Les Bell
Blog entry by Les Bell
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
Cryptominer Targets Linux Systems Via Redis
A new and 'improved' variant of the SkidMap malware has been detected by Trustwave, using a honeypot in Central Europe. SkidMap was first reported by Trend Micro almost four years ago; its primary function is cryptomining, although it could be turned to other objectives by its operator.
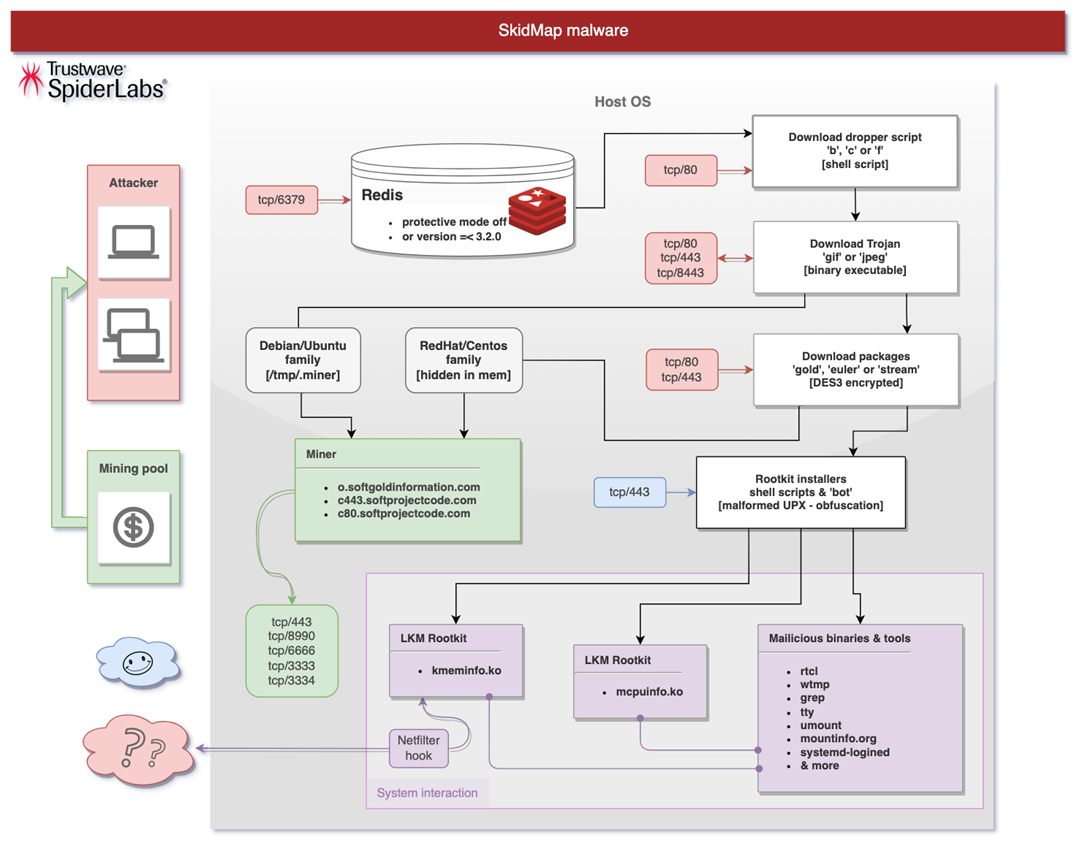
The SkidMap infection chain (image credit: Trustwave)
This latest variant initially infects its target via insecure Redis server installations - either versions prior to version 3.2.0 or instances running with protective mode disabled. The initial infection creates variables which contain base64-encoded cron jobs; when these run they will use either curl or wget to download and tun a dropper script.
The dropper, in turn, downloads an ELF executable called gif into /var/lib. When tun, this installs some SSH keys on the root account, disables SELinux, and then becomes persistent via the creation of more cron jobs; every hour the system creates a reverse shell which contacts the attackers' command and control server. The gif executable checks for various /etc/*-release text files to ascertain which Linux distribution it is running on, and depending on what it finds, it will download one of three different packages: 'gold', 'stream' or 'euler'.
Each package runs a series of shell scripts, cleaning up log entries which would indicate the infection and generally preparing the system for installation of a rootkit which consists of executables and Linux kernel modules. This will hide the operation of the ultimate payload, which is a cryptominer, but the rootkit modules have advanced functionality which go well beyond this - for example, allowing reconfiguring Netfilter to intercept network datagrams.
Once infection is complete, this malware is going to prove difficult to detect - it certainly evades ClamAV and Rkhunter, although Lynis and Chkrootkit do show indications of its presence. A better approach is to put some effort into securing vulnerable Redis installations in the first place, by installing version 3.2.0 or later, setting a strong password and using network segmentation to limit external access.
Zdonczyk, Radoslaw, Honeypot Recon: New Variant of SkidMap Targeting Redis, blog post, 2 August 2023. Available online at https://www.trustwave.com/en-us/resources/blogs/spiderlabs-blog/honeypot-recon-new-variant-of-skidmap-targeting-redis/.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.