Les Bell
Blog entry by Les Bell
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
Zero-Day RCE Vulnerability Impacts Windows, Office
Microsoft has today warned of an unpatched remote code execution vulnerability in multiple Windows and Office versions. The vulnerability, CVE-2023-36884, which has a CVSS base score of 8.3, is reportedly being actively exploited in the wild, using specially-crafted Microsoft Office documents.
While the Redmondites work up a patch, potential victims can mitigate possible infections by setting the following registry key:
Computer\HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Internet Explorer\Main\FeatureControl\FEATURE_BLOCK_CROSS_PROTOCOL_FILE_NAVIGATIONThe active exploitation was first uncovered by the Blackberry Threat Research and Intelligence team, who found two malicious documents submitted from an IP address in Hungary, sent as lures to an organization supporting Ukraine abroad, and a document targeting guests at the Vilnius NATO Summit who may also be providing support to Ukraine. Their analysis led them to attribute this operation to the RomCom group, also known as Tropical Scorpius, Storm-0978, UNC2596 and Void Rabisu, which has a history of attacks against Ukrainian politicians and their Western contacts.
The lures detected by Blackberry were Word documents delivered via a spear-phishing campaign, and when opened used CVE-2023-36884 to download an OLE object and connect to a C2 server in a typosquatting domain - a classic RomCom technique. In this case, they registered the domain ukrainianworldcongress[.]info, which is sufficiently close to the genuine ukrainianworldcongress[.]org that it will escape notice by most users.
The Blackberry blog post provides a detailed run-down of what their researchers observed, while Microsoft Threat Intelligence has also blogged on this, providing additional background information on RomCom campaigns. Finally, the MSRC vulnerability page provides a brief description and mitigation advice.
Blackberry Research & Intelligence Team, RomCom Threat Actor Suspected of Targeting Ukraine's NATO Membership Talks at the NATO Summit, blog post, 8 July 2023. Available online at https://blogs.blackberry.com/en/2023/07/romcom-targets-ukraine-nato-membership-talks-at-nato-summit.
Microsoft Threat Intelligence, Storm-0978 attacks reveal financial and espionage motives, blog post, 11 July 2023. Available online at https://www.microsoft.com/en-us/security/blog/2023/07/11/storm-0978-attacks-reveal-financial-and-espionage-motives/.
Microsoft Security Resource Center, Office and Windows HTML Remote Code Execution Vulnerability (CVE-2023-36884), vulnerability info, 11 July 2023. Available online at https://msrc.microsoft.com/update-guide/vulnerability/CVE-2023-36884.
New Ransomware: Big Head
