Les Bell
Blog entry by Les Bell
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
Kubernetes Admins Urged to Patch Against Remote Command Execution Vuln
Administrators of Kubernetes clusters with Windows endpoints are being urged to update, following the discovery by Akamai security researcher Tomer Peled of a high-severity vulnerability which allows remote command execution. Analysing the vulnerability revealed the underlying root causes: an insecure function call and the lack of user input sanitization. And working forward again from there revealed two more vulnerabilities with the same root causes.
The vulnerabilities are:
All three have a CVSS score of 8.8, and fixes for them were released on 23 August, but they do not yet appear in the National Vulnerability Database.
CVE-2023-3676 allows remote command execution, and the way it does this is instructive. Kubernetes allows directories to be shared between a created pod and the underlying host, and this is done by adding volume parameters in the pod's YAML configuration file. This file is parsed by the kubelet service, and it validates the YAML subPath parameter by calling a function called isLinkPath(), which is where the vulnerability can be exploited:
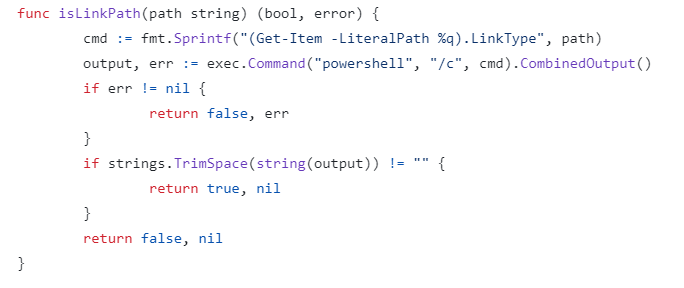
In order to validate the existence of a mount point path, this function directly inserts the path parameter, which is picked up from the YAML file, into a Windows PowerShell command, and then calls exec.Command() to execute it. The presence of exec.Command() is a massive red flag: any code that calls the isLinkPath() function would need to ruthlessly sanitize the path string passed to it. In particular, much like POSIX shells (e.g. bash), PowerShell allows parameter expansion using $( ) syntax. Any command - e.g. Start-process cmd - can be inserted into the $( ), and by placing this into the subPath parameter of the YAML file, it will get passed into the isLinkPath() function, which will assign the cmd variable the value
(Get-Item -LiteralPath $(Start-process cmd).LinkType)
then get PowerShell to execute it - which will first run StartProcess cmd, starting a command prompt, and then try to run Get-Item -LiteralPath on the result. This will probably fail, but for the attacker that's not a problem - they've got the shell they wanted.
Peled's write-up provides a proof-of-concept example, as well as suggested mitigations, the primary one being to apply a patch that fixes the vulnerability, by passing the path parameter to PowerShell as an environment variable, thereby avoiding the parameter expansion. Crude, but effective.
Peled, Tomer, Can't Be Contained: Finding a Command Injection Vulnerability in Kubernetes, blog post, 13 September 2023. Available online at https://www.akamai.com/blog/security-research/kubernetes-critical-vulnerability-command-injection.
CISA Adds Five Vulns to Known Exploited Vulnerabilites Catalog
CISA has added five vulnerabilities to its Known Exploited Vulnerabilities Catalog over the last couple of days.
- CVE-2023-36761 - a Microsoft Word Information Disclosure Vulnerability
- CVE-2023-36802 - a Microsoft Streaming Service Proxy Elevation of Privilege Vulnerability
- CVE-2023-35674 - Android Framework Privilege Escalation Vulnerability
- CVE-2023-20269 - Cisco Adaptive Security Appliance and Firepower Threat Defense Unauthorized Access Vulnerability
- CVE-2023-4863 - Google Chrome Heap-Based Buffer Overflow Vulnerability
In other news, yesterday was the monthly Windows Patchday; September's security updates consists of 59 vulnerabilities.
CISA, CISA Adds Two Known Vulnerabilities to Catalog, alert, 12 September 2023. Available online at https://www.cisa.gov/news-events/alerts/2023/09/12/cisa-adds-two-known-vulnerabilities-catalog.
CISA, CISA Adds Three Known Vulnerabilities to Catalog, alert, 13 September 2023. Available online at https://www.cisa.gov/news-events/alerts/2023/09/13/cisa-adds-three-known-vulnerabilities-catalog.
Microsoft Security Resource Center, September 2023 Security Updates, release note, 12 September 2023. Available online at https://msrc.microsoft.com/update-guide/releaseNote/2023-Sep.
US Agencies Warn of Deepfake Threats
As machine learning and AI continues to rapidly evolve, the US National Security Agency, FBI and CISA have released an information sheet on the problem of deepfaking - the use of synthetic media by threat actors. These AI-generated images, audio and video are used for a variety of tactics, ranging from information operations to spread false information to phishing and whaling attacks.
The 18-page report delves into the challenges posed by deepfakes, the impact deepfaking can have on organizations, and recommendations for mitigating attacks which use them.
CISA, NSA, FBI, and CISA Release Cybersecurity Information Sheet on Deepfake Threats, cybersecurity advisory, 12 September 2023. Available online at https://www.cisa.gov/news-events/alerts/2023/09/12/nsa-fbi-and-cisa-release-cybersecurity-information-sheet-deepfake-threats.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.