Les Bell
Blog entry by Les Bell
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
GTA VI Videos Leaked, Source Code Stolen
The company behind the incredibly popular Grand Theft Auto series of video games, Rockstar Games, has announced that a threat actor was able to access and download confidential information from their systems, including early development footage of the next edition of the game. The video clips were leaked to a gamer forum by someone calling themselves "teapotuberhacker", suggesting an (unsubstantiated) link to last week's Uber breach, although the material has now been removed. The hacker is demanding a substantial ransom for return of source code and threatening to leak more if not paid.
The videos are claimed to be from a Slack channel used by Rockstar's developers, and the initial breach seems to have been achieved by yet another MFA push deluge - again, similar to the Uber breach. However, Uber is pointing the finger at a different threat actor - see the next story.
Rockstar Games, A Message from Rockstar Games, tweet, 19 September 2022. Available online at https://twitter.com/RockstarGames/status/1571849091860029455.
teapotuberhacker, Hi, Here are 90 fottage/clips from GTA 6, forum post, 18 September 2022. Available online at https://gtaforums.com/topic/985481-gta-6-americas-leak-90-mp4-footagevideos/#comments.
Uber Details Response to Breach
An update from Uber provides more detail on last week's breach, claiming that initial access was achieved when the threat actor used an external contractor's password - likely purchased on the dark web after it was exfiltrated by malware - and coupled this with a deluge of MFA approval requests, to which the contractor eventually succumbed.
Uber's investigations are still continuing, but the company claims that its production systems, which store customer information, were not accessed, and that the attacker did not make any unauthorized changes to their source code. Uber also says that no customer data stored with cloud providers had been accessed.
Uber attributes the attack to the Lapsu$ group, who have previously conducted similar attacks on Cisco, Microsoft and Okta, among others.
Uber Team, Security Update, news release, 19 September 2022. Available online at https://www.uber.com/newsroom/security-update/.
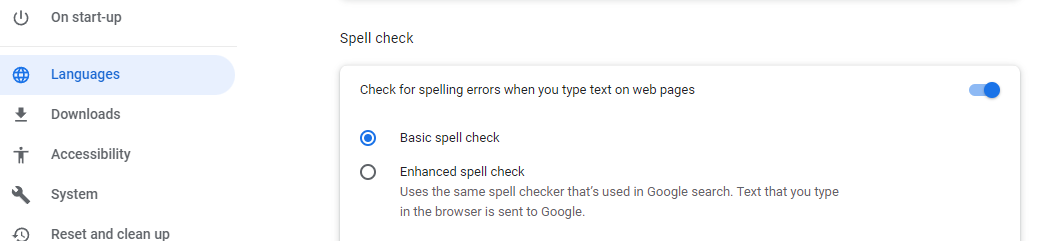
Browser Spell-Checkers Hijack Passwords
Google's Chrome and Microsoft's Edge browsers are both potentialy exposing user passwords by sending them to Google and Microsoft. The exposure occurs when "Enhanced spell check" is enabled, or when Edge's MS Editor is used, in which case any sensitive data entered into form fields will be sent to the vendors' servers, including passwords, if the user clicks on "show password".
This is an obscure, corner-case vulnerability, but users who wish to protect themselves should ensure that this feature is disabled:
otto-js Research Team, Chrome & Edge Enhanced Spellcheck Features Expose PII, Even Your Passwords, news article, 16 September 2022. Available online at https://www.otto-js.com/news/article/chrome-and-edge-enhanced-spellcheck-features-expose-pii-even-your-passwords.
GhostSec Hacks Hotel Swimming Pool
ICS hacking group GhostSec has struck again, according to specialist security firm Otorio, who reported last week on the group's compromises of Berghof PLC devices. This time, the pro-Palestinian hacktivists breached a ProMinent AegisII controller, which continuously measures and controls conductivity abd biocide levels in water - but they did not identify the victim.
Otorio searched for Aegis II controllers on Israeli public IP addresses and successfuly identified the right one, which is managing a hotel swimming pool. Yet again, the breach was due to a password not being changed from the default.
Krivobokov, David, GhostSec Strikes Again in Israel Alleging Water Safety Breach, blog post, 14 September 2022. Available online at https://www.otorio.com/blog/ghostsec-strikes-again-in-israel-seeking-to-impact-swimming-pools/.
Massive Breach of NY Emergency Medical Service
A threat actor, believed to be the Hive ransomware group, has exfiltrated sensitive data, including patient information, from New York medical tranport provider Empress Emergency Medical Services. In a notice to customers, the EMS provider confirms that some of its systems were encrypted and that an "unauthorized party ... copied a small subset of files", revealing that those files contained patient names, dates of service, insurance information and, in some cases, social security numbers.
However, it seems that the breach was much larger than this, totaling 280 GB of contract information, internal budgets and plans, employee and customer info (the latter including email and physical addresses, passport information and more) and the contents of various databases.
Truță, Filip, Hackers Steal 280 GB of Data from NY Emergency Medical Service - Phone Numbers, Passports, SSNs, and More, Bitdefender blog, 19 September 2022. Available online at https://www.bitdefender.com/blog/hotforsecurity/hackers-steal-280gb-of-data-from-ny-emergency-medical-service-phone-numbers-passports-ssns-and-more/.
VMware Releases 2022 Global Incident Response Threat Support
Virtualization (and more) vendor VMware has released its Global Incident Response Threat Report for 2022, delivering 8 "Key Findings":
- Lateral movement is the new battleground - 1 in 10 respondents said they account for at least half of all attacks
- Deepfake attacks shot up 14 percent - 66 percent of respondents witnessed them in the past 12 months
- Cyberattacks have increased since Russia invaded Ukraine - reported 65% of respondents
- Zero-day exploits were encountered by 62% of respondents - up 11% since last year
- Nearly one quarter of attacks now compromise API security - these have emerged as a promising endpoint for exploitation
- Nearly 60% of respondents experienced a ransomware attack in the past 12 months
- 87% of respondents say they are able to disrupt a cybercriminals activities sometimes or often
- Burnout and stress remain a critical issue - although down slightly since last year
Uncredited, Global Incident Response Threat Report, 2022, VMware Inc., September 2022. Available online at https://www.vmware.com/content/dam/learn/en/amer/fy23/pdf/1553238_Global_Incident_Response_Threat_Report_Weathering_The_Storm.pdf.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]() Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License.