Back in June, Fortinet picked up on a new ransomware variant called Big Head, which was likely being distributed as a fake Windows Update; samples were subsequently submitted from the US, Spain, Frane and Turkey. Now researchers at Trend Micro have done a deep dive on the operation of this ransomware, uncovering a significant number of Big Head variants, and providing a detailed analysis of three of them.
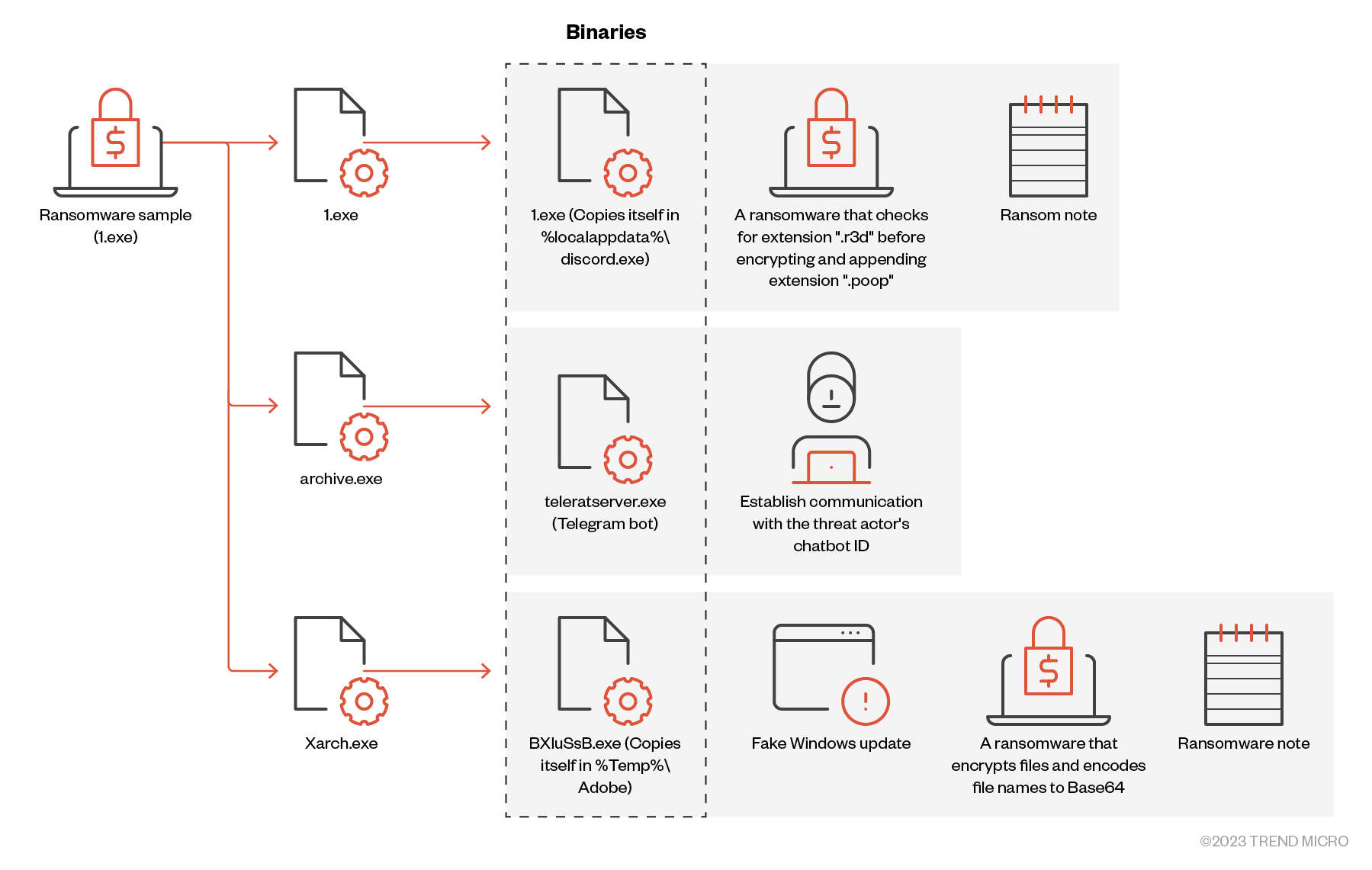
The infection chain of Big Head ransomware sample 1 (image credit: Trend Micro)
The three samples seem to have been distributed via malvertisements as fake Windows updates and fake Word installers; each sample carries three encrypted executables as resources which it decrypts, drops and then runs. In the case of the first sample, each .exe performs a different function: the first randomly generates an ID for this victim, encrypts some files, deletes volume shadow copies and drops the ransom note; the second establishes a C2 channel; the third displays a fake Windows Update window to distract the user while performing the bulk of file encryption before deleting itself.
The second sample carries different executables and while it also performs file encryption for ransom, it also carries a copy of the WorldWind infostealer. The third sample similarly acts as ransomware, but also carries a copy of the Neshta virus - perhaps to act as a distraction for analysts.
Each variant targets specific filetypes and also specific locales; it also takes care to self-terminate if running in CIS locales. Interestingly, the Trend researchers were able to track the malware developers, through their Telegram account, to their YouTube channel where they have uploaded videos demonstrating the malware. The channel name is the Bahasa phrase "aplikasi premium cuma cuma" ("premium application for free") suggesting a SE Asian origin.
At this point, there are no reports of attacks or successful infections with this malware, but it is clear that it is under active development and we can expect further variants in the months to come, making this a useful heads-up to analysts and defenders everywhere.
Gonzalez, Ieriz Nicolle, Katherine Casona and Sarah Pearl Camiling, Tailing Big Head Ransomware’s Variants, Tactics, and Impact, research report, 7 July 2023. Available online at https://www.trendmicro.com/en_us/research/23/g/tailing-big-head-ransomware-variants-tactics-and-impact.html.
More Firefox Updates
It seems like only last week that we reported on the Mozilla Foundation's release of Firefox 115 (it was). And yet here we are, preparing to restart the browser for the installation of Firefox 115.0.2, because of a newly-discovered CVE-2023-3600, a use-after-free vulnerability. You know what to do.
Uncredited, Security Vulnerabilities fixed in Firefox 115.0.2 and Firefox ESR 115.0.2, security advisory, 11 July 2023. Available online at https://www.mozilla.org/en-US/security/advisories/mfsa2023-26/.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.