Les Bell
Blog entry by Les Bell
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
Stolen Microsoft Key - It Could Have Been a Lot Worse
A couple of weeks ago, we brought you news of an attack on Microsoft 365 which affected several US government agencies, and which was believed to be the work of a Chinese APT identified as Storm-0558. The attack was accomplished by forging authentication tokens for Outlook Web Access in Exchange Online and Outlook.com using an acquired Microsoft Managed Service Account (MSA) consumer signing key.
Now, an analysis by Wiz security researcher Shit Tamari indicates that the impact could have been a lot worse. According to the Wiz team, the compromised MSA key could have allowed the threat actor to 'forge access tokens for multiple types of Azure Active Directory applications, including every application that supports personal account authentication, such as SharePoint, Teams, OneDrive, customers’ applications that support the “login with Microsoft” functionality, and multi-tenant applications in certain conditions'.
The breach highlights the importance of identity providers' signing keys in making hard trust decisions. This has long been (sort-of) recognised in the world of TLS certificates - compromising a web site's private key could allow an attacker to masquerade as that site, while compromising the certificate authority's signing private key would allow masquerading as any site using a certificate issued by that CA. But the same concern applies to federated identity management systems which authenticate users via protocols, such as OAuth 2.0 and OpenID, and then trust those users.
The Wiz blog post details how the researchers identified the compromised Microsoft key and then found that it was also able to sign OpenID V 2.0 tokens for multiple types of Azure Active Directory applications.
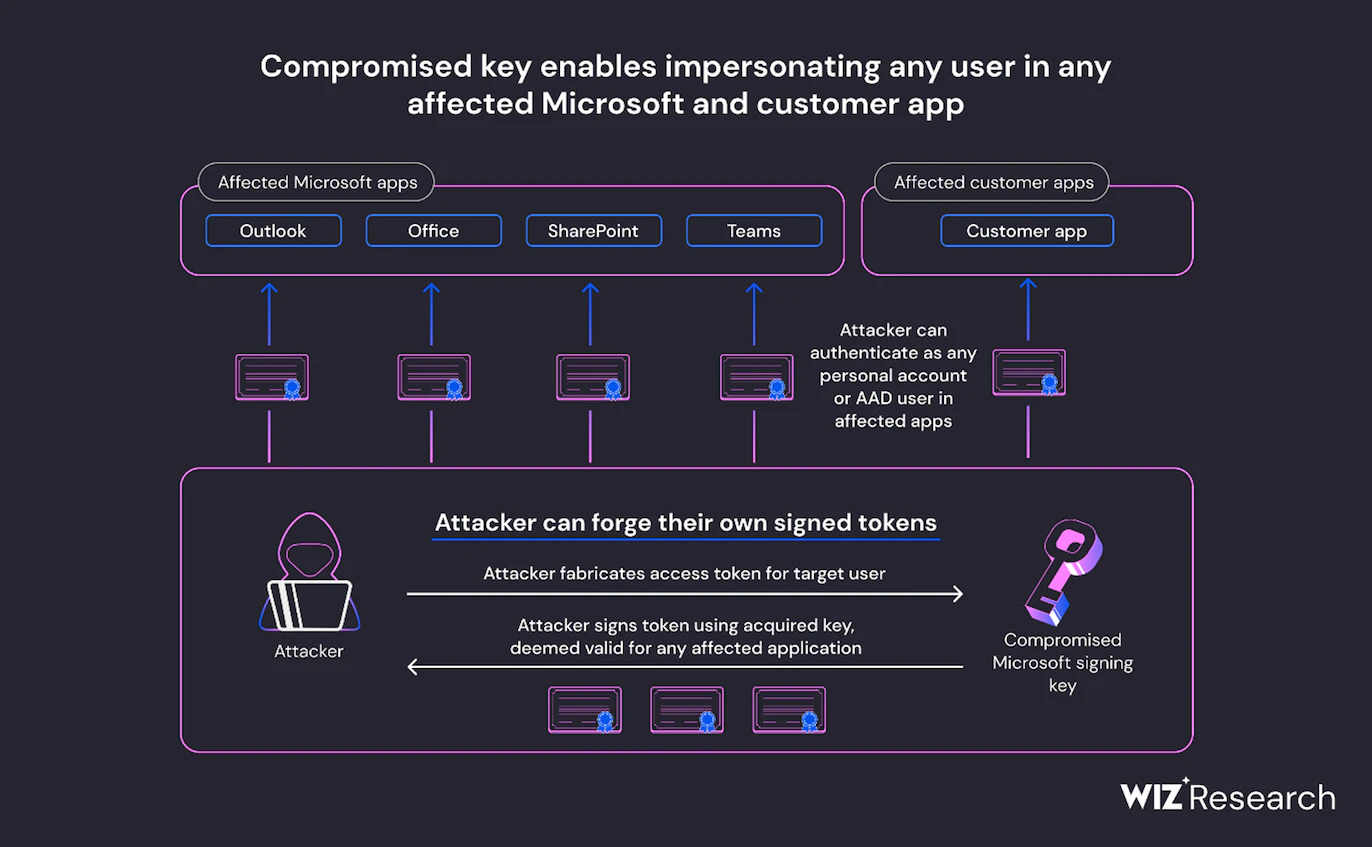
The capabilities of a compromised OpenID signing key (image credit: Wiz Research)
The Wiz blog post clearly outlines the affected applications and provides recommendations for Azure users, including how to detect the compromised key in customer environments.
Tamari, Shir, Compromised Microsoft Key: More Impactful Than We Thought, blog post, 22 July 2023. Available online at https://www.wiz.io/blog/storm-0558-compromised-microsoft-key-enables-authentication-of-countless-micr.
Get Ready for CVSS Version 4.0
Readers are doubtless familiar with the Common Vulnerability Scoring System (CVSS) which allocated a score to vulnerabilities, based on a number of factors, such as whether the attacker needs physical access to the target machine or can run an exploit across the LAN or from the Internet, the attack complexity, and whether the vulnerability will allow the attacker to then pivot to attack other targets. The CVSS score is a key factor in deciding the urgency with which a vulnerability must be patched, along with other factors such as the impact on the specific information asset and the presence of compensating controls such as multiple levels of network segmentation, web application firewalls or an endpoint detection and response product.
Now, FIRST (the Forum of Incident Response and Security Teams) has released the first preview of CVSS 4.0, which is intended to offer finer granularity in base metrics, remove downstream scoring ambiguity, simplify threat metrics and enhance the effectiveness of assessing environment-specific security requirements and compensating controls.
CVSS 4.0 eliminates the somewhat confusing "temporal" metrics of 3.1, instead incorporating a "threat" metric group and also adding two new base metrics: Attack Requirements (AT) and User Interaction (UI) - which can be either Passive (P) or Active (A).
Another important enhancement is new nomenclature to distinguish between the base score and the additional scores:
- CVSS-B: CVSS Base Score
- CVSS-BT: CVSS Base + Threat Score
- CVSS-BE: CVSS Base + Environmental Score
- CVSS-BTE: CVSS Base + Threat + Environmental Score
For some users, the most important change will be the addition of Safety metrics and values to the Supplemental and Environmental metric groups, making CVSS 4.0 more directly applicable to Operational Technology, Industrial Control Systems and IoT environments.
A summary of the changes, along with a highly informative presentation from FIRSTCon23, can be found at https://www.first.org/cvss/v4-0/index.html.
McNulty, Paula, New Common Vulnerability Scoring System (CVSS) set to be cyber sector game-changer, news release, 13 July 2023. Available online at https://www.first.org/newsroom/releases/20230713.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.