Les Bell
Blog entry by Les Bell
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
From the "Who Ever Thought This Was a Good Idea?" File
Back in 2014, ICANN (the Internet Corporation for Assigned Names and Numbers) made a whole range of TLD's (top-level domains) available - mostly for the benefit of domain registrars who run a protection racket advising companies to register in them ("Nice .com domain name you've got here, squire. Be a shame if someone else registered a similar one, narrmean? [sniff]". Sensibly, most companies have not fallen for the bait, but some registered generic TLD's in which they can sell subdomains. Among these was Google, which - after a long delay - is now offering registrations in such TLD's as .dad, .phd, .mov and .zip.
Now, I'm sure you can see the problem with this. Given the convergence of desktop shells and browsers, with URL's such as file:/// being treated in exactly the same way as https://, how do you know if you are looking at a link to a ZIP file, or to a server in the .zip domain? In fact, the Windows File Explorer search bar will open a .zip domain site if it cannot find the corresponding file on the user's machine. Expect the phishing threat actors to develop even more ingenious deceptions, too.
And sure enough, mr.d0x has provided a couple of interesting proof-of-concept examples. Using only straightforward HTML, CSS, JavaScript and some .png and .webp graphics, he has produced convincing emulations of both the WinRAR file archiving utility and the Windows 11 File Explorer window, along with two use cases: credential harvesting and downloading an executable in place of a document file.
mr.d0x, File Archiver In The Browser, blog post, 22 May 2023. Available online at https://mrd0x.com/file-archiver-in-the-browser/.
Blackberry Threat Intelligence Report
Blackberry might not be a major player in the cellphone market these days, but its Cylance acquisition - now rebadged as Blacberry Cybersecurity - makes it a significant player in the enterprise endpoint detection and response market. The telemetry from this suite of products is used to compile Blackberry's quarterly Global Threat Intelligence Report. The latest edition, covering December 2022 to February 2023, was released recently, and - as with many such reports - makes for interesting reading.
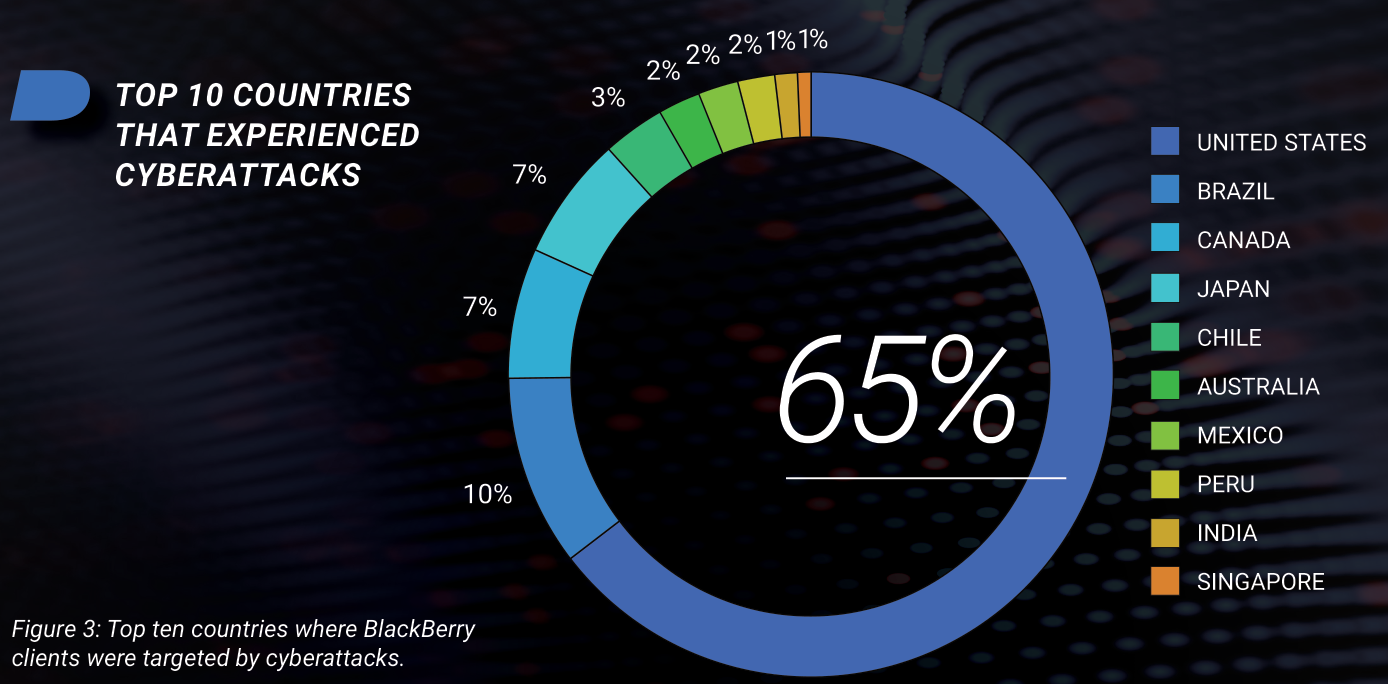
Among the high points:
- Although the US accounted for 65% of attacks detected, Brazil has risen to second place, with 10% of detected attacks. Australia is in sixth place, and Singapore entered the top ten for the first time.
- The most-targeted industries were finance, followed by healthcare and FMCG (fast-moving consumer goods) retailers, collectively accounting for 60% of all malware-based attacks.
- The most frequently-used techniques were droppers, downloaders, remote access trojans and ransomware.
Bestuzhev, Dmitry, et. al., Global Threat Intelligence Report, technical report, April 2023. Available online at https://www.blackberry.com/us/en/solutions/threat-intelligence/2023/threat-intelligence-report-april.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.