and executes the malicious DLL, exploiting the well known DLL search path vulnerability in Windows: rather than only loading DLL's from the system library path, Windows will search the current working directory first and load the malicious DLL instead of the legitimate one.
msvcr100.dll is very similar to an earlier Lazarus Group DLL, cylvc.dll - it decrypts a data file called msvcr100.dat in order to create an executable file in memory, which it then runs, using yet another DLL called diagn.dll to decrypt and run another executable. This process resisted forensic analysis, but since it accesses the memory of the lsass.exe process, it is most likely a credential stealer. Once credentials have been acquired, the threat actor then performs network reconnaisance and pivots to other hosts, using the RDP protocol.
The AhnLabs report includes some analysis and IOC's.
muhan, Lazarus Group Targeting Windows IIS Web Servers, technical report, 23 May 2023. Available online at https://asec.ahnlab.com/en/53132/.
Breached? At Least Think About Changing Passwords
An alarming statistic gleaned from a survey of cybersecurity breaches released by the UK Department for Science, Innovation & Technology last month reveals that only 6% of businesses and 4% of charities updated passwords after their most disruptive breach or attack of the previous 12 months. This is an astonishingly low figure, even allowing for the fact it was based on the 32% of business and 24% of charity survey respondents that had identified a breach, rather than the full sample of respondents. It also leads one to wonder: the survey question asked about only "the most disruptive breach or attack" - how many of the respondents had suffered multiple breaches? Probably more than a few, if their lax password practices are any indication.
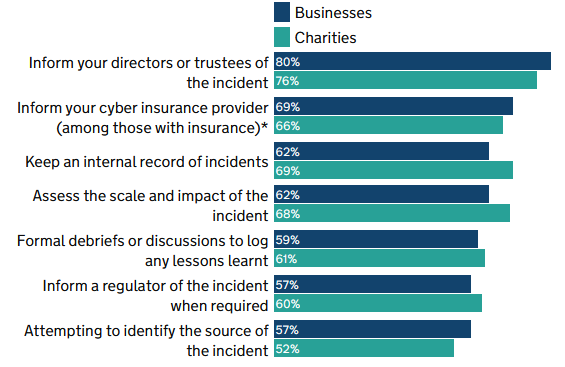
Percentage of organisations that say they take, or would take, the following actions following a cyber security incident (UK Government)
Some of the other statistics are quite alarming - for example, only 57% of businesses and 60% of charities would inform a regulator, and only slightly more would formally debrief to log any lessons learned.
Around one-third of businesses and a quarter of charities reported having experienced some kind of cybersecurity breach or attack in the previous 12 months, with larger businesses and high-income charities being more likely to identify breaches or attacks than small ones.
The report makes fascinating, albeit somewhat scary, reading.
Johns, Emma, et. al., Cyber security breaches survey 2023, UK Department for Science, Innovation & Technology, 19 April 2023. Available online https://www.gov.uk/government/statistics/cyber-security-breaches-survey-2023/cyber-security-breaches-survey-2023.
Stealthy Infostealer Targets Browsers, Crypto Wallets
From Trend Micro comes a report of a new infostealer called Bandit Stealer which is being promoted within the malware community. Bandit Stealer is written in the Go programming language, perhaps with cross-platform compatibility in mind, and makes use of sandbox detection techniques in order to evade detection and analysis by anti-malware products.
The malware attempts to achieve privilege elevation by using the runas.exe utility (a rough equivalent to *ix's sudo command). However, it fails - primarily due to the fact that to run as Administrator it will have to provide a password.
It also checks to see if it running in a container, sandbox, jail or any of several virtualization environments such as KVM, VirtualBox, VMware or Xen. However, while doing this, it also attempts to read /proc/self/status - a directory that only exists on Linux machines, indicating the intention of developing a cross-platform variant. It further downloads a text file containing hardware ID's, IP addresses, MAC addresses, usernames, hostnames and process names that might also indicate that is being run in a sandbox or test environment, and if it sees any of the blacklisted processes, it will attempt to terminate them. Again, the use of Linux-specific commands like pgrep and pkill indicate cross-platform intent.
Bandit Stealer goes on to create an autorun registry entry in order to persist through reboots, and then sets about collecting information, storing it in a vicinfo folder in the user's AppData\Local\ directory. It collects user and host information, Telegram sessions, login data, cookies, web history and credit card details from any of many different browsers, as well pilfering cryptocurrency wallets.
Initial infection seems to be through a drive-by or phishing malmails which carry a dropper.
The Trend Micro report provides a more detailed analysis and IOC's.
Camling, Sarah Pearl and Paul John Bardon, New Info Stealer Bandit Stealer Targets Browsers, Wallets, research report, 26 May 2023. Available online at https://www.trendmicro.com/en_us/research/23/e/new-info-stealer-bandit-stealer-targets-browsers-wallets.html.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.