Les Bell
Blog entry by Les Bell
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
Cloud Cryptojacking Operation Uses Multiple AWS Services
A new cloud-native cryptojacking operation attributed to Indonesian hackers could cost victims massive amounts as it unexpectedly consumes cloud services before they realize what is occurring. The operation, dubbed AMBERSQUID by the Sysdig researchers who uncovered it, makes use of a number of less-commonly-used AWS services such as the Amplify build and deployment platform, the ECS and Fargate container orchestration service, Codebuild, CloudFormation and EC2 Auto Scaling.
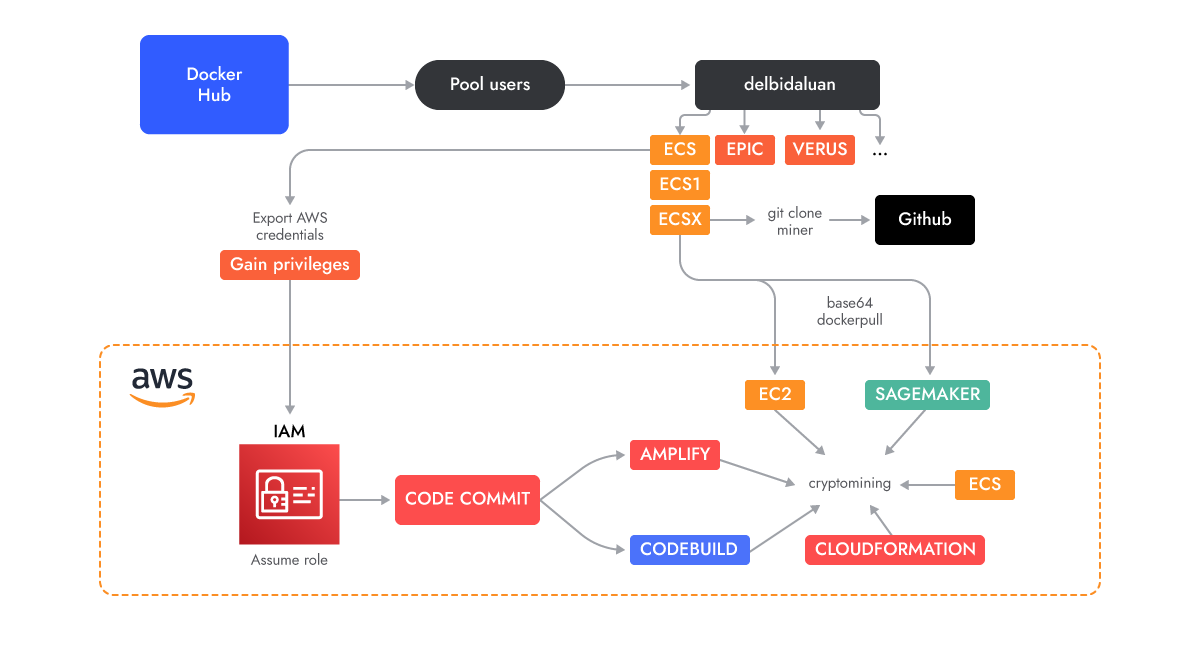
The AMBERSQUID deployment process (Image: Sysdig)
The researchers found AMBERSQUID in an innocuous container image while analysing over 1.7 million Linux images on Docker Hub; static scanning of the image showed no indicators or malicious binaries, and it was only when the image was run that its cryptojacking, using multiple services, was revealed. A number of Docker Hub user accounts are related to this operation - while some have been abandoned, others remain active. When launched, the Docker images download a cryptominer binary from a GitHub account and then run it.
The exploitation begins with execution of a script called amplify-role.sh, which creates the "AWSCodeCommit-Role" role, and then uses it throughout the process in order to add full access permissions for the various AWS services. The scripts that follow use the various services to first, create a private repository for the CodeCommit service in every region, which is then used as a source for the other services, then create five Amplify web apps, running the miner as it does does so, then uses ECS and Fargate to start each container, using 2 virtual CPU's and 4 GB of memory, A similar process is used to run the miner in Codebuild, CloudFormation., EC2 AutoScaling and the Sagemaker deployment tool for machine learning models,
The resulting resource utilization can be very expensive for the victim - assuming a relatively modest number of regions and instance scaling, it would be $US2,244 per day, but it could easily be much more.
While AMBERSQUID targets AWS, the same techniques could be used to exploit similar deployment services offered by other cloud service providers. Defenders tend to focus on the possibility of cryptominers being installed on conventional IaaS instances in EC2, Google Compute Engine, etc. but this case demonstrates that other services need to be secured and monitored as well, with quotas and alerts set even for services not currently in use.
Brucato, Alessandro, AWS’s Hidden Threat: AMBERSQUID Cloud-Native Cryptojacking Operation, blog post, 18 September 2023. Available online at https://sysdig.com/blog/ambersquid/.
Latest Aussie Ransomware Victim: Pizza Hut
Pizza Hut Australia is the latest company to fall victim to a ransomware attack, disclosing the detection of an incident in early September. Subsequent analysis revealed that an unauthorised third party had accessed the data of 193,000 customers, including names, delivery addresses and instructions, email addresses and contact numbers. No usable credit card data or other financial details were exposed.
The affected customers have been contacted by the company, which has also notified the Australian Cyber Security Centre and the Office of the Australian Information Commissioner.
Rawling, Caitlin, Pizza Hut says nearly two-hundred thousand customers affected by data breach, ABC News, 20 September 2023. Available online at https://www.abc.net.au/news/2023-09-20/pizza-hut-customers-affected-by-cyber-hack/102881804.
Upcoming Courses
- SE221 CISSP Fast Track Review, Virtual/Online, 13 - 17 November 2023
- SE221 CISSP Fast Track Review, Sydney, 4 - 8 December 2023
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.